An Internet of Things (IoT) Acceptance Model. Assessing Consumer’s Behavior toward IoT Products and Applications
Abstract
:1. Introduction
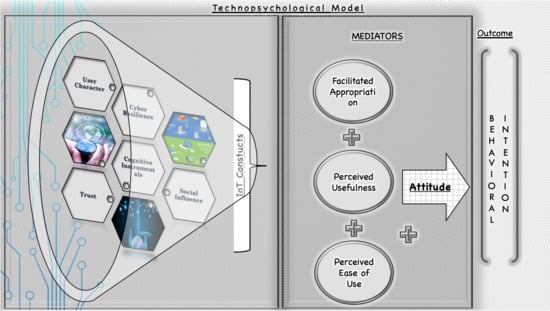
2. Conceptual Model and Hypothesis
2.1. Behavioral Intention
2.2. Attitude
2.3. Facilitated Appropriation
2.4. Perceived Usefulness
2.5. Trust
2.6. Social Influence
2.7. Cognitive Instrumentals
2.8. Cyber Resilience
2.9. User Character
3. Materials and Methods
3.1. Sample
3.2. Measurement Tool and Statistical Analysis
4. Results
5. Discussion of Findings
6. Conclusions
7. Implications for Theory and Practice
8. Limitations and Further Research
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A
List of Abbreviations
| IoT | Internet of Things | TRA | Theory of Reasoned Action |
| IIoT | industrial Internet of Things | TDB | Theory of Planned Behavior |
| TAM | technology acceptance model | BI | behavioral intention |
| UTAUT | Unified Theory of Acceptance and Use of Technology | PU | perceived usefulness |
| IS | information systems | PEOU | perceived ease of use |
| DTPB | Decomposed Theory of Planned Behavior | IDT | Innovation Diffusion Theory |
| ICT | information and communication technologies | TAM | technology acceptance model |
| IoTAM | Internet of Things technology acceptance model | FA | facilitated appropriation |
| LTO | long-term orientation | FL | flexibility |
| UC | user character | AT | attitude |
| CI | cognitive instrumentals | CR | cyber resilience |
| T | trust | SI” | social influence |
Appendix B
| Construct | Definition from Literature | N. of Items | References |
|---|---|---|---|
| User mode | Personality categories towards the acceptance of a new innovation | 2 | Created for the context (self-generated), based on Rogers [40] |
| Cyber-resilience | The ability to continuously deliver the intended outcome despite adverse cyber events | 10 | Created for the context: [75,76,77] |
| Cognitive instrumentals | The mental representations that people use to make a decision as to whether to adopt a technology or not. | 6 | [3,78] |
| Social influence | A psychological concept that acts as the balancing act between self-understand the interests of others | 8 | [3,78] |
| Trust | The individual’s belief in three main aspects, which are ability, integrity, and benevolence, which, in turn, makes customers feel the targeted technology is more dependable and trustworthy to use. | 5 | [79,80] |
| Long-term orientation | Long term orientation can be seen as valuing prospect of the future, and deeming actions unimportant for the short-term achievement. | 8 | [24,28,32,81] |
| Flexibility | The degree to which a user of a particular IoT system believes that he could efficiently use it in many diverse environments or for achieving different objectives beyond those initially specified in the requirements. | 5 | Self-generated—Scale developed using the definition of Economidis [82] |
| Perceived usefulness | The degree to which a user believes that using a particular IoT system he would achieve results and outcomes that he considers useful | 4 | [4,31] |
| Perceived ease of use | The degree to which a user believes that using a particular IoT system would be easy and without much effort to carry it, to install it, to initiate it, to understand its usage, to learn its usage, to remember its usage, as well as to actually access, use, control, maintain, pay and terminate it | 3 | [4,31] |
| Attitude | The degree to which users have positive feelings about using IoT services. | 3 | [83] |
| Behavioral intention | The strength of an individual’s desire to perform a behavior, which is intended to capture “acceptance-like” processes | 5 | [31,84] |
Appendix C
Appendix C.1. Operationalization of the Constructs
Appendix C.1.1. Cyber-Resilience
| CR1 | I am able to adapt to change. |
| CR2 | I can deal with whatever comes. |
| CR3 | I am in control of my life. |
| CR4 | I can cope with pressure and stress. It strengthens me. |
| CR5 | I prefer to take the lead in problem solving. |
| CR6 | I can achieve goals despite obstacles. |
| CR7 | I have pride in my achievements. |
| CR8 | I am not easily discouraged by failure. |
| CR9 | I think of myself as a strong person. |
| CR10 | I like challenges. |
Appendix C.1.2. Cognitive Instrumentals
| CR11 | IoT products and applications are very much applicable to my tasks. |
| CR12 | With IoT products and applications, meeting information needs is much more flexible and dynamic. |
| CR13 | IoT products and applications provide multi-access and searching capability. |
| CR14 | The output of IoT products and applications are error-free. |
| CR15 | I do not have difficulty attributing gains to the use of IoT products and applications. |
| CR16 | The usefulness and benefits of IoT products and applications are readily and easily discernible. |
Appendix C.1.3. Social Influence
| SI1 | People who are important to me would recommend using IoT products and applications. |
