IT Risk Management: Towards a System for Enhancing Objectivity in Asset Valuation That Engenders a Security Culture
Abstract
:1. Introduction
2. Research Method
3. Literature, Regulations, and Standards
3.1. Concepts and Methods
3.2. Asset Valuation
3.3. Third-Party and Supply Chain Cybersecurity
3.4. Cyber Security Culture Framework and IT Governance
3.5. Regulations, Legislation, and International Standards
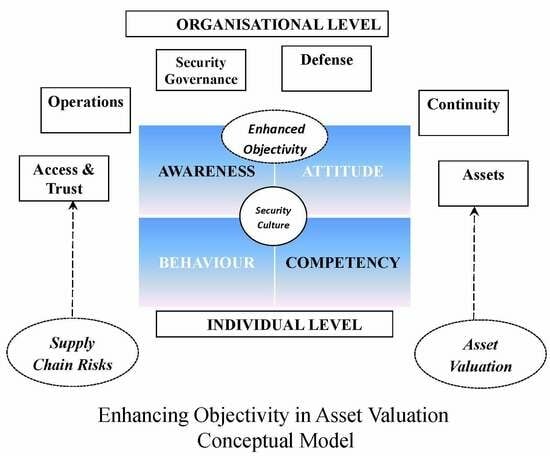
4. Conceptual Model: An Extended Cyber Security Culture Framework
5. Results: System Design and Operation
5.1. System Design
5.2. System Operation
6. Validation and Discussion
6.1. Validation Survey
6.2. Conceptual Model Review
6.3. Balancing Objectivity and Subjectivity
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Exemplar Questionnaire for Asset Valuation
| Survey Score | Asset Value |
|---|---|
| 25–50 | Critical |
| 50–75 | High |
| 75–125 | Medium |
| >125 | Low |
| Survey Score | Asset Owner’s Value |
|---|---|
| 8–16 | Good |
| 16–24 | Could be improved |
| 24–40 | Should be improved |
| >40 | Must be improved |
Appendix A.1. PART I: Asset Valuation: Organizational-Level Dimension in CSCF
- 1.
- Confidentiality: Potential damages that may occur if the most critical information processed by your asset group is disclosed or captured by unauthorised individuals:
- a)
- No damage occurs, the organization and related individuals continue their activities;
- b)
- Damages that may negatively affect the users of the asset occur.
- c)
- Damages that may negatively affect the department of the asset occur.
- d)
- Damages that may negatively affect the entire organization occur.
- e)
- Damages that may negatively affect the entire organization and its stakeholders occur.
- 2.
- Integrity: Potential damages that may occur if the content of the most critical information processed by your asset group is altered by unauthorised individuals:
- a)
- No damage occurs, the organization and related individuals continue their activities.
- b)
- Damages that may negatively affect the users of the asset occur.
- c)
- Damages that may negatively affect the department of the asset occur.
- d)
- Damages that may negatively affect the entire organization occur.
- e)
- Damages that may negatively affect the entire organization and its stakeholders occur.
- 3.
- Availability: What is the maximum duration of service downtime you can tolerate during peak usage periods for the services dependent on the assets in your group?
- a)
- More than 48 h.
- b)
- Between 24 and 48 h.
- c)
- Between 8 and 24 h.
- d)
- Between 4 and 8 h.
- e)
- Less than 1 h.
- 4.
- Answer questions for information asset categories such as people, buildings, machines, systems, applications, information, and infrastructure.
- A.
- Are there rules or guidelines (e.g., security policies, compliance requirements, operational guidelines) that help protect and manage the assets of our organization?
- a)
- Yes, comprehensive rules/guidelines.
- b)
- Yes, but they need improvement.
- c)
- Neutral.
- d)
- No, insufficient rules/guidelines.
- e)
- No rules/guidelines at all.
- B.
- How would you rate the economic value of the assets (for which you are responsible) to our organization’s operations (such as software, information, facilities)?
- a)
- Extremely valuable (purchase decision given by management board).
- b)
- Very valuable (purchase decision given by CIO).
- c)
- Moderately valuable (purchase decision given by department manager and IT manager).
- d)
- Slightly valuable (purchase decision given by department manager).
