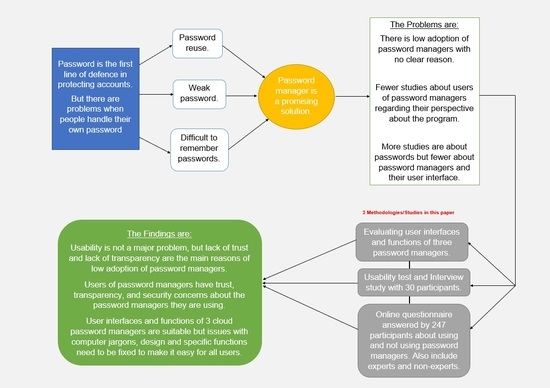
The online questionnaire was completed by 247 participants. We found that 43% of our respondents were 26–35 years old, 25% were 36–45 years old and 22% were 18–25 years old. Also, 2% were between the ages of 56 and 65 years while only 2 participants were 66 years of age or older. The highest level of education for our participants varies, the majority of participants are undergraduates (41%, 101 participants), followed by those with a master’s (32%, 78 participants) or a PhD (11%, 28 participants), while the rest of the responses came from participants with secondary school education and some college. So, most of the participants are well-educated.
As seen above, we found that experts have more online accounts and passwords than non-experts and the difference is significant while there was no significant difference between the two groups in adopting a password manager. So, having educational background related to computer science or information security plays a role in mitigating password reuse.
4.3.1. Non-Users of Password Managers
In this study, there are 134 non-users of password managers, of which 68 (51%) participants have no educational background in computer science or information security (non-experts), whereas 66 (49%) participants do have an educational background related to computer science or information security, so we classified them as experts. Actually, expert participants are expected to adopt password managers because of their higher skills and knowledge of computer science than non-experts, yet, many stated that they did not use a password manager. The vast majority of non-users of password managers are well-educated, 41% of participants have a bachelor’s degree, followed by 31% with a master’s and 13% with a PhD. Also, 40% of non-users are aged 26–35 years, 28% are 36–45 years old while 21% are between the ages of 18 and 25 years.
To understand why this group of participants were not using password managers, a list of 13 options (
Table 20) was provided to them so that they could choose the reasons that applied to them or they could state their own reasons (they must choose at least one reason from the list or write a reason of their own). The reasons are related to the usability of password managers, trust, transparency and security. When we asked non-user participants about their reasons for not using a password manager, most of the reasons that were chosen related to trust issues, followed by security and transparency issues.
The reasons most selected by non-users participants related to trust issue, as 41.8% chose “I do not trust the vendor of a password manager to store my passwords” and 41.8% chose “I do not trust the browser extension of a password manager to fill in my passwords”. Other reasons related to a lack of transparency in password managers, as 38.1% of non-users chose “I do not know where my passwords will be stored in a password manager”, while 22.4% selected “I do not know how my online passwords will be processed in a password manager.” Other participants chose reasons related to security concerns, as 35.8% chose “all my passwords will be leaked, if the database of a password manager is hacked” and 26.1% chose “If the master password is compromised/stolen, all my passwords will be exposed”.
From the results, the main reason selected by non-user participants is that they do not use a password manager because they do not trust the browser extension or the vendor of a password manager, which means that non-user participants have trust issues regarding password managers. Similarly, non-users do not trust password managers to delete passwords permanently from databases. Another reason for not using a password manager is related to a lack of transparency, as non-user participants stated that they do not use a password manager because they do not know where passwords will be stored, and they do not know how passwords are processed in the database of a password manager. One more issue is that 20% of participants do not want to use password managers because passwords will be synchronized through the vendor’s service.
Furthermore, many non-user participants have concerns about the security of the database of a password manager, which means that relying on a password manager to protect passwords can be risky. Non-users have concerns about the master password, because compromising the master password means all stored passwords may fall into the wrong hands. Similarly, 24.6% of non-user participants stated that other people who use the same shared computer could log in to their own password manager account. A tenth reason that causes non-users not to use a password manager is related to the availability of their stored passwords, because they will not be able to access stored passwords if a password manager fails to work (29.1%).
