A Review: Image Processing Techniques’ Roles towards Energy-Efficient and Secure IoT
Abstract
:1. Introduction
1.1. Image Processing’s Role in the Development of IoT Platforms and Systems
1.2. The Problem of Excessive Energy Use
1.3. A Concern with IoT Security in a Connected World
1.4. Contributions and Article Organization
1.4.1. Contributions
- (1)
- It examines a variety of publications and research studies that discuss the designing and building of IoT applications and systems that make use of image-processing techniques. These papers and studies involve the topic of designing and building IoT applications and systems;
- (2)
- It highlights a variety of contributions made by image processing techniques towards other concerns that IoT applications typically face and find difficult to overcome, such as the energy consumption made by IoT systems and the security of IoT data. These issues include: (1) The energy consumption made by IoT systems; and (2) The security of IoT data;
- (3)
- It highlights several different types of IoT applications that depend on image processing techniques, such as image processing-based IoT monitoring applications, image processing-based IoT security applications, image processing-based IoT location detection applications, IoT safety applications, and IoT healthcare applications;
- (4)
- The process of object detection is extremely important and significant since it has an impact on the decision that is made. There won’t be much of a focus on it if there isn’t an accurate edge detection mechanism, though, because so many reviewed publications have used it to finish the jobs they needed to. This article highlights and reviews a number of IoT applications that rely on the object detection process, which is considered crucial to perform such IoT-related tasks as monitoring, classification, and recognition. The applications are discussed in detail in this article;
- (5)
- It uses the PRISMA 2020 method for systematic reviews in order to emphasize precise steps on the extraction technique of the publications and how that strategy has been performed for various cascade-step phases;
- (6)
- It analyzes the reviewed articles according to various criteria;
- (7)
- It discusses a number of important aspects that made it possible for image processing to act as a connection between us and an intelligent and safe IoT environment;
- (8)
- It suggests a mind map highlighting the most important IoT systems-related issues/concerns and their solutions utilizing image processing techniques; to contribute to future research for potential improvements in this regard;
- (9)
- It provides the readers with a number of significant future trends that need to be taken into consideration by potentially interested researchers and designers.
1.4.2. Article’s Organization
2. Existing Reviews
2.1. Current Review Articles
2.2. Research Questions
3. Methodology
3.1. Extraction Process and Filtration Phases
3.1.1. Phase 1
3.1.2. Phase 2
3.1.3. Phase 3
3.2. Inclusion and Exclusion Criteria Strategy
3.3. Distribution of Extracted Papers According to Digital Libraries (DLs)
4. Literature Review
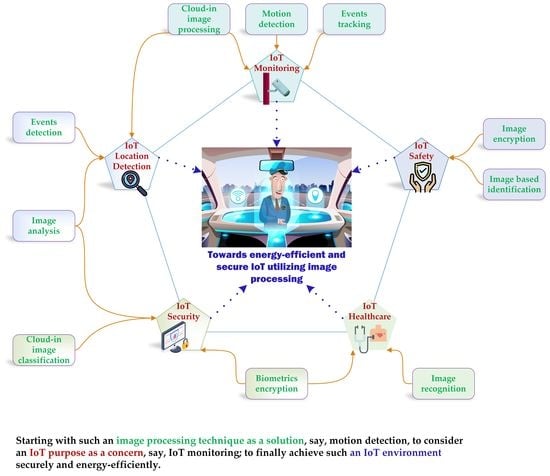
4.1. IoT Monitoring Applications Based on Image Processing
4.2. IoT Security Applications Based on Image Processing
4.3. IoT Safety Applications Based on Image Processing
4.4. IoT Location Detection Applications Based on Image Processing
4.5. IoT Healthcare Applications Based on Image Processing
5. Analysis
5.1. Distribution of Papers According to the Type of IoT Application
5.2. Distribution of Papers According to IoT Application According to the Data of Publishing
5.3. Distribution of Papers According to IoT Application vs. the Utilized Image Processing Technique
6. Discussion
6.1. Image Processing Techniques’ Roles to Address Energy Consumption for IoTSs
- Images will be uploaded to the cloud if they include information that is useful. That minimizes energy use by reducing transmission time spent [45];
- Because of advancements in image processing, transmission times have become significantly shorter. If all of the obtained multi-frame images are transmitted, it will be significantly less time than that;
- Lightweight security measures may be applied before images are sent to the IoT cloud via image processing [57]. As a direct result of this, a significant amount of processing time and available computer resources will be preserved. Thus, achieving long-term energy security is a goal.
6.2. Image Processing Techniques’ Roles to Address Security for IoTSs
6.2.1. Security of Networks
- Image processing has proposed various methods [32,68,69] to address concerns about the safety of the communication channel that runs between the image processing and the final destination. It is said that image processing techniques have a role in strengthening the security of communication channels [68].
- The technique of matching images [29,55] has been used in cloud-stored images, where it has been shown to be effective in maintaining the confidentiality of data storage and communication networks. It has helped to ensure the security and confidentiality of the image that was retrieved from its storage in the cloud. As a result of the matching procedure, communications have been made more secure [29].