| SI2 | People who are important to me would find using IoT products and applications beneficial. |
| SI3 | People who influence my behavior think that I should use IoT products and applications. |
| SI4 | People in my environment who use IoT products and applications have a high profile. |
| SI5 | Using IoT products and applications is considered a status symbol. |
| SI6 | People in my environment who use IoT products and applications have more prestige than those who do not. |
| SI7 | I have seen people who are important to me using IoT products and applications. |
| SI8 | Previous knowledge informs my present appreciation of IoT products and applications in the connected world environment. |
Appendix C.1.4. Trust
| TR1 | IoT products and applications are trustworthy. |
| TR2 | IoT products and applications providers keep my best interests in mind. |
| TR3 | IoT products and applications provide reliable information. |
| TR4 | IoT products and applications providers keep promises and commitments. |
| TR5 | I feel assured that IoT products and applications providers protect me from problems I may encounter. |
| TR6 | IoT products and applications are trustworthy. |
Appendix C.1.5. Long-Term Orientation
| LTO1 | Respect for tradition is important to me. |
| LTO2 | I plan for the long term. |
| LTO3 | Family heritage is important to me. |
| LTO4 | I value a strong link to my past. |
| LTO5 | I work hard for success in the future. |
| LTO6 | I do not mind giving up today’s fun for success in the future. |
| LTO7 | Traditional values are important to me. |
| LTO8 | Persistence is important to me. |
Appendix C.1.6. Flexibility
| FL1 | I believe in IoT products and applications versatility. |
| FL2 | I believe in IoT products and applications portability. |
| FL3 | I believe in IoT products and applications transferability. |
| FL4 | I believe in IoT products and applications reusability. |
| FL5 | I believe in IoT products and applications modifiability. |
Appendix C.1.7. Perceived Usefulness
| PU1 | I think that IoT products and applications will improve my performance of daily activities and tasks. |
| PU2 | I think that IoT products and applications will make it easier for me to do my daily activities and tasks. |
| PU3 | I think that IoT products and applications will reduce the effort required in accomplishing my daily activities and tasks. |
| PU4 | I think that IoT products and applications will improve my quality of life. |
| PU5 | I think that IoT products and applications will improve my performance of daily activities and tasks. |
Appendix C.1.8. Perceived Ease of Use
| PEOU1 | Learning to use IoT products and applications is clear and easy for me. |
| PEOU2 | Using IoT products and applications does not require a lot of mental/physical effort. |
| PEOU3 | I think using IoT products and applications is easy and understandable. |
Appendix C.1.9. Attitude
| AT1 | I like using IoT products and applications. |
| AT2 | I feel good about using IoT products and applications. |
| AT3 | Overall, my attitude towards using IoT products and applications is favorable. |
Appendix C.1.10. Behavioral Intention
| BI1 | Given the chance, I intend to use IoT products and applications. |
| BI2 | I am willing to use IoT products and applications in the near future. |
| BI3 | I will frequently use IoT products and applications. |
| BI4 | I will recommend IoT products and applications to others. |
| BI5 | I will continue using IoT products and applications in the future. |
References
- Ashton, K. That ‘internet of things’ thing. Rfid J. 2009, 22, 97–114. [Google Scholar]
- Peoples, C.; Parr, G.; McClean, S.; Scotney, B.; Morrow, P. Performance evaluation of green data centre management supporting sustainable growth of the internet of things. Simul. Model. Pract. Theory 2013, 34, 221–242. [Google Scholar] [CrossRef]
- McLellan, C. Cyber Security in 2015: What to Expect; 2015; Available online: https://www.zdnet.com/article/cybersecurity-in-2015-what-to-expect/ (accessed on 3 November 2020).
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. Mis Q. 1989, 13, 319–340. [Google Scholar] [CrossRef] [Green Version]
- Bagozzi, R.P. The legacy of the technology acceptance model and a proposal for a paradigm shift. J. Assoc. Inf. Syst. 2007, 8, 244–254. [Google Scholar] [CrossRef]
- Benbasat, I.; Barki, H. Quo vadis, TAM? J. Assoc. Inf. Syst. 2007, 8, 211–218. [Google Scholar] [CrossRef] [Green Version]
- Moon, J.W.; Kim, Y.G. Extending the TAM for a World-Wide-Web context. Inf. Manag. 2001, 38, 217–230. [Google Scholar] [CrossRef]
- Mącik, R. The Adoption of the Internet of Things by Young Consumers–an Empirical Investigation. Econ. Environ. Stud. 2017, 17, 363–388. [Google Scholar] [CrossRef]
- Shang, W.; Yu, Y.; Droms, R.; Zhang, L. Challenges in IoT networking via TCP/IP architecture. In Technical Report NDN-0038; Available online: https://named-data.net/wp-content/uploads/2016/02/ndn-0038-1-challenges-iot.pdf (accessed on 29 October 2020).
