N-STGAT: Spatio-Temporal Graph Neural Network Based Network Intrusion Detection for Near-Earth Remote Sensing
Abstract
:1. Introduction
- Expanding the latest IoT network intrusion detection dataset by incorporating the status of the node, which better reflects the situation of the near-Earth remote sensing system and enables better evaluation of the proposed method.
- This article proposes for the first time the application of spatio-temporal graph neural networks to network intrusion detection in near-Earth remote sensing systems and further improves the method to better align with the characteristics of near-Earth remote sensing systems, providing a new solution for network intrusion detection.
- The proposed method is validated by the extended dataset and compared with some recently effective IoT network intrusion detection methods. The results show that the proposed method outperforms other methods.
2. Related Work
3. Background
3.1. GNN and LSTM
3.1.1. GNN
3.1.2. LSTM
3.1.3. STGNN
3.2. Datasets
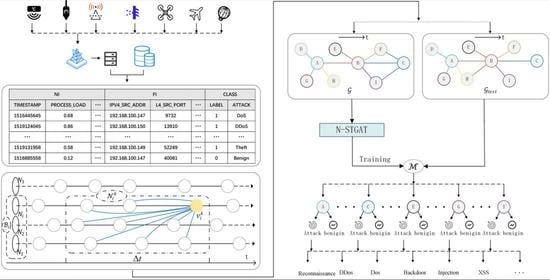
4. Method Description
4.1. Problem Definition
4.2. Pre-Processing and Graph Construction
4.3. N-STGAT Training
| Algorithm 1: Pseudocode of the N-STGAT algorithm. | |
| Input: ) node features ; GAT weight matrices ; non-linearity ; LSTM weight matrices ; LSTM initialization | |
| Output: node features ; | |
| 1 | for = 1 to do |
| 2 | for to length() do |
| 3 | for to length() do |
| 4 | |
| 5 | end |
| 6 | |
| 7 | |
| 8 | |
| 9 | |
| 10 | |
| 11 | |
| 12 | |
| 13 | |
| 14 | end |
| 15 | end |
| 16 | //FC is fully connected layers |
4.4. N-STGAT Detection
5. Experimental Evaluation
5.1. Evaluation Metrics
5.2. Result
5.2.1. Loss and Accuracy Comparison in Training
5.2.2. Binary Classification Results
5.2.3. Multiclass Classification Results
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wang, D.; Zhang, J.; Du, B.; Xia, G.-S.; Tao, D. An Empirical Study of Remote Sensing Pretraining. IEEE Trans. Geosci. Remote. Sens. 2023, 61, 5608020. [Google Scholar] [CrossRef]
- Goswami, A.; Sharma, D.; Mathuku, H.; Gangadharan, S.M.P.; Yadav, C.S.; Sahu, S.K.; Pradhan, M.K.; Singh, J.; Imran, H. Change Detection in Remote Sensing Image Data Comparing Algebraic and Machine Learning Methods. Electronics 2022, 11, 431. [Google Scholar] [CrossRef]
- Sun, X.; Zhang, Y.; Shi, K.; Zhang, Y.; Li, N.; Wang, W.; Huang, X.; Qin, B. Monitoring water quality using proximal remote sensing technology. Sci. Total. Environ. 2022, 803, 149805. [Google Scholar] [CrossRef]
- Chen, J.; Chen, S.; Fu, R.; Li, D.; Jiang, H.; Wang, C.; Peng, Y.; Jia, K.; Hicks, B.J. Remote Sensing Big Data for Water Environment Monitoring: Current Status, Challenges, and Future Prospects. Earth’s Future 2022, 10, e2021EF002289. [Google Scholar] [CrossRef]