6.2.2. Security of Contents
- Zigzag image encryption may be more resistant to data attacks [66];
- As a result of advancements in image processing, IoT devices and networks are now able to transmit data safely. The current conventional security scheme, in particular the two-step authentication, has been proposed to be replaced by a biometric encryption scheme that uses image processing [48];
- IoTSs stored on a server and hence subject to attack at the server level benefit from image block splitting as a security measure. Increased security and decreased attack likelihood are two benefits of block-based image encryption schemes [68];
- Encryption of images may improve the safety of the contents of images. However, improvements to this method are currently being made to enhance the functionality of privacy protection for contents of images connected to IoTSs [50];
- The matching procedure helps to increase the safety of image data associated with the IoT [29].
7. A Suggested Mind Map
8. Future Trends
- Image processing seeks to help IoT be more secure, wherein all items linked with its infrastructure are engaged. Therefore, image processing techniques are continually being improved, and as a result, research that is devoted to improving image processing techniques should also try to reflect this improvement towards the growth of IoT in terms of various factors, including the security and safety of data [48];
- When attempting to match images from both the collected and previously stored in-cloud images, it is essential that the data storage and communication networks used to do this be secure. Hence, the security of communication between the cloud and image-matching processing portion, on the one hand, and the safety and privacy of the remembered in-cloud-stored image, on the other hand, is a major concern and is a future trend of interaction between and integration of IoT and image processing;
- In the case of IoTSs, the entire system will fail if there is an issue with the security of image matching processing or with the safety of image content, regardless of whether or not the fault is discovered;
- As a result, researchers need to have been concerned with this problem and ought to have either enhanced the security of communication between IoT parties [29];
- Image processing can contribute to IoT by decreasing the distance between two distant and remote workplaces;
- In the very near future, various programs will be employed for the objective of accessing digital and sensitive workplaces;
- An authentication and verification process by a third party, which might be the owner of the digital asset, as an example, is required to guarantee not just permitted access but also the security and confidentiality of its contents;
- So, initially, the first party will apply for authorized entry to the workplace. Secondly, a captured image is transmitted to the other party for verification purposes; however, a matching process is employed to help the decision-making. The third possibility is that the other party will permit such authorized access to keep the contents secure;
- For example, security improvement and computation time required to analyze either a single image or multi-frame images will be emphasized. An IoTS may either allow or deny an access request made by the authorized person [55];
- Recently, the problem of image encryption has been extensively considered to execute an image transfer to cloud storage. For the purpose of this operation, having a secure communication method is equally as vital as having secure image content. Image-based encryption is yet to progress to serve better and help in this goal. There is a requirement to boost the performance of the IoTS that wants to transmit images to cloud storage or to a distant portion. The most crucial problem to be addressed regarding IoTS performance is the security of the images’ contents [50];
- Sending multi-frame images to the cloud with a little file size will be an important challenge in the future of IoT implementation. This is one of the key issues for both image processing and IoTSs owing to the massive storage created in the cloud. For IoTSs requiring the transmission of multi-frame images via IoT networks, a solution to this problem is to provide a system that prioritizes the transfer of particular frames depending on analysis decisions made by image processes. Images containing significant content will be uploaded to the cloud [45];
- Another important barrier to image processing in the setting of IoT-implemented systems is connected to the security of the communication channel between the source of image processing and the destination. Because of the importance of transferring digital material while maintaining the safety of the communication route, this problem is still difficult to solve. Hence, presently proposed studies are tackling this problem by observing that the security system is essential to reach a high degree of lightweight;
- In accordance with [57], a smaller image is better for IoT-cloud image transfer. The data size across IoT communication channels will be decreased as a consequence, helping to minimize overall energy usage. This will contribute to shifting energy-friendly IoT seeking to realize the vision of the development of sustainable energy. One of the future trends towards sustainable energy in the IoT environment is to use effective security schemes that serve to considerably decrease the size of the image to minimize both transmission time and size;
- One method for increasing the security of images stored in the IoT cloud or on other servers is to divide them into blocks of images, which may be used to create a double-phase security scheme for images;
- Embedding a password mechanism should have helped the attainment of the integrity target of encrypted medical images [64]. As long as you embed an OTP in the encrypted medical image, the authorized person may verify the embedded OTP by comparing it to another OTP that was transmitted via a secure channel.
