Reversible Data Hiding in Encrypted Color Halftone Images with High Capacity
Abstract
:1. Introduction
- (1)
- Only the halftone image joins the embedding process. Fu and Oscar proposed RDH-EH algorithm by forced complementary toggling at pseudo-random locations if only the halftone image is available [25]. Lien et al. introduced a high-capacity RDH method for ordered dithered halftone images, which applied dither matrix to pixel pairs so that abundant data can be hidden into these pixel pairs [26]. Kim et al. proposed a separable RDH algorithm, which used Hamming codes to embed watermark [27].
- (2)
- The continuous-tone image joins the embedding process. For the situation in which the original continuous-tone image is available, Fu and Oscar proposed an algorithm that integrates the data hiding operation into the error diffusion process [25]. Lo et al.’s algorithm embedded the binary data into the halftone images with reference to the original continuous-tone image by evaluating the absolute difference between the neighboring gray-level pixels [28]. This method is extended from that of Fu and Au [25].
2. Related Works
3. Proposed Scheme
3.1. Image Encryption
3.2. Data Embedding
- (1)
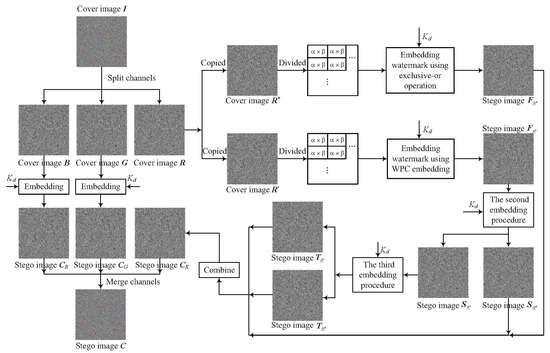
- Taking cover image as an example, for the first WPC embedding, the service provider first copies it into two identical cover images and . We partition each of them into non-overlapping blocks of size ; each block is denoted as and , where w is the total number of blocks for each channel image:where rounds x to the nearest integer towards .The service provider first encrypts the watermark bywhere , because we perform the embedding process three times on one channel image and there are three channels, is the encrypted watermark, and is determined via standard stream cipher using data-hiding key . Then, for every four bits of each , we group them to a block. Thus, the jth watermark block is obtained asFor cover image , we read one block , and convert it into a column vector . Let the first four elements of be the dry elements of WPC. Generate the pseudo-random binary matrix of dimensions by using . Then, to generate the column vector , which satisfieswe need first calculate according to Equation (3). Next, the exclusive-or operations between and are implemented. After that, the last four columns of each are removed to form . Finally, is solved based on the solvability of the linear equations and thenHaving , new blocks are formed and, then, these blocks are combined to produce stego image by following raster scanning order.As for cover image , we embed each watermark vector into . First, the first four bits of each block are converted to a vector . Then, embed watermark vector into byAfter all blocks of are modified, we obtain new blocks and also stego image .
- (2)
- For the second WPC embedding, we take image as the cover image. The same as the above procedure, the service provider first copies into two identical images and . For cover image , we take the same WPC embedding operation as in Step (1) and then generate stego image . For cover image , we embed watermark vector in it and then we get stego image .
- (3)
- As for the third WPC embedding, we take image as the cover image and copy it into two same images and . After the third embedding procedure, stego images and are produced.
- (4)
- Finally, we combine four images , , , and into one image using . As demonstrated in Figure 3, supposing that each image is sized and the pixels are represented by different color, we stagger-stitch these pixels up–down and left–right.
| Algorithm 1 Data embedding. |
Input: Cover image , watermark , and data-hiding key Output: Stego image
|
3.3. Extraction and Recovery
| Algorithm 2 Extraction and recovery. |
Input: Stego image , secret key and Output: Original halftone image and watermark
|
3.3.1. Watermark Extraction
3.3.2. Image Recovery
4. Experimental Results and Discussions
4.1. Reversibility
4.2. Security
4.3. Embedding Capacity
4.4. Quality of the Marked Image
4.5. Computational Complexity
4.6. Feature Comparisons
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Cox, I.; Miller, M.; Bloom, J.; Fridrich, J.; Kalker, T. Digital Watermarking and Steganography; Morgan Kaufmann: San Francisco, CA, USA, 2007. [Google Scholar]