- Hancke, G.P.; Markantonakis, K.; Mayes, K.E. Security challenges for user-oriented RFID applications within the “Internet of things”. J. Int. Technol. 2010, 11, 307–313. [Google Scholar]
- Medaglia, C.M.; Serbanati, A. An overview of privacy and security issues in the internet of things. In Internet Things; Springer: Berlin/Heidelberg, Germany, 2010; pp. 389–395. [Google Scholar]
- Mendez Mena, D.; Papapanagiotou, I.; Yang, B. Internet of things: Survey on security. Inf. Secur. J. A Glob. Perspect. 2018, 27, 162–182. [Google Scholar] [CrossRef]
- Uckelmann, D.; Harrison, M.; Michahelles, F. An architectural approach towards the future internet of things. In Archit. Internet Things; Springer: Berlin/Heidelberg, Germany, 2011; pp. 1–24. [Google Scholar]
- Guinard, D.; Trifa, V.; Mattern, F.; Wilde, E. From the internet of things to the web of things: Resource-oriented architecture and best practices. In Architecting the Internet of Things; Springer: Berlin/Heidelberg, Germany, 2011; pp. 97–129. [Google Scholar]
- Hong, H.G. Measurement Framework for the Acceptance of Internet of Things Product. Indian J. Sci. Technol. 2016, 9, 46. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. Siot: Giving a social structure to the internet of things. IEEE Commun. Lett. 2011, 15, 1193–1195. [Google Scholar] [CrossRef]
- Turhan, G. An assessment towards the acceptance of wearable technology to consumers in Turkey: The application to smart bra and t-shirt products. J. Text. Inst. 2013, 104, 375–395. [Google Scholar] [CrossRef]
- Istepanian, R.S.; Sungoor, A.; Faisal, A.; Philip, N. Internet of M-Health Things’m-IOT’. Available online: https://digital-library.theiet.org/content/conferences/10.1049/ic.2011.0036 (accessed on 29 October 2020).
- Gao, Y.; Li, H.; Luo, Y. An empirical study of wearable technology acceptance in healthcare. Ind. Manag. Data Syst. 2015, 115, 1704–1723. [Google Scholar] [CrossRef]
- Schlick, J.; Ferber, S.; Hupp, J. IoT applications–value creation for industry. In Aalborg; River Publisher: Gistrup, Denmark, 2013. [Google Scholar]
- Li, X.J.; Wang, D. Architecture and existing applications for internet of things. Appl. Mech. Mater. 2013, 347, 3317–3321. [Google Scholar] [CrossRef]
- Evanschitzky, H.; Iyer, G.R.; Pillai, K.G.; Kenning, P.; Schütte, R. Consumer trial, continuous use, and economic benefits of a retail service innovation: The case of the personal shopping assistant. J. Prod. Innov. Manag. 2015, 32, 459–475. [Google Scholar] [CrossRef] [Green Version]
- Tsai, M.-C.; Lee, W.; Wu, H.-C. Determinants of RFID adoption intention: Evidence from Taiwanese retail chains. Inf. Manag. 2010, 47, 255–261. [Google Scholar] [CrossRef]
- Prayoga, T.; Abraham, J. Technopsychology of IoT Optimization in the Business World. In The Internet of Things in the Modern Business Environment; IGI Global: Hershey, PA, USA, 2017; pp. 50–75. Available online: https://www.igi-global.com/chapter/technopsychology-of-iot-optimization-in-the-business-world/234934 (accessed on 29 October 2020).