- Li, J.; Hong, D.; Gao, L.; Yao, J.; Zheng, K.; Zhang, B.; Chanussot, J. Deep learning in multimodal remote sensing data fusion: A comprehensive review. Int. J. Appl. Earth Obs. Geoinf. 2022, 112, 102926. [Google Scholar] [CrossRef]
- Lo, W.W.; Layeghy, S.; Sarhan, M.; Gallagher, M.; Portmann, M. E-GraphSAGE: A Graph Neural Network based Intrusion Detection System for IoT. In Proceedings of the NOMS 2022-2022 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 25–29 April 2022; pp. 1–9. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Shu, L.; Friha, O.; Yang, X. Cyber Security Intrusion Detection for Agriculture 4.0: Machine Learning-Based Solutions, Datasets, and Future Directions. IEEE/CAA J. Autom. Sin. 2022, 9, 407–436. [Google Scholar] [CrossRef]
- He, H.; Sun, X.; He, H.; Zhao, G.; He, L.; Ren, J. A Novel Multimodal-Sequential Approach Based on Multi-View Features for Network Intrusion Detection. IEEE Access 2019, 7, 183207–183221. [Google Scholar] [CrossRef]
- Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. An Anomaly Mitigation Framework for IoT Using Fog Computing. Electronics 2020, 9, 1565. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Moustafa, N.; Portmann, M. NetFlow Datasets for Machine Learning-Based Network Intrusion Detection Systems. In Big Data Technologies and Applications; Deze, Z., Huang, H., Hou, R., Rho, S., Chilamkurti, N., Eds.; BDTA WiCON 2020; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Springer: Cham, Switzerland, 2020; Volume 371. [Google Scholar] [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R. An ensemble learning and fog-cloud architecture-driven cyber-attack detection framework for IoMT networks. Comput. Commun. 2020, 166, 110–124. [Google Scholar] [CrossRef]
- Churcher, A.; Ullah, R.; Ahmad, J.; Rehman, S.U.; Masood, F.; Gogate, M.; Alqahtani, F.; Nour, B.; Buchanan, W.J. An Experimental Analysis of Attack Classification Using Machine Learning in IoT Networks. Sensors 2021, 21, 446. [Google Scholar] [CrossRef]
- Cheng, Q.; Wu, C.; Zhou, S. Discovering Attack Scenarios via Intrusion Alert Correlation Using Graph Convolutional Networks. IEEE Commun. Lett. 2021, 25, 1564–1567. [Google Scholar] [CrossRef]
- Caville, E.; Lo, W.W.; Layeghy, S.; Portmann, M. Anomal-E: A self-supervised network intrusion detection system based on graph neural networks. Knowl.-Based Syst. 2022, 258, 110030. [Google Scholar] [CrossRef]
- Huang, Y.; Bi, H.; Li, Z.; Mao, T.; Wang, Z. Stgat: Modeling Spatial-Temporal Interactions for Human Trajectory Prediction. In Proceedings of the IEEE/CVF International Conference on Computer Vision, Seoul, Korea, 27 October 2019–2 November 2019; pp. 6272–6281. Available online: https://openaccess.thecvf.com/content_ICCV_2019/html/Huang_STGAT_Modeling_Spatial-Temporal_Interactions_for_Human_Trajectory_Prediction_ICCV_2019_paper.html (accessed on 4 August 2022).
