Certificate Management Scheme for VANETs Using Blockchain Structure
Abstract
:1. Introduction
Contribution
2. Background and Related Works
Comparison of Our Proposal with Related Works
3. Preliminaries
3.1. Notation
3.2. Blockchain Technology
3.3. Encryption Scheme
3.4. Digital Signature Schemes
3.5. Ring Signatures
- (): This algorithm takes as input security parameter λ and outputs a public and secret key pair ().
- (): This randomized algorithm takes as input a set of public keys , a secret signing key , and a message M, where .
- (,M): This deterministic algorithm takes as input the ring and a purported signature Σ on M, and outputs either 1 (valid) or 0 (invalid).
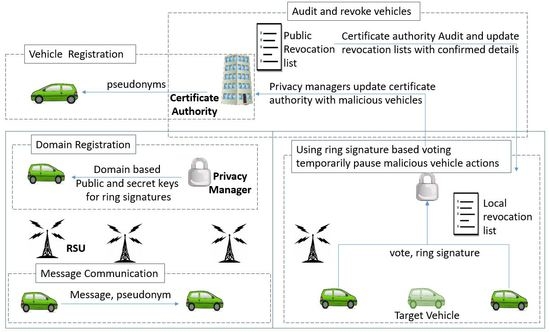
4. High Level Idea of the Proposal
4.1. Blockchain Based Structure
4.2. Local Revocation—A Voting Based Revocation
4.3. Preserving the Privacy of Voting Participants
4.4. Proposed Scheme
- : Network consists of PMs who has one security domain. Each PM oversees a certain amount of RSUs based on the geographical establishment of RSUs. CA generates an encryption–decryption key pair () and gives the decryption key () to the established PMs. Moreover, CA initializes and broadcasts CRL and LCRLs.
- : A new vehicle who wants to join the network has its vehicle id interact with CA, and CA issues a set of short-lived pseudonym certificates () to the vehicle. CA maintains a mapping table of and pseudonyms .
- : When a vehicle i enters to an area, the relevant PM obtains pseudonym certificate ID () of the vehicle, which is currently in the active status and issues a public and secret key pair () to the vehicle.
- : A vehicle transmits a message M by signing the message using the secret signing key of a valid pseudonym and appending the pseudonym certificate . The message receiving party (another vehicle or RSU) authenticates the sender and accepts the message if authentication is passed. The receiver verifies the sender’s certificate first against the LCRL and then against the CRL.
- : When a PM observes or receives a complaint against misbehavior of a vehicle, it initiates voting against that vehicle. Thus, any vehicle that agrees with the voting procedure can send his vote which is signed anonymously using ring signatures. A user i creates a ring R with other users’ public keys and his public key , and generates a ring signature using the relevant secret key . Once the vote count reaches the decided threshold value t, PM obtains the targeted vehicle’s certificate-token and adds the token to the local revocation list .
- : Periodically, PMs sends LCRLs to CA with other information. Then, CA investigates, permanently revokes mischievous vehicles, and updates CRL with the vehicle-token. Once the CRL is updated, PMs obtain the copy of CRL, and their LCRL becomes empty because actual misbehavior is punished and added to CRL by CA. Thus, PMs should release the innocent vehicles whose certificates are in LCRL.
5. Construction of the Proposed Scheme
| Algorithm 1: Algorithms of the scheme |
| ; ; ; |
| Return . |
| Parse as ; ; ; |
| For : |
| Select and ; Select a active time period ; |
| ; ; |
| ; ; |
| ; |
| ; |
| ; |
| ; |
| ; |
| Return (); |
| Parse as ; |
| Parse as (); |
| If then return 0; |
| Parse as |
| If is note valid against current-time then return 0; |
| ; |
| Return () |
| Parse as ; |
| Sender: Return |
| Receiver: |
| ; |
| Parse as (); |
| Parse as |
| If is note valid against current-time then ; |
| If , then ; |
| If then ; |
| If then For : If then ; |
| If then For : If then ; |
| Return |
| User i: ; ; |
| Block-Manager: |
| If vote count satisfies the threshold value then do the followings. |
| Parse as (); |
| Parse as |
| Parse as ; |
| Return |
| For : Parse as ; |
| If is dishonest then, |
| Return CRL |
6. Security Discussion
6.1. Security of Certificate Issuing Process
6.2. Security of the Revocation Process
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhang, D.; Zhang, T.; Liu, X. Novel self-adaptive routing service algorithm for application in VANET. Appl. Intell. 2019, 49, 1866–1879. [Google Scholar] [CrossRef]
- World Health Organization. Death on the Roads. Based on the WHO Global Status Report on Road Safety 2018; World Health Organization: Geneva, Switzerland, 2018; Available online: https://extranet.who.int/roadsafety/death-on-the-roads/#deaths (accessed on 10 January 2022).
- World Health Organization. Global Status Report on Road Safety 2018; World Health Organization: Geneva, Switzerland, 2018; Available online: http://apps.who.int/iris/bitstream/handle/10665/277370/WHO-NMH-NVI-18.20-eng.pdf?ua=1 (accessed on 18 August 2021).
