Featured Reviews of Future Internet Research
Share This Topical Collection
Editor
 Prof. Dr. Dino Giuli
Prof. Dr. Dino Giuli
 Prof. Dr. Dino Giuli
Prof. Dr. Dino Giuli
E-Mail
Website
Collection Editor
Department of Information Engineering (DINFO), University of Florence, Via Santa Marta, 3, 50139 Florence, Italy
Interests: information society; smart cities; e-government; e-mobility; smart mission critical systems; remote-sensing systems
Special Issues, Collections and Topics in MDPI journals
Topical Collection Information
Dear colleagues,
A significant proportion of paper contributions in MDPI’s journal “Future Internet” are increasingly being framed as scientific reviews about selected topics.
This trend appears quite more fitting into the increasing relevance of the wide systemic and interdisciplinary approach of future internet that is needed to assure the quality of the research outcomes and human benefits to be sought for the new age of living based on future internet evolution.
Particularly in such a wide systemic and interdisciplinary scenario, it is particularly advantageous to extend and enhance review paper contributions on important topics in order to properly and beneficially orient current research about future internet.
Therefore, this Topical Collection is introduced and promoted within the editorial asset of the "Future Internet" journal. Within this Topical Collection we will publish contributed and invited papers referring to pre -selected basic and/or hot topics. The Topical Collection will typically join sub-topics of the macrodisciplinary areas 1, 2, 3 included in the "Scope" of this journal.
Prof. Dr. Dino Giuli
Collection Editor
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the collection website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Future Internet is an international peer-reviewed open access monthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript.
The Article Processing Charge (APC) for publication in this open access journal is 1600 CHF (Swiss Francs).
Submitted papers should be well formatted and use good English. Authors may use MDPI's
English editing service prior to publication or during author revisions.
Published Papers (14 papers)
Open AccessReview
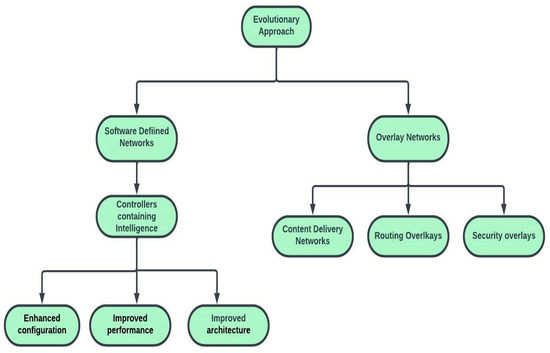
Future Internet Architectures on an Emerging Scale—A Systematic Review
by
Sarfaraz Ahmed Mohammed and Anca L. Ralescu
Cited by 4 | Viewed by 7073
Abstract
Future Internet is a general term that is used to refer to the study of new Internet architectures that emphasize the advancements that are paving the way for the next generation of internet. Today’s internet has become more complicated and arduous to manage
[...] Read more.
Future Internet is a general term that is used to refer to the study of new Internet architectures that emphasize the advancements that are paving the way for the next generation of internet. Today’s internet has become more complicated and arduous to manage due to its increased traffic. This traffic is a result of the transfer of 247 billion emails, the management of more than a billion websites and 735 active top-level domains, the viewing of at least one billion YouTube videos per day (which is the source of main traffic), and the uploading of more than 2.5 billion photos to Facebook every year. The internet was never anticipated to provide quality of service (QoS) support, but one can have a best effort service that provides support for video streams and downloaded media applications. Therefore, the future architecture of the internet becomes crucial. Furthermore, the internet as a service has witnessed many evolving conflicts among its stakeholders, leading to extensive research. This article presents a systematic review of the internet’s evolution and discusses the ongoing research efforts towards new internet architectures, as well as the challenges that are faced in increasing the network’s performance and quality. Moreover, as part of these anticipated future developments, this article draws attention to the Metaverse, which combines the emerging areas of augmented reality, virtual reality, mixed reality, and extended reality, and is considered to be the next frontier for the future internet. This article examines the key role of the blockchain in organizing and advancing the applications and services within the Metaverse. It also discusses the potential benefits and challenges of future internet research. Finally, the article outlines certain directions for future internet research, particularly in the context of utilizing blockchains in the Metaverse.
