Defining the Minimum Security Baseline in a Multiple Security Standards Environment by Graph Theory Techniques
Abstract
:1. Introduction
2. Prior and Related Work
3. The Proposed Method for MSB Identification and Verification Against Deployed Controls
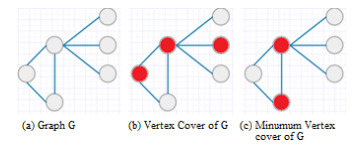
- to apply minimum weighted vertex cover algorithms in order to ensure those critical requirements having a lower value will be presented in a newly generated graph;
- to apply the selected minimum vertex cover algorithm with additional rules to ensure that higher level security requirements will not be overwritten by lower level requirements, and requirements without direct connections with another standard will not be removed.
- Restriction to remove requirements, with a connection to parent vertex but no links to other standards. To achieve that, additional null vertex to such vertex will be added.
- Additional evaluation of removed vertexes in order to ensure that vertexes without a direct connection to other standards are not removed from the graph. If such vertex were removed, we would restore them manually.
- represent information security standards’ requirements to be mapped as separate graphs;
- generate a new graph by linking requirements of N subgraphs (representing different information security standards);
- add a vertex to the vertexes with a single edge;
- apply minimum vertex cover algorithm.
4. Experimental Method Verification Results and Discussion
5. Conclusions and Future Work
- Application of graph theory and graph optimization algorithms, such as minimum vertex cover algorithms, to the standards mapping graph can be effectively used for removing duplicating requirements and ensuring spending minimization on information security;
- The method is capable of processing original graphs with relatively high numbers of vertexes, and the optimization rate of removed duplicated vertexes has reached 74.5% in the case of our experiment and can be even higher if a more significant number of regulating documents have to be applied;
- Application of isomorphism features provides a user-friendly way of evaluating the current state of controls deployed by the organization against the desired MSB state.
Author Contributions
Funding
Conflicts of Interest
References
- General Data Protection Regulation. Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the Protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of Such Data, and Repealing Directive 95/46/EC (General Data Protection Regulation). Available online: http://eur-lex.europa.eu/legal-content/EN/TXT/?uri=uriserv:OJ.L_.2016.119.01.0001.01.ENG (accessed on 20 January 2019).
- PCI DSS: 2016. Payment Card Industry Data Security Standard; International Information Security Standard; PCI Security Standards Council: Wakefield, MA, USA, 2016.
- Sarbanes-Oxley Act of 2002. US Mandatory Regulatory Requirements; US EPA: Washington, DC, USA, 2002.
- ISACA. COBIT 5: A Business Framework for the Governance and Management of Enterprise IT; ISACA: Schaumburg, IL, USA, 2018. [Google Scholar]
- Internal Control–Integrated Framework; Developed by Committee of Sponsoring Organizations of the Treadway Commission (COSO); COSO: USA, 2013.
- Fung, D.C.Y.; Hong, S.H.; Koschutzki, D.; Schreiber, F.; Xu, K. 2.5D Visualisation of overlapping biological networks. J. Integr. Bioinf. 2008, 5, 90. [Google Scholar] [CrossRef]
- Dudas, P.M.; de Jongh, M.; Brusilovsky, P. A semi-supervised approach to visualizing and manipulating overlapping communities. In Proceedings of the 17th International Conference on Information Visualisation, London, UK, 16–18 July 2013. [Google Scholar]
- Telea, A.; Ersoy, O. Image-based edge bundles: Simplified visualization of large graphs. In Proceedings of the Eurographics/IEEE-VGTC Symposium on Visualization, Bordeaux, France, 9–11 June 2010; p. 29. [Google Scholar]
- Zavadskas, E.K.; Turskis, Z.; Vilutiene, T. Integrated group fuzzy multi-criteria model: Case of facilities management strategy selection. Expert Syst. Appl. 2017. [Google Scholar] [CrossRef]
- Health Insurance Portability and Accountability Act. US Mandatory Regulatory Requirements for Health Insurance Sector; HIPAA; United States Congress: Washington, DC, USA, 1996.