- Rauschnabel, P.A.; Brem, A.; Vens, B.S. Who will buy smart glasses? Empirical results of two pre-market-entry studies on the role of personality in individual awareness and intended adoption of Google Glass wearables. Comput. Hum. Behav. 2015, 49, 635–647. [Google Scholar] [CrossRef]
- Revels, J.; Tojib, D.; Tsarenko, Y. Understanding consumer intention to use mobile services. Australas Mark. J. 2010, 18, 74–80. [Google Scholar] [CrossRef]
- Prayoga, T.; Abraham, J. Behavioral Intention to Use IoT Health Device: The Role of Perceived Usefulness, Facilitated Appropriation, Big Five Personality Traits, and Cultural Value Orientations. Int. J. Electr. Comput. Eng. 2016, 6, 1751–1765. [Google Scholar]
- Prayoga, T.; Abraham, J. Social-Psychological-Health Predictors of Fondness of Arkenstone among Indonesians. Abnorm. Behav. Psychol. 2016, 2, 1000116. [Google Scholar] [CrossRef] [Green Version]
- Gursoy, D.; Spangenberg, E.R.; Rutherford, D.G. The hedonic and utilitarian dimensions of attendees’ attitudes toward festivals. J. Hosp. Tour. Res. 2006, 30, 279–294. [Google Scholar] [CrossRef]
- Karahoca, A.; Karahoca, D.; Aksöz, M. Examining intention to adopt to internet of things in healthcare technology products. Kybernetes 2018, 47, 742–770. [Google Scholar] [CrossRef]
- Gao, L.; Bai, X. A unified perspective on the factors influencing consumer acceptance of internet of things technology. Asia Pac. J. Mark. Logist. 2014, 26, 211–231. [Google Scholar] [CrossRef]
- Bearden, W.O.; Money, R.B.; Nevins, J.L. A measure of long-term orientation: Development and validation. J. Acad. Mark. Sci. 2006, 34, 456–467. [Google Scholar] [CrossRef]
- Venkatesh, V.; Davis, F.D. A theoretical extension of the technology acceptance model: Four longitudinal field studies. Manag. Sci. 2000, 46, 186–204. [Google Scholar] [CrossRef] [Green Version]
- Ha, S.; Stoel, L. Consumer e-shopping acceptance: Antecedents in a technology acceptance model. J. Bus. Res. 2009, 62, 565–571. [Google Scholar] [CrossRef]
- Pavlou, P.A. Consumer acceptance of electronic commerce: Integrating trust and risk with the technology acceptance model. Int. J. Electron. Commer. 2003, 7, 101–134. [Google Scholar]
- Kalantari, M. Consumers’ adoption of wearable technologies: Literature review, synthesis, and future research agenda. Int. J. Technol. Mark. 2017, 12, 274–307. [Google Scholar] [CrossRef]
- Venkatesh, V.; Bala, H. Technology acceptance model 3 and a research agenda on interventions. Decis. Sci. 2008, 39, 273–315. [Google Scholar] [CrossRef] [Green Version]
- Björck, F.; Henkel, M.; Stirna, J.; Zdravkovic, J. Cyber resilience–fundamentals for a definition. In New Contributions in Information Systems and Technologies; Springer: Berlin/Heidelberg, Germany, 2015; pp. 311–316. [Google Scholar]
- Verdegem, P.; De Marez, L. Rethinking determinants of ICT acceptance: Towards an integrated and comprehensive overview. Technovation 2011, 31, 411–423. [Google Scholar] [CrossRef] [Green Version]
- Rogers, E.M. Diffusion of Innovation, 4th ed.; The Free: New York, NY, USA, 1995. [Google Scholar]
- Rogers, E.M. Diffusion of Innovations; Simon and Schuster: New York, NY, USA, 2010. [Google Scholar]
- Taylor, S.; Todd, P. Decomposition and crossover effects in the theory of planned behavior: A study of consumer adoption intentions. Int. J. Res. Mark. 1995, 12, 137–155. [Google Scholar] [CrossRef]
- Kittur, A.; Chi, E.H.; Suh, B. Crowdsourcing user studies with Mechanical Turk. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Montreal, QC, Canada, 25–30 April 2018; ACM: New York, NY, USA, 2018; pp. 453–456. [Google Scholar]
- Paolacci, G.; Chandler, J.; Ipeirotis, P.G. Running experiments on Amazon mechanical Turk. Judgm. Decis. Mak. 2010, 5, 411–419. [Google Scholar]