- e)
- Not valuable (purchase decision given by asset owner).
- C.
- How difficult is it to replace a specific IT asset in the event of malfunctions, security breaches, or other IT-related incidents? Please select the option that best describes your organization’s approach.
- a)
- International Procurement (greatest difficulty): Requires sourcing the replacement from international vendors, involving extended delivery times and potentially complex logistics.
- b)
- National Procurement: Involves obtaining the asset from vendors within the country but outside the local region, which can be time-consuming due to distance and shipping.
- c)
- Regional Sourcing: The asset is sourced from suppliers outside the city or local area, necessitating additional time for procurement due to regional distance.
- d)
- City-Wide Sourcing: Replacement can be found within the nearest big city but may require sourcing from specific vendors, offering a moderate level of difficulty and time commitment.
- e)
- Quick, Local Procurement (lowest difficulty): The asset can be easily and quickly replaced from local stores or supermarkets, ensuring immediate availability and minimal downtime.
- 5.
- Business continuity: how confident are you in the resilience of our critical assets to ensure smooth business operations in the event of unexpected disruptions?
- a)
- Very confident in the resilience and backup strategies of our critical assets.
- b)
- Somewhat confident; some assets are well-protected, but others need more robust plans.
- c)
- Neutral; unsure about the resilience levels of our assets.
- d)
- Somewhat unconfident; many assets lack sufficient protection or backup plans.
- e)
- Not confident at all; our critical assets are vulnerable to disruptions.
- 6.
- Crisis management: What measures are in place to protect our key assets, thereby safeguarding our reputation and maintaining the interests of our partners during unexpected events?
- a)
- Comprehensive crisis management plan.
- b)
- Regular communication with partners.
- c)
- Limited or no specific steps.
- d)
- Not sure.
- e)
- Nobody in the company knows.
- 7.
- Access: How well do you think we control who can access our resources and information?
- a)
- Very well (zero trust access management).
- b)
- Adequately (identity access management solution is used).
- c)
- Neutral (VLAN segmentation and we have a firewall).
- d)
- Inadequately (no network segmentation but we have a firewall).
- e)
- Poorly (we do not have a firewall).
- 8.
- Trust: How do we make sure that our interactions with outside parties like suppliers and customers are secure and trustworthy?
- a)
- SLA and regular audits and reviews.
- b)
- SLA.
- c)
- Basic security measures.
- d)
- Verbal confirmation.
- e)
- It does not exist.
- 9.
- Data security: How confident are you in the security of the data and systems in your area of responsibility, which are shared with our third-party vendors?
- a)
- Highly confident.
- b)
- Moderately confident.
- c)
- Neutral.
- d)
- Somewhat unconfident.
- e)
- Not confident at all
- 10.
- Operations: Do our daily operational practices incorporate measures to protect and secure our key assets?
- a)
- Always; asset security is a top priority in all our operations.
- b)
- Often; we regularly consider asset security in our operational decisions.
- c)
- Sometimes; asset security is considered, but not consistently.
- d)
- Rarely; asset security is seldom a focus in our daily operations.
- e)
- Never; we do not integrate asset security into our operational practices.
- 11.
- Asset security: Are there any areas in our daily operations where you think security of our assets could be improved?
- a)
- Yes, many areas.
- b)
- Yes, a few areas.
- c)
- Neutral.
- d)
- Not many areas.
- e)
- No, not at all.
- 12.
- Technology protection: Do you believe that our current technology infrastructure enhances the security of our assets?
- a)
- Strongly agree; our technology significantly enhances asset security.
- b)
- Agree; our technology generally supports asset security.
- c)
- Neutral; unsure about the impact of our technology on asset security.
- d)
- Disagree; our technology does little to improve asset security.
- e)
- Strongly disagree; our technology infrastructure weakens asset security.
- 13.
- Security procedures: Are you aware of the procedures to follow in the event of a security breach or incident involving our assets in your responsibility?
- a)
- Fully aware and trained.
- b)
- Somewhat aware.
- c)
- Neutral.
- d)
- Not very aware.
- e)
- Unaware.
- 14.
- Governance: How well do you think we plan and manage our efforts to keep our information assets safe?