- ISO/IEC 27001 Family–Information Security Management Systems. International Organization for Standardization. Available online: https://www.iso.org/isoiec-27001-information-security.html (accessed on 5 November 2018).
- Souag, A.; Salinesi, C.; Comyn-Wattiau, I. Ontologies for security requirements: A literature survey and classification. In Advanced Information Systems Engineering Workshops Lecture Notes in Business Information Processing; Springer: Berlin, Germany, 2012; Volume 112, pp. 61–69. [Google Scholar]
- Pardo, C.; Pino, F.J.; Garcia, F.; Piattini, M.; Baldassarre, M.T. An ontology for the harmonization of multiple standards and models. Comput. Stand. Interfaces 2012, 34, 48–59. [Google Scholar] [CrossRef]
- Ahuja, S. Integration of COBIT, Balanced Scorecard and SSE-CMM as a Strategic Information Security Management (ISM) Framework. [Online]. 2009. Available online: https://www.cerias.purdue.edu/assets/pdf/bibtex_archive/2009-21.pdf (accessed on 11 November 2018).
- Ramanauskaite, S.; Olifer, D.; Goranin, N.; Cenys, A. Security ontology for adaptive mapping of security standards. Int. J. Comput. Commun. Control 2013, 8, 813–825. [Google Scholar] [CrossRef]
- Peng, Y.; Kou, G.; Shi, Y.; Chen, Z.X. A descriptive framework for the field of data mining and knowledge discovery. Int. J. Inf. Technol. Decis. Mak. 2008, 7, 639–682. [Google Scholar] [CrossRef]
- Mandatory Security Baseline Definition. CERN Computer Security. Available online: https://security.web.cern.ch/security/rules/en/baselines.shtml (accessed on 13 November 2018).
- Bartens, T.; de Haes, S.; Lamoen, Y.; Schulte, F.; Voss, S. On the Way to a Minimum Baseline in IT Governance: Using Expert Views for Selective Implementation of COBIT 5. In Proceedings of the 2015 48th Hawaii International Conference on System Sciences (HICSS), Kauai, HI, USA, 5–8 January 2015. [Google Scholar] [CrossRef]
- De Haes, S.; Van Grembergen, W. An Exploratory Study into the Design of an IT Governance Minimum Baseline through Delphi Research. Commun. Assoc. Inf. Syst. 2008, 22, 24. Available online: http://aisel.aisnet.org/cais/vol22/iss1/24 (accessed on 21 November 2018). [CrossRef]
- Olifer, D.; Goranin, N.; Kaceniauskas, A.; Cenys, A. Controls-based approach for evaluation of information security standards implementation costs. Technol. Econ. Dev. 2017, 23, 196–219. [Google Scholar] [CrossRef]
- Olifer, D.; Goranin, N.; Janulevicius, J.; Kaceniauskas, A.; Cenys, A. Integration of Controls-Based Method for Evaluation of Security Requirements Implementation Cost with BPMN and EPC Business Process Modelling Techniques (SPBP 2017); SPBP: Barcelona, Spain, 2017; pp. 698–711. [Google Scholar]
- Ruohonen, K. Graph Theory. 2012. Available online: http://math.tut.fi/~ruohonen/GT_English.pdf (accessed on 24 November 2018).
- Eshtay, M.; Sliet, A.; Sharieh, A. NMVSA Greedy Solution for Vertex Cover Problem. (IJACSA) Int. J. Adv. Comput. Sci. Appl. 2016, 7. [Google Scholar] [CrossRef] [Green Version]
- Minimum Vertex Cover Definition. Available on Wolfram MathWorld Portal. Available online: http://mathworld.wolfram.com/MinimumVertexCover.html (accessed on 21 November 2018).
