GRAPH4: A Security Monitoring Architecture Based on Data Plane Anomaly Detection Metrics Calculated over Attack Graphs
Abstract
:1. Introduction
- We present a security monitoring architecture that integrates attack graphs generated on the control plane with anomaly detection metrics calculated on the data plane.
- We demonstrate how the control plane can exploit its knowledge of the network configuration in order to optimize the allocation of low-level metrics collectors, thus placing them only on specific data plane devices.
- We evaluate the effectiveness of GRAPH4 presenting a PoC related to Distributed Denial of Service detection.
2. Background
2.1. Security Metrics
- Vulnerability metrics, which consist of measures of system vulnerabilities that depend on the user, the interface, the hardware, or software in general. Examples are password [10], attack surface [11] and software vulnerabilities (https://nvd.nist.gov/vuln-metrics/cvss, accessed on 1 October 2023).
- Defense metrics, which measure the strength and the effort needed for placing defense mechanisms in a system. They consist of the evaluation of preventive, reactive, and proactive defenses, such as in [12].
- Situation metrics, which focus on the security state of a system and depend on the moment of analysis; these metrics dynamically evolve from time to time following the outcome of attack–defense interactions. Examples are metrics based on the frequency of security incidents or related to the investment for the security improvement [13]. Those are mainly subdivided into data-driven metrics, such as the network maliciousness metric [14], or model-driven metrics, such as the fraction of compromised computers.
- Attack metrics, which measure the strength of sustained attacks. The categories previously proposed focus on the assessment of the level of security of the system via the analysis of configurations and devices; conversely, attack metrics focus on quantifying and analyzing cyberattacks and threats faced and are essential for assessing risk, measuring the success of security measures, and guiding the allocation of resources. Examples are the network bandwidth that a botnet can use to launch DOS attacks or the occurrence of obfuscation in malware samples [15].
2.2. P4 and Data Plane Programmability
- Reconfigurability: The packet parsing logic and processing rules can be dynamically installed and updated by the controller.
- Protocol independence: By giving rule names, key types, and typed match+action tables in the header fields, the controller can determine how to process header fields, freeing the switch from fixed actions taken on standard packet formats.
- Target independence: The P4 code is completely portable for every target. The P4 compiler is tasked with translating program features that make use of target-specific capabilities.
- 1.
- Header types: packet header definitions, i.e., the set of fields and their sizes.
- 2.
- Parsers: finite-state machines that map packets into headers and metadata.
- 3.
- Tables: data structures defining matching fields and actions applied to them.
- 4.
- Actions: code fragments that describe packet manipulation and can consider external data supplied by the control plane at runtime.
- 5.
- Match–action units: elements that construct lookup keys from packet fields’ metadata and use them to find the right action and execute it.
- 6.
- Control flows: imperative blocks that describe packet processing on a target using the data-dependent sequence of match–action unit invocations.
2.3. Network Traffic Entropy
3. Related Works
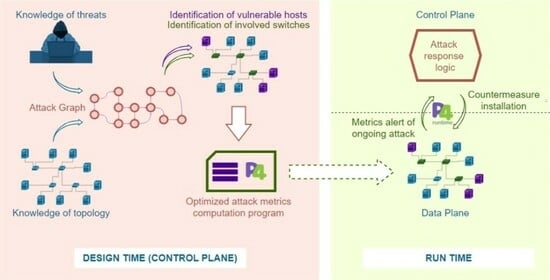
4. GRAPH4 Architecture
4.1. Control Plane
- 1.
- 2.
- It knows the set of nodes that are vulnerable to certain types of attack and can use this information to optimize the allocation of low-level metrics.
4.2. Data Plane
4.3. Workflow
- 1.
- The AG Generator is fed with information about the topology of the network (hosts, active services, connections, etc.), which is used to generate the AG that identifies the vulnerable paths of the network.
- 2.
- The control plane, with that knowledge, can identify the vulnerable hosts that need to be monitored.
- 3.
- The control plane identifies the switches that are involved in forwarding traffic to or from said hosts and prepares the rules to be installed.
- 4.
- The Match Action Tables (MATs), which implement the low-level detection of attacks, are installed in the relevant switches.
- 5.
- The data plane carries out network monitoring by inspecting the traffic and, if the metrics indicate that an attack is detected, it notifies the control plane.
