Lightweight Cipher for H.264 Videos in the Internet of Multimedia Things with Encryption Space Ratio Diagnostics
Abstract
:1. Introduction
- Q1.
- Are those encryption schemes computationally efficient enough (in terms of execution/encoding time) to employ in an IoMT communication environment?
- Q2.
- Is the analyzed ESR effective enough to apply SE to visually secure the videos encoded with one or other of the two common entropy coders in common codec use, that is, context adaptive variable length coding (CAVLC) and context adaptive binary arithmetic coding (CABAC) (see Section 4.1)?
1.1. Context
- Design of a joint crypto-compression scheme acting upon selected video syntax elements output by the entropy engine of an H.264/AVC encoder. SE is applied, keeping in mind the requirements of IoMT devices.
- Ensuring that those selected syntax elements do not, once encrypted, have the potential to crash a decoder at the receiver. In other words, ensuring that they are format compatible with the H.264/AVC standard, even when encrypted.
- Application of ESR to the output from two entropy coders, CAVLC and CABAC. ESR is used as a diagnostic tool to obtain efficient SE. ESR was applied to ten test or benchmark video sequences. (The same procedure has been applied to video clips captured by constrained RasPi cameras.)
- Finding that the ESR estimate for CABAC is less than CAVLC, which implies that the CABAC entropy coder is suitable for IoMT cameras.
- Introducing an innovative, single-round, lightweight cipher EXPer (with five sequential steps of block-level eXclusive OR (XOR) cipher and bit-level permutation).
- Performing a series of experiments with EXPer upon the output of an H.264/AVC encoder, comparing that cipher to simple XOR and the industry-standard advanced encryption standard (AES) [11]. Therefore, three different ciphers are extensively tested (from different aspects) on multiple videos with varying color and motion characteristics. The perceptual strength of the ciphers is compared through different video quality metrics and their computational efficiency is evaluated in terms of execution time on tested videos.
- Performing cryptanalysis that EXPer is secure against a variety of attacks, including key guessing, perceptual, known-plaintext attacks as well as statistical and inference attacks.
2. Related Studies
3. Materials and Methods
- Selection of syntax elements for two entropy engines, such as, CAVLC and CABAC.
- EXPer, an innovative lightweight cipher based on a combination of XOR and bit-level permutation rounds, with three different 128-bit keys.
- ESR is calculated according to the selected syntax elements of CAVLC and CABAC, as a way of diagnosing the effective visual protection (Section 4).
- SE is applied by utilizing EXPer, according to the guidance given by ESR (Section 4).
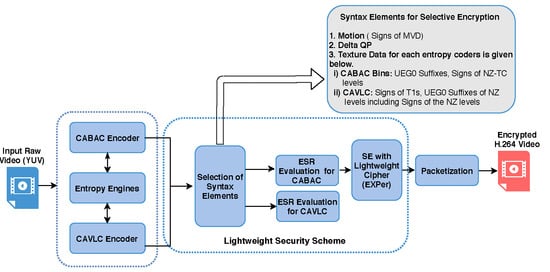
3.1. Syntax Elements Selection of Entropy Coders
3.2. Lightweight Cipher
3.2.1. Working of EXPer
- Step 1: In the first step, the input bitstream is encrypted by performing an XOR operation with a 128-bit secret key. Let X be the selected syntax elements (or bins) of the CABAC entropy coder. Then, X is XORed with the secret key, k_1. In other words, each 128-bit block of the stream of selected syntax elements, extracted from the original compressed bitstream, is encrypted and then in encrypted form is placed back into the output bitstream:where ⊕ is the XOR operator, X contains the syntax elements (or bins) selected from any input bitstream, and X’ contains the resulting encrypted syntax elements, grouped in blocks of 128-bits.X⊕ k_1 = X’
- Step 2: In the second step, a permutation is applied to the encrypted output X’ of (1). Thus, the selected and encrypted syntax elements are re-ordered through the permutation. Specifically, the elements of X’, on a byte-by-byte basis, are cyclically permutated by offset value v_1 using a circular right-shift operator. The shift operation in general is represented in (2), in which the input bytes are transformed, byte-by-byte, into the encrypted and permuted output, as shown in (2) for an offset value one, and in general in (3) by the value of v_1(x1, x2, x3…) ↦ (x2, x3, x4…)where ↦ is a transformation symbol and >>> is a circular shift operator that signifies transforming X’ into the X’’ bitstream, through a circular right-shift of the bits of each byte of X’. v_1 denotes an offset value.X’ >>> v_1 = X’’
- Step 3: In the next step, the resulting output of the previous step, which is X’’, is again transformed by an XOR operation with the 128-bit sub-key k_2, as:X’’⊕ k_2 = X’’’As already mentioned in Section 3.2, k_2 is derived by means of a PRF.