- Hirsh, J.B.; Kang, S.K.; Bodenhausen, G.V. Personalized persuasion: Tailoring persuasive appeals to recipients’ personality traits. Psychol. Sci. 2012, 23, 578–581. [Google Scholar] [CrossRef]
- Jia, Y.; Xu, B.; Karanam, Y.; Voida, S. Personality-targeted gamification: A survey study on personality traits and motivational affordances. In Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems, San Jose, CA, USA, 7–12 May 2016; ACM: New York, NY, USA; pp. 2001–2013. [Google Scholar]
- Buhrmester, M.; Kwang, T.; Gosling, S.D. Amazon’s Mechanical Turk: A new source of inexpensive, yet high-quality, data? Perspect. Psychol. Sci. 2011, 6, 3–5. [Google Scholar] [CrossRef]
- Bentley, F.R.; Daskalova, N.; White, B. Comparing the reliability of Amazon Mechanical Turk and Survey Monkey to traditional market research surveys. In Proceedings of the 2017 CHI Conference Extended Abstracts on Human Factors in Computing Systems, Denver, CO, USA, 6–11 May 2017; ACM: New York, NY, USA, 2017; pp. 1092–1099. [Google Scholar]
- Palan, S.; Schitter, C. Prolific. ac—A subject pool for online experiments. J. Behav. Exp. Financ. 2018, 17, 22–27. [Google Scholar] [CrossRef]
- Mellis, A.M.; Bickel, W.K. Mechanical Turk data collection in addiction research: Utility, concerns and best practices. Addiction 2020, 115, 1960–1968. [Google Scholar] [CrossRef]
- Coppock, A.; McClellan, O.A. Validating the demographic, political, psychological, and experimental results obtained from a new source of online survey respondents. Res. Politics 2019, 6, 1. [Google Scholar] [CrossRef]
- Acquisti, A.; Grossklags, J. Privacy and rationality in individual decision making. IEEE Secur. Priv. 2005, 3, 26–33. [Google Scholar] [CrossRef]
- Kline, R.B. Principles and Practices of Structural Equation Modeling; Guilford Press: New York, NY, USA, 2005. [Google Scholar]
- McDonald, R.P.; Ho, M.H.R. Principles and practice in reporting structural equation analyses. Psychol. Methods 2002, 7, 64. [Google Scholar] [CrossRef]
- Kim, S.B.; Sun, K.A.; Kim, D.Y. The influence of consumer value-based factors on attitude-behavioral intention in social commerce: The differences between high-and low-technology experience groups. J. Travel Tour. Mark. 2013, 30, 108–125. [Google Scholar] [CrossRef]
- Goode, J. Mind the gap: The digital dimension of college access. J. High. Educ. 2010, 81, 583–618. [Google Scholar] [CrossRef]
- Porter, C.E.; Donthu, N. Using the technology acceptance model to explain how attitudes determine Internet usage: The role of perceived access barriers and demographics. J. Bus. Res. 2006, 59, 999–1007. [Google Scholar] [CrossRef]
- Wixom, B.H.; Todd, P.A. A theoretical integration of user satisfaction and technology acceptance. Inf. Syst. Res. 2005, 16, 85–102. [Google Scholar] [CrossRef]
- Thatcher, J.B.; McKnight, D.H.; Baker, E.W.; Arsal, R.E.; Roberts, N.H. The role of trust in postadoption IT exploration: An empirical examination of knowledge management systems. IEEE Trans. Eng. Manag. 2011, 58, 56–70. [Google Scholar] [CrossRef]
- Yang, H.; Yu, J.; Zo, H.; Choi, M. User acceptance of wearable devices: An extended perspective of perceived value. Telemat. Inform. 2016, 33, 256–269. [Google Scholar] [CrossRef]
- Wu, L.H.; Wu, L.C.; Chang, S.C. Exploring consumers’ intention to accept smartwatch. Comput. Hum. Behav. 2016, 64, 383–392. [Google Scholar] [CrossRef]
- Amin, M.; Rezaei, S.; Abolghasemi, M. User satisfaction with mobile websites: The impact of perceived usefulness (PU), perceived ease of use (PEOU) and trust. Nankai Bus. Rev. Int. 2014, 5, 258–274. [Google Scholar] [CrossRef]
- Yang, K.C.C. Exploring factors affecting the adoption of mobile commerce in Singapore. Telemat. Inform. 2005, 22, 257–277. [Google Scholar] [CrossRef]
- Rouibah, K.; Abbas, H.; Rouibah, S. Factors affecting camera mobile phone adoption before e-shopping in the Arab world. Technol. Soc. 2011, 33, 271–283. [Google Scholar] [CrossRef]
