Innovation in Information Security
Share This Topical Collection
Editors
 Dr. Gianluca Lax
Dr. Gianluca Lax
 Dr. Gianluca Lax
Dr. Gianluca Lax
E-Mail
Website
Collection Editor
Department of Information Engineering, Infrastructure and Sustainable Energy (DIIES), University Mediterranea of Reggio Calabria, 89122 Reggio Calabria, Italy
Interests: privacy; access control; blockchain; social network analysis
Special Issues, Collections and Topics in MDPI journals
 Dr. Antonia Russo
Dr. Antonia Russo
 Dr. Antonia Russo
Dr. Antonia Russo
E-Mail
Website
Collection Editor
Department of Information Engineering, Infrastructure and Sustainable Energy (DIIES), University Mediterranea of Reggio Calabria, 89122 Reggio Calabria, Italy
Interests: security; privacy; access control; social network analysis
Special Issues, Collections and Topics in MDPI journals
Topical Collection Information
Dear Colleagues,
Information is increasingly becoming a key asset of organizations and, in general, of people. An information breach can cost millions of dollars because it can reduce share value, ruin a reputation, or result in legal liability. For this reason, research in designing and implementing security mechanisms to keep information and information systems free from threats is a complex, timely, and rewarding challenge.
The objective of this collection is to bring together the state-of-the-art research contributions that include but are not limited to:
- information risks
- risk management
- information threats
- information vulnerabilities
- information disclosure
- unauthorized access
- devaluation of information
- confidentiality
- integrity
- availability
- privacy
- authenticity and trustworthiness
- non-repudiation
- accountability and auditability
- cryptography for information security
- machine learning for information security
- disruptive technologies for information security
- new trends in information security
Dr. Gianluca Lax
Dr. Antonia Russo
Collection Editors
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. All papers will be peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the collection website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for a preliminary check of suitability.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Applied Sciences is an international peer-reviewed open access semimonthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript. The Article Processing Charge (APC) for publication in this open access journal is 2300 CHF (Swiss Francs). Submitted papers should be well formatted and use good English. Authors may use MDPI's English editing service prior to publication or during author revisions.
Published Papers (25 papers)
Open AccessArticle
A Quantum-Secure Cryptographic Algorithm Integrating Fractals and Prime Numbers
by
Gerardo Iovane, Elmo Benedetto and Antonio Di Lauro
Viewed by 610
Abstract
The present work introduces a new scheme of data cryptography in the context of emerging trends due to the challenge of defending critical network infrastructure against new exploit systems based on artificial intelligence or defending against quantum threats. In this paper, we will
[...] Read more.
The present work introduces a new scheme of data cryptography in the context of emerging trends due to the challenge of defending critical network infrastructure against new exploit systems based on artificial intelligence or defending against quantum threats. In this paper, we will present an innovative cryptographic system composed of keys coming from fractals and prime numbers that are additionally manipulated through mathematical operations using matrices and quantum security. This technique ensures a high level of security, as demonstrated by the NIST
p-values calculated on the key. This paper works upon the foundation on the previous work F&NIF (Fractal & Numerical Information Fusion), as we will discuss in the paper. In this work, we take this procedure and expand it with these new added features, using new fractal schemes and, in particular, implementing a novel quantum security procedure. This algorithm creates a security key applicable to cryptography that is resistant to quantum attacks since this procedure is quantum-crypto-agile.
Full article
►▼
Show Figures
Open AccessArticle
Detecting Phishing URLs Based on a Deep Learning Approach to Prevent Cyber-Attacks
by
Qazi Emad ul Haq, Muhammad Hamza Faheem and Iftikhar Ahmad
Viewed by 963
Abstract
Phishing is one of the most widely observed types of internet cyber-attack, through which hundreds of clients using different internet services are targeted every day through different replicated websites. The phishing attacker spreads messages containing false URL links through emails, social media platforms,
[...] Read more.
Phishing is one of the most widely observed types of internet cyber-attack, through which hundreds of clients using different internet services are targeted every day through different replicated websites. The phishing attacker spreads messages containing false URL links through emails, social media platforms, or messages, targeting people to steal sensitive data like credentials. Attackers generate phishing URLs that resemble those of legitimate websites to gain these confidential data. Hence, there is a need to prevent the siphoning of data through the duplication of trustworthy websites and raise public awareness of such practices. For this purpose, many machine learning and deep learning models have been employed to detect and prevent phishing attacks, but due to the ever-evolving nature of these attacks, many systems fail to provide accurate results. In this study, we propose a deep learning-based system using a 1D convolutional neural network to detect phishing URLs. The experimental work was performed using datasets from Phish-Tank, UNB, and Alexa, which successfully generated 200 thousand phishing URLs and 200 thousand legitimate URLs. The experimental results show that the proposed system achieved 99.7% accuracy, which was better than the traditional models proposed for URL-based phishing detection.
Full article
►▼
Show Figures
Open AccessArticle
Anonymous Access System with Limited Number of Uses in a Trustless Environment
by
Francesc Garcia-Grau, Jordi Herrera-Joancomartí and Aleix Dorca Josa
Viewed by 600
Abstract
This article proposes a novel method for managing usage counters within an anonymous credential system, addressing the limitation of traditional anonymous credentials in tracking repeated use. The method takes advantage of blockchain technology through Smart Contracts deployed on the Ethereum network to enforce
[...] Read more.
This article proposes a novel method for managing usage counters within an anonymous credential system, addressing the limitation of traditional anonymous credentials in tracking repeated use. The method takes advantage of blockchain technology through Smart Contracts deployed on the Ethereum network to enforce a predetermined maximum number of uses for a given credential. Users retain control over increments by providing zero-knowledge proofs (ZKPs) demonstrating private key possession and agreement on the increment value. This approach prevents replay attacks and ensures transparency and security. A prototype implementation on a private Ethereum blockchain demonstrates the feasibility and efficiency of the proposed method, paving the way for its potential deployment in real-world applications requiring both anonymity and usage tracking.
