CoKnowEMe: An Edge Evaluation Scheme for QoS of IoMT Microservices in 6G Scenario
Abstract
:1. Introduction
1.1. Telecommunication Evolution and Status of 5G Deployment
1.2. Beyond 5G Networks towards 6G Revolution
1.3. 6G as a Key Enabler for Internet of Medical Things
1.4. A Complex and Dynamical Approach for a Context-Based Evaluation Model
| Reference | Year | Keywords |
|---|---|---|
| [13] | 2020 | Emergency Service, Healthcare, 5G Communications, 6G Communications, Wireless Communications, Internet of Things, Internet of Everything, Vehicular Technology, Drones, Mobile Hospital, Hospital-to-Home Services, Fire Control, Accidental Services, Natural Disaster. |
| [9] | 2020 | 6G mobile communication, 5G mobile communication, Reliability, Wireless networks, Internet of Things, Intelligent sensors. |
| [10] | 2020 | Complex systems, complex networks, networked complex system, 5G, 6G, wireless communications, wireless networks, mobile communication networks, modelling |
| [11] | 2019 | 6G mobile communication, 5G mobile communication, Market research, Wireless communication, Sensors, Wireless sensor networks. |
| [12] | 2020 | 6G, wireless communications, terahertz band, intelligent communication environments, pervasive artificial intelligence, network automation, all-spectrum reconfigurable transceivers, ambient backscatter communications, cell-free massive MIMO, Internet of NanoThings, Internet of BioNanoThings, quantum communications. |
| [8] | 2020 | 5G, 6G, artificial intelligence, automation, beyond 5G, data rate, massive connectivity, virtual reality, terahertz. |
| [16] | 2020 | Computer Science, Distributed, Parallel, Cluster Computing, Artificial Intelligence, Networking and Internet Architecture. |
| [17] | 2020 | Self-learning edge intelligence, technological framework, seamless integration, communication networks, mobile edge computing, key missing components, edge-native AI, self-supervised generative adversarial nets, potential performance improvement, automatic data learning, edge computing networks, key research problems, edge-native artificial intelligence, communication network, wireless 6G cellular systems, self-learning architecture, self-learning-enabled 6G edge intelligence. |
| [18] | 2021 | Edge intelligence, 6G, Ultra-reliable low-latency, COVID-19, Internet of drones, Holographic communication. |
| [22] | 2020 | 6G, architecture, B5G, cellular communication, convergence, orchestration, sub-networks, wireless networks. |
| [30] | 2021 | Aggregation, differentiated services (Diffserv), edge intelligence, network traffic, preference logic, quality of experience (QoE), quality of service (QoS). |
| [32] | 2020 | Massive MIMO, holographic beamforming, Internet of everything (IoE), Machine learning, Distributed security. |
| [33] | 2021 | MEC, EGT, Temporal multiplex network, Social network, 6G. |
1.5. Organization of the Paper
- In Section 2 we briefly introduce background and methods.
- In Section 3 we detail the novel evaluation scheme, the analytical methodology and the performance evaluation in a complex networked scenario.
- In Section 4 we conclude by discussing the potential implications of the proposal and the future works.
1.6. Contributions of the Paper
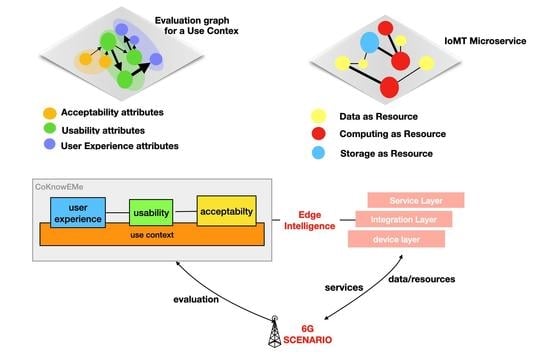
- We propose a novel evaluation scheme, which has been called CoKnowEMe (context knowledge evaluation model), for IoMT microservices in accordance with the complex approach suitable for the forthcoming 6G generation, taking into account what this paradigm will introduce in terms of enabling technologies, in particular driving towards more edge intelligent capabilities, such as computing, machine learning and evaluation of quality of services close to the users.
