Design and Implementation of Automated Steganography Image-Detection System for the KakaoTalk Instant Messenger
Abstract
:1. Introduction
- We proposed an automated detection model that can automatically collect and detect steganography image files shared in SNS IMs.
- We show experimental results that validate our proposed automated detection system work successfully according to our design purpose.
2. Background and Related Works
2.1. Overveiw of Traditional Botnets
2.2. Steganography-Based Botnet (Stego-Botnet)
2.3. Existing Studies Related to Stego-Botnets
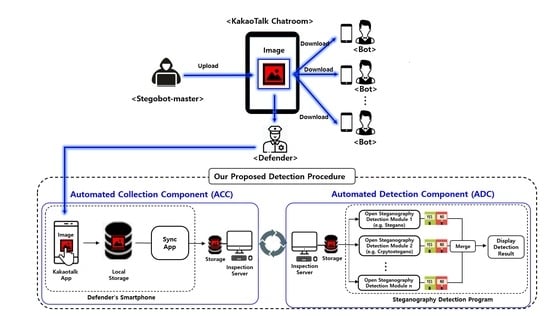
3. Design of Automated Steganography Image-Detection System
3.1. Automated Detection Procedure of Steganography Images Shared in a KakaoTalk Chatroom
3.2. Design of Our Proposed System Model
4. Implementation and Experiments
4.1. Implementation
4.1.1. Automated Collection Component (ACC)
4.1.2. Automated Detection Component (ADC)
4.2. Experiments
4.2.1. Experimental Purpose and Methods
4.2.2. Experimental Results and Analysis
5. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
References
- Zhou, Y.; Jiang, X. Dissecting Android Malware: Characterization and Evolution. In Proceedings of the 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 24–25 May 2012; pp. 95–109. [Google Scholar]
- Geol, D.; Jain, A. Mobile phishing attacks and defence mechanisms: State of art and open research challenges. Comput. Secur. 2017, 73, 10. [Google Scholar] [CrossRef]
- La Polla, M.; Martinelli, F.; Sgandurra, D. A Survey on Security for Mobile Devices. IEEE Commun. Surv. Tutor. 2012, 15, 446–471. [Google Scholar] [CrossRef] [Green Version]
- Yin, T.; Zhang, Y.; Li, S. Dr-SNbot: A social network-based botnet with strong destroy-resistance. In Proceedings of the 9th IEEE International Conference on Networking, Architecture, and Storage (NAS), Tianjin, China, 6–8 August 2014; pp. 191–199. [Google Scholar]
- Zhang, J.; Zhang, R.; Zhang, Y.; Yan, G. The rise of social botnets: Attacks and countermeasures. IEEE Trans. Dependable Secur. Comput. 2016, 15, 1068–1082. [Google Scholar] [CrossRef] [Green Version]
- Yang, C.; Harkreader, R.; Gu, G. Die free or live hard? Empirical evaluation and new design for fighting evolving twitter spammers. In Proceedings of the International Workshop on Recent Advances in Intrusion Detection, Menlo Park, CA, USA, 20–21 September 2011; pp. 318–337. [Google Scholar]
- Wu, D.; Fang, B.; Yin, J.; Zhang, F.; Cui, X. Slbot: A serverless botnet based on service flux. In Proceedings of the 2018 IEEE Third International Conference on Data Science in Cyberspace (DSC), Guangzhou, China, 18–21 June 2018; pp. 181–188. [Google Scholar]
- WeChat. Available online: https://www.wechat.com (accessed on 27 September 2020).
- KakaoTalk. Available online: https://www.kakaocorp.com/service/KakaoTalk?lang=en (accessed on 21 September 2020).
- Mokel, T.; Eloff, J.; Olivier, M. An Overview of Image Steganography. In Proceedings of the ISSA 2005 New Knowledge Today Conference, Sandton, South Africa, 29 June–1 July 2005. [Google Scholar]
- Kanzariya, K.; Nimavat, V. Comparison of Various Images Steganography Techniques. Int. J. Comput. Sci. Manag. Res. 2013, 2, 1213–1217. [Google Scholar]
- Sharda, S.; Budhiraja, S. Image Steganography: A Review. Int. J. Emerg. Technol. Adv. Eng. 2013, 3, 707–710. [Google Scholar]
- Singh, S.; Singh, A. A Review on the Various Recent Steganography Techniques. Int. J. Comput. Sci. Netw. 2013, 2, 142–156. [Google Scholar]
- Makkar, I.; Troia, F.; Visaggio, C.; Austin, T.; Stamp, M. Sociobot: A twitter-based botnet. Int. J. Comput. Sci. Netw. 2017, 12, 1–12. [Google Scholar] [CrossRef]
- Faghani, M.; Nguyen, U. Socellbot: A new botnet design to infect smartphones via online social networking. In Proceedings of the IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), Montreal, QC, Canada, 29 April–2 May 2012; pp. 1–5. [Google Scholar]
- Steghide. Available online: http://steghide.sourceforge.net (accessed on 27 September 2020).