- Cai, S.; Su, K.; Luo, C.; Sattar, A. NuMVC: An efficient local search algorithm for minimum vertex cover. J. Artif. Intell. Res. 2013, 46, 687–716. [Google Scholar] [CrossRef]
- Ding, L.; Gu, B.; Hong, X.; Dixon, B. Articulation node based routing in delay tolerant networks. In Proceedings of the IEEE International Conference, Galveston, TX, USA, 9–13 March 2009; pp. 1–6. [Google Scholar]
- Zeng, Y.; Wang, D.; Liu, W.; Xiong, A. An approximation algorithm for weak vertex cover problem in IP network traffic measurement. In Proceedings of the 2009 IEEE International Conference on Network Infrastructure and Digital Content, Beijing, China, 6–8 November 2009; pp. 182–186. [Google Scholar]
- Oliveto, P.S.; Yao, X.; He, J. Analysis of Population-based Evolutionary Algorithms for the Vertex Cover Problem. In Proceedings of the 2008 IEEE Congress on Evolutionary Computation (IEEE World Congress on Computational Intelligence), Hong Kong, China, 1–6 June 2008; pp. 1563–1570. [Google Scholar]
- Karp, R. Reducibility among Combinatorial Problems; Plenum Press: New York, NY, USA, 1972. [Google Scholar]
- Chvatal, V. A Greedy Heuristic for the Set-Covering Problem. Math. Oper. Res. 1979, 4, 233–235. [Google Scholar] [CrossRef]
- Clarkson, K. A modification to the greedy algorithm for vertex cover problem. Inf. Process. Lett. 1983, 16, 23–25. [Google Scholar] [CrossRef]
- Balaji, S.; Swaminathan, V.; Kannan, K. Optimization of Un-weighted Minimum Vertex Cover. World Acad. Sci. Eng. Technol. 2010, 67, 214–219. [Google Scholar]
- Gajurel, S.; Bielefeld, R. A Simple NOVCA: Near Optimal Vertex Cover Algorithm. Procedia Comput. Sci. 2012, 9, 747–753. [Google Scholar] [CrossRef] [Green Version]
- Khan, I.; Ahmad, I.; Khan, M. AVSA, Modified Vertex Support Algorithm for Approximation of MVC. Int. J. Adv. Sci. Technol. 2014, 67, 71–78. [Google Scholar] [CrossRef]
- Khan, I.; Kha, H.N. Modified Vertex Support Algorithm: A New approach for approximation of Minimum vertex cover. Res. J. Comput. Inf. Technol. Sci. 2013, 1, 7–11. [Google Scholar]
- Delbot, F.; Laforest, C. A better list heuristic for vertex covers. Inf. Process. Lett. 2008, 107, 125–127. [Google Scholar] [CrossRef]
- Khan, I.; Khan, H. Experimental Comparison of Five Approximation Algorithms for Minimum Vertex Cover. Int. J. u- e-Serv. Sci. Technol. 2014, 7, 69–84. [Google Scholar] [CrossRef]
- Warnow, T. Approximation Algorithms. 21 February 2005. Available online: http://tandy.cs.illinois.edu/dartmouth-cs-approx.pdf (accessed on 20 October 2018).
- Williams, V. Algorithms for Fixed Subgraph Isomorphism. 28 September 2016. Available online: http://theory.stanford.edu/virgi/cs267/lecture1.pdf (accessed on 21 October 2018).