- Chen, C.; Xiang, B.; Liu, Y.; Wang, K. A Secure Authentication Protocol for Internet of Vehicles. IEEE Access 2019, 7, 12047–12057. [Google Scholar] [CrossRef]
- Wu, T.Y.; Chen, C.M.; Wang, F.; Meng, C.; Wang, E.K. A provably secure certificateless public key encryption with keyword search. J. Chin. Inst. Eng. 2019, 42, 1–9. [Google Scholar] [CrossRef]
- Pan, J.S.; Lee, C.Y.; Sghaier, A.; Zeghid, M.; Xie, J. Novel Systolization of Subquadratic Space Complexity Multipliers Based on Toeplitz Matrix-Vector Product Approach. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 1614–1622. [Google Scholar] [CrossRef]
- Zhang, W.; Ma, K.; Yu, N. Reversibility improved data hiding in encrypted images. Signal Process. 2014, 94, 118–127. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Zhang, L.; Qin, Z.; Sun, X.; Ren, K. A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2594–2608. [Google Scholar] [CrossRef]
- Qian, Z.; Xu, H.; Luo, X.; Zhang, X. New framework of reversible data hiding in encrypted JPEG bitstreams. IEEE Trans. Circuits Syst. Video Technol. 2018, 29, 351–362. [Google Scholar] [CrossRef]
- Shi, H.; Liu, D.; Lu, H.; Zhou, C. A homomorphic encrypted reversible information hiding scheme for integrity authentication and piracy tracing. Multimed. Tools Appl. 2018, 77, 20535–20567. [Google Scholar] [CrossRef]
- Yang, C.H.; Tsai, M.H. Improving histogram-based reversible data hiding by interleaving predictions. IET Image Process. 2010, 4, 223–234. [Google Scholar] [CrossRef] [Green Version]
- Luo, H.; Pan, T.; Pan, J.; Chu, S.; Yang, B. Development of a Three-Dimensional Multimode Visual Immersive System With Applications in Telepresence. IEEE Syst. J. 2017, 11, 2818–2828. [Google Scholar] [CrossRef]
- Weng, S.; Chen, Y.; Ou, B.; Chang, C.; Zhang, C. Improved K-Pass Pixel Value Ordering Based Data Hiding. IEEE Access 2019, 7, 34570–34582. [Google Scholar] [CrossRef]
- Fridrich, J.; Goljan, M.; Du, R. Lossless data embedding for all image formats. In Security and Watermarking of Multimedia Contents IV; International Society for Optics and Photonics: Orlando, FL, USA, 2002; Volume 4675, pp. 572–583. [Google Scholar]
- Weng, S.; Pan, J.s.; Li, L. Reversible data hiding based on an adaptive pixel-embedding strategy and two-layer embedding. Inf. Sci. 2016, 369, 144–159. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef] [Green Version]
- Du, Y.; Yin, Z.; Zhang, X. Improved lossless data hiding for jpeg images based on histogram modification. Comput. Mater. Contin. 2018, 55, 495–507. [Google Scholar]
- Tai, W.L.; Yeh, C.M.; Chang, C.C. Reversible data hiding based on histogram modification of pixel differences. IEEE Trans. Circuits Syst. Video Technol. 2009, 19, 906–910. [Google Scholar]
- Luo, L.; Chen, Z.; Chen, M.; Zeng, X.; Xiong, Z. Reversible image watermarking using interpolation technique. IEEE Trans. Inf. Forensics Secur. 2009, 5, 187–193. [Google Scholar]
- Puech, W.; Chaumont, M.; Strauss, O. A reversible data hiding method for encrypted images. In Security, Forensics, Steganography, and Watermarking of Multimedia Contents X; International Society for Optics and Photonics: Orlando, FL, USA, 2008; Volume 6819, p. 68191E. [Google Scholar]
- Zhang, X. Reversible data hiding in encrypted image. IEEE Signal Process. Lett. 2011, 18, 255–258. [Google Scholar] [CrossRef]
- Hong, W.; Chen, T.S.; Wu, H.Y. An improved reversible data hiding in encrypted images using side match. IEEE Signal Process. Lett. 2012, 19, 199–202. [Google Scholar] [CrossRef]
- Zhang, X. Separable reversible data hiding in encrypted image. IEEE Trans. Inf. Forensics Secur. 2012, 7, 826–832. [Google Scholar] [CrossRef]
- Qian, Z.; Zhang, X.; Wang, S. Reversible data hiding in encrypted JPEG bitstream. IEEE Trans. Multimed. 2014, 16, 1486–1491. [Google Scholar] [CrossRef]
- Ma, K.; Zhang, W.; Zhao, X.; Yu, N.; Li, F. Reversible data hiding in encrypted images by reserving room before encryption. IEEE Trans. Inf. Forensics Secur. 2013, 8, 553–562. [Google Scholar] [CrossRef]
- Fu, Y.; Kong, P.; Yao, H.; Tang, Z.; Qin, C. Effective reversible data hiding in encrypted image with adaptive encoding strategy. Inf. Sci. 2019, 494, 21–36. [Google Scholar] [CrossRef]
- Fu, M.S.; Au, O.C. Data hiding watermarking for halftone images. IEEE Trans. Image Process. 2002, 11, 477–484. [Google Scholar]