- a)
- Very effectively.
- b)
- Effectively.
- c)
- Neutral.
- d)
- Ineffectively.
- e)
- Very ineffectively.
- 15.
- Evaluation: Do we have effective methods to evaluate the success of our asset security management?
- a)
- Yes, very comprehensive and effective evaluation methods.
- b)
- Yes, but our evaluation methods could be improved.
- c)
- Neutral; not sure about the effectiveness of our evaluation methods.
- d)
- No, our methods for evaluating asset security are not very effective.
- e)
- No, we lack any methods to evaluate asset security effectiveness.
- 16.
- Leadership: How visible and involved are our senior leaders in promoting cybersecurity practices for asset security?
- a)
- Highly visible and involved.
- b)
- Moderately visible and involved.
- c)
- Neutral.
- d)
- Seldom visible and involved.
- e)
- Not visible or involved at all.
- 17.
- Empowerment: Do you feel encouraged to provide feedback or suggestions on our cybersecurity policies and practices?
- a)
- Strongly encouraged.
- b)
- Encouraged.
- c)
- Neutral.
- d)
- Discouraged.
- e)
- Strongly discouraged.
Appendix A.2. PART II: Asset Owner’s Valuation: Individual-Level Dimension in CSCF
- 18.
- Attitude
- A.
- Do feel informed and involved in our organization’s cybersecurity policies and initiatives?
- a)
- Very informed and involved.
- b)
- Somewhat informed and involved.
- c)
- Neutral.
- d)
- Not informed or involved.
- e)
- Completely unaware and not involved at all.
- B.
- Do you think the training and resources provided by our organization make you feel prepared to handle cybersecurity challenges?
- a)
- Highly prepared.
- b)
- Reasonably prepared.
- c)
- Neutral.
- d)
- Unprepared.
- e)
- Completely unprepared.
- C.
- How responsible do you feel personally for maintaining cybersecurity in your daily tasks?
- a)
- Strongly feel responsible.
- b)
- Feel responsible.
- c)
- Neutral.
- d)
- Do not feel very responsible.
- e)
- Do not feel responsible at all.
- 19.
- Awareness
- A.
- How well do you think you know and understand the organization’s information security policies and procedures?
- a)
- Very well.
- b)
- Moderately well.
- c)
- Neutral.
- d)
- Not very well.
- e)
- Not at all.
- B.
- Are you aware of your specific roles and responsibilities in ensuring information security within the organization?
- a)
- Highly aware.
- b)
- Aware.
- c)
- Neutral.
- d)
- Not really aware.
- e)
- Totally unaware.
- 20.
- Behaviour
- A.
- How often do you see people following our security rules and guidelines in their daily work? (Are you aware of, and actively report, any security policy violations or suspicious activities? Have you noticed any instances where security rules were not followed?)
- a)
- Always.
- b)
- Often.
- c)
- Sometimes.
- d)
- Rarely.
- e)
- Not sure.
- B.
- Do you consistently adhere to the organization’s information security policies and procedures in your daily work?
- a)
- Always.
- b)
- Often.
- c)
- Sometimes.
- d)
- Rarely.
- e)
- Not sure.
- 21.
- Competency
- A.
- How confident are you in your ability to follow our security rules and guidelines? (Do you feel equipped with the necessary skills and knowledge to comply with our organization’s cybersecurity policies?)
- a)
- Very confident.
- b)
- Confident.
- c)
- Neutral.
- d)
- Not very confident.
- e)
- Not confident at all.
- B.
- Do you think your company provides enough training to help you understand and follow our security practices?
- a)
- Training is very good.
- b)
- Training is reasonable.
- c)
- Neutral.
- d)
- Training is not really good enough.
- e)
- Training is poor and not fit for purpose.