Full article
►▼
Show Figures
Open AccessArticle
A Secure Median Implementation for the Federated Secure Computing Architecture
by
Christian Goelz, Solveig Vieluf and Hendrik Ballhausen
Viewed by 794
Abstract
In Secure Multiparty Computation (MPC or SMPC), functions are evaluated in encrypted peer-to-peer networks without revealing the private inputs of the participating parties. The median is a non-trivial computation in MPC and is particularly relevant in fields like medicine and economics. Here, we
[...] Read more.
In Secure Multiparty Computation (MPC or SMPC), functions are evaluated in encrypted peer-to-peer networks without revealing the private inputs of the participating parties. The median is a non-trivial computation in MPC and is particularly relevant in fields like medicine and economics. Here, we provide an MPC implementation of the median for the Federated Secure Computing (FSC) framework. It is tested on synthetic datasets with varying sizes (
to
) and number of participants (
to
) across different network environments and hardware configurations. Using minimal networking and computational resources on a commercial hyperscaler, we evaluated real-world performance with breast cancer (
) and heart disease (
) datasets. Our results showed effective scaling up to
entries with runtime between 1 and 4 s, but runtime exceeded 15 s for
entries. The runtime increased linearly with the number of parties, remaining below one minute for up to
parties. Tests with real-world medical data highlight significant network overhead, with runtime increasing from 16 to 17 s locally to over 800 s across hyperscaler regions, emphasizing the need to minimize latency for practical deployment.
Full article
►▼
Show Figures
Open AccessArticle
Malware Classification Using Dynamically Extracted API Call Embeddings
by
Sahil Aggarwal and Fabio Di Troia
Viewed by 1581
Abstract
Malware classification stands as a crucial element in establishing robust computer security protocols, encompassing the segmentation of malware into discrete groupings. Recently, the emergence of machine learning has presented itself as an apt approach for addressing this challenge. Models can undergo training employing
[...] Read more.
Malware classification stands as a crucial element in establishing robust computer security protocols, encompassing the segmentation of malware into discrete groupings. Recently, the emergence of machine learning has presented itself as an apt approach for addressing this challenge. Models can undergo training employing diverse malware attributes, such as opcodes and API calls, to distill valuable insights for effective classification. Within the realm of natural language processing, word embeddings assume a pivotal role by representing text in a manner that aligns closely with the proximity of similar words. These embeddings facilitate the quantification of word resemblances. This research embarks on a series of experiments that harness hybrid machine learning methodologies. We derive word vectors from dynamic API call logs associated with malware and integrate them as features in collaboration with diverse classifiers. Our methodology involves the utilization of Hidden Markov Models and Word2Vec to generate embeddings from API call logs. Additionally, we amalgamate renowned models like BERT and ELMo, noted for their capacity to yield contextualized embeddings. The resultant vectors are channeled into our classifiers, namely Support Vector Machines (SVMs), Random Forest (RF), k-Nearest Neighbors (kNNs), and Convolutional Neural Networks (CNNs). Through two distinct sets of experiments, our objective revolves around the classification of both malware families and categories. The outcomes achieved illuminate the efficacy of API call embeddings as a potent instrument in the domain of malware classification, particularly in the realm of identifying malware families. The best combination was RF and word embeddings generated by Word2Vec, ELMo, and BERT, achieving an accuracy between 0.91 and 0.93. This result underscores the potential of our approach in effectively classifying malware.
Full article
►▼
Show Figures
Open AccessArticle
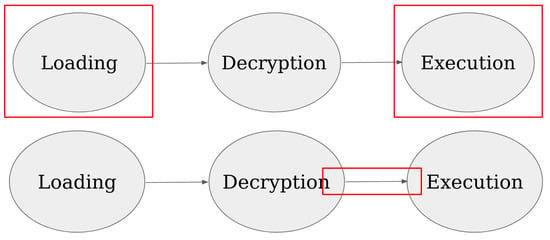
JITScanner: Just-in-Time Executable Page Check in the Linux Operating System
by
Pasquale Caporaso, Giuseppe Bianchi and Francesco Quaglia
Viewed by 976
Abstract
Modern malware poses a severe threat to cybersecurity, continually evolving in sophistication. To combat this threat, researchers and security professionals continuously explore advanced techniques for malware detection and analysis. Dynamic analysis, a prevalent approach, offers advantages over static analysis by enabling observation of
[...] Read more.
Modern malware poses a severe threat to cybersecurity, continually evolving in sophistication. To combat this threat, researchers and security professionals continuously explore advanced techniques for malware detection and analysis. Dynamic analysis, a prevalent approach, offers advantages over static analysis by enabling observation of runtime behavior and detecting obfuscated or encrypted code used to evade detection. However, executing programs within a controlled environment can be resource-intensive, often necessitating compromises, such as limiting sandboxing to an initial period. In our article, we propose an alternative method for dynamic executable analysis: examining the presence of malicious signatures within executable virtual pages precisely when their current content, including any updates over time, is accessed for instruction fetching. Our solution, named JITScanner, is developed as a Linux-oriented package built upon a Loadable Kernel Module (LKM). It integrates a user-level component that communicates efficiently with the LKM using scalable multi-processor/core technology. JITScanner’s effectiveness in detecting malware programs and its minimal intrusion in normal runtime scenarios have been extensively tested, with the experiment results detailed in this article. These experiments affirm the viability of our approach, showcasing JITScanner’s capability to effectively identify malware while minimizing runtime overhead.