- Lien, B.K.; Lin, Y.M.; Lee, K.Y. High-capacity reversible data hiding by Maximum-span pixel Pairing on ordered dithered halftone images. In Proceedings of the 2012 IEEE 19th International Conference on Systems, Signals and Image Processing (IWSSIP), Vienna, Austria, 11–13 April 2012; pp. 76–79. [Google Scholar]
- Kim, C.; Shin, D.; Leng, L.; Yang, C.N. Separable reversible data hiding in encrypted halftone image. Displays 2018, 55, 71–79. [Google Scholar] [CrossRef]
- Lo, C.C.; Lee, C.M.; Liao, B.Y.; Pan, J.S. Halftone Image Data Hiding with Reference to Original Multitone Image. In Proceedings of the 2008 IEEE International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Harbin, China, 15–17 August 2008; pp. 265–268. [Google Scholar]
- Naor, M.; Shamir, A. Visual cryptography. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1994; pp. 1–12. [Google Scholar]
- Yan, B.; Xiang, Y.; Hua, G. Improving the Visual Quality of Size-Invariant Visual Cryptography for Grayscale Images: An Analysis-by-Synthesis (AbS) Approach. IEEE Trans. Image Process. 2019, 28, 896–911. [Google Scholar] [CrossRef]
- Stallings, W. The RC4 stream encryption algorithm. In Cryptography and Network Security; Prentice Hall: Upper Saddle River, NJ, USA, 2005. [Google Scholar]
- Mohr, A. Quantum Computing in Complexity Theory and Theory of Computation; Business in Calgary: Carbondale, IL, USA, 2014. [Google Scholar]
- Lien, B.K.; Lin, Y.m. High-capacity reversible data hiding by maximum-span pairing. Multimed. Tools Appl. 2011, 52, 499–511. [Google Scholar] [CrossRef]
- Chen, Y.Y.; Chen, W.S. High-quality blind watermarking in halftones using random toggle approach. Multimed. Tools Appl. 2018, 77, 8019–8041. [Google Scholar] [CrossRef]
- Jia, Y.; Yin, Z.; Zhang, X.; Luo, Y. Reversible data hiding based on reducing invalid shifting of pixels in histogram shifting. Signal Process. 2019, 163, 238–246. [Google Scholar] [CrossRef] [Green Version]
- Li, J.; Li, X.; Yang, B. Reversible data hiding scheme for color image based on prediction-error expansion and cross-channel correlation. Signal Process. 2013, 93, 2748–2758. [Google Scholar] [CrossRef]










| Embedding Levels | Number of Result Images | Aspect Ratio |
|---|---|---|
| Zero | 1 | : |
| Once | 2 | : |
| Twice | 3 | : |
| Triple | 4 | : |
| Parameter | q | n | ||
|---|---|---|---|---|
| Value | 1 | 8 | 4 | 8 |
| Block Size | Block Amount | Size of m | ||
|---|---|---|---|---|
| 98,304 | 4 | 1,179,648 | 1.5 | |
| 98,304 | 2 | 589,824 | 0.75 | |
| 49,152 | 3 | 442,368 | 0.5625 | |
| 12,288 | 20 | 737,280 | 0.9375 | |
| 3072 | 32 | 294,912 | 0.375 | |
| 3072 | 16 | 147,456 | 0.1875 | |
| 3072 | 8 | 73,728 | 0.0938 |
| Method | Real Reversible | Embedding Capacity (bits) | Image Type | Application Domain |
|---|---|---|---|---|
| Zhang [19] | No | Below 4400 [23] | Grayscale continuous-tone | Encrypt |
| Zhang [21] | Yes | 4400 | Grayscale continuous-tone | Encrypt |
| Ma et al. [23] | Yes | 131,072 | Grayscale continuous-tone | Encrypt |
| Fu et al. [24] | Yes | 416,809 | Grayscale continuous-tone | Encrypt |
| Lien et al. [33] | Yes | 79,438 | Grayscale halftone | Plaintext |
| Chen et al. [34] | No | 23,814 | Grayscale halftone | Plaintext |
| Jia et al. [35] | Yes | 56,617 | Grayscale continuous-tone | Plaintext |
| Kim et al. [27] | No | 4096 | Grayscale halftone | Encrypt |
| Li et al. [36] | Yes | 725,000 | Color continuous-tone | Plaintext |
| Ours | Yes | 1,179,648 | Color halftone | Encrypt |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, Y.-X.; Yan, B.; Pan, J.-S.; Yang, H.-M.; Chen, N. Reversible Data Hiding in Encrypted Color Halftone Images with High Capacity. Appl. Sci. 2019, 9, 5311. https://doi.org/10.3390/app9245311
Sun Y-X, Yan B, Pan J-S, Yang H-M, Chen N. Reversible Data Hiding in Encrypted Color Halftone Images with High Capacity. Applied Sciences. 2019; 9(24):5311. https://doi.org/10.3390/app9245311
Chicago/Turabian StyleSun, Yu-Xia, Bin Yan, Jeng-Shyang Pan, Hong-Mei Yang, and Na Chen. 2019. "Reversible Data Hiding in Encrypted Color Halftone Images with High Capacity" Applied Sciences 9, no. 24: 5311. https://doi.org/10.3390/app9245311
APA StyleSun, Y. -X., Yan, B., Pan, J. -S., Yang, H. -M., & Chen, N. (2019). Reversible Data Hiding in Encrypted Color Halftone Images with High Capacity. Applied Sciences, 9(24), 5311. https://doi.org/10.3390/app9245311