9. Conclusions
9.1. Final Thoughts and Remarks
- Image processing has been used in IoT monitoring applications, according to [42];
- Image processing techniques have made a significant contribution to IoT’s ability to protect data transferred between devices and networks;
- By using a variety of image processing techniques, image processing techniques have reinforced the encryption idea applied to digital data. When comparing an image processing-based security solution to a non-image processing-based method, the number of vulnerabilities is decreased [48];
- The use of sensors and cameras for detecting movement and collecting images helps improve home safety [29];
- At the perception layer, image processing has contributed to the safe transmission of sensitive material to the network layer. Cloud-based storage will be used for the images. It is thus possible to use the proposed security strategy for a wide range of IoTSs, including cloud-enabled IoT, that require encrypting images using random and sophisticated patterns with the aid of CAs [49];
- By grouping the infected images into groups, image processing has helped identify malware assaults. Malware binaries are used to create malware images. Because malware images are classified, IoT devices impacted by an assault will be better protected in terms of security; as a result, the DDoS virus is a well-known assault against IoT devices [51];
- IoTSs have been able to benefit greatly from image processing. An image processing technique may be used to record images (as a video stream) for the purpose of performing monitoring tasks for an area or environment, such as an industrial zone containing sensitive equipment. Image processing can be used not only to analyze acquired images at the site or at the fog nodes but it can also be used to secure the communication channel between regions where images are captured and fog nodes before any transferring of these images have taken place. Creating an energy-friendly system design might lower other parameters like transmission time, bandwidth, storage, and transmission cost. In addition, image protection is a second responsibility. With the use of various image processing techniques and other mathematical models, such as the CA rule conception, it may be implemented in which images themselves can be encrypted;
- A lot of processing and computing resources will be saved using lightweight security solutions before images are sent to the IoT Cloud [57];
- According to [68], maintaining secure communication channels during image transmission isn’t enough; IoT servers devoted to image storage must also be kept at a high level of security. The probability of the secret image (or any other IoT-associated data) being hacked is reduced, and the content’s safety is improved when it is divided up into blocks;
- Embedding a password into an encrypted image that conceals medical data is possible [64]. Using a verification technique performed to the encrypted image’s embedded password and sending that password to the authorized individual improves image content security in terms of integrity;
- Many IoTSs employ image processing as a monitoring and security tool. Several related smart systems have integrated image processing-based security schemes with non-image processing-based schemes in terms of security [46,47] since image processing has played an effective role in strengthening security;
- Many IoTSs that provide location detection services have made use of image processing techniques;
- (a)
- IoTSs will be able to provide improved services in terms of object localization if image processing is used in conjunction with the cloud and IoT settings [61];
- (b)
- It is mentioned that image processing and position detection methods like GPS have been employed and exploited to increase a variety of services that are significant and critical in our everyday activities, such as the identification and prevention of plant catastrophes [62];
- (c)
- UAVs, wireless sensors, drones, cloud computing, and other technologies have all been used in conjunction with image processing to improve position recognition in open areas that may be covered by the image capture process using UAVs [25];
- Many IoT healthcare applications use image processing, such as [65]. To make IoT-related services more convenient, image processing has been used, where collected images may be analyzed remotely by people; then the necessary action can be taken via the IoT platform;