- 6.
- When the control plane is notified of an attack, it can deploy countermeasures, e.g., by installing additional MATs on the switches.
5. Proof of Concept
5.1. The Data Plane Low-Level Metric
5.2. AG Cuts
- 1.
- The PPT is indeed quite variable but shows statistical stability when comparing single values with the average; therefore, we assume we are facing a stationary and ergodic stochastic process;
- 2.
- The average PPT for the two cases is almost independent of the number of packets involved in security metric calculation, and because of this, we assume that we can make some general statement not depending on the actual shape of the AGs but just on the number of hosts identified as vulnerable;
- 3.
- The overall processing burden in the switch is a linear function of the number of traffic flows considered suspicious (i.e., the number of suspicious hosts), and therefore, we are interested in the security metric calculation. On average, the overall processing burden in the switch is a multiple of the number of flows according to the average packet processing time.
- 1.
- The overhead generated in a single switch by the process of metric elaboration will be linearly influenced by the number V of hosts identified as possibly vulnerable;
- 2.
- The total overhead generated in the network by the entire metric calculation processes will have a directly proportional relationship with the number of switches that compute the metric.
6. Discussion and Limitations of the Study
7. Conclusions and Future Works
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| DDoS | Distributed Denial of Service |
| CPS | Cyber–Physical Systems |
| SDN | Software-Defined Networks |
| DPP | Data Plane Programmability |
| AG | Attack Graph |
| MAT | Match Action Table |
| PoC | Proof of Concept |
| PPT | Packet Processing Time |
References
- Ahmed, M.; Mahmood, A.N.; Hu, J. A survey of network anomaly detection techniques. J. Netw. Comput. Appl. 2016, 60, 19–31. [Google Scholar] [CrossRef]
- Gori, G.; Melis, A.; Berardi, D.; Prandini, M.; Al Sadi, A.; Callegati, F. Towards the Creation of Interdisciplinary Consumer-Oriented Security Metrics. In Proceedings of the 2023 IEEE 20th Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2023; pp. 957–958. [Google Scholar]
- Gori, G.; Melis, A.; Rinieri, L.; Prandini, M.; Al Sadi, A.; Callegati, F. Metrics for Cyber-Physical Security: A call to action. In Proceedings of the 2022 International Symposium on Networks, Computers and Communications (ISNCC), Shenzhen, China, 19–22 July 2022; pp. 1–4. [Google Scholar]
- Melis, A.; Layeghy, S.; Berardi, D.; Portmann, M.; Prandini, M.; Callegati, F. P-scor: Integration of constraint programming orchestration and programmable data plane. IEEE Trans. Netw. Serv. Manag. 2020, 18, 402–414. [Google Scholar] [CrossRef]
- Pendleton, M.; Garcia-Lebron, R.; Cho, J.H.; Xu, S. A survey on systems security metrics. ACM Comput. Surv. CSUR 2016, 49, 1–35. [Google Scholar] [CrossRef]
- Obadia, M.; Bouet, M.; Rougier, J.L.; Iannone, L. A greedy approach for minimizing SDN control overhead. In Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015; pp. 1–5. [Google Scholar]
- Ding, D.; Savi, M.; Siracusa, D. Tracking Normalized Network Traffic Entropy to Detect DDoS Attacks in P4. IEEE Trans. Dependable Secur. Comput. 2021, 19, 4019–4031. [Google Scholar] [CrossRef]
- Gao, S.; Handley, M.; Vissicchio, S. Stats 101 in p4: Towards in-switch anomaly detection. In Proceedings of the Twentieth ACM Workshop on Hot Topics in Networks, Virtual Event, 10–12 November 2021; pp. 84–90. [Google Scholar]
- Swanson, M.M.; Bartol, N.; Sabato, J.; Hash, J.; Graffo, L. Security Metrics Guide for Information Technology Systems; Special Publication (NIST SP); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2003.
