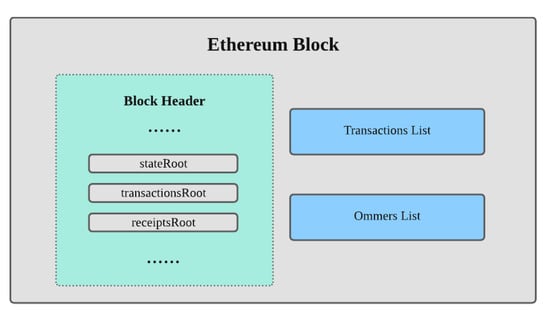
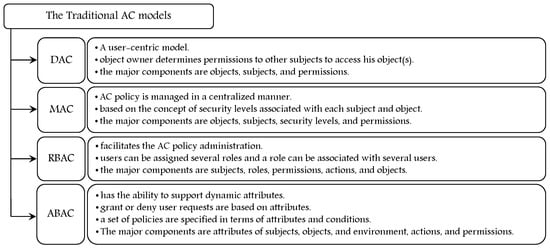
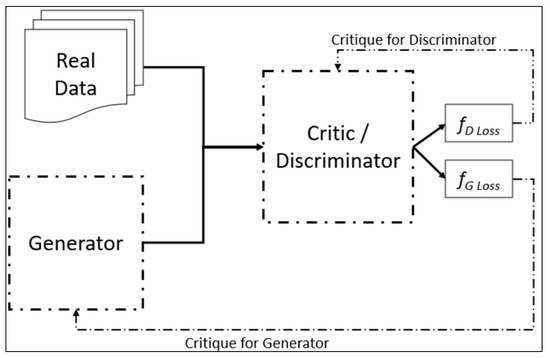
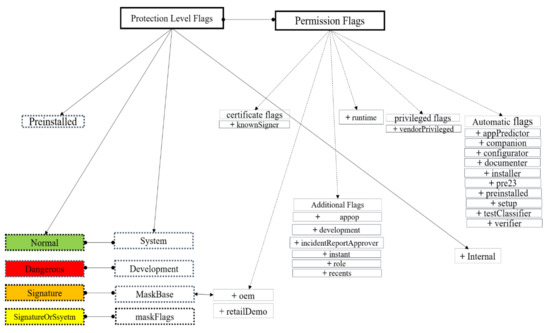
Intelligent Security and Privacy Approaches against Cyber Threats
A topical collection in Journal of Cybersecurity and Privacy (ISSN 2624-800X). This collection belongs to the section "Security Engineering & Applications".
Viewed by 309338Editor
Interests: intrusion detection; threat intelligence; privacy preservation; digital forensics; machine/deep learning; network systems; IoT; cloud
Special Issues, Collections and Topics in MDPI journals
Topical Collection Information
Dear Colleagues,
As many organizations have moved to work from home, cyber attackers have expanded their advanced persistent threats (APT), such as phishing, spear-phishing and zero-day attacks, to exploit vulnerabilities of home networks. It is urgent to develop well-designed privacy security approaches, algorithms, protocols, standards and policies for safeguarding home and organization networks against new cyber threats.
The reason for this challenge is that the policy of Bring your Own device (BYOD) allows individuals to use various Internet of Things (IoT) devices, operating systems and tools, which are different in the settings of security and privacy. The technical and humanized practices of ‘Security-Based Organization’ and ‘Security-Based Home’ will enrich individuals' knowledge for protecting their home networks and securing their organizations’ assets. ‘Security-Based Organization’ denotes that organizations often provide security services and tools and training to employees with less effort from the employees and high visibility of security services, while ‘Security-Based Home’ denotes that individuals need new cyber practices which adapt security to home networks. The transition to work from home needs new security and privacy models that would employ Artificial Intelligence (AI), blockchain, human factor models, cognitive models. and secure big data analytics to secure home networks and safeguard organization assets.
Topics of interest include but are not limited to:
- Intelligent security practices and model-based AI against COVID-19 threats;
- Privacy-enabled human factor models against COVID-19 cyberattacks;
- AI-based Intrusion Detection Systems for discovering COVID-19 cyberattacks;
- AI-based cognitive models against COVID-19 cyberattacks;
- Privacy-driven human analytical behaviours in home networks;
- Privacy-preserving algorithms and approaches for protecting data of home networks;
- Secure Big Data analytics to analyze heterogeneous IoT and home elements;
- Secure and distributed semantic techniques for modeling home networks;
- Blockchain technologies for trusting home and organization systems and networks;
- Threat intelligence for pivoting COVID-19 cyber-attacks.
Dr. Nour Moustafa
Guest Editor
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the collection website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Journal of Cybersecurity and Privacy is an international peer-reviewed open access quarterly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript. The Article Processing Charge (APC) for publication in this open access journal is 1000 CHF (Swiss Francs). Submitted papers should be well formatted and use good English. Authors may use MDPI's English editing service prior to publication or during author revisions.
Keywords
- security
- privacy
- artificial intelligence
- intrusion detection
- human factors
- privacy preservation