Embedding an Identity-Based Short Signature as a Digital Watermark
Abstract
:1. Introduction
2. Related Work
2.1. Lossless Compression
2.2. Difference Expansion
2.3. Histogram Shifting
3. Identity-Based Short Digital Signature
| Signature scheme | Signature size | Public key size | Private key size |
|---|---|---|---|
| ECDSA | 320 | 160 | 160 |
| IBS-1 | 160 | 160 | 160 |
3.1. IBS-1 Signature Scheme
- Setup takes a security parameter as input (here, is the unary notation for the security parameter, i.e., key material is k bits long), and returns the master (signing) key s plus a set of system parameters params that includes the system public key ;
- KeyGen takes as inputs the master key s and an identity , and returns a secret signature key ;
- Sign takes as inputs the secret signature key and a message , and returns the signature σ of m;
- Vrf takes as inputs and σ. It returns 1 if σ is a valid signature of m related to , and 0 otherwise.
| Algorithm 1 Setup algorithm |
|
| Algorithm 2 KeyGen algorithm |
|
| which represent private key corresponding to the identity id. |
| Algorithm 3 IBS-1 signature scheme |
|
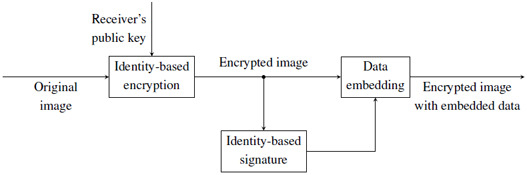
4. Proposal
4.1. Tiling with Unequal Patches
- A quality function that determines if it is convenient to expand a patch p including its western, southwestern, and southern neighbors. The quality function can be a general measure of the spatial correlation among pixels or of the entropy, or a pixel value prediction method such as, for example, Checkerboard Based Prediction (CBP) [25]. An alternative idea that can be used when the actual embedding function is computationally light is to actually apply it to the patches separately and to the combined patch, comparing the relative gain/loss. Clearly, storing partial results speeds the computation up.
- A penalty function accounting for constraints that a bigger patch imposes over adjacent patches. Figure 1 shows, for example, that a 3-by-3 patch (labeled as c) constrains the two basic patches labeled a and b to be considered as basic patches only. As penalty function, we used a count of the basic patches that were deprived from the opportunity of being expanded:

4.2. Using Identity-Based Short Signatures


5. Conclusions
Author Contributions
Conflicts of Interest
References
- Tsai, J.S.; Huang, W.B.; Kuo, Y.H. On the selection of optimal feature region set for robust digital image watermarking. IEEE Trans. Image Process. 2011, 20, 735–743. [Google Scholar] [CrossRef] [PubMed]
- Zhang, X. Separable Reversible Data Hiding in Encrypted Image. IEEE Trans. Inf. Forensic Secur. 2012, 7, 826–832. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Advances in Cryptology—CRYPTO 2001; Springer: Berlin, Germany, 2001; pp. 213–229. [Google Scholar]
- Goljan, M.; Fridrich, J.; Du, R. Distortion-free data embedding for images. Inf. Hiding 2001, 2137, 27–41. [Google Scholar]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef]
- Alattar, A.M. Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans. Image Process. 2004, 13, 1147–1156. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Li, X.; Yang, B.; Guo, Z. Efficient generalized integer transform for reversible watermarking. IEEE Signal Process. Lett. 2010, 17, 567–570. [Google Scholar] [CrossRef]
- Ni, Z.; Shi, Y.Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Li, X.; Yang, B.; Zeng, T. Efficient reversible watermarking based on adaptive prediction-error expansion and pixel selection. IEEE Trans. Image Process. 2011, 20, 3524–3533. [Google Scholar] [PubMed]
- Thodi, D.M.; Rodriguez, J.J. Expansion embedding techniques for reversible watermarking. IEEE Trans. Image Process. 2007, 16, 721–729. [Google Scholar] [CrossRef] [PubMed]
- Wang, C.; Li, X.; Yang, B. Efficient reversible image watermarking by using dynamical prediction-error expansion. In Proceedings of the 17th IEEE International Conference on Image Processing (ICIP), Hong Kong, China, 26–29 September 2010; pp. 3673–3676.