- Step 4: In the fourth step, the previously encrypted output X’’’ is permutated once again with offset value v_2, again by a circular right-shift operator, applied on a per byte basis:X’’’ >>> v_2 = X’’’’
- Step 5: In the final step, the resulting bitstream, X’’’’, is XORed with the 128-bit sub_key2 (k_3), to produce encrypted bitstream Eoutput:X’’’’⊕ k_3 = EoutputSubsequently, the bits of encrypted bitstream Eoutput are re-merged with the compressed video bitstream. In that way, a decoder receives a format compatible bitstream, according to the format of the H.264/AVC standard.
4. Experimental Results and Discussion
4.1. Calculation of ESR for Entropy Coders
4.2. Performance of EXPer
4.3. Computational Cost Analysis
4.4. Security Analysis of EXPer
4.4.1. Perceptual Security
4.4.2. Peak signal to noise ratio (PSNR)
4.4.3. Pixel-correlation analysis
4.4.4. Structural Similarity Index (SSIM)
5. Comparison of EXPer with State-of-the-Art Ciphers
5.1. Comparative Visual Quality Analysis
5.2. Comparative Computational Efficiency
5.3. Comparative Security Analysis
5.4. Comparative Entropy Analysis
5.5. Cryptanalysis of Proposed ESR-Validated Security Scheme
5.5.1. Differential Attack
5.5.2. Known-Plaintext and Correlation Attack
5.5.3. Interference Attack
5.6. Discussion and Limitations
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutorials 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Alvi, S.A.; Afzal, B.; Shah, G.A.; Atzori, L.; Mahmood, W. Internet of Multimedia Things: Vision and challenges. Ad Hoc Networks 2015, 33, 87–111. [Google Scholar] [CrossRef]
- Aslam, A.; Curry, E. Towards a generalized approach for deep neural network based event processing for the Internet of Multimedia Things. IEEE Access 2018, 6, 25573–25587. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Futur. Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Networks 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Kim, S.K.; Sahu, N.; Preda, M. Beginning of a new standard: Internet of Media Things. KSII Trans. Internet Inf. Syst. 2017, 11, 5182–5199. [Google Scholar]
- Shifa, A.; Asghar, M.N.; Fleury, M. Multimedia security perspectives in IoT. In Proceedings of the 2016 Sixth International Conference on Innovative Computing Technology (INTECH), Dublin, Ireland, 24–26 August 2016; pp. 550–555. [Google Scholar]
- Semertzidis, T.; Dimitropoulos, K.; Koutsia, A.; Grammalidis, N. Video sensor network for real-time traffic monitoring and surveillance. IET Intell. Transp. Syst. 2010, 4, 103. [Google Scholar] [CrossRef]
- Asghar, M.N.; Kousar, R.; Majid, H.; Fleury, M. Transparent encryption with scalable video communication: Lower-latency, CABAC-based schemes. J. Vis. Commun. Image Represent. 2017, 45, 122–136. [Google Scholar] [CrossRef]
- Shifa, A.; Afgan, M.S.; Asghar, M.N.; Fleury, M.; Memon, I.; Abdullah, S.; Rasheed, N. Joint crypto-stego scheme for enhanced image protection with nearest-centroid clustering. IEEE Access 2018, 6, 16189–16206. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology. Advanced Encryption Standard (AES). 2001, no. 197. Available online: https://nvlpubs.nist.gov/nistpubs/fips/nist.fips.197.pdf (accessed on 10 March 2019).