- We shed light on both architectural and analytical procedure, following a complex approach, consisting of three different interoperable levels, underlining how the interoperability of these chained different levels changes in accordance with the context of use.
- We follow the complex approach in line with the future 6G network and with the moving of the intelligence from the central cloud to edge computing resources since the computing of each evaluation module can represent a resource at edge level. A completely dynamic and heterogeneous topology requires an intelligence at edge level also for the evaluation of the services provided in order to introduce the same degree of adaptability. To this aim, we have also performed simulations to display properties of a networked set of heterogeneous attributes.
- We conduct a deep investigation concerning suitable attributes for each category considered in the evaluation scheme, summarizing this procedure and the findings of the selection and classification in the supplementary information document.
2. Materials and Methods
2.1. IoMT, Microservices and Edge Intelligence
2.2. A Complex Perspective towards 6G
2.3. Acceptability
2.4. Usability
2.5. User Experience
2.6. Weighted Sum Model (WSM)
3. Results
3.1. Scenario
3.2. Glossary
- Attribute: A measurable physical or abstract property of a service entity that can be measured using a quality metric.
- Metric: A measurement scale (i.e., nominal, ordinal, interval, ratio or absolute) combined with a measurement approach (i.e., measurement method or measurement function) that describes how the measurement is to be conducted. Each metric can also have multiple ways in which it can be calculated. There are three types of metrics:
- -
- Basic metric: A metric that does not depend on any other metric and uses a measurement method as a measurement approach.
- -
- Derived metric: A metric derived from other basic or derived metrics, using a measurement function as a measurement approach.
- -
- Indicator: A high-level quantitative metric derived from other metrics and using an analysis model as a measurement approach.
- Measurement method: A logical sequence of operations that are used to quantify a quality attribute using a basic metric.
- Unit of measurement: Quantity taken as a sample and term of comparison for the measurement of all quantities of the same species.
3.3. CoKnowEMe: Architectural and Analytical Model
- Supplier: Person, organization or body, belonging to a specific sector that provides a specific type of service.
- Broker: Intermediary who negotiates the relationship between consumer and service provider.
- Consumer: Person or organization that maintains a commercial relationship and uses the services made available by service providers.
- End user: The people or organizations that are the customers of the service.
- Developer: Intended as a service partner, it can be a developer, integrator, tester, etc.
3.3.1. Approach to Literature Review, Entry Selection and Classification
3.3.2. First Level: Acceptability
3.3.3. Second Level: Usability
3.3.4. Third Level: User Experience
3.3.5. Use Context
3.3.6. Analytical Model
- 1
- considering the level of acceptability, the first, starting from the bottom, calculated as expressed in Equation (1); this value will constitute the output of the considered level and quantifies the acceptability degree of the service;
- 2
- going up to the usability level, we have to consider what has been obtained at the level of acceptability, as expressed in Equation (2):where j indicates all the attributes of usability. By doing so, we are able to take into account the result obtained at the previous level, weighing it in accordance with its relevance in the current level;
- 3
- proceeding towards the last level, we iterate the procedure, obtaining:where j indicates all the attributes related to the user experience and takes into account the importance of the underlying levels.
3.3.7. Pseudocode of the Model
| Algorithm 1 CoKnowEMe Evaluation Algorithm for IoMT Microservices |
|
3.3.8. Performance Evaluation in a Complex Networked Scenario
4. Conclusions
Supplementary Materials
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zhang, Z.; Xiao, Y.; Ma, Z.; Xiao, M.; Ding, Z.; Lei, X.; Karagiannidis, G.K.; Fan, P. 6G wireless networks: Vision, requirements, architecture and key technologies. IEEE Veh. Technol. Mag. 2019, 14, 28–41. [Google Scholar] [CrossRef]
- Forge, S.; Vu, K. Forming a 5G strategy for developing countries: A note for policy makers. Telecommun. Policy 2020, 44, 101975. [Google Scholar] [CrossRef]
- Mcketta, I. Massive Expansions and Huge Improvements in Speed: The Worldwide Growth of 5G in 2020. Available online: https://www.speedtest.net/insights/blog/world-5g-report-2020 (accessed on 2 July 2021).
- OOKLA 5G MAP. Available online: https://www.speedtest.net/ookla-5g-map (accessed on 2 July 2021).