- Sanfeliua, A.; Alquézarb, R.; Andradea, J.; Climentc, J.; Serratosad, F.; Vergésa, J. Graph-based representations and techniques for image processing and image analysis. Pattern Recognit. 2002, 35, 639–650. [Google Scholar] [CrossRef] [Green Version]
- Conte, D. Graph matching applications in pattern recognition and image processing. In Proceedings of the International Conference on IEEE Image Processing Proceeding, Barcelona, Spain, 14–17 September 2003. [Google Scholar]
- Fan, W. Graph Pattern Matching Revised for Social Network Analysis. In Proceedings of the 15th International Conference on Database Theory ICDT, Berlin, Germany, 26–29 March 2012. [Google Scholar]
- Raymond, J.W.; Willett, P. Maximum Common Subgraph Isomorphism Algorithms for the Matching of Chemical Structures. J. Comput.-Aided Mol. Des. 2002, 16, 521–533. [Google Scholar] [CrossRef]
- Balaban, A.T. Applications of Graph Theory in Chemistry. J. Chem. Inf. Comput. Sci. 1985, 25, 334–343. [Google Scholar] [CrossRef]
- Elmsallati, A.; Clark, C.; Kalita, J. Global Alignment of Protein-Protein Interaction Networks: A Survey. IEEE/ACM Trans. Comput. Biol. Bioinf. 2007, 6, 689–705. [Google Scholar] [CrossRef] [PubMed]
- Lee, J.; Kasperovics, R.; Han, W.; Lee, J. An In-depth Comparison of Subgraph Isomorphism Algorithms in Graph Databases. In Proceedings of the 39th International Conference on Very Large Data Bases, Proceedings of the VLDB Endowment, Riva del Garda, Trento, Italy, 26–30 August 2013; Volume 6, p. 2. [Google Scholar]
- Shasha, D.; Wang, J.T.L.; Giugno, R. Algorithmics and applications of tree and graph searching. In Proceedings of the Twenty-First ACM SIGMOD-SIGACT-SIGART Symposium on Principles of Database Systems PODS, Madison, WI, USA, 3–5 June 2002; pp. 39–52. [Google Scholar]
- Cheng, J.; Ke, Y.; Ng, W.; Lu, A. Fg-index: Towards verification-free query processing on graph databases. In Proceedings of the 2007 ACM SIGMOD International Conference on Management of Data, SIGMOD, Beijing, China, 11–14 June 2007; pp. 857–872. [Google Scholar]
- Ullmann, J.R. An algorithm for subgraph isomorphism. J. ACM 1976, 23, 31–42. [Google Scholar] [CrossRef]
- Cordella, L.P.; Foggia, P.; Sansone, C.; Vento, M. A (sub)graph isomorphism algorithm for matching large graphs. IEEE Trans. Pattern Anal. Mach. Intell. 2004, 26, 1367–1372. [Google Scholar] [CrossRef] [PubMed]
- Shang, H.; Zhang, Y.; Lin, X.; Yu, J.X. Taming verification hardness: An efficient algorithm for testing subgraph isomorphism. Proc. VLDB Endow. 2008, 1, 364–375. [Google Scholar] [CrossRef]
- Zhao, P.; Han, J. On graph query optimization in large networks. Proc. VLDB Endow. 2010, 3, 340–351. [Google Scholar] [CrossRef] [Green Version]
- Mongiovi, M.; Natale, R.D.; Giugno, R.; Pulvirenti, A.; Ferro, A.; Sharan, R. Sigma: A set-cover-based inexact graph matching algorithm. J. Bioinf. Comput. Biol. 2010, 8, 199–218. [Google Scholar] [CrossRef]
- Khan, A.; Li, N.; Yan, X.; Guan, Z.; Chakraborty, S.; Tao, S. Neighborhood based fast graph search in large networks. In Proceedings of the SIGMOD, Athens, Greece, 12–16 June 2011; pp. 901–912. [Google Scholar]
- Minimum Baseline Standart Explanation Developed by Information Systems Security Association (New York Metro Chapter). Available online: https://www.nymissa.org/wp-content/uploads/2016/01/Minimum-Baseline-Standards-Presentation_02-21-2016.pdf (accessed on 24 November 2018).
- Microsoft Security Recommendations. Available online: https://blogs.technet.microsoft.com/secguide/ (accessed on 25 January 2019).
- Cisco Network Security Baseline. Available online: https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Security/Baseline_Security/securebasebook.html (accessed on 25 January 2019).
- Cybersecurity Best Practices Developed by Center for Internet Security. Available online: https://www.cisecurity.org/cybersecurity-best-practices/ (accessed on 25 January 2019).
- Vulnerability Scanning Tools for Potential Security Gaps Identification. Available online: https://www.tenable.com/products/tenable-io (accessed on 25 January 2019).
- HITRUST Cyber Security Framework v9.1. 2018. Available online: https://hitrustalliance.net/ (accessed on 15 October 2018).
- Cytoscape Is an Open Source Software Platform for Visualizing Complex Networks and Integrating These with any Type of Attribute Data–Cytoscape 3.6.1. Available online: http://www.cytoscape.org (accessed on 15 October 2018).