- Casas, P.; Mazel, J.; Owezarski, P. Unsupervised Network Intrusion Detection Systems: Detecting the Unknown without Knowledge. Comput. Commun. 2012, 35, 772–783. [Google Scholar] [CrossRef] [Green Version]
- Friha, O.; Ferrag, M.A.; Shu, L.; Maglaras, L.; Choo, K.-K.R.; Nafaa, M. FELIDS: Federated learning-based intrusion detection system for agricultural Internet of Things. J. Parallel Distrib. Comput. 2022, 165, 17–31. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Shu, L.; Djallel, H.; Choo, K.-K.R. Deep Learning-Based Intrusion Detection for Distributed Denial of Service Attack in Agriculture 4.0. Electronics 2021, 10, 1257. [Google Scholar] [CrossRef]
- Raghuvanshi, A.; Singh, U.K.; Sajja, G.S.; Pallathadka, H.; Asenso, E.; Kamal, M.; Singh, A.; Phasinam, K. Intrusion Detection Using Machine Learning for Risk Mitigation in IoT-Enabled Smart Irrigation in Smart Farming. J. Food Qual. 2022, 2022, 1–8. [Google Scholar] [CrossRef]
- Vormayr, G.; Zseby, T.; Fabini, J. Botnet Communication Patterns. IEEE Commun. Surv. Tutor. 2017, 19, 2768–2796. [Google Scholar] [CrossRef]
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Surveying Port Scans and Their Detection Methodologies. Comput. J. 2011, 54, 1565–1581. [Google Scholar] [CrossRef]
- Kambourakis, G.; Moschos, T.; Geneiatakis, D.; Gritzalis, S. Detecting DNS Amplification Attacks. In Critical Information Infrastructures Security; Lopez, J., Hämmerli, B.M., Eds.; CRITIS 2007; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2007; Volume 5141. [Google Scholar] [CrossRef]
- Leichtnam, L.; Totel, E.; Prigent, N.; Mé, L. Sec2graph: Network Attack Detection Based on Novelty Detection on Graph Structured Data. In Detection of Intrusions and Malware, and Vulnerability Assessment, Proceedings of the DIMVA 2020, 24–26 June 2020, Lisbon, Portugal; Lecture Notes in Computer Science; Maurice, C., Bilge, L., Stringhini, G., Neves, N., Eds.; Springer: Cham, Switzerland, 2020; Volume 12223. [Google Scholar] [CrossRef]
- Ali, A.; Zhu, Y.; Zakarya, M. Exploiting dynamic spatio-temporal correlations for citywide traffic flow prediction using attention based neural networks. Inf. Sci. 2021, 577, 852–870. [Google Scholar] [CrossRef]
- Ali, A.; Zhu, Y.; Zakarya, M. Exploiting dynamic spatio-temporal graph convolutional neural networks for citywide traffic flows prediction. Neural Netw. 2021, 145, 233–247. [Google Scholar] [CrossRef]
- Hao, J.; Liu, J.; Pereira, E.; Liu, R.; Zhang, J.; Zhang, Y.; Yan, K.; Gong, Y.; Zheng, J.; Zhang, J.; et al. Uncertainty-guided graph attention network for parapneumonic effusion diagnosis. Med. Image Anal. 2021, 75, 102217. [Google Scholar] [CrossRef]
- Jiang, W. Graph-based deep learning for communication networks: A survey. Comput. Commun. 2021, 185, 40–54. [Google Scholar] [CrossRef]
- Jiang, W.; Luo, J. Graph neural network for traffic forecasting: A survey. Expert Syst. Appl. 2022, 207, 117921. [Google Scholar] [CrossRef]
- He, X.; Deng, K.; Wang, X.; Li, Y.; Zhang, Y.; Wang, M. LightGCN: Simplifying and Powering Graph Convolution Network for Recommendation. In Proceedings of the 43rd International ACM SIGIR Conference on Research and Development in Information Retrieval (SIGIR ‘20), New York, NY, USA, 25 July 2020; pp. 639–648. [Google Scholar] [CrossRef]
- Sun, P.; Guo, Z.; Wang, J.; Li, J.; Lan, J.; Hu, Y. Deepweave: Accelerating Job Completion Time with Deep Reinforcement Learning-Based Coflow Scheduling. In Proceedings of the International Joint Conferences on Artificial Intelligence, Virtual, 19–26 August 2021; pp. 3314–3320. Available online: https://www.ijcai.org/proceedings/2020/0458.pdf (accessed on 4 October 2022).
- Xu, K.; Hu, W.; Leskovec, J.; Jegelka, S. How powerful are graph neural networks? arXiv 2018, arXiv:1810.00826. [Google Scholar] [CrossRef]
- Cai, H.; Zheng, V.W.; Chang, K.C.-C. A Comprehensive Survey of Graph Embedding: Problems, Techniques, and Applications. IEEE Trans. Knowl. Data Eng. 2018, 30, 1616–1637. [Google Scholar] [CrossRef] [Green Version]
- Veličković, P.; Cucurull, G.; Casanova, A.; Romero, A.; Liò, P.; Bengio, Y. Graph attention networks. arXiv 2017, arXiv:1710.10903. [Google Scholar] [CrossRef]
- Kipf, T.N.; Welling, M. Semi-supervised classification with graph convolutional networks. arXiv 2016, arXiv:1609.02907. [Google Scholar] [CrossRef]
- Hamilton, W.; Ying, Z.; Leskovec, J. Inductive Representation Learning on Large Graphs. In Proceedings of the Advances in Neural Information Processing Systems, Long Beach, CA, USA, 4 December 2017; Volume 30. Available online: https://proceedings.neurips.cc/paper_files/paper/2017/file/5dd9db5e033da9c6fb5ba83c7a7ebea9-Paper.pdf (accessed on 7 August 2022).