- Openstego. Available online: https://www.openstego.com (accessed on 27 September 2020).
- Gaonkar, S.; Dessai, N.; Costa, J.; Borkar, A.; Aswale, S.; Shetgaonkar, P. A Survey on Botnet Detection Techniques. In Proceedings of the 2020 International Conference on Emerging Trends in Information Technology and Engineering (ic-ETITE), Vellore, India, 24–25 February 2020; pp. 1–6. [Google Scholar]
- Sonawane, S. A Survey of Botnet and Botnet Detection Methods. Int. J. Eng. Res. Technol. 2018, 7, 57–61. [Google Scholar]
- FORTINET Threat Landscape Report Q4 2018. Available online: https://www.fortinet.com/content/dam/fortinet/assets/threat-reports/threat-report-q4-2018.pdf (accessed on 24 October 2020).
- Stegano·PyPI. Available online: https://pypi.org/project/stegano (accessed on 21 September 2020).
- Cryptosteganography·PyPI. Available online: https://pypi.org/project/cryptosteganography (accessed on 30 November 2020).
- Khattak, S.; Ramay, N.; Khan, K.; Syed, A.; Khayam, S. A Taxonomy of Botnet Behavior, Detection, and Defense. IEEE Commun. Surv. Tutor. 2014, 16, 898–924. [Google Scholar] [CrossRef]
- Vormayr, G.; Ramay, K.; Fabini, J. Botnet communication patterns. IEEE Commun. Surv. Tutor. 2017, 19, 2768–2796. [Google Scholar] [CrossRef]
- Imam, M.; Nir, M.; Matrawy, A. A Survey on Botnet Architectures, Detection and Defences. Int. J. Netw. Secur. 2014, 17, 264–281. [Google Scholar]
- Acarali, D.; Rajarajan, M.; Komninos, N.; Herwono, I. Survey of approaches and features for the identification of HTTP-based botnet traffic. J. Netw. Comput. Appl. 2016, 76, 1–15. [Google Scholar] [CrossRef] [Green Version]
- Eslahi, M.; Rohmad, S.; Nilsaz, H.; Naseri, M.; Tahir, N.; Hashim, H. Periodicity Classification of HTTP Traffic to Detect HTTP Botnets. In Proceedings of the IEEE Symposium on Computer Applications & Industrial Electronics (ISCAIE), Langkawi, Malaysia, 12–14 April 2015. [Google Scholar]
- Zeidanloo, H.; Manaf, A.; Vahdani, P.; Tabatabaei, F.; Zamani, M. Botnet detection based on traffic monitoring. In Proceedings of the IEEE International Conference on Networking and Information Technology, Manila, Philippines, 11–12 June 2010. [Google Scholar]
- Yang, Z.; Wang, B. A Feature Extraction Method for P2P Botnet Detection Using Graphic Symmetry Concept. Symmetry 2019, 11, 326. [Google Scholar] [CrossRef] [Green Version]
- Saad, S.; Traore, I.; Ghorbani, A.; Sayed, B.; Zhao, D.; Lu, W.; Felix, J.; Hakimian, P. Detecting P2P Botnets through Network Behavior Analysis and Machine Learning. In Proceedings of the IEEE Ninth Annual International Conference on Privacy, Security and Trust, Montreal, QC, Canada, 19–21 July 2011; pp. 174–180. [Google Scholar]
- Ferrara, E.; Varol, O.; Davis, C.; Menczer, F.; Flammini, A. The rise of social bots. Commun. ACM 2014, 59, 96–104. [Google Scholar] [CrossRef] [Green Version]
- Nagaraja, S.; Houmansdr, A.; Piyawongwisai, P.; Singh, V.; Agarwal, P.; Borisov, N. Stegobot: A covert social network botnet. In Proceedings of the Information Hiding Conference, Prague, Czech Republic, 18–20 May 2011; pp. 299–313. [Google Scholar]
- Yuk, S.; Cho, Y. A Study on Steganography-based Botnet C & C Covert Communication Model using Thumbnail Images in SNS Instant Messengers. In Proceedings of the KSII Spring/Fall Conference, Jeju, Korea, 22–23 May 2020; pp. 197–198. [Google Scholar]
- Kwak, M.; Cho, Y. Video Steganography-based Botnet Communication in Telegram Messenger. In Proceedings of the 15th Asia Pacific International Conference on Information Science and Technology (APIC-IST 2020), Seoul, Korea, 5–7 July 2020; pp. 50–73. [Google Scholar]
- Kartaltepe, E.; Morales, J.; Xu, S.; Sandhu, R. Social Network-Based Botnet Command-and-Control: Emerging Threats and Countermeasures. In Applied Cryptography and Network Security, Lecture Notes in Computer Science; Zhou, J., Yung, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6123, pp. 511–528. [Google Scholar]
- Hiney, J.; Dakve, T.; Szczypiorski, K.; Gaj, K. Using Facebook for Image Steganography. In Proceedings of the 10th International Conference on Availability, Reliability and Security, Toulouse, France, 24–27 August 2015; pp. 442–447. [Google Scholar]
- Jeon, J.; Cho, Y. Construction and Performance Analysis of Image Steganography-Based Botnet in KakaoTalk Openchat. Computers 2019, 8, 61. [Google Scholar] [CrossRef] [Green Version]
- Number of Global Monthly Active Kakaotalk Users from 1st Quarter 2013 to 2nd Quarter 2020. Available online: https://www.statista.com/statistics/278846/kakaotalk-monthly-active-users-mau (accessed on 28 September 2020).