Full article
►▼
Show Figures
Open AccessArticle
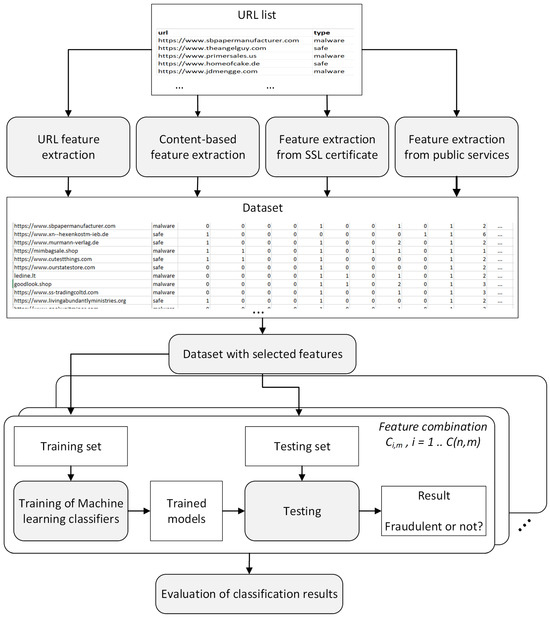
Experimental Evaluation of Possible Feature Combinations for the Detection of Fraudulent Online Shops
by
Audronė Janavičiūtė, Agnius Liutkevičius, Gedas Dabužinskas and Nerijus Morkevičius
Viewed by 1193
Abstract
Online shopping has become a common and popular form of shopping, so online attackers try to extract money from customers by creating online shops whose purpose is to compel the buyer to disclose credit card details or to pay money for goods that
[...] Read more.
Online shopping has become a common and popular form of shopping, so online attackers try to extract money from customers by creating online shops whose purpose is to compel the buyer to disclose credit card details or to pay money for goods that are never delivered. Existing buyer protection methods are based on the analysis of the content of the online shop, customer reviews, the URL (Uniform Resource Locator) of the website, the search in blacklists or whitelists, or the combination of the above-mentioned methods. This study aims to find the minimal set of publicly and easily obtainable features to create high-precision classification solutions that require little computing and memory resources. We evaluate various combinations of 18 features that belong to three possible categories, namely URL-based, content-based, and third-party services-based. For this purpose, the custom dataset is created, and several machine learning models are applied for the detection of fraudulent online shops based on these combinations of features. The results of this study show that even only four of the most significant features allow one to achieve 0.9342 classification accuracy, while 0.9605 accuracy is reached with seven features, and the best accuracy of 0.9693 is achieved using thirteen and fifteen features.
Full article
►▼
Show Figures
Open AccessArticle
RoseCliff Algorithm: Making Passwords Dynamic
by
Afamefuna P. Umejiaku and Victor S. Sheng
Viewed by 1334
Abstract
Authentication in the digital landscape faces persistent challenges due to evolving cyber threats. Traditional text-based passwords, which are vulnerable to various attacks, necessitate innovative solutions to fortify user systems. This paper introduces the RoseCliff Algorithm, which is a dual authentication mechanism designed to
[...] Read more.
Authentication in the digital landscape faces persistent challenges due to evolving cyber threats. Traditional text-based passwords, which are vulnerable to various attacks, necessitate innovative solutions to fortify user systems. This paper introduces the RoseCliff Algorithm, which is a dual authentication mechanism designed to enhance resilience against sophisticated hacking attempts and to continuously evolve stored passwords. The study explores encryption techniques, including symmetric, asymmetric, and hybrid encryption, thereby addressing the emerging threats posed by quantum computers. The RoseCliff Algorithm introduces introduces dynamism into passwords that allows for more secured communication across multiple platforms. To assess the algorithm’s robustness, potential attacks such as brute force, dictionary attacks, man-in-the-middle attacks, and machine learning-based attacks are examined. The RoseCliff Algorithm, through its dynamic password generation and encryption methodology, proves effective against these threats. Usability evaluation encompasses the implementation and management phase, focusing on seamless integration, and the user experience, emphasizing clarity and satisfaction. Limitations are acknowledged, thus urging further research into encryption technique resilience, robustness against breaches, and the integration of emerging technologies. In conclusion, the RoseCliff Algorithm emerges as a promising solution, thereby effectively addressing the complexities of modern authentication challenges and providing a foundation for future research and enhancements in digital security.
Full article
Open AccessArticle
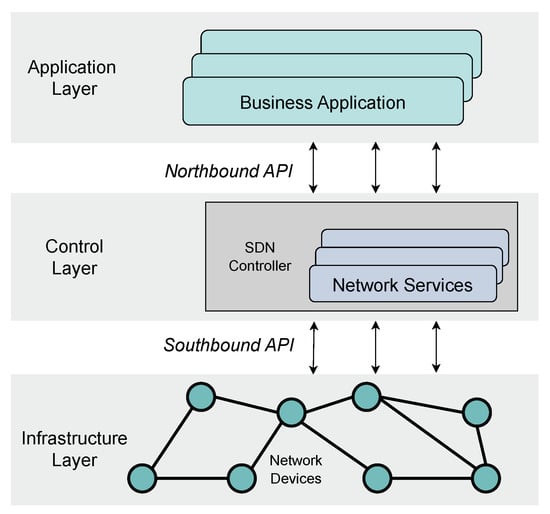
Detection and Mitigation of Security Threats Using Virtualized Network Functions in Software-Defined Networks
by
Manuel Domínguez-Dorado, Jesús Calle-Cancho, Jesús Galeano-Brajones, Francisco-Javier Rodríguez-Pérez and David Cortés-Polo
Viewed by 2426
Abstract
The evolution of interconnected systems and the evolving demands in service requirements have led to data centers integrating multiple heterogeneous technologies that must coexist. Consequently, the resource management and the security of the infrastructure are becoming more complex than in traditional scenarios. In
[...] Read more.
The evolution of interconnected systems and the evolving demands in service requirements have led to data centers integrating multiple heterogeneous technologies that must coexist. Consequently, the resource management and the security of the infrastructure are becoming more complex than in traditional scenarios. In this context, technologies such as Software-Defined Networking (SDN) or Network Function Virtualization (NFV) are being embraced as mechanisms that facilitate communication management. The integration of both technologies into a single framework, termed Software-Defined NFV (SDNFV) introduces a multitude of tools for managing the security of the data center’s resources. This work delineates the primary characteristics of the evolution of these communication networks and their application to information security and communications within a data center. It presents an illustrative use case demonstrating the application of these next-generation technologies to detect and mitigate a security issue through virtualized network functions deployed in containers.