- Morosan, C. Theoretical and empirical considerations of guests’ perceptions of biometric systems in hotels. J. Hosp. Tour. Res. 2012, 36, 52–84. [Google Scholar] [CrossRef]
- Fliegel Frederick, C.; Kivlin Joseph, E. Attributes of innovations as factors in diffusion. Am. J. Sociol. 1966, 72, 235–248. [Google Scholar] [CrossRef]
- Ostlund Lyman, E. Perceived innovation attributes as predictors of innovativeness. J. Consum. Res. 1974, 1, 23–29. [Google Scholar] [CrossRef]
- Szajna, B. Empirical evaluation of the revised technology acceptance model. Manag. Sci. 1996, 42, 85–92. [Google Scholar] [CrossRef]
- Tornatzky, L.G.; Klein, K.J. Innovation characteristics and innovation adoption-implementation: A meta-analysis of findings. IEEE Trans. Eng. Manag. 1982, 1, 28–45. [Google Scholar] [CrossRef]
- Heidenreich, S.; Kraemer, T.; Handrich, M. Satisfied and unwilling: Exploring cognitive and situational resistance to innovations. J. Bus. Res. 2016, 69, 2440–2447. [Google Scholar] [CrossRef]
- Laukkanen, T. Consumer adoption versus rejection decisions in seemingly similar service innovations: The case of the Internet and mobile banking. J. Bus. Res. 2016, 69, 2432–2439. [Google Scholar] [CrossRef]
- Abuarqoub, A.; Abusaimeh, H.; Hammoudeh, M.; Uliyan, D.; Abu-Hashem, M.A.; Murad, S.; Al-Fayez, F. A survey on internet of things enabled smart campus applications. In Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19–20 July 2017; pp. 1–7. [Google Scholar]
- Kwon, M.; Saluja, G.; Adaval, R. Who said what: The effects of cultural mindsets on perceptions of endorser–message relatedness. J. Consum. Psychol. 2015, 25, 389–403. [Google Scholar] [CrossRef]
- Faraji-Rad, A.; Melumad, S.; Johar, G.V. Consumer desire for control as a barrier to new product adoption. J. Consum. Psychol. 2017, 27, 347–354. [Google Scholar] [CrossRef]
- Campbell-Sills, L.; Stein, M.B. Psychometric analysis and refinement of the Connor–Davidson resilience scale (CD-RISC): Validation of a 10-item measure of resilience. J. Trauma. Stress Off. Publ. Int. Soc. Trauma. Stress Stud. 2007, 20, 1019–1028. [Google Scholar] [CrossRef]
- Connor, K.M.; Davidson, J.R. Development of a new resilience scale: The Connor-Davidson resilience scale (CD-RISC). Depress. Anxiety 2003, 18, 76–82. [Google Scholar] [CrossRef]
- Hua, J.; Chen, Y.; Luo, X.R. Are we ready for cyberterrorist attacks?—Examining the role of individual resilience. Inf. Manag. 2018, 55, 928–938. [Google Scholar] [CrossRef]
- Izuagbe, R.; Popoola, S.O. Social influence and cognitive instrumental factors as facilitators of perceived usefulness of electronic resources among library personnel in private universities in South-west, Nigeria. Libr. Rev. 2017, 66, 679–694. [Google Scholar] [CrossRef] [Green Version]
- Alalwan, A.A.; Baabdullah, A.M.; Rana, N.P.; Tamilmani, K.; Dwivedi, Y.K. Examining adoption of mobile internet in Saudi Arabia: Extending TAM with perceived enjoyment, innovativeness and trust. Technol. Soc. 2018, 55, 100–110. [Google Scholar] [CrossRef]
- Gefen, D.; Karahanna, E.; Straub, D.W. Trust and TAM in online shopping: An integrated model. Mis Q. 2003, 27, 51–90. [Google Scholar] [CrossRef]
- Sharma, P. Measuring personal cultural orientations: Scale development and validation. J. Acad. Mark. Sci. 2010, 38, 787–806. [Google Scholar] [CrossRef]
- Economides, A.A. User Perceptions of Internet of Things (IoT) Systems. In Proceedings of the International Conference on E-Business and Telecommunications, Lisbon, Portugal, 26–28 July 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 3–20. [Google Scholar]
- Hsu, C.L.; Lin, J.C.C. An empirical examination of consumer adoption of Internet of Things services: Network externalities and concern for information privacy perspectives. Comput. Hum. Behav. 2016, 62, 516–527. [Google Scholar] [CrossRef]