- Long, M.; Peng, F.; Li, H. Separable reversible data hiding and encryption for HEVC video. J. Real-Time Image Process. 2018, 14, 171–182. [Google Scholar] [CrossRef]
- Shahid, Z.; Puech, W. Visual Protection of HEVC Video by Selective Encryption of CABAC Binstrings. IEEE Trans. Multimed. 2014, 16, 24–36. [Google Scholar] [CrossRef]
- Adeyemi-Ejeye, A.O.; Alreshoodi, M.; Al-Jobouri, L.; Fleury, M. Prospects for live higher resolution video streaming to mobile devices: achievable quality across wireless links. J. Real-Time Image Process. 2018, 16, 127–141. [Google Scholar] [CrossRef]
- Lookabaugh, T.; Sicker, D.C. Selective encryption for consumer applications. IEEE Commun. Mag. 2004, 42, 124–129. [Google Scholar] [CrossRef]
- Asghar, M.N.; Fleury, M.; Makki, S. Interoperable conditional access with video selective encryption for portable devices. Multimed. Tools Appl. 2017, 76, 13139–13152. [Google Scholar] [CrossRef]
- Dufaux, F. Video scrambling for privacy protection in video surveillance—Recent results and validation framework. SPIE Defense, Secur. Sens. 2011, 8063, 1–14. [Google Scholar]
- Peng, F.; Zhu, X.-w.; Long, M. An ROI privacy protection scheme for H.264 video based on FMO and chaos. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1688–1699. [Google Scholar] [CrossRef]
- Massoudi, A.; Lefebvre, F.; De Vleeschouwer, C.; Macq, B.; Quisquater, J.-J. Overview on selective encryption of image and video: Challenges and perspectives. EURASIP J. Inf. Secur. 2008, 2008, 1–18. [Google Scholar] [CrossRef]
- Zhang, Z.-K.; Cho, M.C.Y.; Wang, C.-W.; Hsu, C.-W.; Chen, C.-K.; Shieh, S. IoT security: Ongoing challenges and research opportunities. In Proceedings of the 2014 IEEE 7th International Conference on Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014; pp. 230–234. [Google Scholar]
- Ghanbari, M. Standard codecs: Image compression to Advanced Video Coding; IET: London, UK, 2003. [Google Scholar]
- Wiegand, T.; Sullivan, G.J.; Bjontegaard, G.; Luthra, A. Overview of the H.264/AVC video coding standard. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 560–576. [Google Scholar] [CrossRef]
- Stutz, T.; Uhl, A. A survey of H.264 AVC/SVC encryption. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 325–339. [Google Scholar] [CrossRef]
- Schwarz, H.; Marpe, D.; Wiegand, T. Overview of the scalable video coding extension of the H.264/AVC standard. IEEE Trans. Circuits Syst. Video Technol. 2007, 17, 1103–1120. [Google Scholar] [CrossRef]
- Shahid, Z.; Chaumont, M.; Puech, W. Fast protection of H.264/AVC by selective encryption of CAVLC and CABAC for I and P frames. IEEE Trans. Circuits Syst. Video Technol. 2011, 21, 565–576. [Google Scholar] [CrossRef]
- Bjøntegaard, G.; Lillevold, K. Context-adaptive VLC coding of coefficients. 2002, JVT document JVT-C028. Available online: https://www.itu.int/wftp3/av-arch/jvt-site/2002_05_Fairfax/JVT-C028.doc (accessed on 10 March 2019).
- Marpe, D.; Schwarz, H.; Wiegand, T. Context-based adaptive binary arithmetic coding in the H.264/AVC video compression standard. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 620–636. [Google Scholar] [CrossRef]
- Sullivan, G.J.; Ohm, J.-R.; Han, W.-J.; Wiegand, T. Overview of the High Efficiency Video Coding (HEVC) standard. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 1649–1668. [Google Scholar] [CrossRef]
- Usman, M.; Jan, M.A.; He, X.; Nanda, P. Data sharing in secure multimedia wireless sensor networks. In Proceedings of the 2016 IEEE Trustcom/BigDataSE/ISPA, Tianjin, China, 23–26 August 2016; pp. 590–597. [Google Scholar]
- Raspberry Pi. Available online: https://projects.raspberrypi.org/en/projects/getting-started-with-picamera/7 (accessed on 30 November 2018).