- Berardi, D.; Callegati, F.; Melis, A.; Prandini, M. Password similarity using probabilistic data structures. J. Cybersecur. Priv. 2020, 1, 78–92. [Google Scholar] [CrossRef]
- Manadhata, P.K.; Wing, J.M. An attack surface metric. IEEE Trans. Softw. Eng. 2010, 37, 371–386. [Google Scholar] [CrossRef]
- Hong, J.B.; Enoch, S.Y.; Kim, D.S.; Nhlabatsi, A.; Fetais, N.; Khan, K.M. Dynamic security metrics for measuring the effectiveness of moving target defense techniques. Comput. Secur. 2018, 79, 33–52. [Google Scholar] [CrossRef]
- Zhan, Z.; Xu, M.; Xu, S. A characterization of cybersecurity posture from network telescope data. In Proceedings of the Trusted Systems: 6th International Conference, INTRUST 2014, Beijing, China, 16–17 December 2014; Revised Selected Papers 6; Springer: Berlin, Germany, 2015; pp. 105–126. [Google Scholar]
- Zhang, J.; Durumeric, Z.; Bailey, M.; Liu, M.; Karir, M. On the Mismanagement and Maliciousness of Networks. In Proceedings of the NDSS, San Diego, CA, USA, 23–26 February 2014; Volume 14, pp. 23–26. [Google Scholar]
- Roundy, K.A.; Miller, B.P. Binary-code obfuscations in prevalent packer tools. ACM Comput. Surv. CSUR 2013, 46, 1–32. [Google Scholar] [CrossRef]
- Ahmed, R.K.A. Security metrics and the risks: An overview. Int. J. Comput. Trends Technol. IJCTT 2016, 41, 106–112. [Google Scholar] [CrossRef]
- Bosshart, P.; Daly, D.; Gibb, G.; Izzard, M.; McKeown, N.; Rexford, J.; Schlesinger, C.; Talayco, D.; Vahdat, A.; Varghese, G.; et al. P4: Programming Protocol-Independent Packet Processors. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 87–95. [Google Scholar] [CrossRef]
- Consortium, T.P.L. P4Runtime Specification. 2020. Available online: https://opennetworking.org/wp-content/uploads/2020/10/P4Runtime-Specification-120.html (accessed on 1 October 2023).
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Gharbaoui, M.; Contoli, C.; Davoli, G.; Borsatti, D.; Cuffaro, G.; Paganelli, F.; Cerroni, W.; Cappanera, P.; Martini, B. An experimental study on latency-aware and self-adaptive service chaining orchestration in distributed NFV and SDN infrastructures. Comput. Netw. 2022, 208, 108880. [Google Scholar] [CrossRef]
- Sadi, A.A.; Savi, M.; Berardi, D.; Melis, A.; Prandini, M.; Callegati, F. Real-time Pipeline Reconfiguration of P4 Programmable Switches to Efficiently Detect and Mitigate DDoS Attacks. In Proceedings of the 2023 26th Conference on Innovation in Clouds, Internet and Networks and Workshops (ICIN), Paris, France, 6–9 March 2023; pp. 21–23. [Google Scholar] [CrossRef]
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Lall, A.; Sekar, V.; Ogihara, M.; Xu, J.; Zhang, H. Data streaming algorithms for estimating entropy of network traffic. ACM SIGMETRICS Perform. Eval. Rev. 2006, 34, 145–156. [Google Scholar] [CrossRef]
- Wang, L.; Singhal, A.; Jajodia, S. Toward measuring network security using attack graphs. In Proceedings of the 2007 ACM Workshop on Quality of Protection, Alexandria, VA, USA, 29 October 2007; pp. 49–54. [Google Scholar]
- Lippmann, R.; Ingols, K.; Scott, C.; Piwowarski, K.; Kratkiewicz, K.; Artz, M.; Cunningham, R. Validating and restoring defense in depth using attack graphs. In Proceedings of the MILCOM 2006—2006 IEEE Military Communications Conference, Washington, DC, USA, 23–25 October 2006; pp. 1–10. [Google Scholar]
- Mehta, V.; Bartzis, C.; Zhu, H.; Clarke, E.; Wing, J. Ranking attack graphs. In Proceedings of the International Workshop on Recent Advances in Intrusion Detection, Hamburg, Germany, 20–22 September 2006; pp. 127–144. [Google Scholar]
