Dependable and Secure Voting Mechanism in Edge Computing
Abstract
:1. Introduction
2. Related Work
3. System
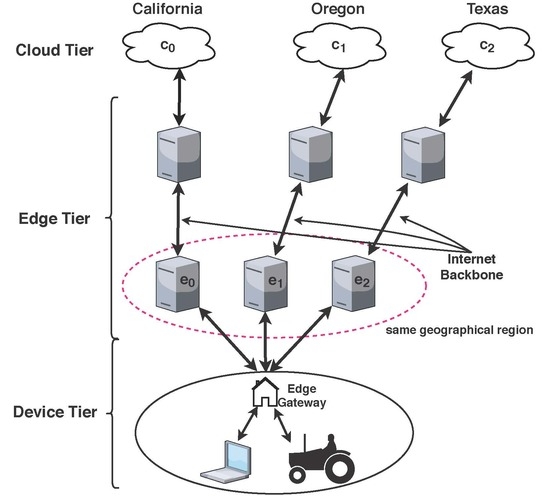
3.1. Architecture
3.2. System Model
3.2.1. Algorithm
- Voting: All correct processes must terminate with single value v.
- Agreement: All correct processes must choose the same value v.
- Termination: Processing or communication delays are bounded to a value .
3.2.2. Client
3.2.3. Edge Node
4. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Singh, S.; Jeong, Y.S.; Park, J.H. A Survey on Cloud Computing Security. J. Netw. Comput. Appl. 2016, 75, 200–222. [Google Scholar] [CrossRef]
- Persico, V.; Botta, A.; Montieri, A.; Pescape, A. A First Look at Public-Cloud Inter-Datacenter Network Performance. In Proceedings of the IEEE Global Communications Conference, Washington, DC, USA, 4–8 December 2016; pp. 1–7. [Google Scholar]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Solutions, I. IoT Transforming the Future of Agriculture. 2019. Available online: https://www.iotsworldcongress.com/iot-transforming-the-future-of-agriculture/ (accessed on 13 December 2019).
- Rani, B.K.; Rani, B.P.; Babu, A.V. Cloud Computing and Inter-Clouds—Types, Topologies and Research Issues. Procedia Comput. Sci. 2015, 50, 24–29. [Google Scholar] [CrossRef] [Green Version]
- Horwitz, L. Can Smart City Infrastructure Alleviate the Strain of City Growth? Available online: https://www.cisco.com/c/en/us/solutions/internet-of-things/smart-city-infrastructure.html (accessed on 13 December 2019).
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X. Security and Privacy in Smart City Applications: Challenges and Solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Tang, B.; Chen, Z.; Hefferman, G.; Wei, T.; He, H.; Yang, Q. A Hierarchical Distributed Fog Computing Architecture for Big Data Analysis in Smart Cities. In Proceedings of the ASE Big Data & Social Informatics 2015, Kaohsiung, Taiwan, 7–9 October 2015. [Google Scholar]
- Ogino, T.; Kitagami, S.; Shiratori, N. A multi-agent based flexible IoT edge computing architecture and application to ITS. Int. J. Netw. Comput. 2019, 14, 47–52. [Google Scholar] [CrossRef]
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine Generals Problem. ACM Trans. Program. Lang. Syst. 1982, 4, 382–401. [Google Scholar] [CrossRef] [Green Version]
- Sousa, J.; Bessani, A.; Vukolic, M. A Byzantine Fault-Tolerant Ordering Service for the Hyperledger Fabric Blockchain Platform. In Proceedings of the 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Luxembourg, 25–28 June 2018; pp. 51–58. [Google Scholar] [CrossRef] [Green Version]
- Infosec Institute. Security Issues in Edge Computing and the IoT. Available online: https://resources.infosecinstitute.com/security-issues-in-edge-computing-and-the-iot (accessed on 23 August 2018).
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, Fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef] [Green Version]
- Meza, J.; Wu, Q.; Kumar, S.; Mutlu, O. Revisiting Memory Errors in Large-Scale Production Data Centers: Analysis and Modeling of New Trends from the Field. In Proceedings of the IEEE/IFIP 45th International Conference on Dependable Systems and Networks, Rio de Janeiro, Brazil, 22–25 June 2015; pp. 415–426. [Google Scholar]
- Nightingale, E.B.; Douceur, J.R.; Orgovan, V. Cycles, Cells and Platters: An Empirical Analysisof Hardware Failures on a Million Consumer PCs. In Proceedings of the 6th Conference on Computer Systems (EuroSys), Salzburg, Austria, 10–13 April 2011; pp. 343–356. [Google Scholar] [CrossRef]
- Schroeder, B.; Pinheiro, E.; Weber, W.D. DRAM Errors in the Wild: A Large-scale Field Study. In Proceedings of the 11th International Joint Conference on Measurement and Modeling of Computer Systems, Seattle, WA, USA, 15–19 June 2009; pp. 193–204. [Google Scholar] [CrossRef]
- Cloud Security Alliance. Cloud Security Alliance Warns Providers of ‘The Notorious Nine’ Cloud Computing Top Threats in 2013. Available online: https://cloudsecurityalliance.org/articles/ca-warns-providers-of-the-notorious-nine-cloud-computing-top-threats-in-2013/ (accessed on 25 February 2013).