- KNOEMA. Status of 5G Commercial Deployment in OECD Countries. Available online: https://knoema.com/uhgjnwd/status-of-5g-commercial-deployment-in-oecd-countries/ (accessed on 2 July 2021).
- Bank, E.I. Accelerating the 5G Transition in Europe: How to Boost Investments in Transformative 5G Solutions Main Report. Available online: https://op.europa.eu/en/publication-detail/-/publication/85f94ef8-86d0-11eb-ac4c-01aa75ed71a1/language-en (accessed on 2 July 2021).
- Ericsson Mobility Report: More than Half a Billion 5G Subscriptions by the End of 2021. Available online: https://www.ericsson.com/en/mobility-report/reports/june-2021 (accessed on 2 July 2021).
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6G wireless communication systems: Applications, requirements, technologies, challenges and research directions. IEEE Open J. Commun. Soc. 2020, 1, 957–975. [Google Scholar] [CrossRef]
- Giordani, M.; Polese, M.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Toward 6G networks: Use cases and technologies. IEEE Commun. Mag. 2020, 58, 55–61. [Google Scholar] [CrossRef]
- Sergiou, C.; Lestas, M.; Antoniou, P.; Liaskos, C.; Pitsillides, A. Complex Systems: A Communication Networks Perspective Towards 6G. IEEE Access 2020, 8, 89007–89030. [Google Scholar] [CrossRef]
- Saad, W.; Bennis, M.; Chen, M. A vision of 6G wireless systems: Applications, trends, technologies, and open research problems. IEEE Netw. 2019, 34, 134–142. [Google Scholar] [CrossRef] [Green Version]
- Akyildiz, I.F.; Kak, A.; Nie, S. 6G and beyond: The future of wireless communications systems. IEEE Access 2020, 8, 133995–134030. [Google Scholar] [CrossRef]
- Nayak, S.; Patgiri, R. A Vision on Intelligent Medical Service for Emergency on 5G and 6G Communication Era. EAI Endorsed Trans. Internet Things 2020, 6, e2. [Google Scholar] [CrossRef]
- Scatá, M.; Attanasio, B.; Aiosa, G.V.; La Corte, A. The Dynamical Interplay of Collective Attention, Awareness and Epidemics Spreading in the Multiplex Social Networks During COVID-19. IEEE Access 2020, 8, 189203–189223. [Google Scholar] [CrossRef]
- Gatouillat, A.; Badr, Y.; Massot, B.; Sejdić, E. Internet of medical things: A review of recent contributions dealing with cyber-physical systems in medicine. IEEE Internet Things J. 2018, 5, 3810–3822. [Google Scholar] [CrossRef] [Green Version]
- Peltonen, E.; Bennis, M.; Capobianco, M.; Debbah, M.; Ding, A.; Gil-Castiñeira, F.; Jurmu, M.; Karvonen, T.; Kelanti, M.; Kliks, A.; et al. 6G white paper on edge intelligence. arXiv 2020, arXiv:2004.14850. [Google Scholar]
- Xiao, Y.; Shi, G.; Li, Y.; Saad, W.; Poor, H.V. Toward Self-Learning Edge Intelligence in 6G. IEEE Commun. Mag. 2020, 58, 34–40. [Google Scholar] [CrossRef]
- Gupta, R.; Reebadiya, D.; Tanwar, S. 6G-enabled Edge Intelligence for Ultra-Reliable Low Latency Applications: Vision and Mission. Comput. Stand. Interfaces 2021, 77, 103521. [Google Scholar] [CrossRef]
- Pustokhina, I.V.; Pustokhin, D.A.; Gupta, D.; Khanna, A.; Shankar, K.; Nguyen, G.N. An effective training scheme for deep neural network in edge computing enabled Internet of medical things (IoMT) systems. IEEE Access 2020, 8, 107112–107123. [Google Scholar] [CrossRef]
- Guerreiro, J.; Rodrigues, L.; Correia, N. Allocation of Resources in SAaaS Clouds Managing Thing Mashups. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1597–1609. [Google Scholar] [CrossRef]
- Fernández-Villamor, J.I.; Iglesias, C.A.; Garijo, M. Microservices-Lightweight Service Descriptions for REST Architectural Style. In Proceedings of the ICAART, Valencia, Spain, 22–24 January 2010; pp. 576–579. [Google Scholar]
- Ziegler, V.; Viswanathan, H.; Flinck, H.; Hoffmann, M.; Räisänen, V.; Hätönen, K. 6G architecture to connect the worlds. IEEE Access 2020, 8, 173508–173520. [Google Scholar] [CrossRef]
