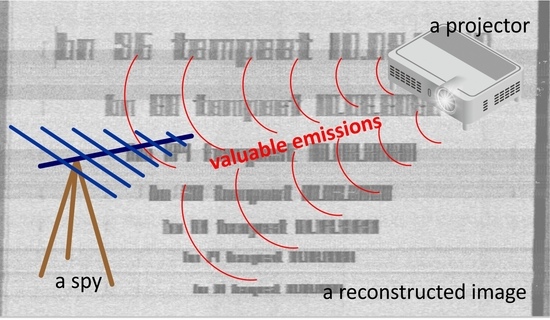
Method of Colors and Secure Fonts Used for Source Shaping of Valuable Emissions from Projector in Electromagnetic Eavesdropping Process
Abstract
:1. Introduction
2. Materials and Methods
2.1. Equipment Used and Discussion
2.2. Test Bed Setup
- to demonstrate the risk of information loss in a non-invasive way, related to the uncritical use of projectors to display information graphically;
- to propose the use of safe fonts to counteract the process of electromagnetic infiltration;
- to present the method of colors used as a solution supporting electromagnetic protection of processed graphic information;
- to indicate the method of colors as a test signal in emission safety tests according to SDIP-27/2 standard [3].
- to demonstrate the superiority of safe fonts over traditional ones in protecting text data processed by the projector against electromagnetic infiltration;
- to indicate pairs of colors that increase the level of electromagnetic safety;
- to indicate pairs of colors that increase the radiation efficiency of the source of undesirable emissions for the assessment of the device in accordance with SDIP-27/2 [3].
3. Results
4. Discussions
4.1. Video Projectors
4.1.1. The Method of Colors
4.1.2. The Method of Colors and Safe Fonts
5. Conclusions
- the safe fonts;
- the method of colors.
6. Patents
Author Contributions
Funding
Conflicts of Interest
References
- TEMPEST and EMS Policy. Available online: https://www.ncsc.gov.uk/information/tempest-and-ems-policy (accessed on 13 October 2020).
- Information Assurance Security Guidelines on Accreditation of EU TEMPEST Companies; Council of the European Union, The General Secretariat: Brussels, Belgium, 2019; Available online: https://data.consilium.europa.eu/doc/document/ST-7887-2019-INIT/en/pdf (accessed on 16 November 2012).
- NATO Standard (2009) SDIP-27/2: NATO TEMPEST Requirements and Evaluation Procedures; (Published March 2016 but not for Publicuse, NATOCONFIDENTIAL); NATO Military Committee Communication and Information Systems Security and Evaluation Agency (SECAN), Supreme Headquarters Allied Powers Europe (SHAPE): Mons, Belgium, 2009.
- EU Standard (2013) IASG 7–03: Information Assurance Security Guidelines on EU TEMPEST Requirements and Evaluation Procedures; (Published March 2016 but not for Publicuse, EUCONFIDENTIAL); General Secretariat of the Council of the European Union (GSC): Brussels, Belgium, 2013.
- Macovei, A.; Butnariu, V.; Boitan, A.; Rosu, G.; Trip, B.; Halunga, S. Detection of Electromagnetic Emissions Transmitted on the Power Line Through Electrical Conduction. In Proceedings of the International Conference on Applied and Theoretical Electricity (ICATE), Craiova, Romania, 4–6 October 2018. [Google Scholar]
- Kubiak, I. Font Design—Shape Processing of Text Information Structures in the Process of Non-Invasive Data Acquisition. Computers 2019, 8, 70. [Google Scholar] [CrossRef] [Green Version]
- Ulas, C.; Sahin, S.; Memisoglu, E.; Asık, U.; Karadeniz, C.; Kılıc, B.; Sarac, U. Automatic Tempest test and analysis system design. Int. J. Cryptogr. Inf. Secur. 2014, 4, 1–12. [Google Scholar] [CrossRef]
- Kuhn, M.G. Compromising Emanations: Eavesdropping Risks of Computer Displays; Technical Report No.577; UCAM-CL-TR-577; University of Cambridge: Cambridge, UK, 2004. [Google Scholar]
- Zhang, N.; Lu, Y.; Cui, Q.; Wang, Y. Investigation of unintentional video emanations froma VGA connector in the desktop computers. IEEE Trans. Electromagn. Compat. 2017, 59, 1826–1834. [Google Scholar] [CrossRef]
- Kubiak, I. Video signal level (colour intensity) and effectiveness of electromagnetic infiltration. Bull. Pol. Acad. Sci. Tech. Sci. 2016, 64, 207–218. [Google Scholar] [CrossRef] [Green Version]
- Kubiak, I. Influence of the method of colors on levels of electromagnetic emissions from video standards. IEEE Trans. Electromagn. Compat. 2018, 61, 1129–1137. [Google Scholar] [CrossRef]
- Boitan, A.; Bărtușică, R.; Halunga, S.; Bîndar, V. Video signal recovery from the laser printer LCD display. In Advanced Topics in Optoelectronics, Microelectronics, and Nanotechnologies, IX; Proceedings of SPIE: Bellingham, WA, USA, 2018; Volume 10977, p. 1097726. [Google Scholar] [CrossRef]
- Kubiak, I.; Loughry, J. LED Arrays of Laser Printers as Valuable Sources of Electromagnetic Waves for Acquisition of Graphic Data. Electronics 2019, 8, 1078. [Google Scholar] [CrossRef] [Green Version]
- Grzesiak, K.; Przybysz, A. Emission security of laser printers. In Concepts and Implementations for Innovative Military Communications and Information Technologies; Military University of Technology: Warsaw, Poland, 2010; Available online: https://www.wil.waw.pl/artprac/Emission_security_of_laser_printers.pdf (accessed on 13 October 2020).