- Smagulova, K.; James, A.P. A survey on LSTM memristive neural network architectures and applications. Eur. Phys. J. Spéc. Topics 2019, 228, 2313–2324. [Google Scholar] [CrossRef]
- Yu, B.; Yin, H.; Zhu, Z. Spatio-temporal graph convolutional networks: A deep learning framework for traffic forecasting. arXiv 2017, arXiv:1709.04875. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Portmann, M. Towards a Standard Feature Set for Network Intrusion Detection System Datasets. Mob. Netw. Appl. 2021, 27, 357–370. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Futur. Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef] [Green Version]
- Moustafa, N. A new distributed architecture for evaluating AI-based security systems at the edge: Network TON_IoT datasets. Sustain. Cities Soc. 2021, 72, 102994. [Google Scholar] [CrossRef]












| Dataset | Release Year | No. Classes | No. Features | No. Data | Benign Ratio |
|---|---|---|---|---|---|
| NF-BoT-IoT-v2 | 2021 | 5 | 43 | 37,763,497 | 0.0 to 10.0 |
| NF-ToN-IoT-v2 | 2021 | 10 | 43 | 16,940,496 | 3.6 to 6.4 |
| Feature | Description |
|---|---|
| TIMESTAMP | The timestamp when the data flow is sent. |
| PROCESS_LOAD | 1 min load average |
| PROCESS_ID | Idle CPU percentage. |
| PROCESS_HI | Hard interrupt CPU percentage |
| PROCESS_US | User-space CPU percentage, |
| PROCESS_SY | Kernel-space CPU percentage |
| MEMORY_USED | Memory used ratio |
| MEMORY_BUFFER | Memory cache ratio |
| MEMORY_NETWORK | Memory used by network module ratio |
| NET_PAKAGES | Number of packets sent |
| NET_ BANDWIDTH_OUT | Network egress bandwidth |
| NET_TCP_CONNECTIONS | Number of TCP connections |
| DISK_READ | Disk read speed |
| DISK_WRITE | Disk write speed |
| NI | FI | CLASS | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| TIMESTAMP | PROCESS_LOAD | PROCESS_ID | … | IPV4_SRC_ADDR | L4_SRC_PORT | ... | L7_PROTO | IN_BYTES | IN_PKTS | ... | DNS_TTL_ANSWER | FCMRC | LABEL | ATTACK |
| 1556149715 | 0.63 | 0.32 | ... | 192.168.100.148 | 59,826 | ... | 188 | 56 | 2 | ... | 0 | 0 | 1 | DDos |
| 1554143041 | 0.72 | 0.49 | ... | 192.168.100.150 | 61,662 | ... | 7 | 280 | 2 | ... | 0 | 0 | 1 | DoS |
| 1556286369 | 0.16 | 0.76 | ... | 192.168.100.147 | 47,080 | ... | 1 | 13 | 1 | ... | 0 | 331 | 1 | RN |
| 1556200073 | 0.21 | 0.84 | ... | 192.168.100.3 | 43,362 | ... | 0 | 60 | 1 | ... | 0 | 0 | 1 | Theft |
| 1554130829 | 0.14 | 0.89 | ... | 192.168.100.3 | 80 | ... | 7 | 44 | 1 | ... | 0 | 0 | 0 | Benign |