- Pamula, J.; Jajodia, S.; Ammann, P.; Swarup, V. A weakest-adversary security metric for network configuration security analysis. In Proceedings of the 2nd ACM Workshop on Quality of Protection, Alexandria, VA, USA, 30 October 2006; pp. 31–38. [Google Scholar]
- Leversage, D.J.; Byres, E.J. Estimating a system’s mean time-to-compromise. IEEE Secur. Priv. 2008, 6, 52–60. [Google Scholar] [CrossRef]
- Homer, J.; Ou, X.; Schmidt, D. A Sound and Practical Approach to Quantifying Security Risk in Enterprise Networks; Kansas State University Technical Report; Kansas State University: Manhattan, KS, USA, 2009; pp. 1–15. [Google Scholar]
- Poolsappasit, N.; Dewri, R.; Ray, I. Dynamic security risk management using bayesian attack graphs. IEEE Trans. Dependable Secur. Comput. 2011, 9, 61–74. [Google Scholar] [CrossRef]
- Wang, L.; Jajodia, S.; Singhal, A.; Cheng, P.; Noel, S. k-zero day safety: A network security metric for measuring the risk of unknown vulnerabilities. IEEE Trans. Dependable Secur. Comput. 2013, 11, 30–44. [Google Scholar] [CrossRef]
- Zhang, M.; Wang, L.; Jajodia, S.; Singhal, A.; Albanese, M. Network diversity: A security metric for evaluating the resilience of networks against zero-day attacks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1071–1086. [Google Scholar] [CrossRef]
- Ramos, A.; Lazar, M.; Holanda Filho, R.; Rodrigues, J.J. Model-based quantitative network security metrics: A survey. IEEE Commun. Surv. Tutor. 2017, 19, 2704–2734. [Google Scholar] [CrossRef]
- Ou, X.; Govindavajhala, S.; Appel, A.W. MulVAL: A logic-based network security analyzer. In Proceedings of the USENIX Security Symposium, Baltimore, MD, USA, 31 July–5 August 2005; Volume 8, pp. 113–128. [Google Scholar]
- Stan, O.; Bitton, R.; Ezrets, M.; Dadon, M.; Inokuchi, M.; Ohta, Y.; Yagyu, T.; Elovici, Y.; Shabtai, A. Extending attack graphs to represent cyber-attacks in communication protocols and modern it networks. IEEE Trans. Dependable Secur. Comput. 2020, 19, 1936–1954. [Google Scholar] [CrossRef]
- Boyer, W.; McQueen, M. Ideal based cyber security technical metrics for control systems. In Proceedings of the Critical Information Infrastructures Security: Second International Workshop, CRITIS 2007, Málaga, Spain, 3–5 October 2007; Revised Papers 2; Springer: Berlin, Germany, 2008; pp. 246–260. [Google Scholar]
- Ceri, S.; Gottlob, G.; Tanca, L. What you always wanted to know about Datalog (and never dared to ask). IEEE Trans. Knowl. Data Eng. 1989, 1, 146–166. [Google Scholar] [CrossRef]










Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gori, G.; Rinieri, L.; Al Sadi, A.; Melis, A.; Callegati, F.; Prandini, M. GRAPH4: A Security Monitoring Architecture Based on Data Plane Anomaly Detection Metrics Calculated over Attack Graphs. Future Internet 2023, 15, 368. https://doi.org/10.3390/fi15110368
Gori G, Rinieri L, Al Sadi A, Melis A, Callegati F, Prandini M. GRAPH4: A Security Monitoring Architecture Based on Data Plane Anomaly Detection Metrics Calculated over Attack Graphs. Future Internet. 2023; 15(11):368. https://doi.org/10.3390/fi15110368
Chicago/Turabian StyleGori, Giacomo, Lorenzo Rinieri, Amir Al Sadi, Andrea Melis, Franco Callegati, and Marco Prandini. 2023. "GRAPH4: A Security Monitoring Architecture Based on Data Plane Anomaly Detection Metrics Calculated over Attack Graphs" Future Internet 15, no. 11: 368. https://doi.org/10.3390/fi15110368
APA StyleGori, G., Rinieri, L., Al Sadi, A., Melis, A., Callegati, F., & Prandini, M. (2023). GRAPH4: A Security Monitoring Architecture Based on Data Plane Anomaly Detection Metrics Calculated over Attack Graphs. Future Internet, 15(11), 368. https://doi.org/10.3390/fi15110368