References
- Zwikael, O.; Ahn, M. The effectiveness of risk management: An analysis of project risk planning across industries and countries. Risk Anal. 2011, 31, 25–37. [Google Scholar] [CrossRef]
- Zayed, T.; Amer, M.; Pan, J. Assessing risk and uncertainty inherent in Chinese highway projects using AHP. Int. J. Proj. Manag. 2008, 26, 408–419. [Google Scholar] [CrossRef]
- Irizar, J.; Wynn, M. Development and Application of a New Maturity Model for Risk Management in the Automotive Industry. In Global Risk and Contingency Management Research in Times of Crisis; Vajjhala, N.R., Strang, K.D., Eds.; IGI Global: Hershey, PA, USA, 2022; pp. 29–52. [Google Scholar] [CrossRef]
- Carleton, J.; Krishnamoorthi, S. Digital Risk: The Security Challenge Beyond Your Perimeter; Frost & Sullivan White Paper; Frost & Sullivan: Santa Clara, CA, USA, 2019. [Google Scholar]
- Karlsson, F.; Hedström, K.; Goldkuhl, G. Practice-based discourse analysis of information security policies. Comput. Secur. 2017, 67, 267–279. [Google Scholar] [CrossRef]
- Awati, R. Segregation of Duties (SoD). 2023. Available online: https://www.techtarget.com/whatis/definition/segregation-of-duties-SoD (accessed on 8 August 2023).
- Irizar, J.; Wynn, M. Centricity in Project Risk Management: New Dimensions for Improved Practice. Int. J. Adv. Intell. Syst. 2015, 8, 209–218. Available online: https://eprints.glos.ac.uk/2429/ (accessed on 3 January 2024).
- Vandezande, N. Cybersecurity in the EU: How the NIS2-directive stacks up against its predecessor. Comput. Law Secur. Review 2024, 52, 105890. [Google Scholar] [CrossRef]
- Habbal, A.; Ali, M.K.; Abuzaraida, M.A. Artificial Intelligence Trust, Risk and Security Management (AI TRiSM): Frameworks, applications, challenges and future research directions. Expert Syst. Appl. 2024, 240, 122442. [Google Scholar]
- Ahmadi, S. Security and Privacy Challenges in Cloud-Based Data Warehousing: A Comprehensive Review. IJCST 2024, 11, 17–27. [Google Scholar]
- Hanneke, R.; Asada, Y.; Lieberman, L.; Neubauer, L.C.; Fagen, M. The Scoping Review Method: Mapping the Literature in Structural Change Public Health Interventions; SAGE Publications Ltd.: Thousand Oaks, CA, USA, 2017. [Google Scholar] [CrossRef]
- Miles, M.B.; Huberman, A.M. Qualitative Data Analysis: An Expanded Source Book, 2nd ed.; Sage: Newbury Park, CA, USA, 1994. [Google Scholar]
- Greca, I.M.; Moreira, A.M. Mental models, conceptual models, and modelling. Int. J. Sci. Educ. 2000, 22, 1–11. [Google Scholar] [CrossRef]
- Wand, Y.; Weber, R. Research Commentary: Information Systems and Conceptual Modeling—A Research Agenda. Inf. Syst. Res. 2002, 13, 363–371. [Google Scholar]
- Levering, B. Concept Analysis as Empirical Method. Int. J. Qual. Methods 2002, 1, 35–48. [Google Scholar] [CrossRef]
- Georgiadou, A.; Mouzakitis, S.; Bounas, K.; Askounis, D. A Cyber-Security Culture Framework for Assessing Organization Readiness. J. Comput. Inf. Syst. 2020, 62, 452–462. [Google Scholar] [CrossRef]
- Mishra, S.K.; Mishra, A.; Mohapatra, D.P. Risk Analysis of a system at design level using UML Diagrams. In Proceedings of the 2013 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Mysore, India, 22–25 August 2013; Available online: https://ieeexplore.ieee.org/document/6637170 (accessed on 9 August 2023).