| NI | FI | CLASS | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| TIMESTAMP | PROCESS_LOAD | PROCESS_ID | ... | IPV4_SRC_ADDR | L4_SRC_PORT | ... | L7_PROTO | IN_BYTES | IN_PKTS | ... | DNS_TTL_ANSWER | FCMRC | LABEL | ATTACK |
| 1556292791 | 0.11 | 0.86 | ... | 192.168.1.193 | 49,228 | ... | 0 | 1600 | 40 | ... | 86,400 | 0 | 0 | Benign |
| 1555849991 | 0.43 | 0.36 | ... | 192.168.1.31 | 59,779 | ... | 0 | 50 | 1 | ... | 0 | 0 | 1 | ddos |
| 1555589471 | 0.54 | 0.53 | ... | 192.168.1.31 | 37,514 | ... | 0 | 70 | 1 | ... | 23 | 0 | 1 | dos |
| 1554955914 | 0.32 | 0.71 | ... | 192.168.1.31 | 34,165 | ... | 0 | 54 | 1 | ... | 0 | 0 | 1 | injection |
| 1555366378 | 0.16 | 0.68 | ... | 192.168.1.31 | 60,540 | ... | 0 | 50 | 1 | ... | 0 | 0 | 1 | mitm |
| 1555365718 | 0.19 | 0.76 | ... | 192.168.1.31 | 60,918 | ... | 7 | 84 | 2 | ... | 0 | 0 | 1 | password |
| 1555371958 | 0.22 | 0.64 | ... | 192.168.1.33 | 4444 | ... | 0 | 28,296 | 133 | ... | 0 | 0 | 1 | rn |
| 1555284910 | 0.22 | 0.43 | ... | 192.168.1.32 | 41,244 | ... | 3 | 44 | 1 | ... | 0 | 0 | 1 | scanning |
| 1555003930 | 0.24 | 0.91 | ... | 192.168.1.32 | 46,187 | ... | 0 | 70 | 1 | ... | 57 | 0 | 1 | xss |
| 1555029142 | 0.38 | 0.42 | ... | 192.168.1.79 | 60,766 | ... | 0 | 63 | 1 | ... | 0 | 0 | 1 | backdoor |
| Hyperparameter | Values |
|---|---|
| No. layers | 1 |
| No. hidden | 256 |
| No. k | 1 |
| Learning rate | 2 × 10−3 |
| Activation func. | ReLU |
| Loss func. | Cross-entropy |
| Optimizer | Adam |
| Metric | Definition |
|---|---|
| Recall | |
| Precision | |
| F1-Score | |
| Accuracy |
| DataSet | Algorithm | Recall | Precision | F1-Score | Accuracy |
|---|---|---|---|---|---|
| NF-BoT-IoT-v2 | SVM | 0.8485 | 0.9367 | 0.8904 | 0.8299 |
| Random Forest | 0.8212 | 0.9151 | 0.8656 | 0.7923 | |
| GAT | 0.9013 | 0.9633 | 0.9313 | 0.8917 | |
| E-GraphSAG | 0.9615 | 0.9825 | 0.9719 | 0.9547 | |
| Anomal-E | 0.9412 | 0.9859 | 0.963 | 0.9412 | |
| N-STGAT | 0.9812 | 0.9927 | 0.9869 | 0.9788 | |
| NF-ToN-IoT-v2 | SVM | 0.7689 | 0.8991 | 0.8289 | 0.7415 |
| Random Forest | 0.7368 | 0.9307 | 0.8224 | 0.7409 | |
| GAT | 0.8746 | 0.9724 | 0.9209 | 0.8776 | |
| E-GraphSAG | 0.9578 | 0.9867 | 0.972 | 0.9551 | |
| Anomal-E | 0.9461 | 0.9846 | 0.965 | 0.9441 | |
| N-STGAT | 0.9755 | 0.9827 | 0.9791 | 0.9661 |
| DataSet | Algorithm | Weighted Recall | Weighted F1-Score |
|---|---|---|---|
| NF-BoT-IoT-v2 | SVM | 0.7101 | 0.6948 |
| Random Forest | 0.7719 | 0.7492 | |
| GAT | 0.7227 | 0.7021 | |
| E-GraphSAG | 0.8797 | 0.8461 | |
| Anomal-E | 0.865 | 0.8016 | |
| N-STGAT | 0.915 | 0.9264 | |
