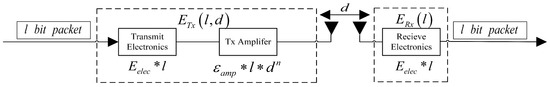
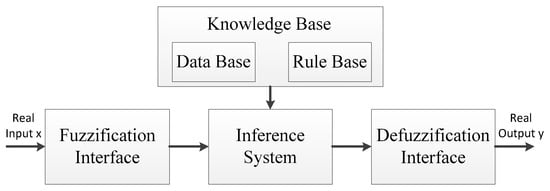
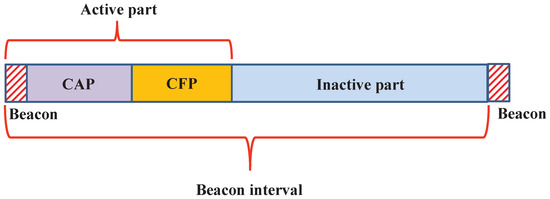
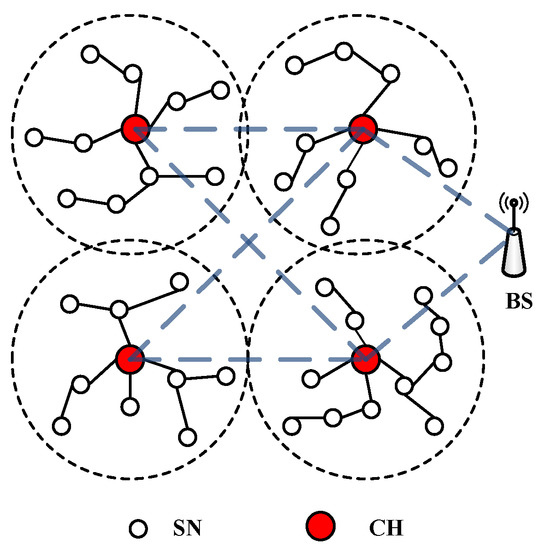
Smart Communication Protocols and Algorithms for Sensor Networks
(Closed)
A topical collection in Sensors (ISSN 1424-8220). This collection belongs to the section "Sensor Networks".
Viewed by 200310
Share This Topical Collection
Editors
 Dr. Jaime Lloret
Dr. Jaime Lloret
 Dr. Jaime Lloret
Dr. Jaime Lloret
E-Mail
Website
Collection Editor
Integrated Management Coastal Research Institute, Universitat Politecnica de Valencia, 46022 Valencia, Spain
Interests: network protocols; network algorithms; wireless sensor networks; ad hoc networks; multimedia streaming
Special Issues, Collections and Topics in MDPI journals
 Prof. Dr. Guangjie Han
Prof. Dr. Guangjie Han
 Prof. Dr. Guangjie Han
Prof. Dr. Guangjie Han
E-Mail
Website
Collection Editor
Department of Information and Communication Engineering, Hohai University, Nanjing, China
Interests: Internet of Things; Industrial Internet of Things; machine learning and artificial intelligence; mobile computing; security and privacy
Special Issues, Collections and Topics in MDPI journals
Topical Collection Information
Dear Colleagues,
The use of smart communication systems is becoming one of the key issues to provide high performance communication systems for sensor networks, deployed in any type of environment, such as cities, rural areas, and underwater areas. Technical advances in such environments will benefit human quality-of-life, increase world sustainability, and decrease the production costs in agriculture and aquaculture.
Selected excellent papers from the following conferences are also welcome to be published in the collection.
- CCF National Conference of Computer Applications (CCF NCCA 2022)
- International Conference on Industrial Application of Artificial Intelligence (IAAI 2022)
- The Seventh International Conference of Pioneering Computer Scientists, Engineers and Educators (ICPCSEE 2022)
Prof. Dr. Jaime Lloret Mauri
Prof. Dr. Guangjie Han
Collection Editors
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the collection website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Sensors is an international peer-reviewed open access semimonthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript.
The Article Processing Charge (APC) for publication in this open access journal is 2600 CHF (Swiss Francs).
Submitted papers should be well formatted and use good English. Authors may use MDPI's
English editing service prior to publication or during author revisions.