Full article
►▼
Show Figures
Open AccessArticle
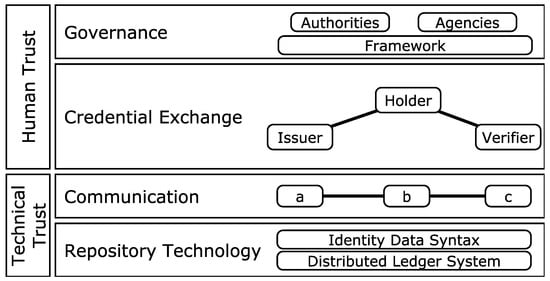
Analyzing the Threats to Blockchain-Based Self-Sovereign Identities by Conducting a Literature Survey
by
Daniela Pöhn, Michael Grabatin and Wolfgang Hommel
Viewed by 2389
Abstract
Self-sovereign identity (SSI) is a digital identity management model managed in a decentralized manner. It allows identity owners to manage and store their digital identities in a software wallet, for example, on a smartphone, without relying on centralized providers. This approach tries to
[...] Read more.
Self-sovereign identity (SSI) is a digital identity management model managed in a decentralized manner. It allows identity owners to manage and store their digital identities in a software wallet, for example, on a smartphone, without relying on centralized providers. This approach tries to enhance the security and privacy of digital identities and, thereby, their owners. With the new eIDAS regulation, elements of SSI, such as the wallet, are being pushed onto the market. However, since the model is relatively new, the security threats are still not fully known. This is shown by a brief security analysis of selected existing SSI wallets. In order to get a picture of the known threats, we systematically analyze and categorize related work in the field of SSI and elements applied by SSI. We then evaluate their application to current SSI systems and identify future work.
Full article
►▼
Show Figures
Open AccessArticle
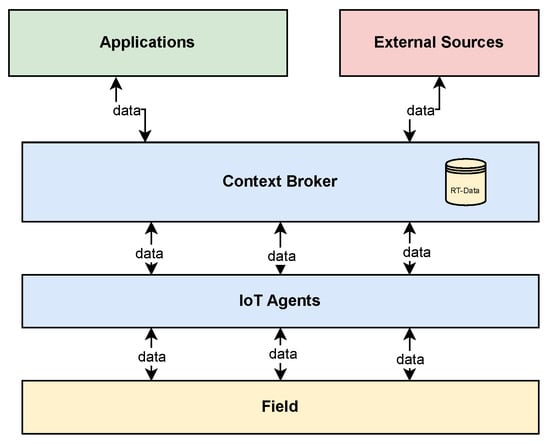
Building Cyber-Resilient Smart Grids with Digital Twins and Data Spaces
by
Luigi Coppolino, Roberto Nardone, Alfredo Petruolo and Luigi Romano
Cited by 3 | Viewed by 2084
Abstract
The rapid expansion of digital twin technology has revolutionized management and testing across various sectors, particularly in safeguarding critical infrastructure like smart grids. Aligned with the NIS2 Directive, Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022,
[...] Read more.
The rapid expansion of digital twin technology has revolutionized management and testing across various sectors, particularly in safeguarding critical infrastructure like smart grids. Aligned with the NIS2 Directive, Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022, digital twins play a critical role in bolstering cybersecurity measures by enabling advanced simulation and real-time monitoring, key aspects emphasized in the directive for enhancing the security of networks and information systems. Concurrently, Europe’s shift towards communal data spaces amplifies the need for robust cyber defences. This paper aims to bolster cybersecurity defences in critical infrastructure, with a particular focus on the energy sector and smart grids. It proposes an innovative architecture for cybersecurity monitoring, converting a Common Information Model-compliant system into a digital twin via the FIWARE platform and incorporating an open-source Security Information and Event Management solution. Validated by a real-world case study, our approach demonstrates significant advancements in protecting smart grids against cyber threats.
Full article
►▼
Show Figures
Open AccessArticle
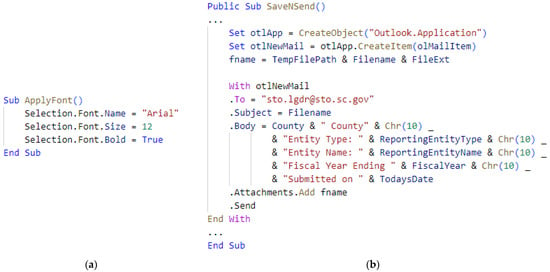
Malicious Office Macro Detection: Combined Features with Obfuscation and Suspicious Keywords
by
Xiang Chen, Wenbo Wang and Weitao Han
Cited by 1 | Viewed by 2134
Abstract
Microsoft has implemented several measures to defend against macro viruses, including the use of the Antimalware Scan Interface (AMSI) and automatic macro blocking. Nevertheless, evidence shows that threat actors have found ways to bypass these mechanisms. As a result, phishing emails continue to
[...] Read more.
Microsoft has implemented several measures to defend against macro viruses, including the use of the Antimalware Scan Interface (AMSI) and automatic macro blocking. Nevertheless, evidence shows that threat actors have found ways to bypass these mechanisms. As a result, phishing emails continue to utilize malicious macros as their primary attack method. In this paper, we analyze 77 obfuscation features from the attacker’s perspective and extract 46 suspicious keywords in macros. We first combine the aforementioned two types of features to train machine learning models on a public dataset. Then, we conduct the same experiment on a self-constructed dataset consisting of newly discovered samples, in order to verify if our proposed method can identify previously unseen malicious macros. Experimental results demonstrate that, compared to existing methods, our proposed method has a higher detection rate and better consistency. Furthermore, ensemble multi-classifiers with distinct feature selection can further enhance the detection performance.
Full article
►▼
Show Figures
Open AccessArticle
A Survey of Detection and Mitigation for Fake Images on Social Media Platforms
by
Dilip Kumar Sharma, Bhuvanesh Singh, Saurabh Agarwal, Lalit Garg, Cheonshik Kim and Ki-Hyun Jung
Cited by 3 | Viewed by 5676
Abstract
Recently, the spread of fake images on social media platforms has become a significant concern for individuals, organizations, and governments. These images are often created using sophisticated techniques to spread misinformation, influence public opinion, and threaten national security. This paper begins by defining
[...] Read more.