- Moloja, D.; Mpekoa, N.; Van Greunen, D. Evaluating two security systems for mobile voting fortification. In Proceedings of the 2nd International Conference on Intelligent and Innovative Computing Applications, Plaine Magnien, Mauritius, 24–25 September 2020; pp. 1–6. [Google Scholar]
- Bevan, N.; Carter, J.; Harker, S. ISO 9241-11 revised: What have we learnt about usability since 1998? In International Conference on Human-Computer Interaction; Springer: Berlin/Heidelberg, Germany, 2015; pp. 143–151. [Google Scholar]
- Jordan, P.W. An Introduction to Usability; CRC Press: Boca Raton, FL, USA, 2020. [Google Scholar]
- Harrison, R.; Flood, D.; Duce, D. Usability of mobile applications: Literature review and rationale for a new usability model. J. Interact. Sci. 2013, 1, 1–16. [Google Scholar] [CrossRef] [Green Version]
- Saleh, A.; Ismail, R.; Fabil, N. Evaluating usability for mobile application: A MAUEM approach. In Proceedings of the 2017 International Conference on Software and e-Business, Essen, Germany, 12–13 June 2017; pp. 71–77. [Google Scholar]
- Kamal, S.A.; Shafiq, M.; Kakria, P. Investigating acceptance of telemedicine services through an extended technology acceptance model (TAM). Technol. Soc. 2020, 60, 101212. [Google Scholar] [CrossRef]
- Alexandru, A.; Coardos, D.; Tudora, E. Acceptance of the technologies deployed for the development of online public services and systems used by elderly. In Proceedings of the IEEE 2019 11th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Pitesti, Romania, 27–29 June 2019; pp. 1–4. [Google Scholar]
- Tang, P.; Dong, Y.; Chen, Y.; Mao, S.; Halgamuge, S. QoE-aware Traffic Aggregation Using Preference Logic for Edge Intelligence. IEEE Trans. Wirel. Commun. 2021. [Google Scholar] [CrossRef]
- Zavadskas, E.K.; Turskis, Z.; Antucheviciene, J.; Zakarevicius, A. Optimization of weighted aggregated sum product assessment. Elektron. Elektrotechnika 2012, 122, 3–6. [Google Scholar] [CrossRef]
- Kaiser, M.S.; Zenia, N.; Tabassum, F.; Al Mamun, S.; Rahman, M.A.; Islam, M.S.; Mahmud, M. 6G Access Network for Intelligent Internet of Healthcare Things: Opportunity, Challenges and Research Directions. In Proceedings of the International Conference on Trends in Computational and Cognitive Engineering, Parit Raja, Malaysia, 21 October 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 317–328. [Google Scholar]
- Attanasio, B.; La Corte, A.; Scatà, M. Evolutionary dynamics of MEC’s organization in a 6G scenario through EGT and temporal multiplex social network. ICT Express 2021, 7, 138–142. [Google Scholar] [CrossRef]
- Bevan, N.; Carter, J.; Earthy, J.; Geis, T.; Harker, S. New ISO standards for usability, usability reports and usability measures. In Proceedings of the International Conference on Human-Computer Interaction, Toronto, ON, Canada, 17–22 July 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 268–278. [Google Scholar]
- Wardhana, S.; Sabariah, M.K.; Effendy, V.; Kusumo, D.S. User interface design model for parental control application on mobile smartphone using user centered design method. In Proceedings of the IEEE 2017 5th International Conference on Information and Communication Technology (ICoIC7), Melaka, Malaysia, 17–19 May 2017; pp. 1–6. [Google Scholar]
- Tan, J.; Rönkkö, K.; Gencel, C. A framework for software usability and user experience measurement in mobile industry. In Proceedings of the IEEE 2013 Joint Conference of the 23rd International Workshop on Software Measurement and the 8th International Conference on Software Process and Product Measurement, Ankara, Turkey, 23–26 October 2013; pp. 156–164. [Google Scholar]