- Alamri, Q.; Ali, M.A.; Tahir, N.M. Information Technology Risk Management in Oman. In Proceedings of the 2020 16th IEEE International Colloquium on Signal Processing & Its Applications (CSPA), Langkawi, Malaysia, 28–29 February 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 308–312. [Google Scholar]
- Martin-Guillerez, D.; Guiochet, J.; Powell, D.; Zanon, C. A UML-based method for risk analysis of human-robot interactions. In Proceedings of the 2nd International Workshop on Software Engineering for Resilient Systems, London, UK, 15–16 April 2010; pp. 32–41. [Google Scholar]
- Bertaux, D. From the life-history approach to the transformation of sociological practice. In Biography and Society: The Life History Approach in the Social Sciences; Bertaux, D., Ed.; Sage: London, UK, 1981; pp. 29–45. [Google Scholar]
- Krosnick, J.A. Improving question design to maximize reliability and validity. In The Palgrave Handbook of Survey Research; Vannette, D.L., Krosnick, J.A., Eds.; Palgrave Macmillan: New York, NY, USA, 2018; pp. 95–101. [Google Scholar]
- Kirvan, P.; Irei, A. Using the FAIR Model to Quantify Cyber-Risk; TechTarget: Newton, MA, UAS, 2023; Available online: https://www.techtarget.com/searchsecurity/tip/Using-the-FAIR-model-to-quantify-cyber-risk (accessed on 9 November 2023).
- Hedström, K.; Kolkowska, E.; Karlsson, F.; Allen, J.P. Value conflicts for information security management. J. Stra-Tegic Inf. Syst. 2011, 20, 373–384. [Google Scholar] [CrossRef]
- Shypovskyi, V. Enhancing the factor analysis of information risk methodology for assessing cyber-resilience in critical infrastructure information systems. Political Sci. Secur. Stud. J. 2023, 4, 25–33. [Google Scholar]
- Crespo-Martinez, P.E. Selecting the Business Information Security Officer with ECU@ Risk and the Critical Role Model. In In-ternational Conference on Applied Human Factors and Ergonomics; Springer: Cham, Switzerland, 2019; pp. 368–377. [Google Scholar]
- Middleton, J. Capita Cyber-Attack: 90 Organisations Report Data Breaches; The Guardian: London, UK, 2023; Available online: https://www.theguardian.com/business/2023/may/30/capita-cyber-attack-data-breaches-ico (accessed on 20 July 2023).
- Cram, W.A.; Proudfoot, J.G.; D’arcy, J. Organizational information security policies: A review and research framework. Eur. J. Inf. Syst. 2017, 26, 605–641. [Google Scholar] [CrossRef]
- Safa, N.S.; Maple, C.; Furnell, S.; Azad, M.A.; Perera, C.; Dabbagh, M.; Sookhak, M. Deterrence and prevention-based model to mitigate information security insider threats in organisations. Future Gener. Comput. Syst. 2019, 97, 587–597. [Google Scholar] [CrossRef]
- Dursun, S.M.; Mutluturk, M.; Taskin, N.; Metin, B. An Overview of the IT Risk Management Methodologies for Securing Information Assets. In Cases on Optimizing the Asset Management Process; IGI Global: Hershey, PA, USA, 2022; pp. 30–47. [Google Scholar] [CrossRef]
- Fredriksen, R.; Kristiansen, M.; Gran, B.A.; Stølen, K.; Opperud, T.A.; Dimitrakos, T. The CORAS framework for a model-based risk management process. In Proceedings of the Computer Safety, Reliability and Security: 21st International Conference Proceedings, SAFECOMP, Catania, Italy, 10–13 September 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 94–105. [Google Scholar]
- Weil, T. Risk assessment methods for cloud computing platforms. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; IEEE: Piscataway, NJ, USA, 2019; Volume 1, pp. 545–547. [Google Scholar]
- Nost, E.; Maxim, M.; Bell, K.; Worthington, J.; DiCicco, H. The State of Vulnerability Risk Management 2023; Forrester Report; Forrester: Cambridge, MA, USA, 2023; Available online: https://reprints2.forrester.com/#/assets/2/1730/RES179028/report (accessed on 22 August 2023).
- Irwin, L. Conducting an Asset-Based Risk Assessment in ISO 27001; Vigilant Software: Ely, UK, 2022; Available online: https://www.vigilantsoftware.co.uk/blog/conducting-an-asset-based-risk-assessment-in-iso-270012013 (accessed on 24 August 2023).