Recently, the spread of fake images on social media platforms has become a significant concern for individuals, organizations, and governments. These images are often created using sophisticated techniques to spread misinformation, influence public opinion, and threaten national security. This paper begins by defining fake images and their potential impact on society, including the spread of misinformation and the erosion of trust in digital media. This paper also examines the different types of fake images and their challenges for detection. We then review the recent approaches proposed for detecting fake images, including digital forensics, machine learning, and deep learning. These approaches are evaluated in terms of their strengths and limitations, highlighting the need for further research. This paper also highlights the need for multimodal approaches that combine multiple sources of information, such as text, images, and videos. Furthermore, we present an overview of existing datasets, evaluation metrics, and benchmarking tools for fake image detection. This paper concludes by discussing future directions for fake image detection research, such as developing more robust and explainable methods, cross-modal fake detection, and the integration of social context. It also emphasizes the need for interdisciplinary research that combines computer science, digital forensics, and cognitive psychology experts to tackle the complex problem of fake images. This survey paper will be a valuable resource for researchers and practitioners working on fake image detection on social media platforms.
Full article
►▼
Show Figures
Open AccessArticle
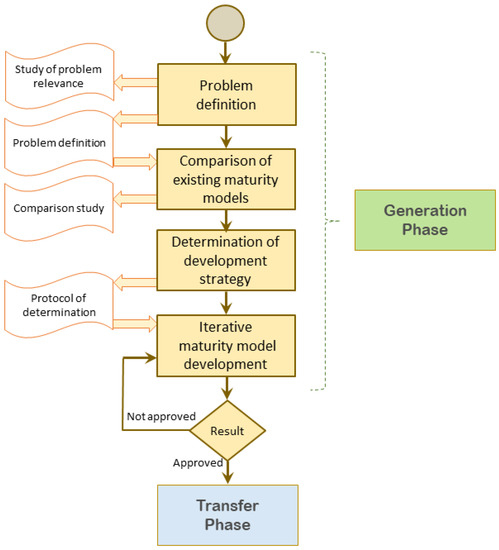
AIM Triad: A Prioritization Strategy for Public Institutions to Improve Information Security Maturity
by
Jorge Hochstetter-Diez, Mauricio Diéguez-Rebolledo, Julio Fenner-López and Cristina Cachero
Cited by 2 | Viewed by 1664
Abstract
In today’s world, private and government organizations are legally obligated to prioritize their information security. They need to provide proof that they are continually improving their cybersecurity compliance. One approach that can help organizations achieve this goal is implementing information security maturity models.
[...] Read more.
In today’s world, private and government organizations are legally obligated to prioritize their information security. They need to provide proof that they are continually improving their cybersecurity compliance. One approach that can help organizations achieve this goal is implementing information security maturity models. These models provide a structured framework for measuring performance and implementing best practices. However, choosing a suitable model can be challenging, requiring cultural, process, and work practice changes. Implementing multiple models can be overwhelming, if possible. This article proposes a prioritization strategy for public institutions that want to improve their information security maturity. We thoroughly analyzed various sources through systematic mapping to identify critical similarities in information security maturity models. Our research led us to create the AIM (Awareness, Infrastructure, and Management) Triad. This triad is a practical guide for organizations to achieve maturity in information security practices.
Full article
►▼
Show Figures
Open AccessArticle
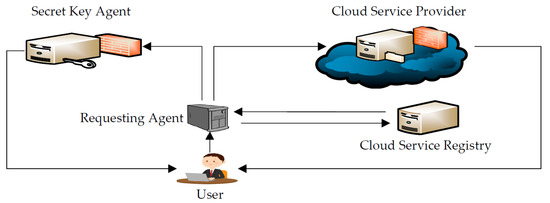
Privacy-Aware Cloud Architecture for Collaborative Use of Patients’ Health Information
by
Fadi Alhaddadin and Jairo Gutierrez
Viewed by 1536
Abstract
Cloud computing appears to be the dreamed-of vision of the healthcare industry; it refers to means of storing and accessing data and programs over the Internet instead of the computer’s hard drive. However, the adoption of cloud computing requires solving several issues, and
[...] Read more.
Cloud computing appears to be the dreamed-of vision of the healthcare industry; it refers to means of storing and accessing data and programs over the Internet instead of the computer’s hard drive. However, the adoption of cloud computing requires solving several issues, and information privacy is a major one. This work proposes a cloud architecture design for the healthcare information system. The proposed architecture enables storing and sharing information in a privacy-preserving manner. Patients’ information in the proposed architecture is divided into four categories identified in the case study data analysis. User identity management protocol (U-IDM) is employed for controlling access to patients’ information, and patients have means of control over who can access their information. A scenario-based instantiation validated the proposed architecture’s privacy-preserving patient data exchange. The instantiation proved that the proposed architecture allows sharing healthcare information without violating the privacy of patients.
Full article
►▼
Show Figures
Open AccessEditor’s ChoiceArticle
HDLNIDS: Hybrid Deep-Learning-Based Network Intrusion Detection System
by
Emad Ul Haq Qazi, Muhammad Hamza Faheem and Tanveer Zia
Cited by 39 | Viewed by 6639
Abstract
Attacks on networks are currently the most pressing issue confronting modern society. Network risks affect all networks, from small to large. An intrusion detection system must be present for detecting and mitigating hostile attacks inside networks. Machine Learning and Deep Learning are currently
[...] Read more.