Full article
►▼
Show Figures
Open AccessReview
The Emerging Technologies of Digital Payments and Associated Challenges: A Systematic Literature Review
by
Khando Khando, M. Sirajul Islam and Shang Gao
Cited by 25 | Viewed by 50156
Abstract
The interplay between finance and technology with the use of the internet triggered the emergence of digital payment technologies. Such technological innovation in the payment industry is the foundation for financial inclusion. However, despite the continuous progress and potential of moving the payment
[...] Read more.
The interplay between finance and technology with the use of the internet triggered the emergence of digital payment technologies. Such technological innovation in the payment industry is the foundation for financial inclusion. However, despite the continuous progress and potential of moving the payment landscape towards digital payments and connecting the population to the ubiquitous digital environment, some critical issues need to be addressed to achieve a more harmonious inclusive and sustainable cashless society. The study aims to provide a comprehensive literature review on the emerging digital payment technologies and associated challenges. By systematically reviewing existing empirical studies, this study puts forward the state-of-the-art classification of digital payment technologies and presents four categories of digital payment technologies:
card payment,
e-payment,mobile payment and cryptocurrencies. Subsequently, the paper presents the key challenges in digital payment technologies categorized into broad themes:
social,
economic,
technical,
awareness and legal. The classification and categorization of payment technologies and associated challenges can be useful to both researchers and practitioners to understand, elucidate and develop a coherent digital payment strategy.
Full article
►▼
Show Figures
Open AccessReview
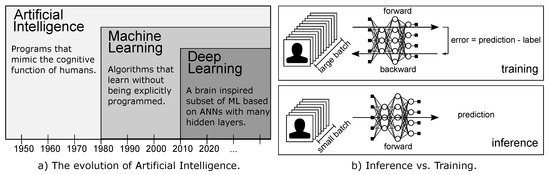
An Updated Survey of Efficient Hardware Architectures for Accelerating Deep Convolutional Neural Networks
by
Maurizio Capra, Beatrice Bussolino, Alberto Marchisio, Muhammad Shafique, Guido Masera and Maurizio Martina
Cited by 135 | Viewed by 14612
Abstract
Deep Neural Networks (DNNs) are nowadays a common practice in most of the Artificial Intelligence (AI) applications. Their ability to go beyond human precision has made these networks a milestone in the history of AI. However, while on the one hand they present
[...] Read more.
Deep Neural Networks (DNNs) are nowadays a common practice in most of the Artificial Intelligence (AI) applications. Their ability to go beyond human precision has made these networks a milestone in the history of AI. However, while on the one hand they present cutting edge performance, on the other hand they require enormous computing power. For this reason, numerous optimization techniques at the hardware and software level, and specialized architectures, have been developed to process these models with high performance and power/energy efficiency without affecting their accuracy. In the past, multiple surveys have been reported to provide an overview of different architectures and optimization techniques for efficient execution of Deep Learning (DL) algorithms. This work aims at providing an up-to-date survey, especially covering the prominent works from the last 3 years of the hardware architectures research for DNNs. In this paper, the reader will first understand what a hardware accelerator is, and what are its main components, followed by the latest techniques in the field of dataflow, reconfigurability, variable bit-width, and sparsity.
Full article
►▼
Show Figures
Open AccessReview
Input Selection Methods for Soft Sensor Design: A Survey
by
Francesco Curreri, Giacomo Fiumara and Maria Gabriella Xibilia
Cited by 24 | Viewed by 5633
Abstract
Soft Sensors (SSs) are inferential models used in many industrial fields. They allow for real-time estimation of hard-to-measure variables as a function of available data obtained from online sensors. SSs are generally built using industries historical databases through data-driven approaches. A critical issue
[...] Read more.
Soft Sensors (SSs) are inferential models used in many industrial fields. They allow for real-time estimation of hard-to-measure variables as a function of available data obtained from online sensors. SSs are generally built using industries historical databases through data-driven approaches. A critical issue in SS design concerns the selection of input variables, among those available in a candidate dataset. In the case of industrial processes, candidate inputs can reach great numbers, making the design computationally demanding and leading to poorly performing models. An input selection procedure is then necessary. Most used input selection approaches for SS design are addressed in this work and classified with their benefits and drawbacks to guide the designer through this step.