- Performing computations via the cloud in recent years, an increased emphasis has been made on the need for security in relation to both the preservation of medical data and images as well as disease prediction. The healthcare business creates enormous amounts of data on a daily basis as a result of the progress of medical technologies. Cloud computing allows for the storage and management of these enormous amounts of data in a manner that is exceptionally secure. A more secure zigzag image encryption technique is utilized to identify illnesses utilizing image processing in a safe cloud computing environment [66].
9.2. Limitations
- The search period is within a certain period of time; thus, there are a number of studies;
- There is a portion of articles that have not been included in this review due to the publishing date(s) being beyond this article’s search period;
- This review has considered two factors which means some other factors have not been considered;
- It has considered the energy consumption caused by the processing of contents-heavy images;
- It has considered the security of images’ contents;
- It has not considered the data size of digital content;
- It has considered the roles of image processing techniques in reducing energy consumption and increasing security;
- In future investigations, researchers can take into account the recently published papers and publications.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
List of Abbreviations
| AI | Artificial intelligence |
| BLE | Bluetooth low energy |
| CA | Cellular Automata |
| DDoS | Denial of service |
| DLs | Digital libraries |
| DNNs | Deep neural networks |
| EOI | Events-of-interest |
| ID | Identity |
| IoT | Internet of Things |
| IoTSs | Internet of Things (IoT)-dependent systems |
| OOI | Object-of-interest |
| OTP | One-time password |
| PIR sensor | Passive infrared sensor |
| RL | Reinforcement learning |
| ROI | Region of interest |
| SVR | Support vector regression |
| UAVs | Unmanned aerial vehicles |
| VGG | Visual Geometry Group |
References
- Hsu, C.-H.; Cheng, S.-J.; Chang, T.-J.; Huang, Y.-M.; Fung, C.-P.; Chen, S.-F. Low-Cost and High-Efficiency Electromechanical Integration for Smart Factories of IoT with CNN and FOPID Controller Design under the Impact of COVID-19. Appl. Sci. 2022, 12, 3231. Available online: https://www.mdpi.com/2076-3417/12/7/3231 (accessed on 11 November 2022). [CrossRef]
- Quy, V.K.; Hau, N.V.; Anh, D.V.; Quy, N.M.; Ban, N.T.; Lanza, S.; Randazzo, G.; Muzirafuti, A. IoT-Enabled Smart Agriculture: Architecture, Applications, and Challenges. Appl. Sci. 2022, 12, 3396. Available online: https://www.mdpi.com/2076-3417/12/7/3396 (accessed on 11 November 2022). [CrossRef]
- Sepasgozar, S.; Karimi, R.; Farahzadi, L.; Moezzi, F.; Shirowzhan, S.; Ebrahimzadeh, S.M.; Hui, F.; Aye, L. A Systematic Content Review of Artificial Intelligence and the Internet of Things Applications in Smart Home. Appl. Sci. 2020, 10, 3074. Available online: https://www.mdpi.com/2076-3417/10/9/3074 (accessed on 11 November 2022). [CrossRef]
- Othman, N.A.; Aydin, I. A face recognition method in the Internet of Things for security applications in smart homes and cities. In Proceedings of the 2018 6th International Istanbul Smart Grids and Cities Congress and Fair (ICSG), Istanbul, Turkey, 25–26 April 2018; pp. 20–24. [Google Scholar] [CrossRef]
- Taştan, M.; Gökozan, H. Real-Time Monitoring of Indoor Air Quality with Internet of Things-Based E-Nose. Appl. Sci. 2019, 9, 3435. Available online: https://www.mdpi.com/2076-3417/9/16/3435 (accessed on 11 November 2022). [CrossRef]
- Zhang, M.; Peng, B.; Chen, Y. An efficient image encryption scheme for industrial Internet-of-Things devices. In Proceedings of the 2nd International ACM Workshop on Security and Privacy for the Internet-of-Things, London, UK, 15 November 2019; pp. 38–43. [Google Scholar]
- Mat, I.; Kassim, M.R.M.; Harun, A.N.; Yusoff, I.M. Smart Agriculture Using Internet of Things. In Proceedings of the 2018 IEEE Conference on Open Systems (ICOS), Langkawi, Malaysia, 21–22 November 2018; pp. 54–59. [Google Scholar] [CrossRef]
- Jacoby, M.; Usländer, T. Digital twin and internet of things—Current standards landscape. Appl. Sci. 2020, 10, 6519. [Google Scholar] [CrossRef]
- Gu, Z.; Li, H.; Khan, S.; Deng, L.; Du, X.; Guizani, M.; Tian, Z. IEPSBP: A cost-efficient image encryption algorithm based on parallel chaotic system for green IoT. IEEE Trans. Green Commun. Netw. 2021, 6, 89–106. [Google Scholar] [CrossRef]
- Lin, C.-H.; Hu, G.-H.; Chan, C.-Y.; Yan, J.-J. Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm. Appl. Sci. 2021, 11, 1329. Available online: https://www.mdpi.com/2076-3417/11/3/1329 (accessed on 1 September 2022). [CrossRef]
