Named Data Networking Architecture
A special issue of Future Internet (ISSN 1999-5903).
Deadline for manuscript submissions: closed (31 December 2019) | Viewed by 5573
Special Issue Editors
Interests: distributed computing; AI; machine learning; deep learning; computing models
Special Issues, Collections and Topics in MDPI journals
Special Issue Information
Dear Colleagues,
As you well know, information processing and information networking architectures took a new direction with the advent of digital computers based on the von Neumann stored-program implementation of the Turing Machine and have contributed to the current accelerated pace of communication, collaboration, and commerce at almost the speed of light. This Special Issue is devoted to examining the current state-of-the-art and future directions in which information processing entities (IPE) and their networking are influenced by the recent advances in mobile computing, 5G-networks, cloud computing and high-performance 100GbE networks, and low-latency SSD/DRAM storage elements.
Physical Address Based Networks:
The current information processing architecture is based on the Church–Turing thesis, which states “a function on the natural numbers is computable by a human being following an algorithm, ignoring resource limitations, if and only if it is computable by a Turing machine.” Information networking is a result of addressing the “resource limitations” of a computation by using shared resources—scarce and expensive CPU and memory at that time—and distributing the information processing using a physical network. Information processing entities (IPE) communicate with each other using their host (or logical) address (usually an IP address used by private or public networks). A domain name server (DNS) provides the mapping between the location and the IPE. Inside each host, multiple IPEs are distinguished by various ports. During the past five or more decades, IP networking using IP addresses has been the dominant protocol providing information networking services, establishing links between the IPE nodes.
Data Centric or Content Centric Address Based Networks:
With the advent of IPE mobility and the demand for never-fail connectivity in the face of fluctuations in the demand and availability of distributed resources, the focus is shifting to provide location transparency and to address data or content (“what” instead of “where” to access). The global connectivity of interacting IPEs, the ephemeral nature of some of their communications impacted by nondeterministic fluctuations in their environment, and the nature of data they exchange (text, voice, and video) are necessitating a new approach, going beyond the physical address-based networks. Data-oriented network architecture replaces DNS names with flat, self-certifying names and a name-based any-cast primitive above the IP layer. CCN uses an overlay network where servers and routers can find content packets located anywhere on a CCN network by consulting two specialized tables: The pending interest table and the forwarding information base. The FIB lists where content is currently stored, while the PIT traces how past requests were forwarded. Nodes can also pluck content packets they have cached in their own content store (CS) to satisfy requests.
Process or Micro-Service Address Based Networks:
More recently, the focus has been shifting to IPEs as microservices which provide specific business (or other) functions, each acting as an “active” node hiding the details of implementation (which itself could be a subnetwork of IPEs). This provides a new class of hierarchical name-oriented microservice networking, where each node executes a specific behavior based on the input. A control overlay allows microservice network provisioning, monitoring, and reconfiguration as required to address fluctuations in their behavior.
In essence, such a hierarchical named network allows the composition of microservices to create a managed process workflow by enabling dynamic configuration and reconfiguration of the microservice network. Examples are Kubernetes orchestrated microservice networks and DIME (distributed intelligent managed element) networks discussed in the literature. Both use hierarchical named microservice networks (and subnetworks) to provision, monitor, and control information processing structures and their resources while addressing nondeterministic fluctuations in the demand for, or availability of needed computing resources. The DIME networks are recently shown to provide more resiliency, efficiency, and scaling than conventional Turing machine networks by Prof. Mark Burgin using the theory of superrecursive algorithms and inductive Turing machines.