Full article
►▼
Show Figures
Open AccessReview
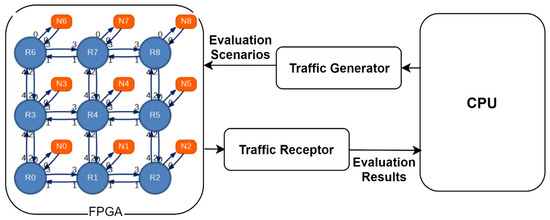
Revisiting the High-Performance Reconfigurable Computing for Future Datacenters
by
Qaiser Ijaz, El-Bay Bourennane, Ali Kashif Bashir and Hira Asghar
Cited by 12 | Viewed by 6854
Abstract
Modern datacenters are reinforcing the computational power and energy efficiency by assimilating field programmable gate arrays (FPGAs). The sustainability of this large-scale integration depends on enabling multi-tenant FPGAs. This requisite amplifies the importance of communication architecture and virtualization method with the required features
[...] Read more.
Modern datacenters are reinforcing the computational power and energy efficiency by assimilating field programmable gate arrays (FPGAs). The sustainability of this large-scale integration depends on enabling multi-tenant FPGAs. This requisite amplifies the importance of communication architecture and virtualization method with the required features in order to meet the high-end objective. Consequently, in the last decade, academia and industry proposed several virtualization techniques and hardware architectures for addressing resource management, scheduling, adoptability, segregation, scalability, performance-overhead, availability, programmability, time-to-market, security, and mainly, multitenancy. This paper provides an extensive survey covering three important aspects—discussion on non-standard terms used in existing literature, network-on-chip evaluation choices as a mean to explore the communication architecture, and virtualization methods under latest classification. The purpose is to emphasize the importance of choosing appropriate communication architecture, virtualization technique and standard language to evolve the multi-tenant FPGAs in datacenters. None of the previous surveys encapsulated these aspects in one writing. Open problems are indicated for scientific community as well.
Full article
►▼
Show Figures
Open AccessReview
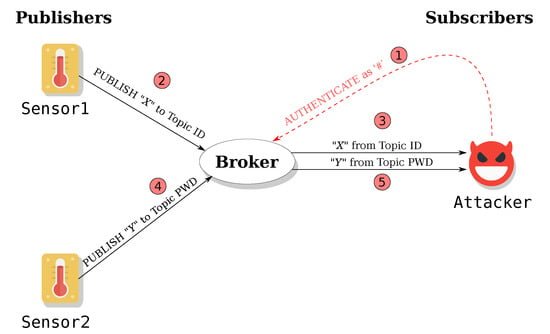
Security of IoT Application Layer Protocols: Challenges and Findings
by
Giuseppe Nebbione and Maria Carla Calzarossa
Cited by 92 | Viewed by 12446
Abstract
IoT technologies are becoming pervasive in public and private sectors and represent presently an integral part of our daily life. The advantages offered by these technologies are frequently coupled with serious security issues that are often not properly overseen or even ignored. The
[...] Read more.
IoT technologies are becoming pervasive in public and private sectors and represent presently an integral part of our daily life. The advantages offered by these technologies are frequently coupled with serious security issues that are often not properly overseen or even ignored. The IoT threat landscape is extremely wide and complex and involves a wide variety of hardware and software technologies. In this framework, the security of application layer protocols is of paramount importance since these protocols are at the basis of the communications among applications and services running on different IoT devices and on cloud/edge infrastructures. This paper offers a comprehensive survey of application layer protocol security by presenting the main challenges and findings. More specifically, the paper focuses on the most popular protocols devised in IoT environments for messaging/data sharing and for service discovery. The main threats of these protocols as well as the Common Vulnerabilities and Exposures (CVE) for their products and services are analyzed and discussed in detail. Good practices and measures that can be adopted to mitigate threats and attacks are also investigated. Our findings indicate that ensuring security at the application layer is very challenging. IoT devices are exposed to numerous security risks due to lack of appropriate security services in the protocols as well as to vulnerabilities or incorrect configuration of the products and services being deployed. Moreover, the constrained capabilities of these devices affect the types of security services that can be implemented.