| NF-ToN-IoT-v2 | SVM | 0.7195 | 0.7514 |
| Random Forest | 0.7786 | 0.7364 | |
| GAT | 0.7699 | 0.8163 | |
| E-GraphSAG | 0.8533 | 0.8204 | |
| Anomal-E | 0.8659 | 0.8425 | |
| N-STGAT | 0.9064 | 0.9142 |
| Dataset | Algorithm | Per Class Recall | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| NF-BoT-IoT-v2 | Benign | RN | DDos | Dos | Theft | ||||||
| SVM | 0.7154 | 0.6148 | 0.8412 | 0.8649 | 0.7225 | ||||||
| Random Forest | 0.8205 | 0.8415 | 0.7451 | 0.5748 | 0.8148 | ||||||
| GAT | 0.8952 | 0.6715 | 0.8216 | 0.7469 | 0.7149 | ||||||
| E-GraphSAG | 0.8756 | 0.8912 | 0.82465 | 0.9051 | 0.8694 | ||||||
| Anomal-E | 0.9049 | 0.8648 | 0.7903 | 0.9417 | 0.8795 | ||||||
| N-STGAT | 0.9506 | 0.9241 | 0.8786 | 0.9207 | 0.9513 | ||||||
| NF-ToN-IoT-v2 | Benign | RN | DDos | Dos | Backdoor | Injection | MITM | Password | Scanning | XSS | |
| SVM | 0.7147 | 0.5792 | 0.8106 | 0.7129 | 0.6129 | 0.6792 | 0.8059 | 0.7138 | 0.846 | 0.7816 | |
| Random Forest | 0.8703 | 0.7126 | 0.6109 | 0.5498 | 0.7159 | 0.8619 | 0.7469 | 0.8759 | 0.7482 | 0.6874 | |
| GAT | 0.8761 | 0.7454 | 0.8418 | 0.7923 | 0.8219 | 0.7619 | 0.8242 | 0.6958 | 0.8716 | 0.9015 | |
| E-GraphSAG | 0.9418 | 0.8819 | 0.9112 | 0.8109 | 0.8846 | 0.7805 | 0.8759 | 0.8904 | 0.8513 | 0.8927 | |
| Anomal-E | 0.8042 | 0.9229 | 0.8496 | 0.8217 | 0.9036 | 0.9158 | 0.8176 | 0.9013 | 0.7219 | 0.9014 | |
| N-STGAT | 0.9712 | 0.9013 | 0.9013 | 0.8735 | 0.9213 | 0.9016 | 0.9254 | 0.9186 | 0.8619 | 0.9208 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Li, J.; Zhao, W.; Han, Z.; Zhao, H.; Wang, L.; He, X. N-STGAT: Spatio-Temporal Graph Neural Network Based Network Intrusion Detection for Near-Earth Remote Sensing. Remote Sens. 2023, 15, 3611. https://doi.org/10.3390/rs15143611
Wang Y, Li J, Zhao W, Han Z, Zhao H, Wang L, He X. N-STGAT: Spatio-Temporal Graph Neural Network Based Network Intrusion Detection for Near-Earth Remote Sensing. Remote Sensing. 2023; 15(14):3611. https://doi.org/10.3390/rs15143611
Chicago/Turabian StyleWang, Yalu, Jie Li, Wei Zhao, Zhijie Han, Hang Zhao, Lei Wang, and Xin He. 2023. "N-STGAT: Spatio-Temporal Graph Neural Network Based Network Intrusion Detection for Near-Earth Remote Sensing" Remote Sensing 15, no. 14: 3611. https://doi.org/10.3390/rs15143611
APA StyleWang, Y., Li, J., Zhao, W., Han, Z., Zhao, H., Wang, L., & He, X. (2023). N-STGAT: Spatio-Temporal Graph Neural Network Based Network Intrusion Detection for Near-Earth Remote Sensing. Remote Sensing, 15(14), 3611. https://doi.org/10.3390/rs15143611