- Venkatesh, V. Determinants of perceived ease of use: Integrating control, intrinsic motivation, and emotion into the technology acceptance model. Inf. Syst. Res. 2000, 11, 342–365. [Google Scholar] [CrossRef] [Green Version]


| Hypotheses | Connection | Description |
|---|---|---|
| H1 | AT+BI | Attitude toward IoT products and applications usage is positively associated with consumers’ behavioral intention to use them. |
| H2 | PU+AT | Perceived Usefulness is positively associated with consumers’ attitude towards IoT products and applications |
| H3 | PEOU+AT | Perceived Ease of Use is positively associated with consumers’ attitude towards IoT products and applications |
| H4 | FA+PU | A consumer’s facilitated Appropriation can predict his/her Perceived Usefulness towards IoT products and applications. |
| H5 | PEOU+PU | There is a positive relationship between PEOU and PU in the context of IoT. |
| H6 | T+PU | Trust will positively influence perceived usefulness related to IoT products and applications |
| H7 | T+PEOU | Trust will positively influence perceived ease of use related to IoT products and applications. |
| H8 | SI+PU | Social influence positively influences perceived usefulness of IoT products and applications |
| H9 | SI+PEOU | Social influence positively influences perceived ease of use of IoT products and applications |
| H10 | CI+PU | Cognitive Instrumentals positively influence perceived usefulness of IoT products and applications |
| H11 | CR+FA | Cyber-resilience is positively associated to facilitated appropriation. |
| H12 | UC+FA | Consumers with higher user character mode rate will exhibit higher facilitated appropriation. |
| Variable | Frequency | % |
|---|---|---|
| Gender | ||
| Male | 385 | 47.4 |
| Female | 427 | 52.6 |
| Age | ||
| 20 to 35 years | 452 | 55.7 |
| 36 to 51 years | 360 | 44.3 |
| User Mode | ||
| Consumer-first mode | 401 | 49.4 |
| Carry-over effect mode | 411 | 50.6 |
| Education | ||
| High school | 152 | 18.6 |
| Technical College | 98 | 12.1 |
| University | 384 | 47.3 |
| Postgraduate | 178 | 22.0 |
| Occupation | ||
| Employee | 257 | 31.6 |
| Merchant | 146 | 18.0 |
| Housekeeper | 28 | 3.4 |
| Student | 212 | 26.1 |
| Other | 169 | 20.9 |
| Variable | Min | Max | Mean | SD | Kurtosis | Skewness | Cronbach Alpha | ||
|---|---|---|---|---|---|---|---|---|---|
| Cyber-resilience | 10 | 70 | 58.02 | 5.948 | −1.137 | 0.087 | 1.997 | 0.204 | 0.846 |
| Cognitive instrumentals | 6 | 42 | 31.57 | 5.054 | −0.436 | 0.087 | 0.349 | 0.204 | 0.837 |
| Long-term orientation | 8 | 56 | 38.27 | 5.764 | −0.341 | 0.087 | −0.572 | 0.204 | 0.871 |
| Flexibility | 5 | 35 | 23.12 | 4.546 | −0.796 | 0.087 | 0.746 | 0.204 | 0.915 |
| Trust | 5 | 35 | 21.57 | 4.208 | −0.391 | 0.087 | 0.724 | 0.204 | 0.894 |
| Social influence | 8 | 56 | 41.05 | 5.567 | −0.468 | 0.087 | 0.486 | 0.204 | 0.952 |
| Perceived ease of use | 3 | 21 | 17.93 | 3.218 | −0.694 | 0.087 | 0.782 | 0.204 | 0.914 |
| Perceived usefulness | 4 | 28 | 19.81 | 3.957 | −0.504 | 0.087 | 0.297 | 0.204 | 0.831 |
| Attitude | 3 | 21 | 17.82 | 3.168 | −0.911 | 0.087 | 1.146 | 0.204 | 0.927 |
| Behavioral intention | 5 | 35 | 31.42 | 4.347 | −0.964 | 0.087 | 1.108 | 0.204 | 0.931 |
| Age | UM | CR | CI | LTO | Fl | TR | SI | PEOU | PU | AT | BI | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Age | 1 | |||||||||||
| UM | −0.129 ** | 1 | ||||||||||
| CR | 0.164 ** | −0.034 | 1 | |||||||||
| CI | 0.061 | 0.037 | 0.597 ** | 1 | ||||||||
| LTO | 0.028 | −0.387 ** | 0.131 ** | 0.146 ** | 1 | |||||||
| FL | 0.062 | −0.143 ** | 0.382 ** | 0.793 ** | 0.503 ** | 1 | ||||||
| TR | −0.046 | 0.049 | 0.483 ** | 0.498 ** | 0.163 ** | 0.271 ** | 1 | |||||
| SI | 0.052 | 0.024 | 0.501 ** | 0.397 ** | 0.152 ** | 0.337 ** | 0.603 ** | 1 | ||||