- Li, S.; Chen, G.; Zheng, X. Chaos-based encryption for digital images and videos. In Multimedia Security Handbook; Furht, B., Kirovski, D., Eds.; RC Press: Boca Raton, FL, USA, 2005; pp. 133–168. [Google Scholar]
- Liu, F.; Koenig, H. A survey of video encryption algorithms. Comput. Secur. 2010, 29, 3–15. [Google Scholar] [CrossRef]
- El Assad, S.; Farajallah, M. A new chaos-based image encryption system. Signal Process. Image Commun. 2016, 41, 144–157. [Google Scholar] [CrossRef]
- Al Salami, S.; Baek, J.; Salah, K.; Damiani, E. Lightweight encryption for smart home. In Proceedings of the 2016 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 382–388. [Google Scholar]
- Yao, X.; Chen, Z.; Tian, Y. A lightweight attribute-based encryption scheme for the Internet of Things. Futur. Gener. Comput. Syst. 2015, 49, 104–112. [Google Scholar] [CrossRef]
- Xin, M. A mixed encryption algorithm used in Internet of Things security transmission system. In Proceedings of the 2015 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery, Xi’an, China, 17–19 September 2015; pp. 62–65. [Google Scholar]
- Prasetyo, K.N.; Purwanto, Y.; Darlis, D. An implementation of data encryption for Internet of Things using Blowfish algorithm on FPGA. In Proceedings of the 2014 2nd International Conference on Information and Communication Technology (ICoICT), Bandung, Indonesia, 28–30 May 2014; pp. 75–79. [Google Scholar]
- Lee, J.-Y.; Lin, W.-C.; Huang, Y.-H. A lightweight authentication protocol for Internet of Things. In Proceedings of the 2014 International Symposium on Next-Generation Electronics (ISNE), Kwei-Shan, Taiwan, 7–10 May 2014; pp. 1–2. [Google Scholar]
- Mahalle, P.N.; Anggorojati, B.; Prasad, N.R.; Prasad, R.R. Identity Authentication and Capability Based Access Control (IACAC) for the Internet of Things. J. Cyber Secur. Mobil. 2013, 1, 309–348. [Google Scholar]
- Sundaram, V.B.; Ramnath, M.; Prasanth, M.; Sundaram, J.V. Encryption and hash based security in Internet of Things. In Proceedings of the 2015 3rd International Conference on Signal Processing, Communication and Networking (ICSCN), Chennai, India, 26–28 March 2015; pp. 1–6. [Google Scholar]
- Gao, T.; Chen, Z. Image encryption based on a new total shuffling algorithm. Chaos, Solitons Fractals 2008, 38, 213–220. [Google Scholar] [CrossRef]
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.B.; Seurin, Y.; Vikkelsoe, C. PRESENT: An ultra-lightweight block cipher. In Cryptographic Hardware and Embedded Systems - CHES 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466. [Google Scholar]
- Zhang, G.; Liu, Q. A novel image encryption method based on total shuffling scheme. Opt. Commun. 2011, 284, 2775–2780. [Google Scholar] [CrossRef]
- Engels, D.; Saarinen, M.-J.O.; Schweitzer, P.; Smith, E.M. The Hummingbird-2 Lightweight Authenticated Encryption Algorithm. In RFIDSec 2011: RFID. Security and Privacy; Juels, A., Paar, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 19–31. [Google Scholar]
- Suzaki, T.; Minematsu, K.; Morioka, S.; Kobayashi, E. TWINE: A lightweight block cipher for multiple platforms. In Proceedings of the 19th International Conference on Selected Areas in Cryptography, SAC 2012, Windsor, ON, Canada, 15–16 August 2012; pp. 339–354. [Google Scholar]
- Albrecht, M.R.; Driessen, B.; Kavun, E.B.; Leander, G.; Paar, C.; Yalçın, T. Block ciphers–Focus on the linear layer (feat. PRIDE). In CRYPTO 2014: Advances in Cryptology – CRYPTO 2014; Garay, J.A., Gennaro, R., Eds.; Springer: Berlin/Heidelberg, Germany; pp. 57–76.