Importantly, the last reasons chosen by non-user participants from the list are related to usability, as only 14.9% chose “it is difficult to use a password manager” while 17.9% selected “it is difficult to recover the account if I forget the master password”. These results show that non-user participants did not mainly abstain from using a password manager because of usability issues but rather due to trust issues, followed by a lack of transparency and security concerns toward password managers. However, only four non-user participants (non-experts) stated that they do not know what a password manager is, while one participant said that they could not be bothered to put in the work to make it happen. Overall, the reasons most chosen by experts and non-experts are related to trust when compared to security and transparency, while reasons related to usability were chosen least by both groups. Thus, we identified the reasons for the low adoption rate of password managers in numbers and percentages (
Table 20).
To determine if having an education related to computer science or information security is an important factor in abstaining from using password managers for 66 expert non-users and 68 non-expert non-users (for choosing and not choosing 13 reasons), we performed an analysis using a Pearson Chi-Square test (
Table 20). We found that there were no significant differences between expert non-users and non-expert non-users for 11 reasons as
p-values were greater than 0.05. For example, “I do not trust the browser extension to fill in my passwords” was chosen by 30 experts and 26 non-experts, and there was no significant difference between both groups for choosing/not choosing this reason X2 (1, n = 134) = 0.718,
p = 0.397.
On the other hand, there were only two reasons out of 13 for which expert non-users selected them more than non-expert non-users; there are 38 experts compared to 18 non-experts who do not trust the vendors of password managers to store passwords, and the difference is significant X2 (1, n = 134) = 13.321, p < 0.001. Furthermore, there are 30 experts compared to 18 non-experts who fear that their passwords will be leaked if the database of the password manager is hacked, and the difference between both groups is significant X2 (1, n = 134) = 5.250, p< 0.022. Therefore, we can see that having an education related to computer science or information security only plays a minor role in not using password managers.
In addition, to see which category was selected the most by non-user participants, every three reasons were grouped in a category (
Table 21) and a McNemar test was used to see if there was any significant difference between these categories. It is important to note that participants who chose a reason from both categories were excluded, for example, usability and trust, so only non-user participants who chose reasons from one category were counted. For example, if a non-user selected 1–3 reasons from the “usability category” but none from the “trust category”, then the result of this non-user participant would be counted. A McNemar test was used as it only counts participants who selected options from one category and eliminates those who selected options from both categories.
The results show that there was a significant difference between the usability and trust categories, as shown by the McNemar exact p-value < 0.001 and test statistic = 26.30. (61 non-user participants chose only trust reasons and 16 participants only chose usability reasons, 25 participants who chose from both categories were excluded, while 32 participants did not choose from trust or usability category). Likewise, there was a significant difference between the usability and transparency categories as shown by the McNemar exact p-value < 0.001 and test statistic = 14.06 (47 participants chose only transparency reasons, 17 chose only usability, 24 participants who chose from both categories were excluded, while 46 participants did not choose from transparency or usability category). It was found that there was a significant difference between the usability and security categories as shown by the McNemar exact p-value < 0.001 and test statistic = 14.78 (48 participants chose only security reasons, 17 participants chose only usability reasons, 24 participants who chose from both categories were excluded, while 45 participants did not choose from security or usability category). The findings show that usability is not the main reason for not a using password manager, rather it is the trust issue followed by transparency and security.
We also used a McNemar test to see if there was any significant difference between the trust, transparency and security categories. We found that there were no significant differences between the trust, transparency and security categories as the McNemar exact p-value was greater than 0.05. There was no significant difference between the trust and transparency categories as shown by the McNemar exact p-value = 0.063 and test statistic = 3.947 (36 participants chose only trust reasons, 21 chose only transparency, 50 participants who chose from both categories were excluded, while 27 participants did not choose from transparency or usability category). There was no significant difference between trust and security categories as McNemar exact p-value = 0.059 and test statistic = 4.083 (31 participants chose only trust reasons, 17 chose only security, 55 participants who chose from both categories were excluded, while 31 participants did not choose from transparency or usability category). There was a similar finding between the security and transparency categories as shown by the McNemar exact p-value = 1.000 and test statistic = 0.021 (24 participants chose only security reasons, 23 chose only transparency, 48 participants who chose from both categories were excluded, while 39 participants did not choose from transparency or usability category).