Keywords
-
Communication protocols for sensor networks
-
Communication algorithms for sensor networks
-
New architectures for smart sensor networks
-
Artificial intelligence applied to sensor nodes communication
-
Smart communication protocols and algorithms for sensors in smart cities
-
Intelligent communication systems to communicate sensors in precision agriculture
-
Smart underwater sensor networks to communicate sensors in aquaculture precision
Published Papers (34 papers)
Open AccessArticle
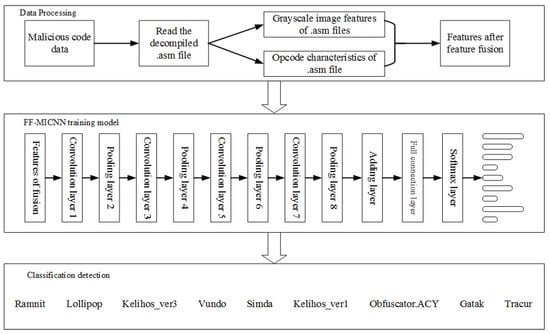
A Malicious Code Detection Method Based on FF-MICNN in the Internet of Things
by
Wenbo Zhang, Yongxin Feng, Guangjie Han, Hongbo Zhu and Xiaobo Tan
Cited by 2 | Viewed by 1920
Abstract
It is critical to detect malicious code for the security of the Internet of Things (IoT). Therefore, this work proposes a malicious code detection algorithm based on the novel feature fusion–malware image convolutional neural network (FF-MICNN). This method combines a feature fusion algorithm
[...] Read more.
It is critical to detect malicious code for the security of the Internet of Things (IoT). Therefore, this work proposes a malicious code detection algorithm based on the novel feature fusion–malware image convolutional neural network (FF-MICNN). This method combines a feature fusion algorithm with deep learning. First, the malicious code is transformed into grayscale image features by image technology, after which the opcode sequence features of the malicious code are extracted by the n-gram technique, and the global and local features are fused by feature fusion technology. The fused features are input into FF-MICNN for training, and an appropriate classifier is selected for detection. The results of experiments show that the proposed algorithm exhibits improvements in its detection speed, the comprehensiveness of features, and accuracy as compared with other algorithms. The accuracy rate of the proposed algorithm is also 0.2% better than that of a detection algorithm based on a single feature.
Full article
►▼
Show Figures
Open AccessArticle
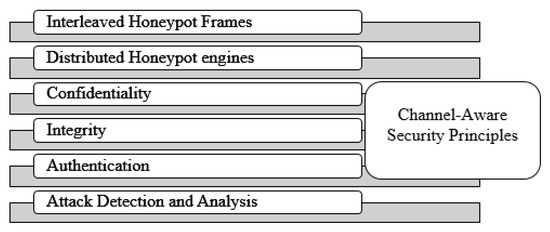
Interleaved Honeypot-Framing Model with Secure MAC Policies for Wireless Sensor Networks
by
Rajasoundaran Soundararajan, Maheswar Rajagopal, Akila Muthuramalingam, Eklas Hossain and Jaime Lloret
Cited by 1 | Viewed by 1915
Abstract
The Wireless Medium Access Control (WMAC) protocol functions by handling various data frames in order to forward them to neighbor sensor nodes. Under this circumstance, WMAC policies need secure data communication rules and intrusion detection procedures to safeguard the data from attackers. The
[...] Read more.
The Wireless Medium Access Control (WMAC) protocol functions by handling various data frames in order to forward them to neighbor sensor nodes. Under this circumstance, WMAC policies need secure data communication rules and intrusion detection procedures to safeguard the data from attackers. The existing secure Medium Access Control (MAC) policies provide expected and predictable practices against channel attackers. These security policies can be easily breached by any intelligent attacks or malicious actions. The proposed Wireless Interleaved Honeypot-Framing Model (WIHFM) newly implements distributed honeypot-based security mechanisms in each sensor node to act reactively against various attackers. The proposed WIHFM creates an optimal Wireless Sensor Network (WSN) channel model, Wireless Interleaved Honeypot Frames (WIHFs), secure hash-based random frame-interleaving principles, node-centric honeypot engines, and channel-covering techniques. Compared to various existing MAC security policies, the proposed model transforms unpredictable IHFs into legitimate frame sequences against channel attackers. Additionally, introducing WIHFs is a new-fangled approach for distributed WSNs. The successful development of the proposed WIHFM ensures resilient security standards and neighbor-based intrusion alert procedures for protecting MAC frames. Particularly, the proposed wireless honeypot methodology creates a novel idea of using honeypot frame traps against open wireless channel attacks. The development of a novel wireless honeypot traps deals with various challenges such as distributed honeypot management principles (node-centric honeypot, secretly interleaved-framing principles, and interleaving/de-interleaving procedures), dynamic network backbone management principles (On Demand Acyclic Connectivity model), and distributed attack isolation policies. This effort provides an effective wireless attack-trapping solution in dynamic WSNs. The simulation results show the advantage of the proposed WIHFM over the existing techniques such as Secure Zebra MAC (SZ-MAC), Blockchain-Assisted Secure-Routing Mechanism (BASR), and the Trust-Based Node Evaluation (TBNE) procedure. The experimental section confirms the proposed model attains a 10% to 14% superior performance compared to the existing techniques.
