Organization Preference Knowledge Acquisition of Multi-Platform Aircraft Mission System Utilizing Frequent Closed Itemset Mining
Abstract
:1. Introduction
1.1. Motivation
1.2. Related Works and Gaps
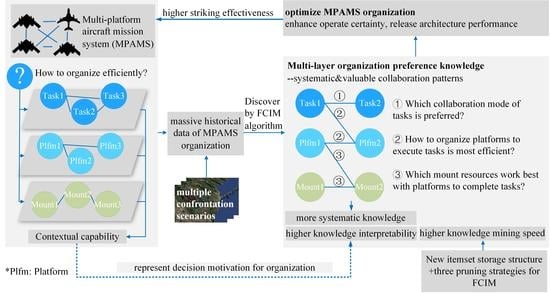
- Limited comprehensive level. The discovered knowledge cannot lead to a systematic and overall understanding of the MPAMS organization. Since current research has only focused on isolated organizational decisions at the separate task, platform, or mount layer. It overlooks the practical correlated multi-layer collaboration modes of the MPAMS architecture in the SoS context, which limits its applicable value.
- Poor interpretability. The discovered knowledge shows only “what to do” but overlooks “why to do”. Such as the knowledge indicates which weapon combinations will produce favorable results, but does not mention the situation background [30,31], i.e., the motivation for this decision. As a result, the isolated knowledge assertion lacks both intrinsic interpretability for the commander and rationality to migrate to similar scenarios.
- Inadequate speed. It is challenging for FCIM to deal with large-scale MPAMS datasets, which possess a complex and dense item distribution, leading to a knowledge construction dilemma with large time consumption. Therefore, the candidate itemset scale, that is, the redundant information in the mining process, should be further reduced to accelerate knowledge discovery, making it capable of handling more complex and large-scale datasets.
1.3. Contributions
1.4. Organization of the Paper
2. Proposed MPAMS Organizational Knowledge Mining Method
2.1. Preliminaries
2.2. Problem Description
2.3. MPAMS Organizational Knowledge Discovery Framework
3. Proposed MPAMS Organizational Knowledge Mining Algorithm-CrossFCI
3.1. Proposed Itemset Storage Structure
3.2. Knowledge Mining Procedure
3.3. Proposed Pruning Strategies
3.4. Algorithm Implementation
- Function 1: Construct the item-mediated linked list to store each item’s transactions.
| Function Conwg() | |
| Input: original transaction database Output: item-mediated linked list G with each graphnode attached with a set of transnodes | |
| 1: | While(!transaction database) |
| 2: | { foreach itemnode in a certain transaction |
| 3: | if then |
| 4: | create graphnode |
| 5: | Transnode* translist = SearchMatch(database, )//read matched transactions in sequence |
| 6: | , |
| 7: | else link to the matched } |
| 8: | Delete |
| End function | |
- Function 2: Update the cross-linked structure according to each incoming graphnode.
| Function Mining() | |
| Input: each graphnode g in the item-mediated linked list G Output: updated cross-linked structure | |
| 1: | Initial() |
| 2: | foreach |
| 3: | { foreach |
| 4: | { mining the longest chain of the branches firstly |
| 5: | mining the itemnode by MiningItem() |
| 6: | } |
| 7: | Link(null,, null, g, 0, 3)//create independent headnode branch for g |
| 8: | //search index itemnode which matches g |
| 9: | if then Link(null, , null, g, 0, 2)//create a new headnode branch for g |
| 10: | else//conduct pruning strategy 3 |
| 11: | if then Link(null,g, 0,4) |
| 12: | } |
| End function | |
- Function 3: Generate new FCI candidates for each headnode branch.
| Function MiningItem(,, g, k) | |
| Input: and : adjacent itemnodes in , g: graphnode, k: the sub-branch index of Output: updated FCI branches in the FCI linked list | |
| 1: | if ( = null) then//imply the tail itemnode of the certain FCI chain |
| 2: | if then Link(, null, g, k, 2)//target that matches g |
| 3: | else//conduct pruning strategy 3 |
| 4: | if then Link( g, k, 4) |
| 5: | else//imply intermediate itemnode of the certain FCI chain |
| 6: | foreach //conduct pruning strategy 2 |
| 7: | { if then |
| 8: | , |
| 9: | else//conduct pruning strategy 1 |
| 10: | foreach sub-branch sub of |
| 11: | MiningItem(, sub, g, sub.index) |
| End function | |
- Function 4: Update the cross-linked structure.