Full article
►▼
Show Figures
Open AccessReview
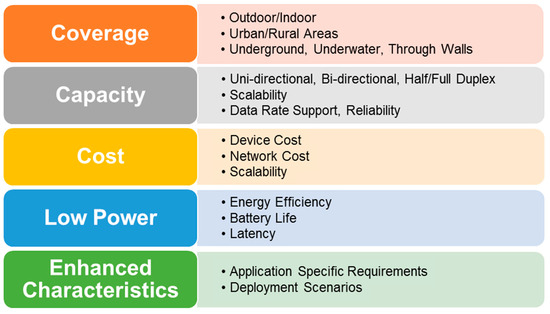
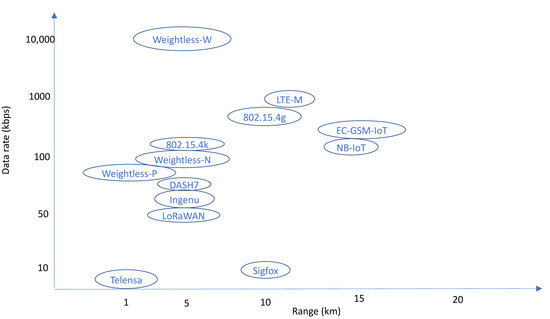
LPWAN Technologies: Emerging Application Characteristics, Requirements, and Design Considerations
by
Bharat S. Chaudhari, Marco Zennaro and Suresh Borkar
Cited by 184 | Viewed by 17350
Abstract
Low power wide area network (LPWAN) is a promising solution for long range and low power Internet of Things (IoT) and machine to machine (M2M) communication applications. This paper focuses on defining a systematic and powerful approach of identifying the key characteristics of
[...] Read more.
Low power wide area network (LPWAN) is a promising solution for long range and low power Internet of Things (IoT) and machine to machine (M2M) communication applications. This paper focuses on defining a systematic and powerful approach of identifying the key characteristics of such applications, translating them into explicit requirements, and then deriving the associated design considerations. LPWANs are resource-constrained networks and are primarily characterized by long battery life operation, extended coverage, high capacity, and low device and deployment costs. These characteristics translate into a key set of requirements including M2M traffic management, massive capacity, energy efficiency, low power operations, extended coverage, security, and interworking. The set of corresponding design considerations is identified in terms of two categories, desired or expected ones and enhanced ones, which reflect the wide range of characteristics associated with LPWAN-based applications. Prominent design constructs include admission and user traffic management, interference management, energy saving modes of operation, lightweight media access control (MAC) protocols, accurate location identification, security coverage techniques, and flexible software re-configurability. Topological and architectural options for interconnecting LPWAN entities are discussed. The major proprietary and standards-based LPWAN technology solutions available in the marketplace are presented. These include Sigfox, LoRaWAN, Narrowband IoT (NB-IoT), and long term evolution (LTE)-M, among others. The relevance of upcoming cellular 5G technology and its complementary relationship with LPWAN technology are also discussed.
Full article
►▼
Show Figures
Open AccessReview
A Survey on Troll Detection
by
Michele Tomaiuolo, Gianfranco Lombardo, Monica Mordonini, Stefano Cagnoni and Agostino Poggi
Cited by 27 | Viewed by 6615
Abstract
A troll is usually defined as somebody who provokes and offends people to make them angry, who wants to dominate any discussion or who tries to manipulate people’s opinions. The problems caused by such persons have increased with the diffusion of social media.
[...] Read more.
A troll is usually defined as somebody who provokes and offends people to make them angry, who wants to dominate any discussion or who tries to manipulate people’s opinions. The problems caused by such persons have increased with the diffusion of social media. Therefore, on the one hand, press bodies and magazines have begun to address the issue and to write articles about the phenomenon and its related problems while, on the other hand, universities and research centres have begun to study the features characterizing trolls and to look for solutions for their identification. This survey aims at introducing the main researches dedicated to the description of trolls and to the study and experimentation of methods for their detection.
Full article
Open AccessArticle
A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices
by
Miao Yu, Jianwei Zhuge, Ming Cao, Zhiwei Shi and Lin Jiang
Cited by 63 | Viewed by 14506
Abstract
With the prosperity of the Internet of Things (IoT) industry environment, the variety and quantity of IoT devices have grown rapidly. IoT devices have been widely used in smart homes, smart wear, smart manufacturing, smart cars, smart medical care, and many other life-related
[...] Read more.
With the prosperity of the Internet of Things (IoT) industry environment, the variety and quantity of IoT devices have grown rapidly. IoT devices have been widely used in smart homes, smart wear, smart manufacturing, smart cars, smart medical care, and many other life-related fields. With it, security vulnerabilities of IoT devices are emerging endlessly. The proliferation of security vulnerabilities will bring severe risks to users’ privacy and property. This paper first describes the research background, including IoT architecture, device components, and attack surfaces. We review state-of-the-art research on IoT device vulnerability discovery, detection, mitigation, and other related works. Then, we point out the current challenges and opportunities by evaluation. Finally, we forecast and discuss the research directions on vulnerability analysis techniques of IoT devices.