- Rahman, M.A.; Hossain, M.S. An internet of medical things-enabled edge computing framework for tackling COVID-19. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Mazayev, A.; Correia, N. A Distributed CoRE-Based Resource Synchronization Mechanism. IEEE Internet Things J. 2019, 7, 4625–4640. [Google Scholar] [CrossRef]
- Bucchiarone, A.; Dragoni, N.; Dustdar, S.; Lago, P.; Mazzara, M.; Rivera, V.; Sadovykh, A. Microservices. In Science and Engineering; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Pastor-Satorras, R.; Castellano, C.; Van Mieghem, P.; Vespignani, A. Epidemic processes in complex networks. Rev. Mod. Phys. 2015, 87, 925. [Google Scholar] [CrossRef] [Green Version]
- Barrat, A.; Barthelemy, M.; Pastor-Satorras, R.; Vespignani, A. The architecture of complex weighted networks. Proc. Natl. Acad. Sci. USA 2004, 101, 3747–3752. [Google Scholar] [CrossRef] [Green Version]
- Menichetti, G.; Remondini, D.; Panzarasa, P.; Mondragón, R.J.; Bianconi, G. Weighted multiplex networks. PLoS ONE 2014, 9, e97857. [Google Scholar] [CrossRef] [Green Version]
- Kivelä, M.; Arenas, A.; Barthelemy, M.; Gleeson, J.P.; Moreno, Y.; Porter, M.A. Multilayer networks. J. Complex Netw. 2014, 2, 203–271. [Google Scholar] [CrossRef] [Green Version]
- Distler, V.; Lallemand, C.; Koenig, V. How acceptable is this? How user experience factors can broaden our understanding of the acceptance of privacy trade-offs. Comput. Hum. Behav. 2020, 106, 106227. [Google Scholar] [CrossRef]
- Islam, M.S.; Grönlund, Å. Factors influencing the adoption of mobile phones among the farmers in Bangladesh: Theories and practices. ICTer 2011, 4, 4–14. [Google Scholar] [CrossRef] [Green Version]
- Beldad, A.D.; Hegner, S.M. Expanding the technology acceptance model with the inclusion of trust, social influence and health valuation to determine the predictors of German users’ willingness to continue using a fitness app: A structural equation modeling approach. Int. J. Hum. Interact. 2018, 34, 882–893. [Google Scholar] [CrossRef] [Green Version]
- Weichbroth, P. Usability of mobile applications: A systematic literature study. IEEE Access 2020, 8, 55563–55577. [Google Scholar] [CrossRef]
- Hussain, A.; Kutar, M. Usability metric framework for mobile phone application. In Proceedings of the 10th Annual PostGraduate Symposium on The Convergence of Telecommunications, Networking and Broadcasting, Liverpool, UK, 22–23 June 2009. [Google Scholar]
- Hertzum, M. Usability Testing: A Practitioner’s Guide to Evaluating the User Experience. Synth. Lect. Hum. Cent. Inform. 2020, 13, i-105. [Google Scholar] [CrossRef]
- Mashapa, J.; van Greunen, D. User experience evaluation metrics for usable accounting tools. In Proceedings of the 2010 Annual Research Conference of the South African Institute of Computer Scientists and Information Technologists, Bela Bela, South Africa, 11–13 October 2010; pp. 170–181. [Google Scholar]
- Helff, F.; Gruenwald, L.; d’Orazio, L. Weighted Sum Model for Multi-Objective Query Optimization for Mobile-Cloud Database Environments. In Proceedings of the EDBT/ICDT Workshops, Bordeaux, France, 15 March 2016. [Google Scholar]
- Huang, A.F.; Lan, C.W.; Yang, S.J. An optimal QoS-based Web service selection scheme. Inf. Sci. 2009, 179, 3309–3322. [Google Scholar] [CrossRef]
- Kohar, R. Optimal Web Service Selection Model using Fuzzy Extended AHP and Weighted Sum Method. J. Digit. Inf. Manag. 2018, 16. [Google Scholar] [CrossRef]
- Sarika, S. Server selection by using weighted sum and revised weighted sum decision models. IJICTR J. 2012, 2, 499–511. [Google Scholar]
- Guerron, X.; Abrahão, S.; Insfran, E.; Fernández-Diego, M.; González-Ladrón-De-Guevara, F. A taxonomy of quality metrics for cloud services. IEEE Access 2020, 8, 131461–131498. [Google Scholar] [CrossRef]