- Hassan, A.; Liu, F.; Wang, F.; Wang, Y. Secure image classification with deep neural networks for IoT applications. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 8319–8337. [Google Scholar] [CrossRef]
- Vermesan, O.; Friess, P.; Guillemin, P.; Giaffreda, R.; Grindvoll, H.; Eisenhauer, M.; Serrano, M.; Moessner, K.; Spirito, M.; Blystad, L.-C. Internet of things beyond the hype: Research, innovation and deployment. In Building the Hyperconnected Society-Internet of Things Research and Innovation Value Chains, Ecosystems and Markets; River Publishers: Gistrup, Denmark, 2022; pp. 15–118. [Google Scholar]
- Bale, A.S.; Saravana Kumar, S.; Varun Yogi, S.; Vura, S.; Baby Chithra, R.; Vinay, N.; Pravesh, P. Chapter 8—Network and security leveraging IoT and image processing: A quantum leap forward. In System Assurances; Johri, P., Anand, A., Vain, J., Singh, J., Quasim, M., Eds.; Academic Press: Cambridge, MA, USA, 2022; pp. 123–141. [Google Scholar]
- Cruz, M.; Mafra, S.; Teixeira, E.; Figueiredo, F. Smart Strawberry Farming Using Edge Computing and IoT. Sensors 2022, 22, 5866. Available online: https://www.mdpi.com/1424-8220/22/15/5866 (accessed on 11 November 2022). [CrossRef]
- Debauche, O.; Mahmoudi, S.; Guttadauria, A. A New Edge Computing Architecture for IoT and Multimedia Data Management. Information 2022, 13, 89. Available online: https://www.mdpi.com/2078-2489/13/2/89 (accessed on 12 November 2022). [CrossRef]
- Malik, S.; Tyagi, A.K.; Mahajan, S. Architecture, Generative Model, and Deep Reinforcement Learning for IoT Applications: Deep Learning Perspective. In Artificial Intelligence-Based Internet of Things Systems; Pal, S., De, D., Buyya, R., Eds.; Springer International Publishing: Cham, Switzerland, 2022; pp. 243–265. [Google Scholar]
- Rahmani, A.M.; Bayramov, S.; Kiani Kalejahi, B. Internet of things applications: Opportunities and threats. Wirel. Pers. Commun. 2022, 122, 451–476. [Google Scholar] [CrossRef]
- Esposito, M.; Palma, L.; Belli, A.; Sabbatini, L.; Pierleoni, P. Recent Advances in Internet of Things Solutions for Early Warning Systems: A Review. Sensors 2022, 22, 2124. Available online: https://www.mdpi.com/1424-8220/22/6/2124 (accessed on 1 November 2022). [CrossRef] [PubMed]
- KhoKhar, F.A.; Shah, J.H.; Khan, M.A.; Sharif, M.; Tariq, U.; Kadry, S. A review on federated learning towards image processing. Comput. Electr. Eng. 2022, 99, 107818. [Google Scholar] [CrossRef]
- Rehman, A.; Saba, T.; Kashif, M.; Fati, S.M.; Bahaj, S.A.; Chaudhry, H. A Revisit of Internet of Things Technologies for Monitoring and Control Strategies in Smart Agriculture. Agronomy 2022, 12, 127. Available online: https://www.mdpi.com/2073-4395/12/1/127 (accessed on 17 November 2022). [CrossRef]
- Bhardwaj, A.; Kaushik, K.; Kumar, M. Taxonomy of Security Attacks on Internet of Things. In Security and Privacy in Cyberspace; Kaiwartya, O., Kaushik, K., Gupta, S.K., Mishra, A., Kumar, M., Eds.; Springer Nature: Singapore, 2022; pp. 1–24. [Google Scholar]
- Smmarwar, S.K.; Gupta, G.P.; Kumar, S. Deep malware detection framework for IoT-based smart agriculture. Comput. Electr. Eng. 2022, 104, 108410. [Google Scholar] [CrossRef]
- Park, S.; Park, S.H.; Park, L.W.; Park, S.; Lee, S.; Lee, T.; Lee, S.H.; Jang, H.; Kim, S.M.; Chang, H.; et al. Design and Implementation of a Smart IoT Based Building and Town Disaster Management System in Smart City Infrastructure. Appl. Sci. 2018, 8, 2239. Available online: https://www.mdpi.com/2076-3417/8/11/2239 (accessed on 20 February 2022). [CrossRef]
- Hsu, T.-C.; Tsai, Y.-H.; Chang, D.-M. The Vision-Based Data Reader in IoT System for Smart Factory. Appl. Sci. 2022, 12, 6586. Available online: https://www.mdpi.com/2076-3417/12/13/6586 (accessed on 1 November 2022). [CrossRef]
- Sharma, A.; Singh, P.K.; Kumar, Y. An integrated fire detection system using IoT and image processing technique for smart cities. Sustain. Cities Soc. 2020, 61, 102332. [Google Scholar] [CrossRef]
- Wang, C.; Han, Y.; Wang, W. An End-to-End Deep Learning Image Compression Framework Based on Semantic Analysis. Appl. Sci. 2019, 9, 3580. Available online: https://www.mdpi.com/2076-3417/9/17/3580 (accessed on 26 February 2022). [CrossRef]
- Jia, Z.; Xu, S.; Mu, S.; Tao, Y. Learning-Based Text Image Quality Assessment with Texture Feature and Embedding Robustness. Electronics 2022, 11, 1611. Available online: https://www.mdpi.com/2079-9292/11/10/1611 (accessed on 11 November 2022). [CrossRef]