Full article
►▼
Show Figures
Open AccessReview
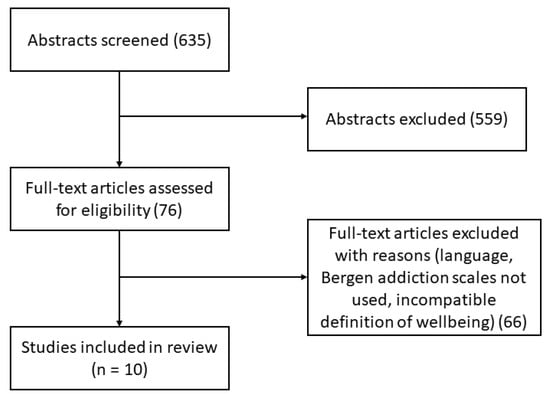
Well-Being and Social Media: A Systematic Review of Bergen Addiction Scales
by
Mirko Duradoni, Federico Innocenti and Andrea Guazzini
Cited by 75 | Viewed by 25296
Abstract
Does social media addiction impair the well-being of non-clinical individuals? Despite the Internet being able to be considered as a promoting factor for individual empowerment, previous literature suggests that the current massive availability of Information and Communication Technologies (ICT) may be dangerous for
[...] Read more.
Does social media addiction impair the well-being of non-clinical individuals? Despite the Internet being able to be considered as a promoting factor for individual empowerment, previous literature suggests that the current massive availability of Information and Communication Technologies (ICT) may be dangerous for users’ well-being. This article discusses the relationship between the most used social media addiction measures (i.e., the Bergen Facebook Addiction Scale—BFAS, the Bergen Social Media Addiction Scale—BSMAS) and well-being. A systematic review considering all the publications indexed by PsycInfo, PsycArticles, PubMed, Science Direct, Sociological Abstracts, Academic Search Complete, and Google Scholar databases was performed to collect the data. Ten of 635 studies were included in the qualitative synthesis. Overall, most of the included works captured a negative but small relationship between BFAS/BSMAS and well-being, across multiple definitions and measurement.
Full article
►▼
Show Figures
Open AccessFeature PaperReview
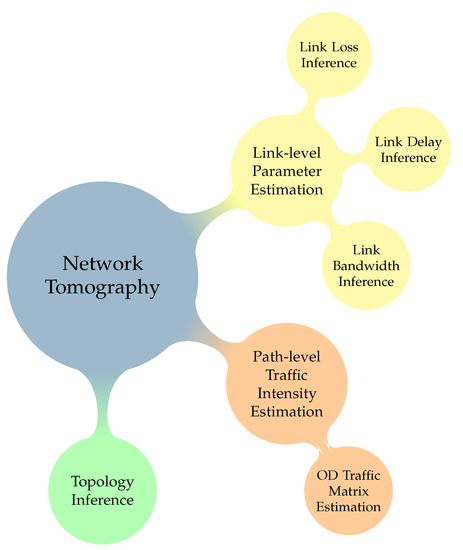
A Review of Advanced Algebraic Approaches Enabling Network Tomography for Future Network Infrastructures
by
Grigorios Kakkavas, Despoina Gkatzioura, Vasileios Karyotis and Symeon Papavassiliou
Cited by 25 | Viewed by 5261
Abstract
Network tomography has emerged as one of the lean approaches for efficient network monitoring, especially aiming at addressing the ever-increasing requirements for scaling and efficiency in modern network architectures and infrastructures. In this paper, we explore
network coding and
compressed sensing as enabling
[...] Read more.
Network tomography has emerged as one of the lean approaches for efficient network monitoring, especially aiming at addressing the ever-increasing requirements for scaling and efficiency in modern network architectures and infrastructures. In this paper, we explore
network coding and
compressed sensing as enabling technologies in the context of network tomography. Both approaches capitalize on algebraic tools for achieving accuracy while allowing scaling of operation as the size of the monitored network increases. Initially, a brief overview of the tomographic problems and the related classification of methods is provided to better comprehend the problems encountered and solutions provided to date. Subsequently, we present representative approaches that employ either one of the aforementioned technologies and we comparatively describe their fundamental operation. Eventually, we provide a qualitative comparison of features and approaches that can be used for further research and technology development for network monitoring in future Internet infrastructures.
