Securing Cooperative Spectrum Sensing Against Collusive SSDF Attack using XOR Distance Analysis in Cognitive Radio Networks
Abstract
:1. Introduction
- Analyze the three types of threats of collusive SSDF attackers in detail. The first one is profit-driven, in which collusive SSDF attackers conspire with each other to falsify the sensing data inspired by some profits such as monopolizing vacant PU spectrums. The second is manipulating the trust mechanism, in which collusive SSDF attackers can improve their trust value quickly. The third is disturbing data fusion, in which collusive SSDF attackers can submit their false sensing data to disturb the data fusion of FC successfully with high trust value.
- Noting the duality of sensing data submitted by collusive SSDF attackers, the XOR distance calculation in line with the type of “0” and “1” historical sensing data is introduced. Based on the fact that collusive SSDF attackers hold the the lower XOR distance and high trust value simultaneously, a lightweight algorithm to detect collusive SSDF attackers is designed.
- Enhance the accuracy of trust evaluation. By reducing the increase of “the number of honest sensing data” with XDA, collusive SSDF attackers will not get a high trust value again. As a result, they can be detected by a trust mechanism.
2. Preliminaries
2.1. Cooperative Spectrum Sensing
2.2. Trust Mechanism
3. Collusive SSDF Attack and Defense Scheme
3.1. Collusive SSDF Attack Overview
- Profit-driven: Inspired by some profits, collusive SSDF attackers can conspire with each other to form a collusive clique to falsify the sensing data intentionally. For example, they can monopolize vacant PU spectrums in the CSS environment. They submit false sensing data together to show the spectrum of a PU is in use, although it is idle. In this case, other SUs would recognize that the licensed spectrum is present and would not use the spectrum. Thus, collusive an SSDF attackers clique can gain exclusive access to the target licensed spectrum.
- Manipulate trust mechanism: By collusion, collusive SSDF attackers can improve their trust value quickly. For example, one of the collusive SSDF attackers who knows the actual status of a PU spectrum would tell this PU spectrum status to his conspirers in advance, and then sends a query message to the FC. Their trust values can be improved quickly if their sensing data are as consistent as the PU spectrum status.
- Disturb data fusion: As we know, the most primal attackers need to disturb some systems. With high trust value, collusive SSDF attackers can bypass the detection of the trust mechanism, and thus submit their false sensing data to indicate that the spectrum band of a PU spectrum is idle. As a result, they can disturb the data fusion of FC successfully, and ultimately deceive honest SUs to interfere PUs. In fact, SUs must never interfere with PUs in CSS [2]. If cause any interference to PUs, the availability of CSS will be questioned.
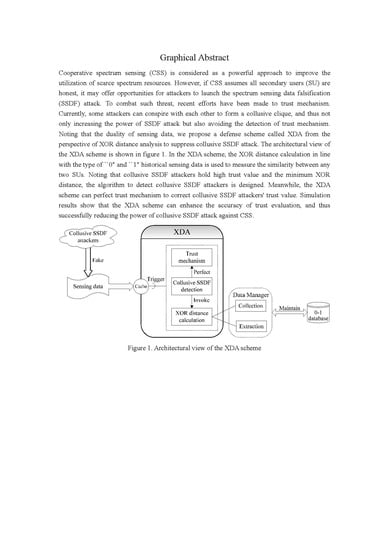
3.2. Design of XDA Scheme
- Duality: SUs often submit the type of “0” and “1” sensing data to represent the hypothesis of the inexistence and the existenc of PU spectrum status. Thus, the sensing behaviors of SUs in the CSS environment can be abstracted as the duality due to the type of “0” and “1” sensing data.
- Action together: Collusive SSDF attackers always submit false sensing data together no matter which threats they would launch. They can fake “1” data together to monopolize vacant PU spectrums, or fake “0” data together to disturb the data fusion.
- High trust value: Collusive SSDF attackers often have high trust value. With the help of each other, they can improve their trust value by manipulating the trust mechanism.