- Kubiak, I. Laser printer as a source of sensitive emissions. Turk. J. Electr. Eng. Comput. Sci. 2018, 26, 1354–1366. Available online: https://pdfs.semanticscholar.org/3d8d/c38f55f1636a4f7dc62c90d4fca567f0f4e1.pdf (accessed on 13 October 2020). [CrossRef]
- Vuagnoux, M.; Pasini, S. Compromising Electromagnetic Emanations of Wired and Wireless Keyboards. In Proceedings of the USENIX Security Symposium, Montreal, QC, Canada, 10–14 August 2009; pp. 1–16. Available online: https://static.usenix.org/events/sec09/tech/full_papers/sec09_attacks.pdf (accessed on 13 October 2020).
- Boitan, A.; Bărtușică, R.; Halunga, S.; Popescu, M.; Ionuță, I. Compromising Electromagnetic Emanations of Wired USB Keyboards. In International Conference on Future Access Enablers of Ubiquitous and Intelligent Infrastructures; Springer: Cham, Switzerland, 2017; pp. 39–44. [Google Scholar] [CrossRef]
- Rognean, X.; Rosu, G.; Boitan, A.; Trip, B.; Butnariu, V.; Kasmi, C.; Fichte, L.O.; Baltag, O. Study of Compromising Emissions of PS/2 Keyboards by Correlative Methods. Rev. Roum. Des Sci. Tech. Ser. Electrotech. Energetique 2020, 65, 15–20. [Google Scholar] [CrossRef]
- Trip, B.; Butnariu, V.; Velicu, V.; Halunga, S.; Boitan, A. Analysis of PS/2 Compromising Emanations. In International Conference Advanced Topics in Optoelectronics, Microelectronics and Nanotechnologies (ATOM202020—23 August 2020, Constanta, Romania), 10th ed.; in press.
- Smulders, P. The threat of information theft by reception of electromagnetic radiation from RS-232 cables. Comput. Secur. 1990, 9, 53–58. [Google Scholar] [CrossRef]
- Boitan, A.; Halunga, S.; Bîndar, V.; Fratu, O. Compromising Electromagnetic Emanations of USB Mass Storage Devices. Wirel. Pers. Commun. 2020, 1–26. [Google Scholar] [CrossRef]
- Wampler, C.; Uluagac, S.; Beyah, R. Information leakage in encrypted IP video traffic. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–7. [Google Scholar]
- Idita, A.; Butnariu, V.; Rosu, G.; Trip, B.; Boitan, A.; Baltag, O. Study of Shielding Effectiveness on Spurious Emissions of Information Systems by Means of Metallic and Carbon Powder Screens. In Proceedings of the International Conference on Applied and Theoretical Electricity (ICATE), Craiova, Romania, 4–6 October 2018; pp. 1–6. [Google Scholar]
- Lee, H.K.; Kim, Y.H.; Kim, S.C. Emission security limits for compromising emanations using electromagnetic emanation security channel analysis. IEICE. Trans. Commun. 2013, 96, 2639–2649. [Google Scholar] [CrossRef]
- Tajima, K.; Ishikawa, R.; Mori, T.; Suzuki, Y.; Takaya, K. A study on risk evaluation of countermeasure technique for preventing electromagnetic information leakage from ITE. In Proceedings of the 2017 International Symposium on Electromagnetic Compatibility—EMCEUROPE, Angers, France, 4–7 September 2017; pp. 1–4. [Google Scholar]
- International Telecommunications Union. Mitigation Methods Against Electromagnetic Security Threats; SeriesK: Protection Against Interference; Recommendation K.115,11/2015; Telecommunication Standardization Sector of ITU: Geneva, Switzerland, 2015. [Google Scholar]
- Xie, C.H.; Wang, T.; Hao, X.; Yang, M.; Zhu, Y.; Li, Y. Localization and Frequency Identification of Large-Range Wide-Band Electromagnetic Interference Sourcesin Electromagnetic Imaging System. Electronics 2019, 8, 499. [Google Scholar] [CrossRef] [Green Version]