Full article
►▼
Show Figures
Open AccessFeature PaperReview
Long-Range Wireless Radio Technologies: A Survey
by
Brandon Foubert and Nathalie Mitton
Cited by 72 | Viewed by 16949
Abstract
Wireless networks are now a part of the everyday life of many people and are used for many applications. Recently, new technologies that enable low-power and long-range communications have emerged. These technologies, in opposition to more traditional communication technologies rather defined as "short
[...] Read more.
Wireless networks are now a part of the everyday life of many people and are used for many applications. Recently, new technologies that enable low-power and long-range communications have emerged. These technologies, in opposition to more traditional communication technologies rather defined as "short range", allow kilometer-wide wireless communications. Long-range technologies are used to form Low-Power Wide-Area Networks (LPWAN). Many LPWAN technologies are available, and they offer different performances, business models etc., answering different applications’ needs. This makes it hard to find the right tool for a specific use case. In this article, we present a survey about the long-range technologies available presently as well as the technical characteristics they offer. Then we propose a discussion about the energy consumption of each alternative and which one may be most adapted depending on the use case requirements and expectations, as well as guidelines to choose the best suited technology.
Full article
►▼
Show Figures
Open AccessReview
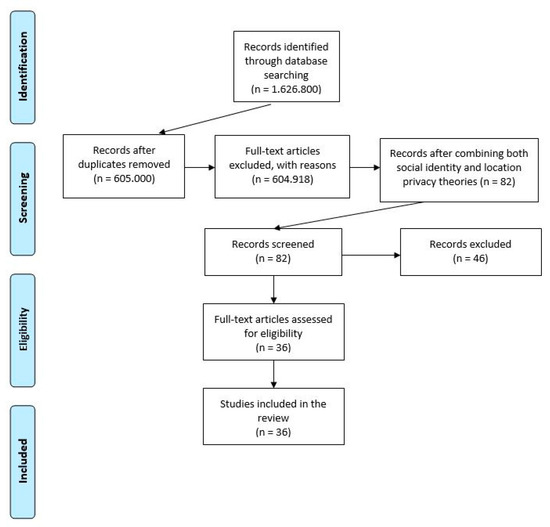
Toward Addressing Location Privacy Issues: New Affiliations with Social and Location Attributes
by
Katerina Vgena, Angeliki Kitsiou, Christos Kalloniatis, Dimitris Kavroudakis and Stefanos Gritzalis
Cited by 7 | Viewed by 4206
Abstract
Nowadays, location-sharing applications (LSA) within social media enable users to share their location information at different levels of precision. Users on their side are willing to disclose this kind of information in order to represent themselves in a socially acceptable online way. However,
[...] Read more.
Nowadays, location-sharing applications (LSA) within social media enable users to share their location information at different levels of precision. Users on their side are willing to disclose this kind of information in order to represent themselves in a socially acceptable online way. However, they express privacy concerns regarding potential malware location-sharing applications, since users’ geolocation information can provide affiliations with their social identity attributes that enable the specification of their behavioral normativity, leading to sensitive information disclosure and privacy leaks. This paper, after a systematic review on previous social and privacy location research, explores the overlapping of these fields in identifying users’ social attributes through examining location attributes while online, and proposes a targeted set of location privacy attributes related to users’ socio-spatial characteristics within social media.
Full article
►▼
Show Figures
Open AccessReview
Blockchain Technology for Intelligent Environments
by
Spyros Voulgaris, Nikos Fotiou, Vasilios A. Siris, George C. Polyzos, Mikael Jaatinen and Yannis Oikonomidis
Cited by 19 | Viewed by 7523
Abstract
In the last few years, we have been witnessing the convergence of the physical with the digital world. The Internet of Things (IoT) is progressing at a fast pace, and IoT devices are becoming pervasive in our physical environments, bringing the vision of
[...] Read more.
In the last few years, we have been witnessing the convergence of the physical with the digital world. The Internet of Things (IoT) is progressing at a fast pace, and IoT devices are becoming pervasive in our physical environments, bringing the vision of Intelligent Environments closer to reality. At the same time, the newly-introduced blockchain technology is offering for the first time ever cryptographically proven trust based on a set of mutually untrusted nodes. Blockchain technology thus has the potential to become a key component of many IoT systems, offering them an unprecedented level of accountability, transparency, and reliability. This paper first lays out the principles on which blockchain systems are operating, along with descriptions of the most noteworthy blockchain implementations. It then presents a number of systems through which blockchains may interact with external systems and third-party data sources. Finally, it provides a survey of the state-of-the-art blockchain-based systems targeting IoT applications.
Full article
►▼
Show Figures