- Barriga, J.J.; Sulca, J.; León, J.L.; Ulloa, A.; Portero, D.; Andrade, R.; Yoo, S.G. Smart Parking: A Literature Review from the Technological Perspective. Appl. Sci. 2019, 9, 4569. Available online: https://www.mdpi.com/2076-3417/9/21/4569 (accessed on 27 February 2022). [CrossRef]
- Dorothy, A.B.; Kumar, S.B.R.; Sharmila, J.J. IoT Based Home Security through Digital Image Processing Algorithms. In Proceedings of the 2017 World Congress on Computing and Communication Technologies (WCCCT), Tiruchirappalli, India, 2–4 February 2017; pp. 20–23. [Google Scholar] [CrossRef]
- Awan, M.J.; Bilal, M.H.; Yasin, A.; Nobanee, H.; Khan, N.S.; Zain, A.M. Detection of COVID-19 in Chest X-ray Images: A Big Data Enabled Deep Learning Approach. Int. J. Environ. Res. Public Health 2021, 18, 10147. Available online: https://www.mdpi.com/1660-4601/18/19/10147 (accessed on 3 March 2022). [CrossRef]
- Anuradha, M.; Jayasankar, T.; Prakash, N.B.; Sikkandar, M.Y.; Hemalakshmi, G.R.; Bharatiraja, C.; Britto, A.S.F. IoT enabled cancer prediction system to enhance the authentication and security using cloud computing. Microprocess. Microsyst. 2021, 80, 103301. [Google Scholar] [CrossRef]
- Godavarthi, B.; Nalajala, P.; Ganapuram, V. Design and implementation of vehicle navigation system in urban environments using internet of things (IoT). In Proceedings of the IOP Conference Series: Materials Science and Engineering, Hyderabad, India, 3–4 July 2017; p. 012262. [Google Scholar]
- Kapoor, A.; Bhat, S.I.; Shidnal, S.; Mehra, A. Implementation of IoT (Internet of Things) and Image processing in smart agriculture. In Proceedings of the 2016 International Conference on Computation System and Information Technology for Sustainable Solutions (CSITSS), Bengaluru, India, 12 December 2016; pp. 21–26. [Google Scholar]
- Bharath, V.; Adyanth, H.; Shreekanth, T.; Suresh, N.; Ananya, M. Intelligent sockets for home automation and security: An approach through IoT and image processing. In The IoT and the Next Revolutions Automating the World; IGI Global: Hershey, PA, USA, 2019; pp. 252–279. [Google Scholar]
- Bolhasani, H.; Mohseni, M.; Rahmani, A.M. Deep learning applications for IoT in health care: A systematic review. Inform. Med. Unlocked 2021, 23, 100550. [Google Scholar] [CrossRef]
- Haghi Kashani, M.; Madanipour, M.; Nikravan, M.; Asghari, P.; Mahdipour, E. A systematic review of IoT in healthcare: Applications, techniques, and trends. J. Netw. Comput. Appl. 2021, 192, 103164. [Google Scholar] [CrossRef]
- Gnoni, M.G.; Bragatto, P.A.; Milazzo, M.F.; Setola, R. Integrating IoT technologies for an “intelligent” safety management in the process industry. Procedia Manuf. 2020, 42, 511–515. [Google Scholar] [CrossRef]
- Nauman, A.; Qadri, Y.A.; Amjad, M.; Zikria, Y.B.; Afzal, M.K.; Kim, S.W. Multimedia Internet of Things: A Comprehensive Survey. IEEE Access 2020, 8, 8202–8250. [Google Scholar] [CrossRef]
- Bharadwaj, H.K.; Agarwal, A.; Chamola, V.; Lakkaniga, N.R.; Hassija, V.; Guizani, M.; Sikdar, B. A Review on the Role of Machine Learning in Enabling IoT Based Healthcare Applications. IEEE Access 2021, 9, 38859–38890. [Google Scholar] [CrossRef]
- Al-Dhief, F.T.; Latiff, N.M.A.; Malik, N.N.N.A.; Salim, N.S.; Baki, M.M.; Albadr, M.A.A.; Mohammed, M.A. A Survey of Voice Pathology Surveillance Systems Based on Internet of Things and Machine Learning Algorithms. IEEE Access 2020, 8, 64514–64533. [Google Scholar] [CrossRef]
- Cui, F. Deployment and integration of smart sensors with IoT devices detecting fire disasters in huge forest environment. Comput. Commun. 2020, 150, 818–827. [Google Scholar] [CrossRef]
- Abas, K.; Obraczka, K.; Miller, L. Solar-powered, wireless smart camera network: An IoT solution for outdoor video monitoring. Comput. Commun. 2018, 118, 217–233. [Google Scholar] [CrossRef]
- Punyavathi, G.; Neeladri, M.; Singh, M.K. Vehicle tracking and detection techniques using IoT. Mater. Today Proc. 2021, 51, 909–913. [Google Scholar] [CrossRef]
- Santhanakrishnan, C.; Annapurani, K.; Singh, R.; Krishnaveni, C. An IOT based system for monitoring environmental and physiological conditions. Mater. Today Proc. 2021, 46, 3832–3840. [Google Scholar] [CrossRef]
- Muhammad, K.; Hamza, R.; Ahmad, J.; Lloret, J.; Wang, H.; Baik, S.W. Secure Surveillance Framework for IoT Systems Using Probabilistic Image Encryption. IEEE Trans. Ind. Inform. 2018, 14, 3679–3689. [Google Scholar] [CrossRef]
- Aydin, I.; Othman, N.A. A new IoT combined face detection of people by using computer vision for security application. In Proceedings of the 2017 International Artificial Intelligence and Data Processing Symposium (IDAP), Malatya, Turkey, 16–17 September 2017; pp. 1–6. [Google Scholar]