- Gasimov, V.; Mustafayeva, E. Implementing Covert Channels to Transfer Hidden Information over WhatsApp on Mobile Phones. Am. J. Eng. Appl. Sci. 2020, 6, 32–35. [Google Scholar]
- Konstantinos, K.; Ergina, K.; Giorgos, P. A Review of Image Steganalysis Techniques for Digital Forensics. J. Inf. Secur. Appl. 2018, 40, 217–235. [Google Scholar]
- Natarajan, V.; Sheen, S.; Anitha, R. Detection of StegoBot: A covert social network botnet. In Proceedings of the 1st ACM International Conference on Security of Internet of Things, Kollam, India, 17–19 August 2012; pp. 36–41. [Google Scholar]
- Natarajan, V.; Sheen, S.; Anitha, R. Multilevel Analysis to Detect Covert Social Botnet in Multimedia Social Networks. Comput. J. 2015, 58, 679–687. [Google Scholar] [CrossRef]
- Foldersync. Available online: https://www.tacit.dk (accessed on 21 September 2020).
- Xiao Steganography. Available online: https://xiao-steganography.en.softonic.com (accessed on 27 September 2020).
- Stealthencrypt. Available online: http://www.stealthencrypt.com/ (accessed on 27 September 2020).
- The Top 29 Steganography Open Source Projects. Available online: https://awesomeopensource.com/projects/steganography (accessed on 4 December 2020).
- Barghuthi, A.; Nedaa, B.; Huwida, S. Social networks IM forensics: Encryption analysis. J. Commun. 2013, 8, 708–715. [Google Scholar] [CrossRef]
- Python. Available online: https://www.python.org (accessed on 21 September 2020).












| Element | Value |
|---|---|
| Defender’s smartphone | Samsung Galaxy S10 5G (Android 10 Q); ACC is installed |
| Inspection server | Lenovo Ideapad L3 (Window 10); ADC is installed |
| Synchronize application | Folder sync ver. 3.0.16 (Freeware) [43] |
| KakaoTalk version | 8.9.6 (released on 24 July 2020) [9] |
| Steganography detection module | Stegano ver. 0.9.8 (coded by Python) [21] Cryptosteganography ver 0.8.3 (coded by Python) [22] |
| Sample cover images | 40 (20 PNG, 20 BMP/Resolution: 640 × 420 pixel) |
| Stego-images | 8 (4 PNG (by Stego), 4 BMP (by Cryptosteganography)) |
| Collection Interval | Num. of Collected/ Inspected Files | Inspection Result | |||
|---|---|---|---|---|---|
| Time Taken to Inspect (Total/Avg. Per File) | Num. of Normal Images | Num. of Stego- Images | |||
| 1st (10:45~11:00) | 4/4 | 7″/1.75″ | 2 | 2 | |
| 2nd (11:00~11:15) | 6/10 | 29″/2.9″ | 8 | 2 | |
| 3rd (11:15~11:30) | 3/13 | 38″/2.92″ | 10 | 3 | |
| 4th (11:30~11:45) | 7/20 | 56″/2.8″ | 16 | 4 | |
| 5th (11:45~12:00) | 6/26 | 1′17″/2.96″ | 21 | 5 | |
| 6th (12:00~12:15) | 4/30 | 1′25″/2.83″ | 24 | 6 | |
| 7th (12:15~12:30) | 2/32 | 1′30″/2.81″ | 26 | 6 | |
| 8th (12:30~12:45) | 8/40 | 1′56″/2.9″ | 32 | 8 | |
| Total | 2 h (00:30~02:30) | 40 | 8′18″/2.73″ | 32 | 8 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, J.; Cho, Y. Design and Implementation of Automated Steganography Image-Detection System for the KakaoTalk Instant Messenger. Computers 2020, 9, 103. https://doi.org/10.3390/computers9040103
Park J, Cho Y. Design and Implementation of Automated Steganography Image-Detection System for the KakaoTalk Instant Messenger. Computers. 2020; 9(4):103. https://doi.org/10.3390/computers9040103
Chicago/Turabian StylePark, Jun, and Youngho Cho. 2020. "Design and Implementation of Automated Steganography Image-Detection System for the KakaoTalk Instant Messenger" Computers 9, no. 4: 103. https://doi.org/10.3390/computers9040103
APA StylePark, J., & Cho, Y. (2020). Design and Implementation of Automated Steganography Image-Detection System for the KakaoTalk Instant Messenger. Computers, 9(4), 103. https://doi.org/10.3390/computers9040103