3.2.1. XOR Distance Calculation
| Procedure 1 Eliminate redundancy |
|
3.2.2. Collusive SSDF Detection
| Procedure 2 Detect collusive SSDF attackers |
|
3.2.3. Perfect Trust Mechanism
| Procedure 3 Perfect trust mechanism |
|
4. Simulation Results and Discussion
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| CSS | Cooperative Spectrum Sensing |
| SU | Secondary User |
| PU | Primary User |
| FC | Fusion Center |
| SSDF | Spectrum Sensing Data Falsification |
| XDA | XOR Distance Analysis |
References
- Federal Communications Commission. Spectrum Policy Task Force. Rep. ET Docket no. 02-135; 2002. Available online: http://www.fcc.gov/sptf/files/SEWGFinalReport_1.pdf (accessed on 25 September 2017).
- Mitola, J. Cognitive Radio: An Integrated Agent Architecture for Software Defined Radio. Ph.D. Dissertation, Royal Instutute of Technology (KTH), Stockholm, Sweden, June 2000. [Google Scholar]
- Akyildiz, I.F.; Lo, B.F.; Balakrishnan, R. Cooperative spectrum sensing in cognitive radio networks: A survey. Phys. Commun. 2011, 4, 40–62. [Google Scholar] [CrossRef]
- Cabric, D.; Mishra, S.; Brodersen, R. Implementation issues in spectrum sensing for cognitive radios. In Proceedings of the Asilomar Conference on Signals, Systems, and Computers, Asilomar, Pacific Grove, CA, USA, 7–10 November 2004; pp. 772–776. [Google Scholar]
- Lin, Y.P.; He, C.; Jiang, L.G.; He, D. Cooperative spectrum sensing based on stochastic resonance in cognitive radio networks. Sci. China Inf. Sci. 2014, 57, 1–10. [Google Scholar]
- Feng, J.Y.; Zhang, Y.Q.; Lu, G.Y.; Zhang, L. Securing cooperative spectrum sensing against rational SSDF Attack in cognitive radio networks. KSII Trans. Int. Inf. Syst. 2014, 8, 1–17. [Google Scholar]
- Chen, R.L.; Park, J.M.; Hou, Y.T. Toward secure distributed spectrum sensing in cognitive radio networks. IEEE Commun. Mag. 2008, 46, 50–55. [Google Scholar] [CrossRef]
- Qin, T.; Yu, H.; Leung, C. Towards a trust-aware cognitive radio architecture. ACM Sigmob. Mob. Comput. Commun. Rev. 2009, 13, 86–95. [Google Scholar] [CrossRef]
- Zeng, K.; Peng, Q.H.; Tang, Y.X. Mitigating spectrum sensing data falsification attacks in hard-decision combining cooperative spectrum sensing. Sci. China Inf. Sci. 2014, 57, 1–9. [Google Scholar] [CrossRef]
- Chen, R.; Park, J.M.; Bian, K. Robust distributed spectrum sensing in cognitive radio networks. In Proceedings of the 30th IEEE INFOCOM Conference, Phoenix, AZ, USA, 13–18 April 2008; pp. 1876–1884. [Google Scholar]
- Kar, S.; Sethi, S.; Sahoo, R.K. A Multi-factor Trust Management Scheme for Secure Spectrum Sensing in Cognitive Radio Networks. Wirel. Pers. Commun. 2017, 97, 2523–2540. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Lo, B.F.; Balakrishnan, R. Cooperative spectrum sensing in cognitive radio networks: A survey. Phys. Commun. 2011, 4, 40–62. [Google Scholar] [CrossRef]
- Peh, E.; Liang, Y.C.; Guan, Y.L.; Zeng, Y. Optimization of cooperative sensing in cognitive radio networks: A sensing-throughput tradeo view. IEEE Trans. Veh. Technol. 2009, 58, 5294–5299. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Lee, W.Y.; Chowdhury, K.R. CRAHNs: Cognitive radio ad hoc networks. Ad Hoc Netw. 2009, 7, 810–836. [Google Scholar] [CrossRef]