As seen above, when we compare between the four categories, we found that the most selected category is trust which implies that trust issue is a major problem that makes people not to use a password manager. It is followed by transparency and security categories as both categories have a similar number of selected times, yet, they were not selected as many as trust category. Also, we found that fewer non-user participants selected usability reasons (category) when compared with trust, transparency and security categories, therefore we can see that usability is only a minor issue for non-users. Moreover, we found that the difference between usability category and the other three categories (trust, transparency and security) is significant. However, we found no significant difference between trust, transparency and security category, yet, trust were selected the most by non-users.
Few non-user participants made a few comments regarding their reasons for not using a password manager. One participant said that they wanted to log in from any other machine without a password manager, another participant said they already use a simpler and more secure system while one non-user had never considered using a password manager because of believing that their passwords will not be obtained by anyone else.
We found interesting findings regarding non-users, trust reasons were the most chosen by non-users for not using password managers as they do not trust the vendor to store passwords. Followed by reasons related to lack of transparency as many non-users do not know where passwords are stored and how password managers process them. Also, non-users chose reasons that related to security such as passwords could be leaked from database because of an attack. Interestingly, we found that the least chosen reasons by non-users were related to usability which implies that usability is only a minor issue while trust, security and transparency are major issues which lead to the low adoption of password managers. Importantly, in regard to the difference between expert non-users and non-expert non-users, we only found a significant difference between them in 2 reasons out of 13 reasons. So, having an educational background related to computer science or information security only plays a minor factor in not using password managers.
4.3.2. Users of Password Managers
In this study, there are 113 users of password managers, of which 62 (55%) user participants have an educational background related to computer science or information security (experts), while 51 (45%) user participants have different educational backgrounds not related to computer science or information security (non-experts). The results show that more expert users use a password manager compared to non-expert users. The vast majority of users (82%) are well-educated, as 41% have a bachelor’s degree, 32% have a master’s and 9% are PhD holders. Regarding users’ ages, 46% of users are aged 26–35 years, 20% are 36–45 years old and 24% are between the ages of 18 and 25 years. The user participants use password managers on different operating systems, 84 users use Windows, followed by Android (53 users), iOS (50 users), Mac OS (40 users) and Linux (10 users).
We asked 113 user participants about the password manager they use (
Table 22). By far, the most used password manager is Chrome (46%), it is followed by cloud password managers LastPass (20%) and 1Password (9%). The results imply that more user participants adopt browser-based password managers such as Chrome rather than cloud-based password managers such as LastPass. The reasons might be related to the simplicity and ease of access to browsers compared to cloud-based password managers, which require installing a separate app and browser extension to use them. LastPass is the second most used, while it ranked first among other cloud-based password managers in this study. As seen in
Table 22, a few more non-expert users than expert users use Chrome, while more experts use LastPass than non-experts. But eight experts use 1Password compared to two non-experts, while all KeePass users are experts, which implies that experts are more aware of cloud-based password managers and KeePass compared to non-experts.
We asked our user participants if they store all their passwords in the password manager they use; 58% of users do not store all their passwords, while 42% users do store all their passwords. The results shows that most of the users in this study only store some passwords online. With regard to experts and non-experts (
Table 23), we found that 28 experts store all their passwords while 34 experts store some passwords. Nineteen non-experts store all their passwords while 32 non-experts store some passwords. To see if there was any difference between experts and non-experts in storing passwords in password managers, we used a Pearson Chi-Square test. We found that there was no significant difference between experts and non-experts in storing passwords in password managers X2 (1, n = 113) = 0.720,
p = 0.396.
To find out in which password managers users store all their passwords, we analyzed the most used password managers. Thirty-four (65%) users of Chrome do not store all their passwords while only 18 (35%) users do store all their passwords. LastPass users who store all their passwords number 11 (48%), while 12 users (52%) only store some passwords. Similarly, six users of 1Password store some passwords while four users store all their passwords. There are three Safari users, three Dashlane and three Apple users who store some passwords, whereas three users of KeePass store all their passwords.
Furthermore, we asked the user participants if they use a random password generator to generate a password for each account (
Table 24). Half of the users (51%) do not use a random password generator, 20% only use a random generator for specific accounts, while 29% use a random password generator for each account. This finding shows that half of the user participants do not use a random password generator for each account although it is offered within the tool. In regard to experts and non-experts, we found that 22 expert users use a random password generator for each account while 28 experts do not use them. Among non-experts, only 11 non-experts use a random password generator for each account while 29 non-experts do not use them. Using a Pearson Chi-Square test, we found that no significant difference between experts and non-experts as regards using a random password generator X2 (2, n = 113) = 2.682,
p = 0.262.