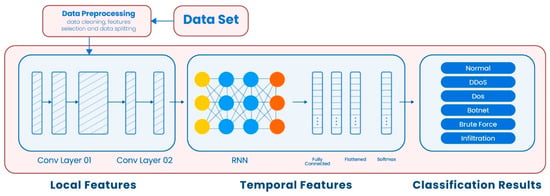
Attacks on networks are currently the most pressing issue confronting modern society. Network risks affect all networks, from small to large. An intrusion detection system must be present for detecting and mitigating hostile attacks inside networks. Machine Learning and Deep Learning are currently used in several sectors, particularly the security of information, to design efficient intrusion detection systems. These systems can quickly and accurately identify threats. However, because malicious threats emerge and evolve regularly, networks need an advanced security solution. Hence, building an intrusion detection system that is both effective and intelligent is one of the most cognizant research issues. There are several public datasets available for research on intrusion detection. Because of the complexity of attacks and the continually evolving detection of an attack method, publicly available intrusion databases must be updated frequently. A convolutional recurrent neural network is employed in this study to construct a deep-learning-based hybrid intrusion detection system that detects attacks over a network. To boost the efficiency of the intrusion detection system and predictability, the convolutional neural network performs the convolution to collect local features, while a deep-layered recurrent neural network extracts the features in the proposed Hybrid Deep-Learning-Based Network Intrusion Detection System (HDLNIDS). Experiments are conducted using publicly accessible benchmark CICIDS-2018 data, to determine the effectiveness of the proposed system. The findings of the research demonstrate that the proposed HDLNIDS outperforms current intrusion detection approaches with an average accuracy of 98.90% in detecting malicious attacks.
Full article
►▼
Show Figures
Open AccessArticle
Towards the Integration of Security Practices in Agile Software Development: A Systematic Mapping Review
by
Yolanda Valdés-Rodríguez, Jorge Hochstetter-Diez, Jaime Díaz-Arancibia and Rodrigo Cadena-Martínez
Cited by 9 | Viewed by 7044
Abstract
Software development must be based on more than just the experience and capabilities of your programmers and your team. The importance of obtaining a quality product lies in the risks that can be exploited by software vulnerabilities, which can jeopardize organizational assets, consumer
[...] Read more.
Software development must be based on more than just the experience and capabilities of your programmers and your team. The importance of obtaining a quality product lies in the risks that can be exploited by software vulnerabilities, which can jeopardize organizational assets, consumer confidence, operations, and a broad spectrum of applications. Several methods, techniques, and models have been suggested and developed to address software security. However, only a few have solid evidence for creating secure software applications. The main objective of this paper is to survey the literature for methods or models suitable for considering the integration of security in all or some of the phases of the software development life cycle and which ones are most considered or neglected. This study represents the beginning of research to generate a methodology that integrates security practices in agile software development, allowing inexperienced developers to create more secure applications.
Full article
►▼
Show Figures
Open AccessArticle
Combining SABSA and Vis4Sec to the Process Framework IdMSecMan to Continuously Improve Identity Management Security in Heterogeneous ICT Infrastructures
by
Daniela Pöhn, Sebastian Seeber and Wolfgang Hommel
Cited by 1 | Viewed by 2127
Abstract
Identity management ensures that users have appropriate access to resources, such as ICT services and data. Thereby, identity management does not only identify, authenticate, and authorize individuals, but also the hardware devices and software applications which the users need for access. In consequence,
[...] Read more.
Identity management ensures that users have appropriate access to resources, such as ICT services and data. Thereby, identity management does not only identify, authenticate, and authorize individuals, but also the hardware devices and software applications which the users need for access. In consequence, identity management is an important element of information security management (ISM) and data governance. As ICT infrastructures are constantly changing, and new threats emerge, identity management has to be continuously improved, just like any other business process. In order to align the identity management process with business requirements, and provide a systematic approach supported by reporting and supporting visualizations, we apply Sherwood Applied Business Security Architecture (SABSA) and Visualization for Security (Vis4Sec) together in our approach, IdMSecMan (identity management security management). We first introduce IdMSecMan, before applying it to the central technical process activities of identification, authentication, and authorization. Our approach is underlined by a case study. Thereby, we, for example, see that enabling multi-factor authentication in organizations impacts other areas that may be overlooked without a structured approach. With IdMSecMan, we provide a process framework to align all decisions and to constantly improve identity management within organizations and inter-organizational collaborations.
Full article
►▼
Show Figures
Open AccessArticle
MASISCo—Methodological Approach for the Selection of Information Security Controls
by
Mauricio Diéguez, Carlos Cares, Cristina Cachero and Jorge Hochstetter
Cited by 3 | Viewed by 2413
Abstract
As cyber-attacks grow worldwide, companies have begun to realize the importance of being protected against malicious actions that seek to violate their systems and access their information assets. Faced with this scenario, organizations must carry out correct and efficient management of their information
[...] Read more.
As cyber-attacks grow worldwide, companies have begun to realize the importance of being protected against malicious actions that seek to violate their systems and access their information assets. Faced with this scenario, organizations must carry out correct and efficient management of their information security, which implies that they must adopt a proactive attitude, implementing standards that allow them to reduce the risk of computer attacks. Unfortunately, the problem is not only implementing a standard but also determining the best way to do it, defining an implementation path that considers the particular objectives and conditions of the organization and its availability of resources. This paper proposes a methodological approach for selecting and planning security controls, standardizing and systematizing the process by modeling the situation (objectives and constraints), and applying optimization techniques. The work presents an evaluation of the proposal through a methodology adoption study. This study showed a tendency of the study subjects to adopt the proposal, perceiving it as a helpful element that adapts to their way of working. The main weakness of the proposal was centered on ease of use since the modeling and resolution of the problem require advanced knowledge of optimization techniques.
Full article
►▼
Show Figures
Open AccessEditor’s ChoiceArticle
A Deep Learning Method for Lightweight and Cross-Device IoT Botnet Detection
by
Marta Catillo, Antonio Pecchia and Umberto Villano
Cited by 19 | Viewed by 4000
Abstract
Ensuring security of Internet of Things (IoT) devices in the face of threats and attacks is a primary concern. IoT plays an increasingly key role in cyber–physical systems. Many existing intrusion detection systems (IDS) proposals for the IoT leverage complex machine learning architectures,
[...] Read more.