- Morid, M.A.; Shajari, M. An enhanced e-commerce trust model for community based centralized systems. Electron. Commer. Res. 2012, 12, 409–427. [Google Scholar] [CrossRef]
- Li, X.Y.; Zhou, F.; Yang, X.D. Scalable feedback aggregating (SFA) overlay for large-Scale P2P trust management. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1944–1957. [Google Scholar] [CrossRef]
- Boukerche, A.; Ren, Y.; Pazzi, R. An adaptive computational trust model for mobile ad hoc networks. In Proceedings of the 5th International Conference on Wireless Communications and Mobile Computing, Leipzig, Germany, 21–24 June 2009; pp. 191–195. [Google Scholar]
- Mohaisen, A.; Hopper, N.; Kim, Y. Keep your friends close: Incorporating trust into social-network-based sybil defenses. In Proceedings of the 30th IEEE INFOCOM Conference, Shanghai, China, 10–15 April 2011; pp. 1943–1951. [Google Scholar]
- Jφsang, A.; Ismail, R. The beta reputation system. In Proceedings of the 15th Bled Electronic Commence Conference, Bled, Slovenia, 17–19 June 2002. [Google Scholar]
- Gamma Function. Available online: http://en.wikipedia.org/wiki/Gammafunction (accessed on 18 October 2017).
- Douceur, J.R. The sybil attack. In International Workshop on Peer-To-Peer Systems; Springer: Berlin/Heidelberg, Germany; pp. 251–260.
- Yu, H.; Gibbons, P.; Kaminsky, M.; Xiao, F. Sybillimit: A near-optimal social network defense against sybil attacks. In Proceedings of the 2008 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 18–22 May 2008. [Google Scholar]
- Yu, H.; Kaminsky, M.; Gibbons, P.; Flaxman, A. Sybilguard: Defending against sybil attacks via social networks. In Proceedings of the 2006 ACM SIGCOMM, Pisa, Italy, 11–15 September 2006; pp. 267–278. [Google Scholar]
- Irani, J.; Pise, N.; Phatak, M. Clustering Techniques and the Similarity Measures used in Clustering: A Survey. Int. J. Comput. Appl. 2016, 134, 9–14. [Google Scholar] [CrossRef]







| Sensing Times | ID(Sensing Data) | |||||
|---|---|---|---|---|---|---|
| 1 | ⋯ | ⋯ | ||||
| 2 | ⋯ | ⋯ | ||||
| ⋯ | ⋯ | ⋯ | ⋯ | ⋯ | ⋯ | ⋯ |
| k | ⋯ | ⋯ | ||||
| Parameters | Description | Default |
|---|---|---|
| Number of SUs | 60 | |
| Number of PUs | 3 | |
| cycle | Number of cycle simulation | 100 |
| round | Rounds of attack | 50 |
| Percentage of attackers | 10∼50% | |
| Threshold of trust value | 0.8 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Feng, J.; Zhang, M.; Xiao, Y.; Yue, H. Securing Cooperative Spectrum Sensing Against Collusive SSDF Attack using XOR Distance Analysis in Cognitive Radio Networks. Sensors 2018, 18, 370. https://doi.org/10.3390/s18020370
Feng J, Zhang M, Xiao Y, Yue H. Securing Cooperative Spectrum Sensing Against Collusive SSDF Attack using XOR Distance Analysis in Cognitive Radio Networks. Sensors. 2018; 18(2):370. https://doi.org/10.3390/s18020370
Chicago/Turabian StyleFeng, Jingyu, Man Zhang, Yun Xiao, and Hongzhou Yue. 2018. "Securing Cooperative Spectrum Sensing Against Collusive SSDF Attack using XOR Distance Analysis in Cognitive Radio Networks" Sensors 18, no. 2: 370. https://doi.org/10.3390/s18020370
APA StyleFeng, J., Zhang, M., Xiao, Y., & Yue, H. (2018). Securing Cooperative Spectrum Sensing Against Collusive SSDF Attack using XOR Distance Analysis in Cognitive Radio Networks. Sensors, 18(2), 370. https://doi.org/10.3390/s18020370