| Function Link(, g, k, mode) | |
| Input: : horizontal FCI linked list, : vertical index linked list, : headnode linked list, :vertical FCI linked list, g: graphnode, k: the sub-branch index of , mode: the structure updating mechanism mode Output: updated attached with new itemnode | |
| 1: | Create new |
| 2: | Switch(mode) |
| 3: | Case 1://neither headnode nor indexnode exists, applicable to the initial itemnode of the structure |
| 4: | Create new , create |
| 5: | Case 2://no indexnode exists, applicable to updating the longest branch of |
| 6: | Create new |
| 7: | Case 3://no headnode exists, construct an independent headnode branch for g |
| 8: | Create new |
| 9: | Case 4://both headnode and indexnode exist, applicable to analysis intermediate branches of |
| 10: | |
| End function | |
4. Results
- How effectively could CrossFCI mine FCIs from the public quantitative datasets?
- How well does CrossFCI’s performance benefit from the proposed three pruning strategies?
- What valuable organization preference knowledge in MPAMS organization has been discovered by CrossFCI?
- How efficiently could CrossFCI adapt to huge MPAMS datasets of different sizes?
4.1. Introduction to Datasets and Algorithms
4.1.1. Public Datasets
4.1.2. Compared Algorithms and Experiment Settings
4.2. Results on Public Datasets
4.2.1. Efficiency Comparison
4.2.2. Scalability Assessment
4.2.3. Pruning Strategy Efficiency Verification
4.3. Results on Wargame Simulation Datasets
4.3.1. Case Description
4.3.2. Data Processing
4.3.3. Results Analysis
- The first column (A1) denoted the contextual capability configuration code, accompanied by the organization modes, which indicated the advantage and disadvantage of a MPAMS against an enemy. The labelled code of each capability is as follows: W is for weak, B is for balanced, and S is for strong.
- The second column (A2) included typical MPAMS organization modes extracted from data. For instance, F1(X1[Y1], X2[Y2])→F2(X3[Y3]) denoted a pattern that task F1 was first conducted via platform X1 and X2, and X1 was equipped with mount Y1 while X2 was equipped with mount Y2. Afterward, task F2 was conducted via platform X3 with mount Y3. The typical features of each mode are marked with bold and underlined fonts.
- The fourth column (B) represented the firepower effectiveness elements in the pattern, which included the integrity of a defender’s key target and the attrition of the attacker. According to the operation objective, the integrity of the defender’s key target comprised three integrity levels of the defender’s ship: damaged, failed, and normal, which were abbreviated as D, F, and N, respectively. The patterns with different integrity levels are highlighted by separate colors in Table 5. Additionally, the attrition of the attacker, namely the aircraft or mount consumption, was divided into three levels by percentage, large, medium, and small levels, represented by symbols L, M, and S, respectively. The superscript indicates the type of aircraft or mount.
- The last column of Table 5 depicts how frequently a FCI occurs, and “6” means a FCI appears six times in all FCIs. The larger the number is, the more typical the FCI is.