- Janakiraman, S.; Thenmozhi, K.; Rayappan, J.B.B.; Amirtharajan, R. Lightweight chaotic image encryption algorithm for real-time embedded system: Implementation and analysis on 32-bit microcontroller. Microprocess. Microsyst. 2018, 56, 1–12. [Google Scholar] [CrossRef]
- Noura, H.; Chehab, A.; Sleem, L.; Noura, M.; Couturier, R.; Mansour, M.M. One round cipher algorithm for multimedia IoT devices. Multimed. Tools Appl. 2018, 77, 18383–18413. [Google Scholar] [CrossRef]
- Lei, B.Y.; Lo, K.T.; Lei, A.H. New H.264 video encryption scheme based on chaotic cipher. In Proceedings of the 2010 International Conference on Communications, Circuits and Systems (ICCCAS), Chengdu, China, 28–30 July 2010; pp. 373–377. [Google Scholar]
- François, M.; Grosges, T.; Barchiesi, D.; Erra, R. A new image encryption scheme based on a chaotic function. Signal Process. Image Commun. 2012, 27, 249–259. [Google Scholar] [CrossRef]
- Bellovin, S.M.; Housley, R. Guidelines for Cryptographic Key Management. 2005. Available online: https://www.rfc-editor.org/rfc/rfc4107.txt (accessed on 17 February 2019).
- Asghar, M.N.; Ghanbari, M.; Fleury, M.; Reed, M.J. Sufficient encryption based on entropy coding syntax elements of H.264/SVC. Multimed. Tools Appl. 2015, 74, 10215–10241. [Google Scholar] [CrossRef]
- Asghar, M.N.; Ghanbari, M. An efficient security system for CABAC bin-strings of H.264/SVC. IEEE Trans. Circuits Syst. Video Technol. 2013, 23, 425–437. [Google Scholar] [CrossRef]
- Khan, J.S.; Ahmad, J. Chaos based efficient selective image encryption. Multidimens. Syst. Signal Process. 2018, 1–19. [Google Scholar] [CrossRef]
- Asghar, M.N.; Ghanbari, M.; Fleury, M.; Reed, M.J. Confidentiality of a selectively encrypted H.264 coded video bit-stream. J. Vis. Commun. Image Represent. 2014, 25, 487–498. [Google Scholar] [CrossRef]
- Test videos. Available online: https://media.xiph.org/video/derf/ (accessed on 16 February 2019).
- JSVM reference software. Available online: https://www.hhi.fraunhofer.de/en/departments/vca/research-groups/image-video-coding/research-topics/svc-extension-of-h264avc/jsvm-reference-software.html (accessed on 16 February 2019).
- Bhardwaj, S.; Mittal, A. A survey on various edge detector techniques. Procedia Technol. 2012, 4, 220–226. [Google Scholar] [CrossRef]
- Huynh-Thu, Q.; Ghanbari, M. The accuracy of PSNR in predicting video quality for different video scenes and frame rates. Telecommun. Syst. 2012, 49, 35–48. [Google Scholar] [CrossRef]
- Wang, Z.; Bovik, A.C.; Sheikh, H.R.; Simoncelli, E.P. Image quality assessment: From error visibility to structural similarity. IEEE Trans. Image Process. 2004, 13, 600–612. [Google Scholar] [CrossRef]
- Arroyo, D.; Li, C.; Li, S.; Alvarez, G.; Halang, W.A. Cryptanalysis of an image encryption scheme based on a new total shuffling algorithm. Chaos, Solitons Fractals 2009, 41, 2613–2616. [Google Scholar] [CrossRef]
- Wang, X.; He, G. Cryptanalysis on a novel image encryption method based on total shuffling scheme. Opt. Commun. 2011, 284, 5804–5807. [Google Scholar] [CrossRef]
