In detail, we found that eight users of 1Password use a random password generator for each account. For LastPass, 12 users use a random password generator for each account, five users only use one for specific accounts while 6 users of LastPass do not use them. Chrome users use random password generators the least as 37 users do not use them while only seven users use a random password generator for each account. From these results, the random password generators of LastPass and 1Password are the most used among all password managers, as they can help to mitigate password reuse and weak passwords. On the other hand, the majority of users who use a browser password manager, for example, in Chrome, do not use a random generator or only use one for specific accounts.
More on this point, we asked user participants who do not use a random password generator to answer another question about their reasons for not using a random password generator; 19% of users did not know how to use a random password generator while 42% did not know that a password manager offers a built-in random password generator. Other users reported many different reasons, 19% said it is hard and complex to remember and type, 7% prefer to create passwords by themselves that are memorable, 5% stated “in case I cannot access the manager” and “I do not feel safe” and 3% reported that “I have never thought about it”.
Moreover, we asked our user participants “Why are you using a password manager?” We found that 46% of users use password managers to store passwords because they cannot remember all their passwords, followed by 26% of users who said it is easy to log in and quick to get access. Only 17% of users use password managers because they are secure and protect their passwords. Also, 7% of users use password managers to generate a unique password for each account and to avoid reuse.
To find out how easy it is to use password managers and their functions, we asked our user participants to answer 10 questions about the password managers they use. The questions are on a Likert scale of 1–5 (ranging from strongly disagree to strongly agree). As each participant has a different experience when using a password manager and some questions might not apply to them, a not applicable (N/A) option was included, for example, some user participants may have never used a password manager on multiple devices. In this part, we analyzed different password managers which are browser-based (Chrome), cloud-based (LastPass and 1Password) and open source (KeePass) in
Table 25.
We found that all users of LastPass and KeePass and nine users of 1Password found it easy to create an account. Likewise, all users of KeePass and 1Password and 22 users of LastPass found it easy to store online passwords. Also, all users of KeePass, nine users of 1Password and 20 users of LastPass found it easy to use the program. The answers to the three questions indicate that those users of password managers found it easy to use the programs, and to store passwords as well.
As for installing the browser extensions of LastPass, KeePass and 1Password, the vast majority of users did not find it difficult to install the browser extensions except four users of LastPass who found it difficult. The great majority of users of LastPass, 1Password and KeePass found it easy to access their passwords except for two users of LastPass and one user of 1Password who chose neutral, so none of these users found it difficult to access passwords stored in these password managers. Similarly, only two users of LastPass need help to use the program. Furthermore, most users of LastPass, 1Password and KeePass found it easy to change passwords, but a few users of each password manager found it hard to change passwords. When we asked these users about using password managers on multiple devices, 14 users of LastPass, seven users of 1Password and two users of KeePass found it easy to use the programs on multiple devices. However, a few users of LastPass and KeePass found it difficult to use the programs on multiple devices.
We asked user participants about how hard it is to reset the master password in these password managers. Eight users of LastPass and two users of 1Password and KeePass found it hard to reset the master password. However, a few users chose “not applicable” for this question, which suggests that they had never tried to reset the master password. Importantly, one of the issues with current password managers is the difficulty in recovering the account when a user forgets their master password. User participants were asked about the difficulty of recovering their account if they forgot the master password, the result is that seven LastPass users, five 1Password users and three KeePass users found it difficult to recover their account when they forgot the master password. But nine users of LastPass and a few users of 1Password and KeePass chose “not applicable”, which means they have never forgotten their master password or never tried to recover their account, so they do not know how difficult it is. It appears that current password managers are easy to use and it is easy to store passwords and access them, but these password managers still have issues regarding their use on multiple devices and recovering accounts.