4.3.4. Efficiency Performance Evaluation
4.3.5. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AAM | Air-to-air missile |
| AEW | Air early warning |
| ASM | Air-to-sea missile |
| CI | Closed itemset |
| FCI | Frequent closed itemset |
| FCIM | Frequent closed itemset mining |
| FI | Frequent itemset |
| IRS | Intelligence, surveillance, and reconnaissance |
| MPAMS | Multi-platform aircraft mission system |
| SoS | System-of-systems |
| UAV | Unmanned aerial vehicle |
Appendix A
| Configuration | Task | Platform | Mount | Capability Code |
|---|---|---|---|---|
| Lng-range | Surveillance + feint + escort + attack | BM × 4 + FB × 4 + FS × 4 + FA × 2 + UAV × 2 + AEW × 1 * | Long-range ASM | Bprcp,Wattk,Selec, Sdefs,Bmnur,Scncl |
| Cls-range | surveillance + feint + escort + attack | BM × 4 + FB × 4 + FS × 4 + FA × 2 + UAV × 2 + AEW × 1 | Close-range ASM | Bprcp,Sattk,Selec, Sdefs,Bmnur,Wcncl |
| Cls&Lng-range | Surveillance + feint + escort + attack | BM × 4 + FB × 4 + FS × 4 + FA × 2 + UAV × 2 + AEW × 1 | Close-range ASM +long-range ASM | Bprcp,Battk,Selec, Sdefs,Bmnur,Bcncl |
| No-escort | Surveillance + feint + attack | BM × 4 + FB × 4 + FS × 6 + UAV × 2 + AEW × 1 | Long-range ASM | Bprcp,Battk,Selec, Bdefs,Bmnur,Wcncl |
| No-feint | Surveillance + escort + attack | BM × 4 + FB × 4 + FS × 4 + FA × 2 + UAV × 2 + AEW × 1 | Long-range ASM | Bprcp,Battk,Selec, Bdefs,Smnur,Wcncl |
| Elec | Surveillance + feint + escort + electronic jamming + attack | BM × 4 + FB × 4 + FS × 3 + FA × 2 + UAV × 2 + EF × 1 + AEW × 1 | Long-range ASM + electronic warfare weapons | Sprcp,Wattk,Selec, Sdefs,Smnur,Bcnc |
| Ultrlng-range | Surveillance + escort + attack | BM × 12 + FA × 2 + UAV × 2 + AEW × 1 | Ultra-long-range ASM | Bprcp,Sattk,Selec, Wdefs,Wmnur,Scncl |
| Bomb | Surveillance + escort + attack | BM × 12 + FA × 2 + UAV × 2 + AEW × 1 | Bomb | Bprcp,Sattk,Selec, Wdefs,Wmnur,Wcncl |
| Bomb&F_cls-range | Surveillance + escort + attack | BM × 8 + FS × 4 +FA × 2 + UAV × 2 + AEW × 1 | Ultra-long-range ASM + close-range ASM | Bprcp,Battk,Selec, Bdefs,Bmnur,Scncl |
| Bomb&Fb_cls-range | Surveillance + escort + attack | BM × 8 + FB × 4 + FA × 2 + UAV × 2 + AEW × 1 | Ultra-long-range ASM + close-range ASM | Bprcp,Battk,Selec, Bdefs,Wmnur,Scncl |
References
- Sapaty, P. Mosaic Warfare: From philosophy to model to solutions. Int. Robot. Automat. J. 2019, 5, 157–166. [Google Scholar] [CrossRef]
- Lemons, G.T.; Carrington, K. F-35 mission systems design, development & verification. In Proceedings of the 2018 Aviation Technology, Integration, and Operations Conference, Atlanta, GA, USA, 25–29 June 2018; pp. 3519–3535. [Google Scholar]
- Bjerke, H.M.; Valaker, S. Command and control in a fifth generation air force: Coordination requirements of air operations with F-35 and the command and control-system of the norwegian armed forces. Scand. J. Mil. Stud. 2022, 5, 14–30. [Google Scholar] [CrossRef]
- Wang, G.; Gu, Q.; Wu, J.; Wang, M. Concept and architecture for new generation aircraft mission system. Acta. Aeronaut. Astronaut. Sin. 2015, 36, 2735–2752. [Google Scholar]
- Harteveld, C.; Kleinman, E.; Rizzo, P.; Schouten, D.; Nguyen, T.H.; Liberty, S.; Kimbrough, W.; Fombelle, P.; El-Nasr, M.S. Teamwork and adaptation in games (TAG) a survey to gauge teamwork. In Proceedings of the 14th International Conference on the Foundations of Digital Games, San Luis Obispo, CA, USA, 26–30 August 2019; pp. 1–12. [Google Scholar]
- Cheng, K.; Chen, G.; Yu, X.; Liu, M.; Shao, T. Knowledge traction and data-driven wargame AI design and key technologies. Syst. Eng. Electron. Technol. 2021, 43, 2911–2917. [Google Scholar]
- Huang, C.; Wei, Z.; Yang, Y.; Zhang, H. Knowledge acquisition for the air combat based on gwo. In Proceedings of the 2019 International Conference on Artificial Intelligence Technologies and Applications, Qingdao, China, 5–7 July 2019; pp. 12078–12087. [Google Scholar]