- Loloei, I.; Shahriari, H.R.; Sadeghi, A. A model for asset valuation in security risk analysis regarding assets’ dependencies. In Proceedings of the 20th Iranian Conference on Electrical Engineering (ICEE2012), Tehran, Iran, 15–17 May 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 763–768. [Google Scholar]
- Tatar, Ü.; Karabacak, B. A hierarchical asset valuation method for information security risk analysis. In Proceedings of the IEEE International Conference on Information Society (i-Society 2012), London, UK, 25–28 June 2012; pp. 286–291. [Google Scholar]
- Kassa, S.G.; Cisa, C. IT asset valuation, risk assessment, and control implementation model. ISACA J. 2017, 3, 1–9. [Google Scholar]
- Ruan, K. Digital Asset Valuation and Cyber Risk Measurement: Principles of Cybernomics; Academic Press: Cambridge, MA, USA, 2019. [Google Scholar]
- Ekstedt, M.; Afzal, Z.; Mukherjee, P.; Hacks, S.; Lagerström, R. Yet another cybersecurity risk assessment framework. Int. J. Inf. Secur. 2023, 22, 1713–1729. [Google Scholar] [CrossRef]
- Berry, H.S. The Importance of Cybersecurity in Supply Chain. In Proceedings of the 11th IEEE International Symposium on Digital Forensics and Security (ISDFS), Chattanooga, TN, USA, 11–12 May 2023; pp. 1–5. [Google Scholar]
- Edwards, B.; Jacobs, J.; Forrest, S. Risky Business: Assessing Security with External Measurements. arXiv 2019, arXiv:1904.11052. [Google Scholar]
- Youssef, A.E. A Framework for Cloud Security Risk Management Based on the Business Objectives of Organizations. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 186–194. [Google Scholar] [CrossRef]
- Dennig, F.L.; Cakmak, E.; Plate, H.; Keim, D.A. VulnEx: Exploring Open-Source Software Vulnerabilities in Large Development Organizations to Understand Risk Exposure. arXiv 2022, arXiv:2108.06259v3. [Google Scholar]
- Goyal, H.P.; Akhil, G.; Ramasubramanian, S. Manage Risks in Complex Engagements by Leveraging Organization-Wide Knowledge Using Machine Learning. arXiv 2022, arXiv:2202.10332. [Google Scholar]
- Hu, K.; Levi, R.; Yahalom, R.; Zerhouni, E. Supply Chain Characteristics as Predictors of Cyber Risk: A Machine-Learning Assessment. arXiv 2023, arXiv:2210.15785v5. [Google Scholar]
- Khani, S.; Gacek, C.; Popov, P. Security-aware selection of web services for reliable composition. arXiv 2015, arXiv:1510.02391. [Google Scholar]
- Hammi, B.; Zeadally, S.; Nebhen, J. Security threats, countermeasures, and challenges of digital supply chains. ACM Comput. Surv. 2023, 55, 316. [Google Scholar]
- Marcu, P.; Hommel, W. Inter-organizational fault management: Functional and organizational core aspects of management architectures. arXiv 2011, arXiv:1101.3891. [Google Scholar] [CrossRef]
- Eyadema, S.I. Outsource Supply Chain Challenges and Risk Mitigation. Unpublished Doctoral Dissertation, Utica College, New York, NY, USA, 2021. [Google Scholar]
- Cristopher, A. Employing COBIT 2019 for Enterprise Governance Strategy. 2019. Available online: https://www.isaca.org/resources/news-and-trends/industry-news/2019/employing-cobit-2019-for-enterprise-governance-strategy (accessed on 11 September 2023).
- OneTrust. Avoid Uncertainty—Empower Your Operations with Risk-Based Decision Making. 2023. Available online: https://www.onetrust.com/solutions/grc-and-security-assurance-cloud/ (accessed on 24 November 2023).
- Archer. Archer GRC Solution. Available online: https://www.archerirm.com/content/grc (accessed on 24 November 2023).
- SAP. Governance, Risk, Compliance (GRC), and Cybersecurity. 2023. Available online: https://www.sap.com/products/financial-management/grc.html (accessed on 24 November 2023).
- Oracle. Oracle Enterprise Governance, Risk and Compliance Documentation. 2023. Available online: https://docs.oracle.com/applications/grc866/ (accessed on 24 November 2023).