With regard to 52 Chrome users, we found that the great majority of users found it easy to use and to store passwords. Similarly, 67% of Chrome users found it easy to use on multiple devices, while only 12% did not find it easy. These results indicate that Chrome is well-known and accessible. Likewise, more than half of Chrome users (65%) found it easy to access their passwords in their browsers while only 14% of users disagreed as they found it difficult. However, only 31% of Chrome users found it easy to change their passwords, 34% neither agreed nor disagreed, while 29% agreed as they found it difficult to change their passwords in Chrome. Lastly, in this part, users always worry about forgetting their master password and it is the same problem with Chrome users. Please note that, a Gmail password can be considered as a master password because it gives access to a user’s email inbox, Google drive, account and so forth [
45]. The results show that 48% of Chrome users found it difficult to recover their master password (Gmail password), while 23% disagreed as they found it easy to recover it.
Previous studies on password managers did not primarily focus on users of password managers and stored passwords. In this study, we believe that there are many users of password managers who have trust and transparency issues and security concerns as regards the password managers they use (
Table 26). Also, we wanted to find out if there was any significant difference between 62 experts and 51 non-experts via a set of questions about password managers. Please note that we used a Mann Whitney test to check for a significant difference between experts and non-experts (
Table 27).
First, we asked user participants if they knew where passwords are stored in a password manager; the findings are that 51% of users of password managers know where passwords are stored, 30% of users do not know, while 19% are not sure about the location of stored passwords. We analyzed these results in depth to discover which groups of users know more about their stored passwords. Half of Chrome and LastPass users know where their passwords are stored, while five expert users of KeePass know the place of stored passwords. However, around half of users of Chrome and LastPass, four Safari users and 4 Dashlane users are not sure or do not about the location of stored passwords.
Similarly, we asked user participants if they knew how passwords are processed in password managers; 41% of users did not know how their passwords are processed at the other end, 23% were not sure, while only 36% of users fully understood the process. So, most users (64%) do not fully understand or are not sure how their passwords are processed in password managers. This finding implies that more work needs to be done to increase the level of transparency between users and password managers regarding storing and processing passwords. In detail, we found that half of Chrome users did not know how their passwords are processed, while half of LastPass users did not know or were not sure. Shockingly, no Dashlane users knew about the process while the majority of Safari and Apple (Keychain) users did not know or were not sure about the process. In contrast, six users of 1Password and four users of KeePass knew about the process.
We asked our user participants if they felt confident to use a browser extension to fill in passwords; 65% felt confident while 10% did not feel confident to do so. However, three non-expert users chose “not applicable”, which implies that they do not use a browser extension (one Chrome, one Firefox, one Safari user). The vast majority of Chrome, LastPass and 1Password users feel confident to use a browser extension to fill in passwords, which means the browser extensions of password managers are useful for most users. One of the questions in the study is to see if users are aware of password synchronization using a vendor’s service; 72% of users were aware of this while only 9% were not aware. We found that the majority of users of Chrome, LastPass, 1Password, Dashlane, KeePass, Safari and Keychain were aware of it.
Another question is about trusting the vendors of password managers to store all passwords. We found that 51% of users of password managers trust the vendors of password managers to store all their passwords while the other half of users either do not trust them or are neutral about it. This finding is surprising as around half of users do not trust or have little trust in vendors. As a result, password managers need to be more transparent about stored passwords to gain users’ trust. In detail, we found that many users of Chrome, LastPass and 1Password trust the vendors to store all their passwords. In contrast, the other half of users of these popular password managers either do not trust them or have little trust in them. Also, three Dashlane users do not trust them while four Safari users are not sure about the vendors.
Moreover, another answer shows that users of password managers are concerned about their stored passwords; 50% of users of password managers are worried about losing all their stored passwords, while only 33% do not worry about it. The reasons for this result could be related to storing passwords in the cloud (3rd party), or to the lack of transparency as users do not see what is happening to their own passwords at the other end. In detail, we found that more than half of users of Chrome, LastPass, Safari and Dashlane were worried about losing their passwords stored in these password managers. However, a few users of KeePass were not worried about losing passwords, as all the passwords are stored locally on the machine and are under the user’s control.
Additionally, we asked user participants if they trust password managers to delete their passwords permanently from their databases. The results show that 47% of users trust password managers, on the other hand 28% do not trust them at all, while 25% of users are not sure if their passwords will be deleted permanently. These findings indicate that 53% of users have trust and transparency issues regarding password managers deleting passwords because users do not see anything at the backend, so they do not know about their deleted passwords. In detail, many users of Chrome do not trust it to delete passwords from the database or are not sure about it, while many users of all the password managers either do not trust them or not sure if their passwords will be deleted.