- Johansson, T. Tactical Simulation in Air-to-Air Combat: Evolutionary Algorithms and Behavior Tree Framework. Master’s Thesis, Lulea University of Technology, Luleå, Sweden, 2018. [Google Scholar]
- Masek, M.; Lam, C.P.; Kelly, L.; Benke, L.; Papasimeon, M. A genetic programming framework for novel behaviour discovery in air combat scenarios. In Proceedings of the ASOR/DORS Conference 2018, Melbourne, Australia, 4–6 December 2021; pp. 263–277. [Google Scholar]
- Masek, M.; Lam, C.P.; Benke, L.; Kelly, L.; Papasimeon, M. Discovering emergent agent behaviour with evolutionary finite state machines. In Proceedings of the International Conference on Principles and Practice of Multi-Agent Systems, Tokyo, Japan, 29 October–2 November 2018; pp. 19–34. [Google Scholar]
- Dong, S.; Xu, W.; Zhang, K. Study on the resolution of multi-aircraft flight conflicts based on an IDQN. Chin. J. Aeronaut. 2022, 35, 195–213. [Google Scholar]
- Lee, D.; Kim, M.J.; Ahn, C.W. Predicting combat outcomes and optimizing armies in StarCraft II by deep learning. Expert. Syst. Appl. 2021, 185, 115592. [Google Scholar] [CrossRef]
- Dong, Y. Deep learning-based opponent aircraft attitude detection in autonomous air combat. J. Aerosp. Inform. Syst. 2019, 16, 162–167. [Google Scholar] [CrossRef]
- Li, B.; Liang, S.; Chen, D.; Li, X. A decision-making method for air combat maneuver based on hybrid deep learning network. Chin. J. Electron. 2022, 31, 107–115. [Google Scholar]
- Hooshyar, D.; Yousefi, M.; Lim, H. Data-driven approaches to game player modeling: A systematic literature review. ACM Comput. Surv. 2018, 50, 90. [Google Scholar] [CrossRef]
- Chee, C.; Jaafar, J.; Aziz, I.A.; Hasan, M.H.; Yeoh, W. Algorithms for frequent itemset mining: A literature review. Artif. Intell. Rev. 2019, 52, 2603–2621. [Google Scholar] [CrossRef]
- Enstad, K. Professional knowledge through wargames and exercises. Scand. J. Mil. Stud. 2022, 5, 233–243. [Google Scholar] [CrossRef]
- Mason, R.C. Wargaming: Its history and future. Int. J. Intell. Secur. Public. Aff. 2018, 20, 77–101. [Google Scholar] [CrossRef]
- López-Felip, M.A.; Davis, T.J.; Frank, T.D.; Dixon, J.A. A cluster phase analysis for collective behavior in team sports. Hum. Mov. Sci. 2018, 59, 96–111. [Google Scholar] [CrossRef]
- Ahmad, S.; Bryant, A.; Kleinman, E.; Teng, Z.; Nguyen, T.H.D.; El-Nasr, M.S. Modeling individual and team behavior through spatio-temporal analysis. In Proceedings of the Annual Symposium on Computer-Human Interaction in Play, Barcelona, Spain, 22–25 October 2019; pp. 601–612. [Google Scholar]
- Javvaji, N.; Harteveld, C.; El-Nasr, M.S. Understanding player patterns by combining knowledge-based data abstraction with interactive visualization. In Proceedings of the Annual Symposium on Computer-Human Interaction in Play, Online, 2–4 November 2020; pp. 254–266. [Google Scholar]
- Yang, P.; Harrison, B.E.; Roberts, D.L. Identifying patterns in combat that are predictive of success in MOBA games. In Proceedings of the Foundations of Digital Games 2014 Conference, Ft. Lauderdale, FL, USA, 3–7 April 2014; pp. 1–8. [Google Scholar]
- Goyal, P.; Sapienza, A.; Ferrara, E. Recommending teammates with deep neural networks. In Proceedings of the 29th on Hypertext and Social Media, Baltimore, MD, USA, 9–12 July 2018; pp. 57–61. [Google Scholar]
- Guzmán, J.G.L.; Medina, C.J.B. Relevant independent variables on MOBA video games to train machine learning algorithms. In Proceedings of the International Conference in Central Europe on Computer Graphics, Visualization and Computer Vision 2021, Online, 6–10 September 2021; pp. 171–179. [Google Scholar]
- Lin, H.; Chen, J.; Song, Y. Warship combat decision support system based on data mining technology. Procedia Comput. Sci. 2022, 166, 248–251. [Google Scholar] [CrossRef]