- Lund, M.S.; Solhaug, B.; Stølen, K. Model-Driven Risk Analysis: The CORAS Approach; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Nost, E.; Burn, J. CISA Releases Directives on Asset Discovery and Vulnerability Enumeration; Forrester: Cambridge, MA, USA, 2022; Available online: https://www.forrester.com/blogs/cisa-releases-directives-on-asset-discovery-and-vulnerability-enumeration/ (accessed on 4 October 2023).
- Rapid7. Evaluating Vulnerability Assessment Solutions. Available online: https://www.rapid7.com/globalassets/_pdfs/whitepaperguide/rapid7-vulnerability-assessment-buyers-guide.pdf (accessed on 9 October 2023).
- EUR-Lex. Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on Measures for a High Common Level of Cybersecurity across the Union, Amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and Re-Pealing Directive (EU) 2016/1148 (NIS 2 Directive); Official Journal of the European Union: Brussels, Belgium, 2022; Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32022L2555 (accessed on 24 November 2023).
- CyberArk/PWC. Getting Ready for the NIS2 Directive; White Paper; CyberArk UK: London, UK, 2023; Available online: https://www.cyberark.com/resources/white-papers/getting-ready-for-nis2?utm_source=google&utm_medium=paid_search&utm_term=emea_english_nl_ie_be_dk_sw_it_es_fr&utm_content=20230220_gb_wc_nis2_get_ready_pwc_wp&utm_campaign=security_privilege_access&gclid=CjwKCAiA6byqBhAWEiwAnGCA4LSZ1FpvLUjXjEyu1LJvBqpKVY73PryI2HnXd_BYvR23uZX74Z19RxoCY9QQAvD_BwE (accessed on 11 November 2023).
- EUR-Lex. Regulation (EU) 2022/2554 of the European Parliament and of the Council of 14 December 2022 on Digital Operational Resilience for the Financial Sector and Amending Regulations (EC) No 1060/2009, (EU) No 648/2012, (EU) No 600/2014, (EU) No 909/2014 and (EU) 2016/1011; Official Journal of the European Union: Brussels, Belgium, 2022; Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32022R2554 (accessed on 11 November 2023).
- ISO 27001; Information Technology—Security Techniques–Information Security Management Systems—Requirements. International Organization for Standardization: Geneva, Switzerland, 2013. Available online: http://www.itref.ir/uploads/editor/42890b.pdf (accessed on 23 August 2023).
- ISO 27005:2022; Information Technology—Security Techniques—Information Security Risk Management. International Organization for Standardization: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/80585.html (accessed on 23 August 2023).
- ISO 31000; Risk Management—Guidelines. International Organization for Standardization: Geneva, Switzerland, 2018. Available online: https://www.iso.org/standard/65694.html (accessed on 30 June 2023).
- Kosutic, D. ISO 31000 and ISO 27001—How Are They Related? 2022. Available online: https://advisera.com/27001academy/blog/2014/03/31/iso-31000-and-iso-27001-how-are-they-related/#:~:text=In%20clause%206.1.-,3%2C%20ISO%2027001%20notes%20that%20information%20security%20management%20in%20ISO,already%20compliant%20with%20ISO%2031000 (accessed on 23 August 2023).
- Harisaiprasad, K. COBIT 2019 and COBIT 5 Comparison; ISACA: Schaumburg, IL, USA, 2020; Available online: https://www.isaca.org/resources/news-and-trends/industry-news/2020/cobit-2019-and-cobit-5-comparison (accessed on 12 October 2023).
- Wambacq, J. Subject-Object in Martin Heidegger, Bruno Latour and Manuel De Landa. 2000. Available online: https://constantvzw.org/verlag/spip.php?article79# (accessed on 25 November 2023).
- O’Donnell, K. Strategies for Addressing the Problems of Subjectivity and Uncertainty in Quality Risk Management Exercises: Part I-The Role of Human Heuristics. J. Valid. Technol. 2020, 16, 76–84. [Google Scholar]
- Wynn, M.; Jones, P. New technology deployment and corporate responsibilities in the metaverse. Knowledge 2023, 3, 543–556. [Google Scholar] [CrossRef]
- Nightingale, C. Managing Cyber Risk through Integrated Supply Chains. Computer Weekly, 21 September 2021. Available online: https://www.computerweekly.com/opinion/Managing-cyber-risk-through-integrated-supply-chains?utm_campaign=20211229_ERU+Transmission+for+12%2F29%2F2021+%28UserUniverse%3A+364164%29&utm_medium=EM&utm_source=ERU&src=8907352&asrc=EM_ERU_198647440&utm_content=eru-rd2-rcpC (accessed on 9 October 2023).