| Proposed Scheme | Year | Platform | Algorithms Used | Strengths | Limitations |
|---|---|---|---|---|---|
| El Assad S, Farajallah M [33] | 2016 | FPGA card or an ASIC/ | Diffusion and chaotic map (2D cat map) | Efficient and provides: A high-level of security, resistance to known plaintext and chosen plaintext attacks | Requires a huge memory capacity |
| Al-Salami et al. [34] | 2016 | Smart Home | Identity-based encryption (IBE), Stateful Diffie-Hellman (DH) Encryption, Private Key Generator (PKI) | Provides favorable computational and communication efficiency | Overhead of handling private key generator (PKG) |
| Yao et al. [35] | 2015 | IoT | Attribute-Based Encryption (ABE), Elliptic Curve Cryptography (ECC), DH, Elliptic Curve Decisional Diffie-Hellman (ECDDHP) | Improved execution efficiency and reduced communication costs | Poor flexibility in revoking attributes and weak scalability |
| Xin M [36] | 2015 | IoT | MD5, ECC, and AES algorithms | Improved security and performance | Increases the complexity and execution speed |
| Prasetyo et al. [37] | 2014 | FPGA module/constrained devices | Blowfish algorithm | Better security and reduced total encryption time | Larger key length requires more resources and suffers from error propagation |
| Algorithm | Target Multimedia | Structure | Target Devices/Platform | Cipher Type | Key Size (bits) | No. of Rounds | Secure Against These Attacks |
|---|---|---|---|---|---|---|---|
| Total shuffling matrix (2006) [41] | Image | Permutation and XOR (Shuffling with a combination of two chaotic streams) | Internet | Not specified | 84 | Multiple iterations | Brute-force attacks |
| Total shuffling scheme {2011) [43] | Image | Permutation–diffusion | Internet | Block | 104 | 1 | Differential attacks Chosen- plaintext & Known-plaintext attacks |
| Hummingbird2 (2012) [44] | General purpose | Hybrid | Low-end controllers, RFID tags, wireless sensors, smart meters | Hybrid | 256 | 4 | Related-key attack Side-channel attacks |
| TWINE (2013) [45] | General purpose | Type-2 generalized Feistel network (GFN-2) | Micro-controller and high-end CPU | Block | 80/128 | 32 | Meet-in-the-Middle attacks |
| PRIDE(2014) [46] | General purpose | Substitution permutation network | 8-bit micro-controller | Block | 128 | 20 | Meet-in-the-Middle attacks, Differential attacks |
| Lightweight chaotic image encryption algorithm (2018) [47] | Image | Chaotic map | 32-bit microcontroller and real-time embedded applications | Block | 128 | Not specified | Not specified |
| One round encryption algorithm (2018) [48] | Image | Substitution permutation network | Multimedia IoT | Stream | 512 | 1 | Key-related, Chosen-plaintext, Known–plaintext attacks |
| Proposed EXPer (2019) | H.264/AVC videos | Bit-wise permutation and XOR over CABAC encoded syntax elements (Bins) | Multimedia IoMT | Stream | 128 | 1 | Perceptual, Key guessing, Known-plaintext, Differential, Statistical & Inference attacks |
| Sr. # | Videos (CIF) | File Size (MB) | Encryption Ratio (%) | |||||
|---|---|---|---|---|---|---|---|---|