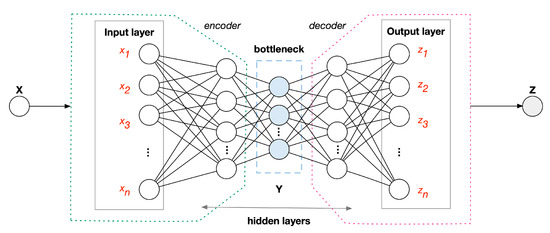
Ensuring security of Internet of Things (IoT) devices in the face of threats and attacks is a primary concern. IoT plays an increasingly key role in cyber–physical systems. Many existing intrusion detection systems (IDS) proposals for the IoT leverage complex machine learning architectures, which often provide one separate model per device or per attack. These solutions are not suited to the scale and dynamism of modern IoT networks. This paper proposes a novel IoT-driven cross-device method, which allows learning a single IDS model instead of many separate models atop the traffic of different IoT devices. A semi-supervised approach is adopted due to its wider applicability for unanticipated attacks. The solution is based on an all-in-one deep autoencoder, which consists of training a single deep neural network with the normal traffic from different IoT devices. Extensive experimentation performed with a widely used benchmarking dataset indicates that the all-in-one approach achieves within 0.9994–0.9997 recall, 0.9999–1.0 precision, 0.0–0.0071 false positive rate and 0.9996–0.9998 F1 score, depending on the device. The results obtained demonstrate the validity of the proposal, which represents a lightweight and device-independent solution with considerable advantages in terms of transferability and adaptability.
Full article
►▼
Show Figures
Open AccessSystematic Review
The eIDAS Regulation: A Survey of Technological Trends for European Electronic Identity Schemes
by
Amir Sharif, Matteo Ranzi, Roberto Carbone, Giada Sciarretta, Francesco Antonio Marino and Silvio Ranise
Cited by 12 | Viewed by 5439
Abstract
The eIDAS regulation aims to provide an interoperable European framework to enable EU citizens to authenticate and communicate with services of other Member States by using their national electronic identity. While a number of high-level requirements (e.g., related to privacy and security) are
[...] Read more.
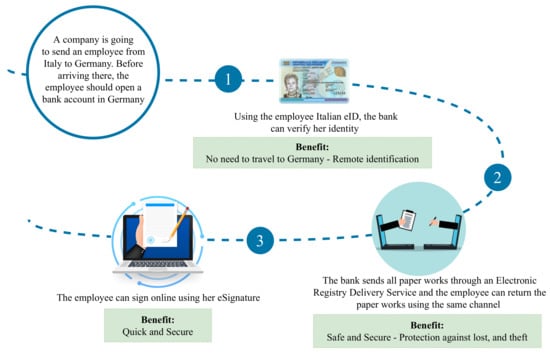
The eIDAS regulation aims to provide an interoperable European framework to enable EU citizens to authenticate and communicate with services of other Member States by using their national electronic identity. While a number of high-level requirements (e.g., related to privacy and security) are established to make interoperability among Member States possible, the eIDAS regulation does not explicitly specify the technologies that can be adopted during the development phase to meet the requirements as mentioned earlier. To the best of our knowledge, there is no work available in the literature investigating the technological trends within the notified eIDAS electronic identity schemes used by Member States. To fill this gap, this paper analyzes how the different technological trends of notified schemes satisfy the requirements of the eIDAS regulation. To do this, we define a set of research questions that allow us to investigate the correlations between different design dimensions such as security, privacy, and usability. Based on these findings, we provide a set of lessons learned that would be valuable to the security community, as they can provide useful insights on how to more efficiently protect interoperable national digital identities. Furthermore, we provide a brief overview regarding the new eIDAS regulation (eIDAS 2.0) that aims to provide a more privacy-preserving electronic identity solution by moving from a centralized approach to a decentralized one.
Full article
►▼
Show Figures
Open AccessArticle
Towards Explainable Quantum Machine Learning for Mobile Malware Detection and Classification
by
Francesco Mercaldo, Giovanni Ciaramella, Giacomo Iadarola, Marco Storto, Fabio Martinelli and Antonella Santone
Cited by 14 | Viewed by 3044
Abstract
Through the years, the market for mobile devices has been rapidly increasing, and as a result of this trend, mobile malware has become sophisticated. Researchers are focused on the design and development of malware detection systems to strengthen the security and integrity of
[...] Read more.
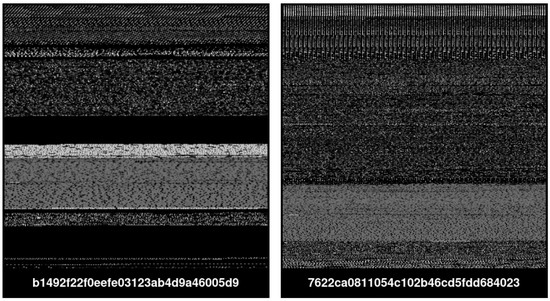
Through the years, the market for mobile devices has been rapidly increasing, and as a result of this trend, mobile malware has become sophisticated. Researchers are focused on the design and development of malware detection systems to strengthen the security and integrity of sensitive and private information. In this context, deep learning is exploited, also in cybersecurity, showing the ability to build models aimed at detecting whether an application is Trusted or malicious. Recently, with the introduction of quantum computing, we have been witnessing the introduction of quantum algorithms in Machine Learning. In this paper, we provide a comparison between five state-of-the-art Convolutional Neural Network models (i.e., AlexNet, MobileNet, EfficientNet, VGG16, and VGG19), one network developed by the authors (called Standard-CNN), and two quantum models (i.e., a hybrid quantum model and a fully quantum neural network) to classify malware. In addition to the classification, we provide explainability behind the model predictions, by adopting the Gradient-weighted Class Activation Mapping to highlight the areas of the image obtained from the application symptomatic of a certain prediction, to the convolutional and to the quantum models obtaining the best performances in Android malware detection. Real-world experiments were performed on a dataset composed of 8446 Android malicious and legitimate applications, obtaining interesting results.