- ISC2. 9 Traits You Need to Succeed as a Cybersecurity Leader. 2020. Available online: https://media.bitpipe.com/io_16x/io_167060/item_2670924/Res%20ID_%201665550744_355_%209-Traits-You-Need-To-Succeed-As-A-Cybersecurity-Leader-Whitepaper-RB.pdf (accessed on 9 October 2023).





| Senior IT auditor/consultant with 30 years’ experience |
| Senior IT auditor/director at a major international consultancy with 20 years’ experience |
| IT audit manager in a bank with 10 years’ experience |
| Executive at IT security, risk and compliance department with 15 years’ experience |
| Cyber security consultant at a major international consultancy with 3 years’ experience |
| Manager at a major international consultancy with 13 years’ experience |
| Information security assistant manager at a major international insurance company |
| Head of IT audit at a leading Turkish banking group |
| Head of IT audit in both public and private sector organisations |
| Chief information security officer at a Turkish financial institution with 20 years’ experience |
| Head of internal audit in a finance bank in Turkey with 5 years’ experience |
| Senior cybersecurity expert with 15 years’ experience |
| Director and IS audit leader at a major international consultancy with 15 years’ experience |
| IT manager and auditor roles with 20 years’ experience |
| Director and IS audit leader in several companies with 20 years’ experience |
| IT security and audit expert in a university with 10 years’ experience |
| No. | Statements | Strongly Agree | Agree | Neutral | Disagree | Strongly Disagree |
|---|---|---|---|---|---|---|
| 1 | The risk assessment method is beneficial for business sustainability. | 8 | 8 | 0 | 0 | 0 |
| 2 | The risk assessment method is suitable for small-scale businesses (<50 staff). | 3 | 8 | 3 | 2 | 0 |
| 3 | The risk assessment method is suitable for medium-sized businesses (50–250 staff). | 3 | 12 | 1 | 0 | 0 |
| 4 | The assessment method is suitable for large businesses (>250 staff). | 6 | 10 | 0 | 0 | 0 |
| 5 | The risk assessment method helps minimise subjectivity. | 1 | 12 | 3 | 0 | 0 |
| 6 | The risk assessment method benefits from the involvement of individuals who have an in-depth understanding of the specific details related to assets. | 8 | 7 | 1 | 0 | 0 |
| 7 | The risk assessment method benefits from a combination of high-level management guidance and operational perspectives. | 8 | 8 | 0 | 0 | 0 |
| 8 | The risk assessment method increases employees’ information security awareness. | 9 | 7 | 0 | 0 | 0 |
| Totals | 46 | 72 | 8 | 2 | 0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Metin, B.; Duran, S.; Telli, E.; Mutlutürk, M.; Wynn, M. IT Risk Management: Towards a System for Enhancing Objectivity in Asset Valuation That Engenders a Security Culture. Information 2024, 15, 55. https://doi.org/10.3390/info15010055
Metin B, Duran S, Telli E, Mutlutürk M, Wynn M. IT Risk Management: Towards a System for Enhancing Objectivity in Asset Valuation That Engenders a Security Culture. Information. 2024; 15(1):55. https://doi.org/10.3390/info15010055
Chicago/Turabian StyleMetin, Bilgin, Sefa Duran, Eda Telli, Meltem Mutlutürk, and Martin Wynn. 2024. "IT Risk Management: Towards a System for Enhancing Objectivity in Asset Valuation That Engenders a Security Culture" Information 15, no. 1: 55. https://doi.org/10.3390/info15010055
APA StyleMetin, B., Duran, S., Telli, E., Mutlutürk, M., & Wynn, M. (2024). IT Risk Management: Towards a System for Enhancing Objectivity in Asset Valuation That Engenders a Security Culture. Information, 15(1), 55. https://doi.org/10.3390/info15010055