- Patil, N.; Ambatkar, S.; Kakde, S. IoT based smart surveillance security system using raspberry Pi. In Proceedings of the 2017 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 6–8 April 2017; pp. 344–348. [Google Scholar] [CrossRef]
- Hossain, M.S.; Muhammad, G.; Rahman, S.M.M.; Abdul, W.; Alelaiwi, A.; Alamri, A. Toward end-to-end biomet rics-based security for IoT infrastructure. IEEE Wirel. Commun. 2016, 23, 44–51. [Google Scholar] [CrossRef]
- Roy, S.; Rawat, U.; Sareen, H.A.; Nayak, S.K. IECA: An efficient IoT friendly image encryption technique using programmable cellular automata. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 5083–5102. [Google Scholar] [CrossRef]
- Roy, S.; Shrivastava, M.; Pandey, C.V.; Nayak, S.K.; Rawat, U. IEVCA: An efficient image encryption technique for IoT applications using 2-D Von-Neumann cellular automata. Multimed. Tools Appl. 2021, 80, 31529–31567. [Google Scholar] [CrossRef]
- Su, J.; Vasconcellos, D.V.; Prasad, S.; Sgandurra, D.; Feng, Y.; Sakurai, K. Lightweight Classification of IoT Malware Based on Image Recognition. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018; pp. 664–669. [Google Scholar] [CrossRef]
- Balla, P.B.; Jadhao, K.T. IoT Based Facial Recognition Security System. In Proceedings of the 2018 International Conference on Smart City and Emerging Technology (ICSCET), Mumbai, India, 5 January 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Wang, K.; Chen, C.-M.; Hossain, M.S.; Muhammad, G.; Kumar, S.; Kumari, S. Transfer reinforcement learning-based road object detection in next generation IoT domain. Comput. Netw. 2021, 193, 108078. [Google Scholar] [CrossRef]
- Sharmila, V.; Rejin Paul, N.R.; Ezhumalai, P.; Reetha, S.; Naresh Kumar, S. IOT enabled smart assistance system using face detection and recognition for visually challenged people. Mater. Today Proc. 2020. [Google Scholar] [CrossRef]
- Nag, A.; Nikhilendra, J.N.; Kalmath, M. IOT Based Door Access Control Using Face Recognition. In Proceedings of the 2018 3rd International Conference for Convergence in Technology (I2CT), Pune, India, 6–8 April 2018; pp. 1–3. [Google Scholar] [CrossRef]
- Li, X.; Li, J.; Yiu, S.; Gao, C.; Xiong, J. Privacy-preserving edge-assisted image retrieval and classification in IoT. Front. Comput. Sci. 2019, 13, 1136–1147. [Google Scholar] [CrossRef]
- Arunkumar, S.; Vairavasundaram, S.; Ravichandran, K.S.; Ravi, L. RIWT and QR factorization based hybrid robust image steganography using block selection algorithm for IoT devices. J. Intell. Fuzzy Syst. 2019, 36, 4265–4276. [Google Scholar] [CrossRef]
- Rukmani, P.; Teja, G.K.; Vinay, M.S. Industrial Monitoring Using Image Processing, IoT and Analyzing the Sensor Values Using Big Data. Procedia Comput. Sci. 2018, 133, 991–997. [Google Scholar] [CrossRef]
- Franco, J.D.; Ramirez-delReal, T.A.; Villanueva, D.; Gárate-García, A.; Armenta-Medina, D. Monitoring of Ocimum basilicum seeds growth with image processing and fuzzy logic techniques based on Cloudino-IoT and FIWARE platforms. Comput. Electron. Agric. 2020, 173, 105389. [Google Scholar] [CrossRef]
- Mahesh, N.; Baluprithviraj, K.N.; Anbarasu, L.; Balaji, B.; Saravana Kumar, U.; Sathish Kumar, S. Quality inspection system using IoT and image processing. Mater. Today: Proc. 2021. [Google Scholar] [CrossRef]
- Alletto, S.; Cucchiara, R.; Fiore, G.D.; Mainetti, L.; Mighali, V.; Patrono, L.; Serra, G. An Indoor Location-Aware System for an IoT-Based Smart Museum. IEEE Internet Things J. 2016, 3, 244–253. [Google Scholar] [CrossRef]
- Kitpo, N.; Inoue, M. Early Rice Disease Detection and Position Mapping System using Drone and IoT Architecture. In Proceedings of the 2018 12th South East Asian Technical University Consortium (SEATUC), Yogyakarta, Indonesia, 12–13 March 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Elhoseny, M.; Ramírez-González, G.; Abu-Elnasr, O.M.; Shawkat, S.A.; Arunkumar, N.; Farouk, A. Secure Medical Data Transmission Model for IoT-Based Healthcare Systems. IEEE Access 2018, 6, 20596–20608. [Google Scholar] [CrossRef]
- Rajagopalan, S.; Janakiraman, S.; Rengarajan, A.; Rethinam, S.; Arumugham, S.; Saravanan, G. IoT Framework for Secure Medical Image Transmission. In Proceedings of the 2018 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 4–6 January 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Jebadurai, J.; Dinesh Peter, J. Super-resolution of retinal images using multi-kernel SVR for IoT healthcare applications. Future Gener. Comput. Syst. 2018, 83, 338–346. [Google Scholar] [CrossRef]