- Open-Source Java App for Visualizing Large Data Matrices–TreeView 3.0. Available online: https://bitbucket.org/TreeView3Dev/treeview3/ (accessed on 15 October 2018).
- Dharwadker, A. The Vertex Cover Algorithm. 10 October 2011. Available online: http://www.dharwadker.org/vertex_cover/ (accessed on 20 October 2018).
- CyIsomorphism Is a Cytoscape App that Provides All the Matchings from a Subgraph of Network 1 to Network 2 Satisfying the Isomorphism Property. Available online: http://apps.cytoscape.org/apps/cyisomorphism (accessed on 25 October 2018).













| Action No. | Description |
|---|---|
| I | Standards’ requirements are presented hierarchically. If vertexes have edges between them that means that requirements are identical. Differentiation by coverage level is out of scope for this method feasibility verification. In case our task link directions are not important. |
| II | Generated graph is reviewed, and temporary vertexes are added. Additional vertexes are added to the graph in order to ensure that the minimum vertex cover algorithm will not remove existing vertexes that do not have direct connections with other standards. |
| III | The mapping graph is represented as an adjacency matrix for technical processing by a vertex cover algorithm. |
| IV | Vertex cover algorithm is applied. The result is presented in the form of rows. Since we assume that duplicated vertexes are identical, and the removal of any vertex would provide a suitable result, this leads to the situation when several similar solutions (several rows) can be generated. To present it as a graph, we extract identified vertexes and edges from the initial mapping graph. |
| V | Vertexes without a direct connection to other standards that were removed from the mapping graph are restored (the process is currently manual). Due to different levels of detail in various standards, the future approach could make use of additional criteria, which would allow removing vertexes, with a specified level of detail. |
| Action No. | Description |
|---|---|
| I | This action includes two main activities: Information gathering about controls deployed; Presentation of information gathered in the form of a graph. Information gathering could be done manually or by automation tools that can process Business Process Model and Notation (BPMN) or Event-Driven Process Chain (EPC) diagrams. The generated graph may have stand-alone vertexes, i.e., not connected with any other vertexes. The process of identification of links between controls in the organization is a complicated task and could be accelerated if it is known if the organization is compliant with one or another security standard. |
| II | MSB and deployed control graphs (DCGs) (or their representation form, like adjacency matrix, table) are imported to the graph processing tool, and the subgraph isomorphism algorithm is executed. If DCG graph has stand-alone vertexes or small subgraphs, then the subgraph isomorphism algorithm is executed for each of them separately. |
| III | Since a stand-alone vertex is isomorphic to any vertex of MSB, additional verification based on a specified criterion (e.g., semantic similarity) should be used. Error verification can be done automatically, by applying addition verification criteria and re-executing the subgraph isomorphism algorithm against subgraph or manually by a security specialist. |
| IV | Controls required by MSB but are not present in DCG are identified. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Olifer, D.; Goranin, N.; Cenys, A.; Kaceniauskas, A.; Janulevicius, J. Defining the Minimum Security Baseline in a Multiple Security Standards Environment by Graph Theory Techniques. Appl. Sci. 2019, 9, 681. https://doi.org/10.3390/app9040681
Olifer D, Goranin N, Cenys A, Kaceniauskas A, Janulevicius J. Defining the Minimum Security Baseline in a Multiple Security Standards Environment by Graph Theory Techniques. Applied Sciences. 2019; 9(4):681. https://doi.org/10.3390/app9040681
Chicago/Turabian StyleOlifer, Dmitrij, Nikolaj Goranin, Antanas Cenys, Arnas Kaceniauskas, and Justinas Janulevicius. 2019. "Defining the Minimum Security Baseline in a Multiple Security Standards Environment by Graph Theory Techniques" Applied Sciences 9, no. 4: 681. https://doi.org/10.3390/app9040681
APA StyleOlifer, D., Goranin, N., Cenys, A., Kaceniauskas, A., & Janulevicius, J. (2019). Defining the Minimum Security Baseline in a Multiple Security Standards Environment by Graph Theory Techniques. Applied Sciences, 9(4), 681. https://doi.org/10.3390/app9040681