1. Introduction
Iterative Learning Control theory (ILC; the staple of ILC can be found in a U.S. patent filled in 1967 and available in 1971 [
1]) is basically a control strategy to improve transient response (or similarly, the controller performance) of dynamical systems that operate repetitively (also called
multi-pass or
repetitive dynamic processes). This is done by adjusting the system control input(s) during the system cycle operations [
1,
2,
3,
4]. Because the system executes the same task multiple times, the control law may learn from the previous system action (or iteration). Hence, the central challenger of ILC design is to use this information from the previous operation to learn and improve the controller execution over the next iteration by following a control objective. Basically, a repetitive dynamic system is a process that has the following two properties:
Repetitive action, and
Iteration.
The first one is the process action that it is periodically repeated, and the second one is the natural iteration between the plant vector state and the repetitive process action.
On the other hand, ILC control strategy has been widely employed in many industrial applications, including manufacturing, robotics, chemical process, among many others [
1]. Furthermore, the main benefits of iterative learning control framework are its low transient tracking error, despite large model uncertainty and disturbances [
1,
5,
6], its short a priori knowledge about the system to be controlled, and its low computational effort for control realization [
7].
To note, ILC theory has also been used in system modeling, two-dimensional systems analysis, linear matrix inequality system design, and in adaptive and robust control innovation (see, for instance, [
5,
6] and references therein). In the meantime, some other ILC strategies are mainly based on Lyapunov’s theory [
8,
9,
10].
Finally, many of the available ILC approaches require identical
resetting initial conditions (at the beginning of each iteration: the well known
resetting condition); however, in real applications, the perfect resetting condition may be not realizable [
6,
8]. Therefore, under different tests on resetting initial conditions, the boundedness along the time evolution and asymptotic stability on each iteration of an ILC system were well proven in [
8]. Actually, this is an important robust property of the ILC tool to design new engineering developments, such as secure communication systems subject to noisy environments.
In this paper, motivated by the
canonical ILC structure stated in [
8], a chaotic secure communication scheme is developed. This design is based on the chaotic logistic-map. Therefore, the proposed design uses the ILC method as a base tool to encrypt and decrypt a message, recalling that the development of new chaotic secure communication systems is still an important open topic [
11,
12,
13,
14,
15].
The remainder of this paper is organized as follows. In
Section 2, the canonical ILC frame is retrieved from [
8].
Section 3 presents our ILC chaotic secure communication system design. Performance numerical evaluation of our scheme is evidenced in
Section 4. Finally, the conclusions are given in
Section 5, including future issues on the subject.
2. The Canonical ILC System
Let us consider the next first-order nonlinear system in the
i-th iteration [
8]:
where
is a known nonlinear function which can be locally Lipschitz,
is the
unknown time-varying parameter, and
T represents the iteration (or operation) time.
Given the reference trajectory supplied by:
where
is a known smooth-function and
r is a reference input signal which produces a bounded response
over the time interval
, the
ILC objective is to find a sequence of appropriate control inputs
for
such that the system state
tracks (as well as possible) the reference trajectory
as
[
8].
A solution to the ILC objective is as follows [
8]:
where
,
and
is the
parameter projection bound, assumed sufficiently large. According to [
8], this ILC—even under random and bounded initial conditions
(if
implies
ideal resetting condition.)—assures the ILC control objective. Finally, the
learning parameter
gives an estimation of the time-varying parameter
over each iteration of the repetitive process.
3. Chaotic Secure Communication Design Based on ILC Theory
This section presents our secure communication system design by employing the chaotic logistic-map and by using the ILC framework as a tool to encrypt and decrypt a message. We are going to use its property for the estimation of the unknown time-varying parameter .
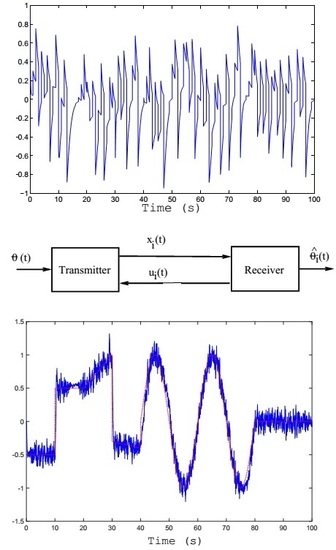
To begin with, let us refer to the main block diagram shown in
Figure 1. Allow us to define the
transmitter block as:
The initial conditions
means that the end state of the preceding iteration becomes the initial state for the new one. Here,
represents the message to be encrypted. In our design, we are using a two-channel communication system. The transmitted signal
goes on one channel, and on the other travels the generated signal
coming from the receiver (see
Figure 1). Both signals have to be in
random-like behavior with the message encrypted in
. Then,
becomes the decrypted signal (an estimation of the transmitted message in
). To complete our design for the transmitter section, let us define
, a
mimic expression from the chaotic logistic-map.
Now,
designing the
receiver block as:
where
is realized by employing the well-known discrete-time
chaotic logistic-system:
The output of the logistic-map
(utilized as the reference signal
to
) is assumed being performed having a
zero-order-holder device (ZOH),
T being the time duration between discrete-time samples. Recall that the
ZOH device is a transformation mechanism to translate a
discrete-time signal to a piece-wise
continuous-time one (see, for instance, Chapter 1 in [
16]).
Stability issue—The stability issue of the overall closed-loop communication system is warranted by the results given in [
9] and stated in
Section 2, including its robustness property.
4. Numerical Experiments
To display numerical experiment results, let us complete our secure communication design by using
s,
Rad, and
, and again,
. The test message used as
and the obtained estimation of the message
at the receiver part are shown in
Figure 2.
Figure 3 shows
and
. We can appreciate a random-like behavior on these, due to the chaotic logistic-map employed in our system. Because they are too similar,
Figure 4 displays a zoomed-in version of the error dynamic. The signal
is pictured in
Figure 5. Finally,
Figure 6 illustrates the numerical results when random noises are presented on each channel of the communication system, where we insert uncorrelated normal distribution noises with zero mean and standard deviation of
. For comparison,
Figure 7 displays the error dynamic for the noisy case. From this, we can note that the external noise helps, in some way, to better hide our secret message.
5. Conclusions
This paper has described an application of the ILC theory to secure communication system design by using a chaotic signal obtained from the chaotic-logistic map. It was also evidenced that the main important benefit of the proposed ILC given in [
8] is robustness, even on variation in the resetting initial conditions and exogenous noise. From our secure communication system, an important design parameter is the
T-time duration of each cycle. By reducing it, we may be able to employ our system to more “faster-time” message signals. It is worth mentioning that the ILC method belongs to the
data-driven systems, due to data measurement used in its learning algorithm [
17].
Finally, we believe that it is important to highlight that the main aim of this paper is to illustrate a kind of academic example of an application of the ILC theory to secure communication system design based on chaotic signals. However, and because it is beyond the author’s expertise, an additional analysis test is missing; for instance, the bit error rate curve over AWGN (Additive White Gaussian Noise) channel, including the possibility to expand our design by using the latest works on chaotic waveform to convey data such as DCSK (Differential Chaos Shift Keying), NR-DCSK (Noise Reduction Differential Chaos Shift Keying), and so on. All of these are left for a future work.