| Only Motion Encrypted | Only Texture Encrypted | Combined (Motion and Texture) Encryption | ||||||
| CAVLC | CABAC | CAVLC | CABAC | CAVLC | CABAC | |||
| 1. | Bus | 21.7 | 0.55% | 0.56% | 23.42% | 10.72% | 23.97% | 11.28% |
| 2. | Coastguard | 43.5 | 0.32% | 0.25% | 21.52% | 4.46% | 21.84% | 4.71% |
| 3. | Container | 43.5 | 0.07% | 0.32% | 6.94% | 10.10% | 7.01% | 10.42% |
| 4. | Crew | 43.5 | 0.45% | 0.07% | 12.57% | 3.17% | 13.01% | 3.24% |
| 5. | Flower | 36.3 | 0.56% | 0.45% | 28.71% | 7.57% | 29.27% | 8.02% |
| 6. | Football | 37.7 | 0.52% | 0.57% | 25.79% | 13.57% | 26.30% | 14.14% |
| 7. | Foreman | 43.5 | 0.30% | 0.52% | 11.61% | 11.30% | 11.92% | 11.82% |
| 8. | Hall | 36.3 | 0.10% | 0.30% | 11.11% | 5.05% | 11.21% | 5.35% |
| 9. | ICE | 34.8 | 0.34% | 0.10% | 6.92% | 4.11% | 7.26% | 4.21% |
| 10. | Mobile | 43.5 | 0.45% | 0.46% | 30.78% | 12.76% | 31.23% | 13.22% |
| Sr.# | Videos (CIF) | File Size (MB) | ESR (%) | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Only Motion | Only Texture | Only Delta QP | Both Motion and Delta QP | Both Texture and Delta QP | Both Motion and Texture | Motion, Texture and Delta QP | |||
| 1. | Bus | 21.7 | 0.56% | 10.72% | 0.06% | 0.62% | 10.78% | 11.28% | 11.34% |
| 2. | Coastguard | 43.5 | 0.25% | 4.46% | 0.04% | 0.29% | 4.50% | 4.71% | 4.75% |
| 3. | Container | 43.5 | 0.32% | 10.10% | 0.02% | 0.34% | 10.12% | 10.42% | 10.44% |
| 4. | Crew | 43.5 | 0.07% | 3.17% | 0.08% | 0.15% | 3.25% | 3.24% | 3.32% |
| 5. | Flower | 36.3 | 0.45% | 7.57% | 0.05% | 0.50% | 7.62% | 8.02% | 8.07% |
| 6. | Football | 37.7 | 0.57% | 13.57% | 0.10% | 0.67% | 13.67% | 14.14% | 14.24% |
| 7. | Foreman | 43.5 | 0.52% | 11.30% | 0.03% | 0.55% | 11.33% | 11.82% | 11.85% |
| 8. | Hall | 36.3 | 0.30% | 5.05% | 0.03% | 0.33% | 5.08% | 5.35% | 5.38% |
| 9. | ICE | 34.8 | 0.10% | 4.11% | 0.04% | 0.14% | 4.15% | 4.21% | 4.25% |
| 10 | Mobile | 43.5 | 0.46% | 12.76% | 0.04% | 0.50% | 12.80% | 13.22% | 13.26% |
| Sr. # | Video (CIF) | File Size (MB) | Encoding time with H.264/AVC Using CABAC (Compression Without Encryption) | Absolute Encryption Time by Applying SE on CABAC (s) | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Only Motion | Only Texture | Only Delta QP | Motion and Texture | Motion and Delta QP | Delta QP and Texture | Motion Texture and Delta QP | ||||
| 1. | Bus | 21.7 | 73.697 s | 1.896 | 1.044 | 1.195 | 1.249 | 0.342 | 1.433 | 2.431 |
| 2. | Coastguard | 43.5 | 133.828 s | 1.622 | 0.177 | 4.045 | 3.655 | 3.831 | 3.528 | 4.012 |
| 3. | Container | 43.5 | 116.386 s | 2.687 | 2.691 | 2.656 | 3.217 | 3.058 | 2.666 | 3.947 |
| 4. | Crew | 43.5 | 156.804 s | 1.601 | 1.803 | 4.151 | 2.928 | 3.373 | 3.079 | 4.512 |
| 5. | Flower | 36.3 | 107.977 s | 1.849 | 2.745 | 1.059 | 2.908 | 0.143 | 3.561 | 3.772 |
| 6. | Football | 37.7 | 143.975 s | 1.154 | 1.149 | 2.995 | 1.866 | 0.129 | 0.989 | 2.958 |
| 7. | Foreman | 43.5 | 134.769 s | 2.419 | 2.285 | 2.793 | 0.993 | 5.483 | 3.603 | 5.988 |
| 8. | Hall | 36.3 | 118.614 s | 1.198 | 3.267 | 3.554 | 3.141 | 3.611 | 3.25 | 3.984 |
| 9. | ICE | 34.8 | 105.232 s | 0.947 | 2.694 | 3.54 | 3.4 | 2.998 | 2.625 | 3.229 |