When we asked our user participants about writing a master password down and storing it in a safe place, 62% disagreed while only 25% stated that they write a master password down and store it in a safe place. Only five users chose “not applicable” for this question. These findings indicate that the majority of users memorize their master password and know the importance of it. Likewise, we found that 53% of users did not store their own passwords in a secondary place because they did not fear the password manager might fail to work. However, 25% of users store their own passwords in a secondary place. Most users of LastPass, 1Password, Dashlane and Safari do not store their own passwords in a secondary place. Yet, there are users of LastPass, KeePass, Dashlane and many users of Chrome who have this fear, thus they store their own passwords in another place.
Furthermore, 65% of users of password managers in this study worry that all their passwords will be exposed if their master password is compromised/stolen. This result indicates that users are aware of the importance of their master password. However, only 14% of users disagreed with this question, while three chrome users chose “not applicable”. In detail, the great majority of Chrome, LastPass, Dashlane and users of other password managers worry about having their passwords exposed if their master password is compromised.
As for whether users open their password manager account on a shared computer, 72% of them had not opened their password manager account on a shared computer, while only 17% had opened it. From this result, we know that users are aware of the risk of using a shared computer. Notably, no 1Password, Dashlane or KeePass users had opened their password manager account on a shared computer, while only a few users of Chrome and LastPass had done so, which is much fewer.
Actually, many cloud password managers such as LastPass offer features whereby a user can store passport information and bank details, the same thing with Chrome which offers google drive. Thus, we asked users if they would let a password manager store their bank details and passport information; 46% would not let a password manager store these details, while 42% would let a password manager store them. To find out which password managers are trusted by their users to store bank details and passport information, we analyzed them individually. Most LastPass and Chrome users would not store their personal information, while no Dashlane users would store their information do so. On the other hand, eight 1Password users and all KeePass users would store this information.
Looking at
Table 27, we found that there were no significant differences between 62 expert users and 51 non-expert users for 12 questions as
p-values were greater than 0.05. For example, there was no significant difference between experts and non-experts in terms of knowing the location of stored password in password manager (U = 1544.0,
p = 0.826, N = 113). Similarly, there was no significant difference between experts and non-experts in terms of trusting vendors to store all their passwords (U = 1491.5,
p = 0.590, N = 113). As seen in
Table 27, we can see that a few more non-experts know where passwords are stored in a password manager, and more of them trust the vendors of password managers to store all their passwords compared to experts. In contrast, more experts feel confident to use the browser extensions of password managers, trust password managers to delete passwords permanently and are aware of password synchronization compared to non-experts. However, the difference between expert users and non-expert users is not significant for using password managers, also for using a random password generator. Therefore, having an education related to computer science or information security does not play any important role in using password managers.
A few user participants made some comments, for example: “I only use password manager for unimportant accounts such as shopping websites”, “I store my passwords in it because it is easy to login my accounts” and “I do not know how secure the password manager is, I just use it to remember my passwords and to not type my password every time when I log in to my accounts”, and one participant wrote “I do not trust password managers, and thus I won’t store the most important passwords in password management services”.
In this part, we found that the most used password manager is the browser-based “Chrome” which may be related to the ease of access to browsers. Also, we found that more than half of users do not store all passwords in the password manager they use while half of users do not use random password generator at all. The reasons for not using random generator are that users do not know how to use it as well as they do not know password managers offer a built-in generator. Interestingly, 46% of users use password managers to store passwords while 26% use it for easy to access which indicates that most of them do not use other features. Regarding expert users and non-expert users, we found no significant difference between them in using password managers which implies that having education related to computer science or information security does not play any significant factor in using password managers.
In regard to the usability of password mangers, we found that the users in this study found password managers easy to use, easy to access and store passwords. However, many users found it difficult to recover the account when they forget the master password. So, we can see that password managers are easy to use but issue related to recovering the account should be solved. Moreover, we found that many users of password managers have security concerns about using a shared computer, worrying about losing stored passwords and the consequences of having the master password compromised. Significantly, around half of users have trust issues towards the vendor of password managers regarding storing all passwords and deleting them permanently. Similarly, many users have transparency issue with password manager regarding the place of stored passwords and the process. This finding answers the question on whether many users have the same trust issues and security concerns as non-users.