- Chen, A. GCreep: Google Engineer Stalked Teens, Spied on Chats. Available online: http://gawker.com/5637234/gcreep-google-engineer-stalked-teens-spied-on-chats (accessed on 13 December 2019).
- Kandias, M.; Virvilis, N.; Gritzalis, D. The Insider Threat in Cloud Computing. In Critical Information Infrastructure Security; Springer: Berlin/Heidelberg, Germany, 2013; Volume 6983, pp. 93–103. [Google Scholar] [CrossRef]
- Whittaker, Z. It Was a Really Bad Month for the Internet. Available online: https://techcrunch.com/2019/07/05/bad-month-for-the-internet/ (accessed on 13 December 2019).
- Ha, K.; Chen, Z.; Hu, W.; Richter, W.; Pillai, P.; Satyanarayanan, M. Towards Wearable Cognitive Assistance. In Proceedings of the 12th Annual International Conference on Mobile Systems, Applications, and Services, Bretton Woods, NH, USA, 16–19 June 2014; pp. 68–81. [Google Scholar]
- Chun, B.G.; Ihm, S.; Maniatis, P.; Naik, M.; Patti, A. CloneCloud: Elastic execution between mobile device and cloud. In Proceedings of the Sixth Conference on Computer Systems, Salzburg, Austria, 10–13 April 2011. [Google Scholar]
- Wang, Q.; Lee, B.; Murray, N.; Qiao, Y. MR-IoT: An information centric MapReduce framework for IoT. In Proceedings of the 15th IEEE Annual Consumer Communications Networking Conference, Las Vegas, NV, USA, 12–15 January 2018; pp. 1–6. [Google Scholar]
- Javed, A.; Heljanko, K.; Buda, A.; Främling, K. CEFIoT: A fault-tolerant IoT architecture for edge and cloud. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 813–818. [Google Scholar]
- Hao, Z.; Yi, S.; Li, Q. EdgeCons: Achieving Efficient Consensus in Edge Computing Networks. In Proceedings of the USENIX Workshop on Hot Topics in Edge Computing, Boston, MA, USA, 10 July 2018. [Google Scholar]
- Stanciu, A. Blockchain Based Distributed Control System for Edge Computing. In Proceedings of the 21st International Conference on Control Systems and Computer Science, Bucharest, Romania, 29–31 May 2017; pp. 667–671. [Google Scholar] [CrossRef]
- Vukolić, M. The Quest for Scalable Blockchain Fabric: Proof-of-Work vs. BFT Replication. In Proceedings of the International Workshop on Open Problems in Network Security, Zurich, Switzerland, 29 October 2015; Volume LNCS-9591, pp. 112–125. [Google Scholar]
- Decker, C.; Seidel, J.; Wattenhofer, R. Bitcoin Meets Strong Consistency. In Proceedings of the 17th International Conference on Distributed Computing and Networking, Singapore, 4–7 January 2016; pp. 1–10. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance and Proactive Recovery. ACM Trans. Comput. Syst. 2002, 20, 398–461. [Google Scholar] [CrossRef]
- Kotla, R.; Alvisi, L.; Dahlin, M.; Clement, A.; Wong, E. Zyzzyva: Speculative Byzantine Fault Tolerance. In Proceedings of the Twenty-First ACM Symposium on Operating Systems Principles, Stevenson, WA, USA, 14–17 October 2007; pp. 45–58. [Google Scholar]
- Rouse, M. Multi-Cloud Strategy. Available online: https://searchcloudcomputing.techtarget.com/definition/multi-cloud-strategy (accessed on 13 December 2019).
- Costa, P.A.; Ramos, F.M.; Correia, M. On the Design of Resilient Multicloud MapReduce. IEEE Cloud Comput. 2018, 4, 74–82. [Google Scholar] [CrossRef]
- Verissimo, P.; Lung, L.C.; Bessani, A.N.; Correia, M.; Veronese, G.S. Efficient Byzantine Fault-Tolerance. IEEE Trans. Comput. 2013, 62, 16–30. [Google Scholar]
- Bessani, A.; Sousa, J.; Alchieri, E.E.P. State Machine Replication for the Masses with BFT-SMART. In Proceedings of the 44th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Atlanta, GA, USA, 23–26 June 2014; pp. 355–362. [Google Scholar]





© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Costa, P.A.R.S.; Beko, M. Dependable and Secure Voting Mechanism in Edge Computing. Future Internet 2019, 11, 262. https://doi.org/10.3390/fi11120262
Costa PARS, Beko M. Dependable and Secure Voting Mechanism in Edge Computing. Future Internet. 2019; 11(12):262. https://doi.org/10.3390/fi11120262
Chicago/Turabian StyleCosta, Pedro A.R.S., and Marko Beko. 2019. "Dependable and Secure Voting Mechanism in Edge Computing" Future Internet 11, no. 12: 262. https://doi.org/10.3390/fi11120262
APA StyleCosta, P. A. R. S., & Beko, M. (2019). Dependable and Secure Voting Mechanism in Edge Computing. Future Internet, 11(12), 262. https://doi.org/10.3390/fi11120262