- Fiore, M.; Casetti, C.; Chiasserini, C.F. Information sharing in VANETs. In Advances in Vehicular Ad-Hoc Networks: Developments and Challenges; IGI Global: Hershey, PA, USA, 2010; pp. 75–96. [Google Scholar]
- Abassi, R. VANET security and forensics: Challenges and opportunities. Wiley Interdiscip. Rev. Forensic Sci. 2019, 1, e1324. [Google Scholar] [CrossRef]
- Kargl, F.; Papadimitratos, P.; Buttyan, L.; Müter, M.; Schoch, E.; Wiedersheim, B.; Thong, T.V.; Calandriello, G.; Held, A.; Kung, A.; et al. Secure vehicular communication systems: Implementation, performance, and research challenges. IEEE Commun. Mag. 2008, 46, 110–118. [Google Scholar] [CrossRef] [Green Version]
- Petit, J.; Schaub, F.; Feiri, M.; Kargl, F. Pseudonym schemes in vehicular networks: A survey. IEEE Commun. Surv. Tutor. 2014, 17, 228–255. [Google Scholar] [CrossRef]
- Saini, I.; Saad, S.; Jaekel, A. Evaluating the effectiveness of pseudonym changing strategies for location privacy in vehicular ad-hoc network. Secur. Priv. 2019, e68. [Google Scholar] [CrossRef] [Green Version]
- Sheikh, M.S.; Liang, J.; Wang, W. Security and privacy in vehicular ad hoc network and vehicle cloud computing: A survey. Wirel. Commun. Mob. Comput. 2020, 2020, 5129620. [Google Scholar] [CrossRef] [Green Version]
- Hubaux, J.P.; Capkun, S.; Luo, J. The security and privacy of smart vehicles. IEEE Secur. Priv. 2004, 2, 49–55. [Google Scholar] [CrossRef] [Green Version]
- Verheul, E.; Hicks, C.; Garcia, F.D. Ifal: Issue first activate later certificates for v2x. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Stockholm, Sweden, 17–19 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 279–293. [Google Scholar]
- Simplicio, M.A., Jr.; Cominetti, E.L.; Patil, H.K.; Ricardini, J.E.; Silva, M.V.M. ACPC: Efficient revocation of pseudonym certificates using activation codes. Ad Hoc Netw. 2019, 90, 101708. [Google Scholar] [CrossRef]
- Bao, S.; Lei, A.; Cruickshank, H.; Sun, Z.; Asuquo, P.; Hathal, W. A pseudonym certificate management scheme based on blockchain for internet of vehicles. In Proceedings of the 2019 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Fukuoka, Japan, 5–8 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 28–35. [Google Scholar]
- Asghar, M.; Pan, L.; Doss, R. An efficient voting based decentralized revocation protocol for vehicular ad hoc networks. Digit. Commun. Netw. 2020, 6, 422–432. [Google Scholar] [CrossRef]
- Arboit, G.; Crépeau, C.; Davis, C.R.; Maheswaran, M. A localized certificate revocation scheme for mobile ad hoc networks. Ad Hoc Netw. 2008, 6, 17–31. [Google Scholar] [CrossRef]
- Khan, T.; Ahmad, N.; Cao, Y.; Jalal, S.A.; Asif, M.; Cruichshank, H. Certificate revocation in vehicular ad hoc networks techniques and protocols: A survey. Sci. China Inf. Sci. 2017, 60, 100301. [Google Scholar] [CrossRef]
- Parno, B.; Perrig, A. Challenges in securing vehicular networks. In Proceedings of the Workshop on hot topics in networks (HotNets-IV), College Park, MD, USA, 14–15 November 2005; pp. 1–6. [Google Scholar]
- Förster, D.; Kargl, F.; Löhr, H. PUCA: A pseudonym scheme with user-controlled anonymity for vehicular ad-hoc networks (VANET). In Proceedings of the 2014 IEEE Vehicular Networking Conference (VNC), Paderborn, Germany, 3–5 December 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 25–32. [Google Scholar]
- Schaub, F.; Ma, Z.; Kargl, F. Privacy requirements in vehicular communication systems. In Proceedings of the 2009 International Conference on Computational Science and Engineering, Vancouver, BC, Canada, 29–31 August 2009; IEEE: Piscataway, NJ, USA, 2009; Volume 3, pp. 139–145. [Google Scholar]
- Shrestha, R.; Bajracharya, R.; Shrestha, A.P.; Nam, S.Y. A new type of blockchain for secure message exchange in VANET. Digit. Commun. Netw. 2020, 6, 177–186. [Google Scholar] [CrossRef]
- Ravi, N.; Verma, S.; Kavita; Zaman, N.Z.; Talib, M.N. Securing VANET Using Blockchain Technology. J. Phys. Conf. Ser. 2021, 1979, 012035. [Google Scholar] [CrossRef]
- Whyte, W.; Weimerskirch, A.; Kumar, V.; Hehn, T. A security credential management system for V2V communications. In Proceedings of the 2013 IEEE Vehicular Networking Conference, Boston, MA, USA, 16–18 December 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1–8. [Google Scholar]
- Kolleda, J.; Frank, L.; Andrews, S.; Poling, T.; Fitzpatrick, D.; Marousek, J.; Hamilton, B.A. National Security Credential Management System (SCMS) Deployment Support: Scms Baseline Summary Report. 2018. Available online: https://rosap.ntl.bts.gov/view/dot/36397 (accessed on 20 December 2021).