- Schwartz, P.J.; O’Neill, D.V.; Bentz, M.E.; Brown, A.; Doyle, B.S.; Liepa, O.C.; Lawrence, R.; Hull, R.D. AI-enabled wargaming in the military decision making process. In Proceedings of the SPIE 11413, Artificial Intelligence and Machine Learning for Multi-Domain Operations Applications II, Online, 27 April–9 May 2020; pp. 118–134. [Google Scholar]
- Cao, G.; Wang, Y.; Zhang, L. Application of association rule mining in operational experiment data analysis. Command Control Simul. 2019, 2, 70–74. [Google Scholar]
- Li, Z.; Zhu, L.; Wei, W. Application of association rule mining to target analysis in electronic countermeasure. Ship Electron. Countermeas. 2015, 38, 1–4. [Google Scholar]
- Xing, S.; Ni, L.; Zhang, H.; Yan, K. Mining of weapon utility based on the replay data of war-game. J. Command Control 2020, 6, 132–140. [Google Scholar]
- Yu, L.; Zhang, D.; Chen, X.; Xie, X. Moba-slice: A time slice based evaluation framework of relative advantage between teams in MOBA games. In Proceedings of the 7th Workshop on Computer Games, Stockholm, Sweden, 13 July 2018; pp. 23–40. [Google Scholar]
- Kleinman, E.; Ahmad, S.; Teng, Z.; Bryant, A.; Nguyen, T.H.D.; Harteveld, C.; El-Nasr, M.S. “And then they died”: Using action sequences for data driven, context aware gameplay analysis. In Proceedings of the 15th International Conference on the Foundations of Digital Games, Bugibba, Malta, 15–18 September 2020; pp. 1–12. [Google Scholar]
- Telikani, A.; Gandomi, A.H.; Shahbahrami, A. A survey of evolutionary computation for association rule mining. Inform. Sci. 2020, 524, 318–352. [Google Scholar] [CrossRef]
- Fasihy, H.; Shahraki, M.H.N. Incremental mining maximal frequent patterns from univariate uncertain data. Knowl.-Based Syst. 2018, 152, 40–50. [Google Scholar] [CrossRef]
- Miholca, D.L.; Czibula, G.; Crivei, L.M. A new incremental relational association rules mining approach. Procedia Comput. Sci. 2018, 126, 126–135. [Google Scholar] [CrossRef]
- Djenouri, Y.; Belhadi, A.; Fournier-Viger, P. Extracting useful knowledge from event logs: A frequent itemset mining approach. Knowl.-Based Syst. 2018, 139, 132–148. [Google Scholar] [CrossRef]
- Dam, T.L.; Ramampiaro, H.; Nørvåg, K.; Duong, Q.H. Towards efficiently mining closed high utility itemsets from incremental databases. Knowl.-Based Syst. 2019, 165, 13–29. [Google Scholar] [CrossRef]
- Martin, T.; Francoeur, G.; Valtchev, P. CICLAD: A fast and memory-efficient closed itemset miner for streams. In Proceedings of the 26th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, Online, 6–10 July 2020; pp. 1810–1818. [Google Scholar]
- Yen, S.; Wu, C.; Lee, Y.; Tseng, V.S.; Hsieh, C.H. A fast algorithm for mining frequent closed itemsets over stream sliding window. In Proceedings of the 2011 IEEE International Conference on Fuzzy Systems, Taipei, China, 27–30 June 2011; pp. 996–1002. [Google Scholar]
- Chi, Y.; Wang, H.; Yu, P.; Muntz, R.R. Moment: Maintaining closed frequent itemsets over a stream sliding window. In Proceedings of the Fourth IEEE International Conference on Data Mining, Brighton, UK, 1–4 November 2004; pp. 59–66. [Google Scholar]
- Škopljanac-Mačina, F.; Blašković, B. Formal concept analysis–overview and applications. Procedia Eng. 2014, 69, 1258–1267. [Google Scholar] [CrossRef]
- Mednikarov, B.; Dereliev, P. Structured description of naval tasks. Inform. Secur. Int. J. 2004, 13, 25–34. [Google Scholar] [CrossRef]
- Chen, Q.; Tian, H.; Wang, P.; Leng, S.; Xiao, Z. A collocation scheme of distributed cooperative operational weapons based on OODA loop. Acta Armamentarii 2021, 42, 1780–1788. [Google Scholar]
- Staff, J. Universal Joint Task List (UJTL); United States Department of Defense: Washington, DC, USA, 2023; Available online: https://www.jcs.mil/Portals/36/Documents/Doctrine/training/ujtl_tasks.pdf?ver=yKLdOVrp5veCK84zYZzIlg%3d%3d (accessed on 13 January 2023).