- Krzewińska, J.; Indyka-Piasecka, A.; Kopel, M.; Kukla, E.; Telec, Z.; Trawiński, B. Usability testing of a responsive web system for a school for disabled children. In Proceedings of the Asian Conference on Intelligent Information and Database Systems, Dong Hoi City, Vietnam, 19–21 March 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 705–716. [Google Scholar]
- Da Costa, R.P.; Canedo, E.D.; De Sousa, R.T.; Albuquerque, R.D.O.; Villalba, L.J.G. Set of usability heuristics for quality assessment of mobile applications on smartphones. IEEE Access 2019, 7, 116145–116161. [Google Scholar] [CrossRef]
- Kabir, M.A.; Salem, O.A.; Rehman, M.U. Discovering knowledge from mobile application users for usability improvement: A fuzzy association rule mining approach. In Proceedings of the 2017 8th IEEE International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 24–26 November 2017; pp. 126–129. [Google Scholar]
- Saleh, A.M.; Al-Badareen, A.B.; Enaizan, O. Automated User Experience Tool Development for Mobile Application. Int. J. Adv. Sci. Technol. 2020, 29, 4929–4940. [Google Scholar]
- Vermeeren, A.P.; Law, E.L.C.; Roto, V.; Obrist, M.; Hoonhout, J.; Väänänen-Vainio-Mattila, K. User experience evaluation methods: Current state and development needs. In Proceedings of the 6th Nordic Conference on Human-Computer Interaction: Extending Boundaries, Reykjavik, Iceland, 16–20 November 2010; pp. 521–530. [Google Scholar]
- International Organization for Standardization ISO:9241-11:2018. Ergonomics of Human-System Interaction Part 11: Usability: Definitions and Concepts; International Organization for Standardization: Geneva, Switzerland, 2018. [Google Scholar]
Short Biography of Authors
 | Grazia Veronica Aiosa received her B.S. degree in Computer Engineering (2016) and M.S. degree in Telecommunication Engineering (2019) from the Dipartimento di Ingegneria Elettrica, Elettronica e Informatica (DIEEI) at University of Catania, Italy. She is currently an Early Stage Researcher at DIEEI, University of Catania. Her research interests include multi-layer networks, social contagion and collective attention. |
 | Barbara Attanasio received her B.S. degree in Computer engineering (2016) and M.S. degree in Telecommunications engineering (2018) from the Dipartimento di Ingegneria Elettrica, Elettronica e Informatica (DIEEI) at University of Catania, Italy. She is currently a Ph.D. student in Systems, Energy, Computer and Telecommunications Engineering at DIEEI, University of Catania. Her research interests Multi Access Edge Computing, Evolutionary Game Theory, Multi-layer networks, Data Science and IoT. |
 | Aurelio La Corte is Associate Professor in Telecommunication Engineering at the University of Catania, Italy. He received the degree in electrical engineering in 1988 and the Ph.D. in Electronic Engineering and Computer Science in 1994. He has more than 25 years of experience in scientific and teaching activity and specific experience in designing telecommunications networks and systems and in managing complex projects. Responsible for various ICT-related activities at the University of Catania, he has been involved in coordinating, designing and developing networks and ICT services.His scientific interests include telecommunication systems and integrated services, innovative ICT services and technological innovation. |