- Deepika, J.; Rajan, C.; Senthil, T. Security and Privacy of Cloud- and IoT-Based Medical Image Diagnosis Using Fuzzy Convolutional Neural Network. Comput. Intell. Neurosci. 2021, 2021, 6615411. [Google Scholar] [CrossRef]
- Anandkumar, R.; Dinesh, K.; Obaid, A.J.; Malik, P.; Sharma, R.; Dumka, A.; Singh, R.; Khatak, S. Securing e-Health application of cloud computing using hyperchaotic image encryption framework. Comput. Electr. Eng. 2022, 100, 107860. [Google Scholar]
- Li, Y.; Tu, Y.; Lu, J.; Wang, Y. A Security Transmission and Storage Solution about Sensing Image for Blockchain in the Internet of Things. Sensors 2020, 20, 916. [Google Scholar] [CrossRef]
- Zadobrischi, E. Analysis and Experiment of Wireless Optical Communications in Applications Dedicated to Mobile Devices with Applicability in the Field of Road and Pedestrian Safety. Sensors 2022, 22, 1023. Available online: https://www.mdpi.com/1424-8220/22/3/1023 (accessed on 11 November 2022). [CrossRef] [PubMed]
- Vanitha, V.; Akila, D. Efficient Computation of Hepatitis Blood Smear Image Encryption Using Enhanced Chaotic Technique for Cloud Storage. In Soft Computing: Theories and Applications; Springer: Berlin/Heidelberg, Germany, 2022; pp. 845–855. [Google Scholar]
















| Ref. | Existing Reviews’ Concerns | Existing Reviews’ Areas |
|---|---|---|
| [35] | Deep learning applications for IoT | IoT healthcare |
| [36] | Techniques related to IoT healthcare | IoT healthcare and e-health |
| [37] | Industrial solutions applied to developments of IoT technologies | Smart objects integrating IoT |
| [38] | Multimedia Internet of Things (M-IoT) applications related to road traffic management, security, industry, and health | M-IoT |
| [39] | Machine learning methods and algorithms assigned to Healthcare Internet of Things (H-IoT) | H-IoT |
| [40] | Machine learning algorithms for IoT devices | Image classification for IoT in the healthcare sector |
| Indexing Service | Scopus OR WOS |
|---|---|
| Database names | IEEE Xplore, ScienceDirect, MDPI, SpringerLink, IOS Press, and Hindawi |
| Search period | 25 February 2022 to 10 March 2022 |
| Paper publishing date | 2016 to 2021 |
| Type of papers collected | Conference proceedings & Journals |
| Scope of a candidate paper | IoT systems, Image processing for IoT applications, IoT healthcare, IoT security applications, and IoT monitoring systems utilizing image processing |
| Image processing related | Image processing techniques considering edge detection, object recognition, video surveillance |
| IoT systems related | IoT Applications such as healthcare, security, and energy-efficient systems. |
| IoT and image processing techniques related | IoT systems using image processing techniques such as smart alert, phenomena detection, e.g., fire detection, hazard objects detection |
| Paper selection | NOT a newspaper, demonstration, poster, or extended abstract. |
| IoT System or Application (Scenario) | ||||||
|---|---|---|---|---|---|---|
| Monitoring | Security | Safety | Location Detection | Healthcare | ||
| Image processing technique (Solution) | Motion detection | × | ||||
| Events detection & tracking | × | × | ||||
| Cloud image processing & analysis | × | × | ||||
| Security scheme | × | × | ||||
| Face recognition | × | × | × | |||
| Biometrics encryption | × | |||||
| Image matching | × | |||||
| Image analysis | × | × | ||||
| Image contents protection | × | |||||
| Image-based identification | × | |||||
| Image content reduction | ||||||
| Image encryption | × | × | × | |||
| Medical image diagnosis | × | |||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Ghaili, A.M.; Kasim, H.; Hassan, Z.; Al-Hada, N.M.; Othman, M.; Kasmani, R.M.; Shayea, I. A Review: Image Processing Techniques’ Roles towards Energy-Efficient and Secure IoT. Appl. Sci. 2023, 13, 2098. https://doi.org/10.3390/app13042098
Al-Ghaili AM, Kasim H, Hassan Z, Al-Hada NM, Othman M, Kasmani RM, Shayea I. A Review: Image Processing Techniques’ Roles towards Energy-Efficient and Secure IoT. Applied Sciences. 2023; 13(4):2098. https://doi.org/10.3390/app13042098
Chicago/Turabian StyleAl-Ghaili, Abbas M., Hairoladenan Kasim, Zainuddin Hassan, Naif Mohammed Al-Hada, Marini Othman, Rafiziana Md. Kasmani, and Ibraheem Shayea. 2023. "A Review: Image Processing Techniques’ Roles towards Energy-Efficient and Secure IoT" Applied Sciences 13, no. 4: 2098. https://doi.org/10.3390/app13042098
APA StyleAl-Ghaili, A. M., Kasim, H., Hassan, Z., Al-Hada, N. M., Othman, M., Kasmani, R. M., & Shayea, I. (2023). A Review: Image Processing Techniques’ Roles towards Energy-Efficient and Secure IoT. Applied Sciences, 13(4), 2098. https://doi.org/10.3390/app13042098