| 10. | Mobile | 43.5 | 129.394 s | 1.786 | 2.773 | 2.809 | 0.893 | 3.683 | 2.038 | 3.186 |
| Average absolute encryption time (s): | 1.715 | 2.062 | 2.879 | 2.226 | 2.639 | 2.677 | 3.801 | |||
| Test Videos | Average PSNR (dB) | Average Pixel Cross-Correlation | ||
|---|---|---|---|---|
| Compressed | Encrypted | Compressed | Encrypted | |
| Football | [Y:31.63,U:37.45,V:39.01] | [Y:10.56,U:18.97,V:19.25] | 0.9816 | 0.0471 |
| ICE | [Y:29.18,U:34.16,V:33.47] | [Y:6.27,U: 14.99,V:11.64] | 0.9991 | −0.0173 |
| Mobile | [Y:32.86,U:38.06,V:39.47] | [Y:6.00,U: 21.97,V:27.32] | 0.9923 | 0.0140 |
| Videos | QP | Encoded Without SE | SE with XOR | SE with AES-CFB | SE with EXPer | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Y | U | V | Y | U | V | Y | U | V | Y | U | V | ||
| Football | 12 | 43.9 | 46.71 | 47.65 | 9.72 | 13.08 | 20.92 | 9.52 | 18.25 | 21.13 | 9.53 | 19.25 | 22.13 |
| 24 | 37.03 | 41.55 | 42.76 | 8.67 | 13.28 | 20.75 | 10.04 | 18.06 | 19.36 | 10.16 | 19.06 | 20.36 | |
| 36 | 31.63 | 37.45 | 39.01 | 9.94 | 13.19 | 20.87 | 10.36 | 17.97 | 18.24 | 10.56 | 18.97 | 19.25 | |
| 48 | 28.72 | 34.99 | 37.1 | 10.63 | 12.94 | 21.07 | 11.31 | 17.38 | 16.9 | 11.51 | 18.4 | 17.96 | |
| Mobile | 12 | 42.72 | 45.18 | 44.96 | 7.05 | 13.26 | 13.95 | 6.07 | 12.47 | 10.46 | 6.00 | 13.47 | 11.46 |
| 24 | 34.69 | 38.46 | 38.03 | 7.09 | 13.2 | 14.04 | 6.06 | 13.18 | 10.79 | 6.19 | 14.18 | 11.79 | |
| 36 | 29.18 | 34.16 | 33.47 | 7.18 | 13.09 | 14.16 | 6.07 | 13.98 | 10.62 | 6.27 | 14.99 | 11.64 | |
| 48 | 24.96 | 31.89 | 31.01 | 7.54 | 14.83 | 13.97 | 7.05 | 15.3 | 11.83 | 7.08 | 16.35 | 12.84 | |
| ICE | 12 | 44.74 | 48.77 | 49.56 | 7.91 | 18.82 | 25.85 | 5.74 | 20.39 | 26.43 | 5.94 | 21.39 | 27.43 |
| 24 | 38.78 | 43.21 | 44.02 | 7.73 | 18.33 | 26.64 | 5.8 | 20.97 | 26.32 | 6 | 21.97 | 27.32 | |
| 36 | 32.86 | 38.06 | 39.47 | 7.93 | 18.74 | 27 | 6.01 | 21.98 | 23.75 | 6.07 | 22.98 | 24.77 | |
| 48 | 29.09 | 36.03 | 37.58 | 8.25 | 18.21 | 27.66 | 5.9 | 18.54 | 19.25 | 5.98 | 19.57 | 20.27 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shifa, A.; Asghar, M.N.; Noor, S.; Gohar, N.; Fleury, M. Lightweight Cipher for H.264 Videos in the Internet of Multimedia Things with Encryption Space Ratio Diagnostics. Sensors 2019, 19, 1228. https://doi.org/10.3390/s19051228
Shifa A, Asghar MN, Noor S, Gohar N, Fleury M. Lightweight Cipher for H.264 Videos in the Internet of Multimedia Things with Encryption Space Ratio Diagnostics. Sensors. 2019; 19(5):1228. https://doi.org/10.3390/s19051228
Chicago/Turabian StyleShifa, Amna, Mamoona Naveed Asghar, Salma Noor, Neelam Gohar, and Martin Fleury. 2019. "Lightweight Cipher for H.264 Videos in the Internet of Multimedia Things with Encryption Space Ratio Diagnostics" Sensors 19, no. 5: 1228. https://doi.org/10.3390/s19051228
APA StyleShifa, A., Asghar, M. N., Noor, S., Gohar, N., & Fleury, M. (2019). Lightweight Cipher for H.264 Videos in the Internet of Multimedia Things with Encryption Space Ratio Diagnostics. Sensors, 19(5), 1228. https://doi.org/10.3390/s19051228