 | Marialisa Scatá received her B.S. and M.S. degrees in Telecommunication Engineering, from (DIEEI), University of Catania, Italy. She received the Ph.D. in Computer Science and Telecommunication Engineering from University of Catania under the supervision of Prof. Aurelio La Corte, with whom she has been collaborating since 2009. During the Ph.D. she attended several schools and conferences. Currently, she works as Postdoctoral Researcher at DIEEI, University of Catania. She serves as reviewer for several top-tier journals. She has an interdisciplinary approach to research and her interests include bio-inspired models, ICT, telecommunications, social networks, complex networks, multi-layer networks, social contagion and epidemic spreading, evolutionary game theory, data mining, machine learning, healthcare applications and cognitive networks. |








| Region | Operator (Number of Covered Cities) | Launch | Penetration Rate Forecast |
|---|---|---|---|
| Australia | Optus (14), Telstra (46), Vodafone (8) [5] | 05/22/2019 [5] | - |
| Austria | A1 Telekom (129), Drei (Three) Austria (4), Magenta Telekom (T-Mobile Austria) (28) [5] | 03/26/2019 [5] | - |
| Belgium | Proximus (79) [5] | 04/02/2020 [5] | - |
| Canada | Bell (5), Rogers (4), Telus (5) [5] | 01/15/2020 [5] | - |
| Czech Republic | O2 (2) [5] | 06/19/2020 [5] | - |
| Finland | DNA (21), Elisa (30), Telia (8) [5] | 07/01/2019 [5] | - |
| European Union | - | - | 29% (2025) [6] |
| Germany | Telecom Deutschland (20), Vodafone (96) [5] | 07/16/2019 [5] | 98% (2022) [2] |
| Gulf Cooperation Council | - | - | 73% (2026) [7] |
| Hungary | Maygar Telekom (2), Vodafone (2) [5] | 10/17/2019 [5] | - |
| India | - | - | 26% (2026) [7] |
| Ireland | Eir (19), Vodafone (5) [5] | 08/13/2019 [5] | - |
| Italy | TIM (8), Vodafone (5) [5] | 06/06/2019 [5] | - |
| Japan | KDDI (15), NTT Docomo (35), Softbank (12) [5] | 03/25/2020 [5] | - |
| Korea | KT (85), LGU+ (85), SKT (85) [5] | 04/03/2019 [5] | 90% (2026) [2] |
| Latin America | - | - | 34% (2026) [7] |
| Latvia | Tele2 (2) [5] | 01/22/2020 [5] | - |
| Middle East and North Africa | - | - | 18% (2026) [7] |
| Netherlands | Vodafone Ziggo (50% of the Netherlands) [5] | 04/28/2020 [5] | - |
| New Zeland | Vodafone (4) [5] | 12/10/2019 [5] | - |
| Norway | Telenor (4), Telia (2) [5] | 03/13/2020 [5] | - |
| North America | - | - | 84% (2026) [7] |
| North-East Asia | - | - | 65% (2026) [7] |
| Poland | Plus (7), T-Mobile (11) [5] | 05/12/2020 [5] | - |
| South East Asia and Oceania | - | - | 33% (2026) [7] |
| Spain | Vodafone (22) [5] | 15/06/2019 [5] | - |
| Sub-Saharan Africa | - | - | 7% (2026) [7] |
| Sweden | 3-Sweden (5), Tele2 (3), Telia (12) [5] | 24/05/2020 [5] | - |
| Switzerland | Sunrise (384), Swisscom (90% population) [5] | 01/04/2019 [5] | - |
| United Kingdom | EE (80), O2 (60), Three (66), Vodafone (44) [5] | 30/05/2019 [5] | - |
| United States | AT&T (335), Sprint (9), T-Mobile (6000), Verizon Wireless (35) [5] | 03/04/2019 [5] | - |
| World | - | - | 12% (2024), 50% (2034) [2] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aiosa, G.V.; Attanasio, B.; La Corte, A.; Scatá, M. CoKnowEMe: An Edge Evaluation Scheme for QoS of IoMT Microservices in 6G Scenario. Future Internet 2021, 13, 177. https://doi.org/10.3390/fi13070177
Aiosa GV, Attanasio B, La Corte A, Scatá M. CoKnowEMe: An Edge Evaluation Scheme for QoS of IoMT Microservices in 6G Scenario. Future Internet. 2021; 13(7):177. https://doi.org/10.3390/fi13070177
Chicago/Turabian StyleAiosa, Grazia Veronica, Barbara Attanasio, Aurelio La Corte, and Marialisa Scatá. 2021. "CoKnowEMe: An Edge Evaluation Scheme for QoS of IoMT Microservices in 6G Scenario" Future Internet 13, no. 7: 177. https://doi.org/10.3390/fi13070177
APA StyleAiosa, G. V., Attanasio, B., La Corte, A., & Scatá, M. (2021). CoKnowEMe: An Edge Evaluation Scheme for QoS of IoMT Microservices in 6G Scenario. Future Internet, 13(7), 177. https://doi.org/10.3390/fi13070177