| Dimension | Method Type | Research Topic | Feature | Drawback | |
|---|---|---|---|---|---|
| Knowledge effectiveness | Other data-driven methods such as clustering [19,20,21], decision tree [22], and deep learning [23]. | Task behavior strategies [19,20,21], team composition patterns [22], and synergistic platform recommendation [23]. | Knowledge type: Based on the target problem, mainly heterogeneous features. Knowledge interpretability: Low, due to black box mode and scarce background information. | (1) Limited knowledge representation flexibility for heterogeneous features. (2) Must design a specific algorithm to fit the target problems, not flexible to transfer. | |
| FCIM | Basic | Discover intrinsic correlations within platforms [25], mount features [25], or task behaviors [26]. | Knowledge type: MPAMS organizational features. Knowledge interpretability: Low, due to vague strike effectiveness feature. | (1) Localized knowledge composition at separate layers, which neglects multi-layer collaboration modes in MPAMS. (2) Limited understanding of the decision motivation, which restricts the knowledge transferability | |
| Causality oriented | Discover correlations between strike effectiveness and above-mentioned task behaviors [27], platforms [28,29], or mount features [29]. | Knowledge type: Strike effectiveness + MPAMS organizational features. Knowledge interpretability: Higher, by incorporating causality correlation. | |||
| Knowledge efficiency | FCIM | Design new item storage structures and pruning strategies [33,34,35,36,37,38,39]. | Reduce searching space and accelerate mining speed. | Cannot adapt to the features of MPAMS datasets. | |
| Transaction Sets D in the Database | Frequent Closed Itemset Family for D | |||
|---|---|---|---|---|
| (1, abcdefgh) (2, abef) (3, bcfgh) (4, befgh) (5, acdg) | (6, abdefh) (7, abcd) (8, bc) (9, d) (10, gh) | 1-abcd:2 2-abd:3 3-ab:4 4-acdg:2 5-acd:3 6-adfh:2 7-ad:4 8-aef:3 | 9-a:5 10-bcfgh:2 11-bc:4 12-befh:3 13-bef:4 14-bfh:4 15-bf:5 16-b:7 | 17-cg:3 18-c:5 19-d:5 20-gh:4 21-g:5 22-h:5 |
| Category | Symbol | Feature | Calculation Formula | Integration |
|---|---|---|---|---|
| Perception | Cprcp | detection range × detection probability | Max | |
| Attacking | Cattk | (damage point × range) × hit probability × number | Sum | |
| Electronic attack | Celec | (damage point × range) × hit probability × number | Sum | |
| Defense | Cdefs | damage point/escape time | Sum | |
| Maneuverability | CMnur | speed × flight range under that speed | Avg | |
| Concealment | Ccncl | (visible discovery distance × infrared discovery distance × radar reflective area)−1 | Min |