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Papadimitratos, P.; Mezzour, G.; Hubaux, J.P. Certificate revocation list distribution in vehicular communication systems. In Proceedings of the Fifth ACM International Workshop on VehiculAr Inter-NETworking, New York, NY, USA, 15 September 2008; pp. 86–87. [Google Scholar]
- Laberteaux, K.P.; Haas, J.J.; Hu, Y.C. Security certificate revocation list distribution for VANET. In Proceedings of the Fifth ACM International Workshop on VehiculAr Inter-NETworking, San Francisco, CA, USA, 15 September 2008; pp. 88–89. [Google Scholar]
- Wasef, A.; Shen, X. EMAP: Expedite message authentication protocol for vehicular ad hoc networks. IEEE Trans. Mob. Comput. 2011, 12, 78–89. [Google Scholar] [CrossRef]
- Raya, M.; Papadimitratos, P.; Aad, I.; Jungels, D.; Hubaux, J.P. Eviction of misbehaving and faulty nodes in vehicular networks. IEEE J. Sel. Areas Commun. 2007, 25, 1557–1568. [Google Scholar] [CrossRef] [Green Version]
- Wasef, A.; Shen, X. EDR: Efficient decentralized revocation protocol for vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2009, 58, 5214–5224. [Google Scholar] [CrossRef] [Green Version]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 5 January 2022).
- Wang, C.; Cheng, X.; Li, J.; He, Y.; Xiao, K. A survey: Applications of blockchain in the Internet of Vehicles. Eurasip J. Wirel. Commun. Netw. 2021, 2021, 77. [Google Scholar] [CrossRef]
- Bellare, M.; Shi, H.; Zhang, C. Foundations of group signatures: The case of dynamic groups. In Cryptographers’ Track at the RSA Conference, Proceedings of the The Cryptographers’ Track at the RSA Conference 2005, San Francisco, CA, USA, 14–18 February 2005; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3376, pp. 136–153. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Tauman, Y. How to leak a secret. In Proceedings of the ASIACRYPT, Gold Coast, Australia, 9–13 December 2001; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2248, pp. 552–565. [Google Scholar]
- Bender, A.; Katz, J.; Morselli, R. Ring signatures: Stronger definitions, and constructions without random oracles. In Theory of Cryptography Conference, Proceedings of the 3rd Theory of Cryptography Conference, TCC 2006, New York, NY, USA, 4–7 March 2006; Springer: Berlin/Heidelberg, Germany, 2006; Volume 3876, pp. 60–79. [Google Scholar]
- Liu, J.K.; Wei, V.K.; Wong, D.S. Linkable spontaneous anonymous group signature for ad hoc groups. In Australasian Conference on Information Security and Privacy, Proceedings of the 9th Australasian Conference, ACISP 2004, Sydney, Australia, 13–15 July 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 325–335. [Google Scholar]
- Chaum, D.; Van Heyst, E. Group signatures. In Proceedings of the EUROCRYPT 1991, LNCS, Brighton, UK, 8–11 April 1991; Springer: Berlin/Heidelberg, Germany, 1991; Volume 547, pp. 257–265. [Google Scholar]
- Fujisaki, E.; Suzuki, K. Traceable ring signature. In International Workshop on Public Key Cryptography, Proceedings of the 10th International Conference on Practice and Theory in Public-Key Cryptography, Beijing, China, 16–20 April 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 181–200. [Google Scholar]





Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Perera, M.N.S.; Nakamura, T.; Hashimoto, M.; Yokoyama, H.; Cheng, C.-M.; Sakurai, K. Certificate Management Scheme for VANETs Using Blockchain Structure. Cryptography 2022, 6, 20. https://doi.org/10.3390/cryptography6020020
Perera MNS, Nakamura T, Hashimoto M, Yokoyama H, Cheng C-M, Sakurai K. Certificate Management Scheme for VANETs Using Blockchain Structure. Cryptography. 2022; 6(2):20. https://doi.org/10.3390/cryptography6020020
Chicago/Turabian StylePerera, Maharage Nisansala Sevwandi, Toru Nakamura, Masayuki Hashimoto, Hiroyuki Yokoyama, Chen-Mou Cheng, and Kouichi Sakurai. 2022. "Certificate Management Scheme for VANETs Using Blockchain Structure" Cryptography 6, no. 2: 20. https://doi.org/10.3390/cryptography6020020
APA StylePerera, M. N. S., Nakamura, T., Hashimoto, M., Yokoyama, H., Cheng, C. -M., & Sakurai, K. (2022). Certificate Management Scheme for VANETs Using Blockchain Structure. Cryptography, 6(2), 20. https://doi.org/10.3390/cryptography6020020