| PEOU | 0.012 | 0.032 | 0.504 ** | 0.396 ** | 0.148 ** | 0.372 ** | 0.764 ** | 0.637 ** | 1 | |||
| PU | −0.019 | 0.037 | 0.513 ** | 0.522 ** | 0.156 ** | 0.401 ** | 0.701 ** | 0.723 ** | 0.761 ** | 1 | ||
| AT | 0.107 ** | 0.006 | 0.497 ** | 0.407 ** | 0.147 ** | 0.384 ** | 0.682 ** | 0.712 ** | 0.752 ** | 0.728 ** | 1 | |
| BI | 0.162 ** | 0.028 | 0.517 ** | 0.381 ** | 0.128 ** | 0.371 ** | 0.598 ** | 0.625 ** | 0.717 ** | 0.701 ** | 0.829 ** | 1 |
| Endogenous | Exogenous | SE | Beta | t | p | SMC |
|---|---|---|---|---|---|---|
| Facilitated Appropriation | User character | 1.000 (0.342) | 0.398 | 2.924 | 0.003 | 0.196 |
| Cyber resilience | 0.113 (0.038) | 0.128 | 2.973 | <0.001 | ||
| PEOU | Social influence | 0.358 (0.042) | 0.349 | 8.523 | <0.001 | 0.648 |
| Trust | 0.411 (0.021) | 0.483 | 19.571 | <0.001 | ||
| PU | Cognitive instrumentals | 0.165 (0.037) | 0.161 | 4.459 | <0.001 | 0.661 |
| Social influence | 0.305 (0.039) | 0.302 | 7.820 | <0.001 | ||
| PEOU | 0.392 (0.039) | 0.462 | 10.051 | <0.001 | ||
| Facilitated Appropriation | 0.061 (0.031) | 0.058 | 1.967 | 0.09 | ||
| Trust | 0.098 (0.035) | 0.136 | 2.800 | 0.001 | ||
| Attitude | PU | 0.283 (0.028) | 0.458 | 10.107 | <0.001 | 0.698 |
| PEOU | 0.301 (0.019) | 0.496 | 15.842 | <0.001 | ||
| Behavioral intention | Attitude | 0.921 (0.025) | 0.927 | 36.840 | <0.001 | 0.812 |
| Endogenous | Exogenous | Standardized Direct Effect | p | Standardized Indirect Effect | p | Standardized Total Effect | p |
|---|---|---|---|---|---|---|---|
| FA | UC | 0.398 | 0.01 | - | 0.398 | 0.01 | |
| CR | 0.128 | 0.007 | - | 0.128 | 0.007 | ||
| PEOU | TR | 0.483 | 0.008 | - | 0.483 | 0.008 | |
| SI | 0.349 | 0.01 | - | 0.349 | 0.01 | ||
| PU | TR | 0.136 | 0.008 | 0.247 | 0.03 | 0.383 | 0.008 |
| SI | 0.302 | 0.008 | 0.141 | 0.008 | 0.443 | 0.008 | |
| CI | 0.161 | 0.01 | - | 0.161 | 0.01 | ||
| FA | 0.058 | 0.05 | - | 0.058 | 0.05 | ||
| PEOU | 0.462 | 0.007 | - | 0.462 | 0.007 | ||
| CR | - | 0.009 | 0.03 | 0.009 | 0.03 | ||
| UC | - | 0.021 | 0.04 | 0.021 | 0.04 | ||
| AT | PEOU | 0.496 | 0.03 | 0.201 | 0.004 | 0.697 | 0.03 |
| PU | 0.458 | 0.005 | - | 0.458 | 0.005 | ||
| SI | - | 0.324 | 0.02 | 0.324 | 0.02 | ||
| TR | - | 0.436 | 0.01 | 0.436 | 0.01 | ||
| CI | - | 0.071 | 0.004 | 0.071 | 0.004 | ||
| CR | - | 0.003 | 0.02 | 0.003 | 0.02 | ||
| UC | - | 0.006 | 0.05 | 0.006 | 0.05 | ||
| FA | - | 0.023 | 0.04 | 0.023 | 0.04 | ||
| BI | AT | 0.927 | 0.01 | - | 0.927 | 0.01 | |
| SI | - | 0.349 | 0.02 | 0.349 | 0.02 | ||
| TR | - | 0.362 | 0.01 | 0.362 | 0.01 | ||
| CI | - | 0.072 | 0.005 | 0.072 | 0.005 | ||
| CR | - | 0.005 | 0.03 | 0.005 | 0.03 | ||
| UC | - | 0.009 | 0.04 | 0.009 | 0.04 | ||
| FA | - | 0.025 | 0.06 | 0.025 | 0.06 | ||
| PEOU | - | 0.592 | 0.01 | 0.592 | 0.01 | ||
| PU | - | 0.407 | 0.004 | 0.407 | 0.004 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tsourela, M.; Nerantzaki, D.-M. An Internet of Things (IoT) Acceptance Model. Assessing Consumer’s Behavior toward IoT Products and Applications. Future Internet 2020, 12, 191. https://doi.org/10.3390/fi12110191
Tsourela M, Nerantzaki D-M. An Internet of Things (IoT) Acceptance Model. Assessing Consumer’s Behavior toward IoT Products and Applications. Future Internet. 2020; 12(11):191. https://doi.org/10.3390/fi12110191
Chicago/Turabian StyleTsourela, Maria, and Dafni-Maria Nerantzaki. 2020. "An Internet of Things (IoT) Acceptance Model. Assessing Consumer’s Behavior toward IoT Products and Applications" Future Internet 12, no. 11: 191. https://doi.org/10.3390/fi12110191
APA StyleTsourela, M., & Nerantzaki, D. -M. (2020). An Internet of Things (IoT) Acceptance Model. Assessing Consumer’s Behavior toward IoT Products and Applications. Future Internet, 12(11), 191. https://doi.org/10.3390/fi12110191