| Dataset | Transaction | Avg (t) | Item | Density |
|---|---|---|---|---|
| Mushroom1 | 8124 | 23 | 119 | 19.3% |
| Retail1 | 88,163 | 10.4 | 16,470 | 0.06% |
| Synth2 | 100,000 | 25.4 | 10,000 | 0.25% |
| Synth22 | 10,000 | 25.5 | 1000 | 2.5% |
| Contextual Capability(A1) | Organization Element (A2) | Index | Firepower Effectiveness (B) | Count |
|---|---|---|---|---|
| Sprcp,Wattk,Selec, Sdefs,Smnur,Bcnc 1 | ISR(AEW)→Feint(UAV)→Elec(F(AR))→Escort(F[A] + FB[A]) →Strike(B[UL] +F[L] + FB[L]) 2 | 1 | 3 | 12 |
| Bprcp,Battk,Selec, Bdefs,Smnur,Wcncl | ISR(AEW)→Escort(F[A] + FB[A]) →Strike(UAV + B[UL] + FB[L] + F(L)) | 2 | 13 | |
| 3 | 10 | |||
| 4 | 1 | |||
| Bprcp,Battk,Selec, Bdefs,Bmnur,Wcncl | ISR(AEW)→Feint(UAV)→Strike(B[UL] + FB[L] + F[L]) | 5 | 11 | |
| 6 | 8 | |||
| Bprcp,Sattk,Selec, Wdefs,Wmnur,Scncl | ISR(AEW)→Feint(UAV)→Escort(F[A])→Strike(B[UL]) | 7 | 18 | |
| Bprcp,Sattk,Selec, Wdefs,Wmnur,Wcncl | ISR(AEW)→Feint(UAV)→ Escort(F[A])→Strike(B[Bomb]) | 8 | 6 | |
| Bprcp,Battk,Selec, Bdefs,Bmnur,Scncl | ISR(AEW)→Feint(UAV)→Escort(F[A])→Strike(B[UL] + F[C]) | 9 | 4 | |
| 10 | 10 | |||
| 11 | 10 | |||
| Bprcp,Battk,Selec, Bdefs,Wmnur,Scncl | ISR(AEW)→Feint(UAV)→Escort(F[A] + FB[A]) →Strike(B[UL] + FB[C]) | 12 | 1 | |
| Bprcp,Sattk,Selec, Sdefs,Bmnur,Wcncl | ISR(AEW)→Feint(UAV)→Escort(F[A] + FB[A]) →Strike(B[UL] + F[L] + FB[C]) | 13 | 14 | |
| Bprcp,Wattk,Selec, Sdefs,Bmnur,Scncl | ISR(AEW)→Feint(UAV)→Escort(F[A] + FB[A]) →Strike(B[UL] + F[L] + FB[L]) | 14 | 4 | |
| 15 | 12 | |||
| Bprcp,Battk,Selec, Sdefs,Bmnur,Bcncl | ISR(AEW)→Feint(UAV)→Escort(F[A] + FB[A]) →Strike(B[UL] + F[L] + FB[C + L]) | 16 | 14 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Y.; Wang, M.; Chu, W.; Wang, G. Organization Preference Knowledge Acquisition of Multi-Platform Aircraft Mission System Utilizing Frequent Closed Itemset Mining. Aerospace 2023, 10, 166. https://doi.org/10.3390/aerospace10020166
Wu Y, Wang M, Chu W, Wang G. Organization Preference Knowledge Acquisition of Multi-Platform Aircraft Mission System Utilizing Frequent Closed Itemset Mining. Aerospace. 2023; 10(2):166. https://doi.org/10.3390/aerospace10020166
Chicago/Turabian StyleWu, Yuqian, Miao Wang, Wenkui Chu, and Guoqing Wang. 2023. "Organization Preference Knowledge Acquisition of Multi-Platform Aircraft Mission System Utilizing Frequent Closed Itemset Mining" Aerospace 10, no. 2: 166. https://doi.org/10.3390/aerospace10020166
APA StyleWu, Y., Wang, M., Chu, W., & Wang, G. (2023). Organization Preference Knowledge Acquisition of Multi-Platform Aircraft Mission System Utilizing Frequent Closed Itemset Mining. Aerospace, 10(2), 166. https://doi.org/10.3390/aerospace10020166