- Lee Ko, W. Time domain solution of electromagnetic problems. Electromagnetics 1992, 12, 403–433. [Google Scholar] [CrossRef]
- Boitan, A.; Bătuşică, R.; Halunga, S.; Fratu, O. Electromagnetic Vulner abilities of LCDP rojectors. In Proceedings of the 6th Conference on the Engineering of Computer Based Systems, Bucharest, Romania, 2–3 September 2019; University Politechnicaof Bucharest: Bucharest, Romania, 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Kubiak, I. Computer Font Resistance to Electromagnetic Infiltration. The Research and Analysis Results; Publishing House of the Military University of Technology: Warsaw, Poland, 2014. [Google Scholar]
- Kubiak, I.; Boitan, A.; Halunga, S. Assessing the Security of TEMPEST Fonts against Electromagnetic Eavesdropping by Using Different Specialized Receivers. Appl. Sci. 2020, 10, 2828. [Google Scholar] [CrossRef] [Green Version]

















| Background Color | Value of RGB—Text | ||
|---|---|---|---|
| R | G | B | |
| Black or white (RGB:000 or 255 255 255) | 0 | 0 | 0 |
| 50 | 50 | 50 | |
| 100 | 100 | 100 | |
| 150 | 150 | 150 | |
| 200 | 200 | 200 | |
| 255 | 0 | 0 | |
| 255 | 50 | 50 | |
| 255 | 100 | 100 | |
| 255 | 150 | 150 | |
| 255 | 200 | 200 | |
| 0 | 255 | 0 | |
| 50 | 255 | 50 | |
| 100 | 255 | 100 | |
| 150 | 255 | 150 | |
| 200 | 255 | 200 | |
| 0 | 0 | 255 | |
| 50 | 50 | 255 | |
| 100 | 100 | 255 | |
| 150 | 150 | 255 | |
| 200 | 200 | 255 | |
| Frequency of Revealing Emission | Text Color RGB | Background Color RGB |
|---|---|---|
| 520 MHz (Figure 14a,b) | 100, 100, 255 | 255, 255, 255 |
| 200, 200, 255 | 255, 255, 255 | |
| 520 MHz (Figure 14c–e) | 50, 50, 255 | 0, 0, 0 |
| 100, 100, 255 | 0, 0, 0 | |
| 200, 200, 255 | 0, 0, 0 | |
| 520 MHz (Figure 14f,g) | 255, 100, 100 | 0, 0, 0 |
| 255, 200, 200 | 0, 0, 0 | |
| 520 MHz (Figure 14h,i) | 50, 255, 50 | 0, 0, 0 |
| 100, 255, 100 | 0, 0, 0 | |
| 455 MHz (Figure 14j–n) | 255, 0, 0 | 255, 255, 255 |
| 255, 50, 50 | 255, 255, 255 | |
| 255, 100, 100 | 255, 255, 255 | |
| 255, 150, 150 | 255, 255, 255 | |
| 255, 200, 200 | 255, 255, 255 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Boitan, A.; Kubiak, I.; Halunga, S.; Przybysz, A.; Stańczak, A. Method of Colors and Secure Fonts Used for Source Shaping of Valuable Emissions from Projector in Electromagnetic Eavesdropping Process. Symmetry 2020, 12, 1908. https://doi.org/10.3390/sym12111908
Boitan A, Kubiak I, Halunga S, Przybysz A, Stańczak A. Method of Colors and Secure Fonts Used for Source Shaping of Valuable Emissions from Projector in Electromagnetic Eavesdropping Process. Symmetry. 2020; 12(11):1908. https://doi.org/10.3390/sym12111908
Chicago/Turabian StyleBoitan, Alexandru, Ireneusz Kubiak, Simona Halunga, Artur Przybysz, and Andrzej Stańczak. 2020. "Method of Colors and Secure Fonts Used for Source Shaping of Valuable Emissions from Projector in Electromagnetic Eavesdropping Process" Symmetry 12, no. 11: 1908. https://doi.org/10.3390/sym12111908
APA StyleBoitan, A., Kubiak, I., Halunga, S., Przybysz, A., & Stańczak, A. (2020). Method of Colors and Secure Fonts Used for Source Shaping of Valuable Emissions from Projector in Electromagnetic Eavesdropping Process. Symmetry, 12(11), 1908. https://doi.org/10.3390/sym12111908