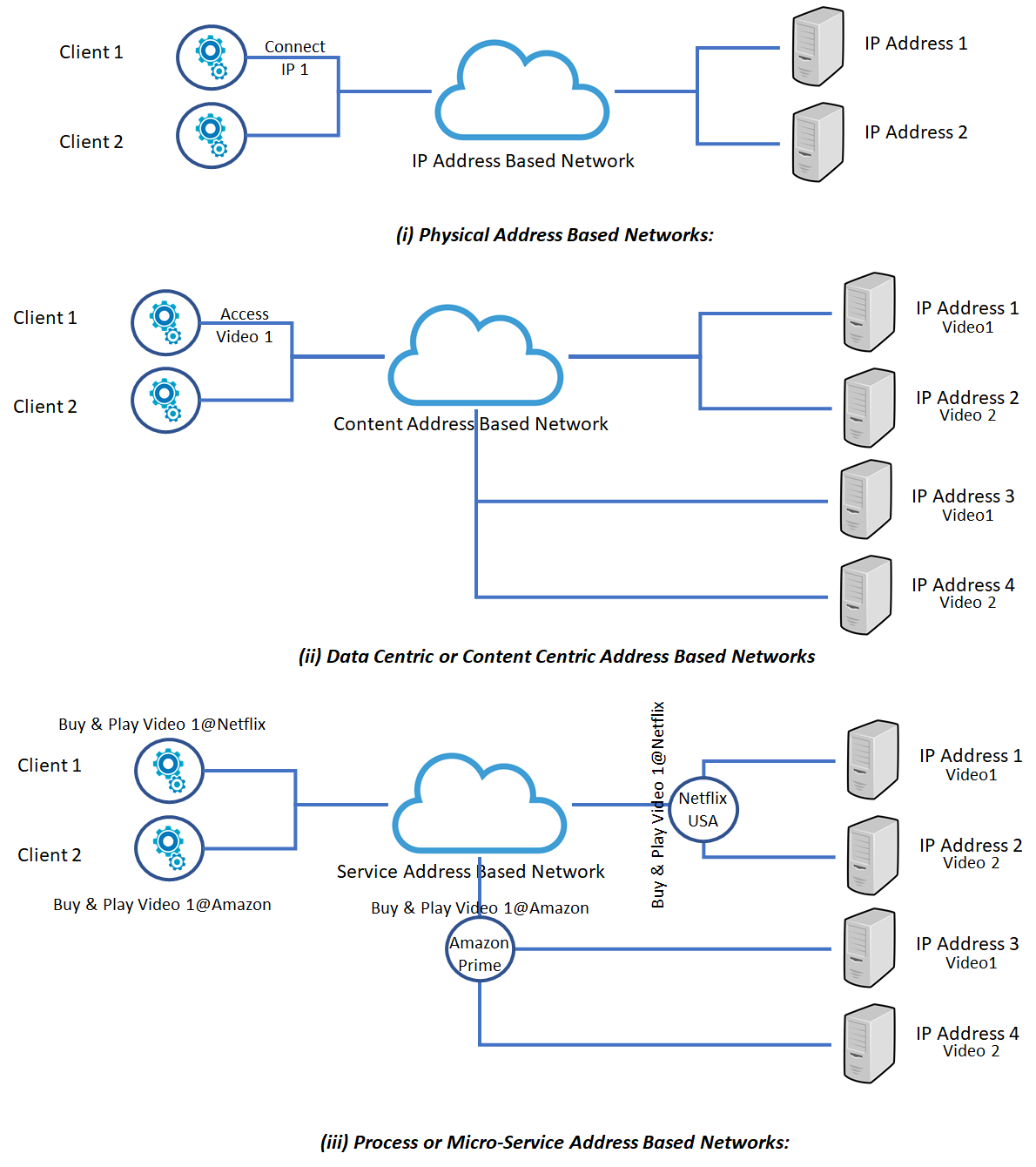
Figure 1. summarizes the three types of networks.
This Special Issue is soliciting conceptual, theoretical, and experimental contributions, discussing and treating challenges, state-of-the-art, and solutions to a set of currently unresolved key questions including but not limited to the following themes related to all sorts of named networks and technologies: Architecture, infrastructure, performance analysis, optimization, orchestration, applications, interoperability, scalability, security, business and technoeconomic aspects, etc.
Dr. Rao Mikkilineni
Dr. Giovanni Morana
Guest Editors
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the special issue website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Future Internet is an international peer-reviewed open access monthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript. The Article Processing Charge (APC) for publication in this open access journal is 1600 CHF (Swiss Francs). Submitted papers should be well formatted and use good English. Authors may use MDPI's English editing service prior to publication or during author revisions.
Keywords
- Computing models for information processing and information networking architectures
- Named network architectures (NNA), design, and Implementation
- Data-oriented network architectures (DONA)
- Content-centric networks (CCN)
- High-performance and low-latency networks
- Network availability and security
- Network slicing and hierarchical controllers
- Content distribution networks (CDN)
- NFV architectures and design
- Software defined networks (SDN)
- Data/control plane performance, interoperability, and scalability
- Machine learning and big data analytics to manage networks
- Performance analysis and optimization
- Resource dimensioning and optimization, traffic offloading
- SDN-NFV support for Internet of Things (IoT)
- SDN-NFV support for big data computing
- Edge and fog computing
- Semantic technologies and ontologies for SDN/NFV
- Network service
Benefits of Publishing in a Special Issue
- Ease of navigation: Grouping papers by topic helps scholars navigate broad scope journals more efficiently.
- Greater discoverability: Special Issues support the reach and impact of scientific research. Articles in Special Issues are more discoverable and cited more frequently.
- Expansion of research network: Special Issues facilitate connections among authors, fostering scientific collaborations.
- External promotion: Articles in Special Issues are often promoted through the journal's social media, increasing their visibility.
- e-Book format: Special Issues with more than 10 articles can be published as dedicated e-books, ensuring wide and rapid dissemination.
Further information on MDPI's Special Issue polices can be found here.