- Zhang, W.; Hu, X.; Li, X.; Yu, N. Recursive Histogram Modification: Establishing Equivalency Between Reversible Data Hiding and Lossless Data Compression. IEEE Trans. Image Process. 2013, 22, 2775–2785. [Google Scholar] [CrossRef] [PubMed]
- Petitcolas, F.A.P.; Anderson, R.J.; Kuhn, M.G. Information Hiding—A Survey. Proc. IEEE 1999, 87, 1062–1078. [Google Scholar] [CrossRef]
- Fiore, U. Selective Redundancy Removal: A Framework for Data Hiding. Futur. Internet 2010, 2, 30–40. [Google Scholar] [CrossRef]
- Yüzkollar, C.; Kocabıçak, Ü. Region based interpolation error expansion algorithm for reversible image watermarking. Appl. Soft Comput. 2015, 33, 127–135. [Google Scholar] [CrossRef]
- Dragoi, I.C.; Coltuc, D. Local-Prediction-Based Difference Expansion Reversible Watermarking. IEEE Trans. Image Process. 2014, 23, 1779–1790. [Google Scholar] [CrossRef] [PubMed]
- Puech, W.; Chaumont, M.; Strauss, O. A reversible data hiding method for encrypted images. In SPIE Electronic Imaging 2008—Security, Forensics, Steganography, and Watermarking of Multimedia Contents; Proceedings of the International Society for Optics and Photonics (SPIE), Bellingham, WA, USA, 2008; Volume 6819, pp. 1463–1475.
- Yin, Z.; Luo, B.; Hong, W. Separable and Error-Free Reversible Data Hiding in Encrypted Image with High Payload. Sci. World J. 2014, 2014, 1–8. [Google Scholar] [CrossRef] [PubMed]
- Zhang, X.; Wang, J.; Wang, Z.; Cheng, H. Lossless and Reversible Data Hiding in Encrypted Images with Public Key Cryptography. IEEE Trans. Circuits Syst. Video Technol. 2015. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Advances in Cryptology; Springer: Berlin, Germany, 1985; pp. 47–53. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public key cryptography. In Advances in Cryptology—ASIACRYPT 2003; Springer: Berlin, Germany, 2003; pp. 452–473. [Google Scholar]
- Rossi, F.; Schmid, G. Identity-based secure group communications using pairings. Comput. Netw. 2015, 89, 32–43. [Google Scholar] [CrossRef]
- Boneh, D.; Lynn, B.; Shacham, H. Short signatures from the Weil pairing. J. Cryptol. 2004, 17, 297–319. [Google Scholar] [CrossRef]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Rad, R.; Wong, K.; Guo, J.M. A Unified Data Embedding and Scrambling Method. IEEE Trans. Image Process. 2014, 23, 1463–1475. [Google Scholar] [CrossRef] [PubMed]
- Thabit, R.; Khoo, B.E. A new robust lossless data hiding scheme and its application to color medical images. Digital Signal Process. 2015, 38, 77–94. [Google Scholar] [CrossRef]
- Arroyo, D.; Diaz, J.; Rodriguez, F.B. Non-conventional Digital Signatures and Their Implementations—A Review. In International Joint Conference CISIS’15 and ICEUTE’15; Herrero, A., Baruque, B., Sedano, J., Quintián, H., Corchado, E., Eds.; Springer: Berlin, Germany, 2015; Volume 369, pp. 425–435. [Google Scholar]
- Dong, C. Jpair: A Quick Introduction. 2010. Available online: https://personal.cis.strath.ac.uk/changyu.dong/jpair/intro.html (accessed on 28 Sep 2015).
- Chatterjee, S.; Sarkar, P.; Barua, R. Efficient computation of Tate pairing in projective coordinate over general characteristic fields. In Information Security and Cryptology—ICISC 2004; Springer: Berlin, Germany, 2005; pp. 168–181. [Google Scholar]
- Lynn, B. On the Implementation of Pairing-Based Cryptosystems. Ph.D. Thesis, The Stanford University, Stanford, CA, USA, 2007. [Google Scholar]
- De Caro, A.; Iovino, V. jPBC: Java pairing based cryptography. In Proceedings of the 2011 IEEE Symposium on IEEE Computers and Communications (ISCC), Kerkyra, Geece, 28 June–1 July 2011; pp. 850–855.
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption) << cost (signature) + cost (encryption). In Advances in Cryptology—CRYPTO’97; Springer: Berlin, Germany, 1997; pp. 165–179. [Google Scholar]
- Fan, J.; Zheng, Y.; Tang, X. A new construction of Identity-Based Signcryption without Random Oracles. Int. J. Found. Comput. Sci. 2014, 25, 1–23. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fiore, U.; Rossi, F. Embedding an Identity-Based Short Signature as a Digital Watermark. Future Internet 2015, 7, 393-404. https://doi.org/10.3390/fi7040393
Fiore U, Rossi F. Embedding an Identity-Based Short Signature as a Digital Watermark. Future Internet. 2015; 7(4):393-404. https://doi.org/10.3390/fi7040393
Chicago/Turabian StyleFiore, Ugo, and Francesco Rossi. 2015. "Embedding an Identity-Based Short Signature as a Digital Watermark" Future Internet 7, no. 4: 393-404. https://doi.org/10.3390/fi7040393
APA StyleFiore, U., & Rossi, F. (2015). Embedding an Identity-Based Short Signature as a Digital Watermark. Future Internet, 7(4), 393-404. https://doi.org/10.3390/fi7040393