Full article
►▼
Show Figures
Open AccessArticle
Evaluation of Survivability of the Automatically Obfuscated Android Malware
by
Himanshu Patel, Deep Patel, Jaspreet Ahluwalia, Vaishali Kapoor, Karthik Narasimhan, Harmanpreet Singh, Harmanjot Kaur, Gadi Harshitha Reddy, Sai Sushma Peruboina and Sergey Butakov
Cited by 3 | Viewed by 2444
Abstract
Malware is a growing threat to all mobile platforms and hundreds of new malicious applications are being detected every day. At the same time, the development of automated software obfuscation techniques allows for the easy production of new malware variants even by attackers
[...] Read more.
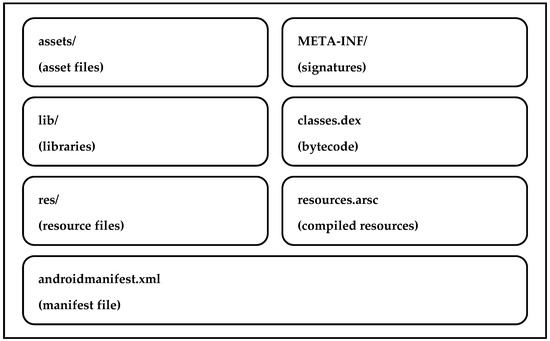
Malware is a growing threat to all mobile platforms and hundreds of new malicious applications are being detected every day. At the same time, the development of automated software obfuscation techniques allows for the easy production of new malware variants even by attackers with entry-level programming skills. Such obfuscation techniques can evade the signature-based mechanism implemented in current antimalware technology. This paper presents the results of a study that examined how automated obfuscation techniques affect malicious and benign applications by two widely used malware detection approaches, namely static and dynamic analyses. The research explored 5000 samples of malware and benign programs and evaluated the impact of automated obfuscation on Android applications. The experimental results indicated that (1) up to 73% of the reviewed applications “survived” the automated obfuscation; (2) automated obfuscation reduced the detection ratio to 65–85% depending on the obfuscation method used. These findings call for a more active use of advanced malware detection methods in commonly used antivirus platforms.
Full article
►▼
Show Figures
Open AccessArticle
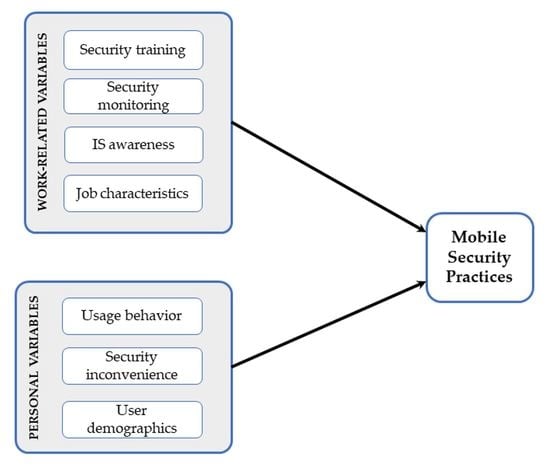
Predictors of Employees’ Mobile Security Practice: An Analysis of Personal and Work-Related Variables
by
Zauwiyah Ahmad, Thian Song Ong, Yen Wen Gan, Tze Hui Liew and Mariati Norhashim
Cited by 4 | Viewed by 2615
Abstract
Personal mobile devices form an integral part of business activities today. Mobile devices, nevertheless, pose various security issues and data privacy threats, which require a close attention. The rational choice theory was utilized to examine the determinants of employees’ security behavior in relation
[...] Read more.
Personal mobile devices form an integral part of business activities today. Mobile devices, nevertheless, pose various security issues and data privacy threats, which require a close attention. The rational choice theory was utilized to examine the determinants of employees’ security behavior in relation to mobile device usage. Employees were postulated to rationally evaluate the costs and benefits of mobile security measures and decide on the option that is perceived to provide the best expected outcome. Twelve out of thirteen hypotheses examined in this study were found to be significant. We also hypothesized that demographics and work-related variables significantly affect employees’ mobile security practices, examined using ordinal logistic regression analysis. The findings indicate the efficacy of the rational choice theory in explaining mobile security behavior. Security inconvenience has been found to be a significant cost to information security measures. Moreover, the findings also showed the influence of gender, job function, past security experience, and perceived risk on the dependent variable. In conclusion, we would like to draw considerable attention to the contribution of security awareness programs and security training to good mobile security behaviors.
Full article
►▼
Show Figures
Open AccessArticle
A Comparative Study of Web Application Security Parameters: Current Trends and Future Directions
by
Jahanzeb Shahid, Muhammad Khurram Hameed, Ibrahim Tariq Javed, Kashif Naseer Qureshi, Moazam Ali and Noel Crespi
Cited by 27 | Viewed by 10010
Abstract
The growing use of the internet has resulted in an exponential rise in the use of web applications. Businesses, industries, financial and educational institutions, and the general populace depend on web applications. This mammoth rise in their usage has also resulted in many
[...] Read more.
The growing use of the internet has resulted in an exponential rise in the use of web applications. Businesses, industries, financial and educational institutions, and the general populace depend on web applications. This mammoth rise in their usage has also resulted in many security issues that make these web applications vulnerable, thereby affecting the confidentiality, integrity, and availability of associated information systems. It has, therefore, become necessary to find vulnerabilities in these information system resources to guarantee information security. A publicly available web application vulnerability scanner is a computer program that assesses web application security by employing automated penetration testing techniques that reduce the time, cost, and resources required for web application penetration testing and eliminates test engineers’ dependency on human knowledge. However, these security scanners possess various weaknesses of not scanning complete web applications and generating wrong test results. Moreover, intensive research has been carried out to quantitatively enumerate web application security scanners’ results to inspect their effectiveness and limitations. However, the findings show no well-defined method or criteria available for assessing their results. In this research, we have evaluated the performance of web application vulnerability scanners by testing intentionally defined vulnerable applications and the level of their respective precision and accuracy. This was achieved by classifying the analyzed tools using the most common parameters. The evaluation is based on an extracted list of vulnerabilities from OWASP (Open Web Application Security Project).
Full article
►▼
Show Figures