Full article
►▼
Show Figures
Open AccessArticle
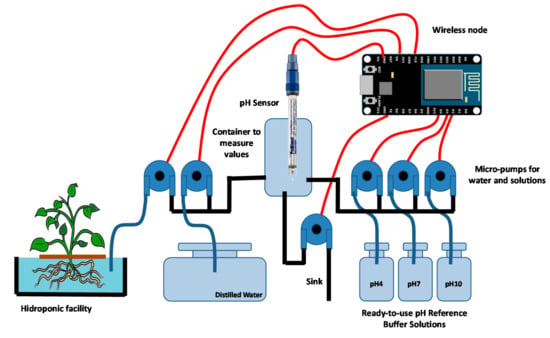
Smart System for Bicarbonate Control in Irrigation for Hydroponic Precision Farming
by
Carlos Cambra, Sandra Sendra, Jaime Lloret and Raquel Lacuesta
Cited by 67 | Viewed by 13718
Abstract
Improving the sustainability in agriculture is nowadays an important challenge. The automation of irrigation processes via low-cost sensors can to spread technological advances in a sector very influenced by economical costs. This article presents an auto-calibrated pH sensor able to detect and adjust
[...] Read more.
Improving the sustainability in agriculture is nowadays an important challenge. The automation of irrigation processes via low-cost sensors can to spread technological advances in a sector very influenced by economical costs. This article presents an auto-calibrated pH sensor able to detect and adjust the imbalances in the pH levels of the nutrient solution used in hydroponic agriculture. The sensor is composed by a pH probe and a set of micropumps that sequentially pour the different liquid solutions to maintain the sensor calibration and the water samples from the channels that contain the nutrient solution. To implement our architecture, we use an auto-calibrated pH sensor connected to a wireless node. Several nodes compose our wireless sensor networks (WSN) to control our greenhouse. The sensors periodically measure the pH level of each hydroponic support and send the information to a data base (DB) which stores and analyzes the data to warn farmers about the measures. The data can then be accessed through a user-friendly, web-based interface that can be accessed through the Internet by using desktop or mobile devices. This paper also shows the design and test bench for both the auto-calibrated pH sensor and the wireless network to check their correct operation.
Full article
►▼
Show Figures
Open AccessArticle
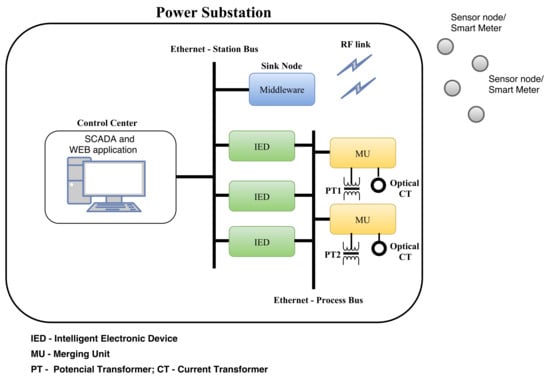
Infrastructure for Integration of Legacy Electrical Equipment into a Smart-Grid Using Wireless Sensor Networks
by
Paulo Régis C. De Araújo, Raimir Holanda Filho, Joel J. P. C. Rodrigues, João P. C. M. Oliveira and Stephanie A. Braga
Cited by 24 | Viewed by 6727
Abstract
At present, the standardisation of electrical equipment communications is on the rise. In particular, manufacturers are releasing equipment for the smart grid endowed with communication protocols such as DNP3, IEC 61850, and MODBUS. However, there are legacy equipment operating in the electricity distribution
[...] Read more.
At present, the standardisation of electrical equipment communications is on the rise. In particular, manufacturers are releasing equipment for the smart grid endowed with communication protocols such as DNP3, IEC 61850, and MODBUS. However, there are legacy equipment operating in the electricity distribution network that cannot communicate using any of these protocols. Thus, we propose an infrastructure to allow the integration of legacy electrical equipment to smart grids by using wireless sensor networks (WSNs). In this infrastructure, each legacy electrical device is connected to a sensor node, and the sink node runs a middleware that enables the integration of this device into a smart grid based on suitable communication protocols. This middleware performs tasks such as the translation of messages between the power substation control centre (PSCC) and electrical equipment in the smart grid. Moreover, the infrastructure satisfies certain requirements for communication between the electrical equipment and the PSCC, such as enhanced security, short response time, and automatic configuration. The paper’s contributions include a solution that enables electrical companies to integrate their legacy equipment into smart-grid networks relying on any of the above mentioned communication protocols. This integration will reduce the costs related to the modernisation of power substations.
Full article
►▼
Show Figures
Open AccessArticle
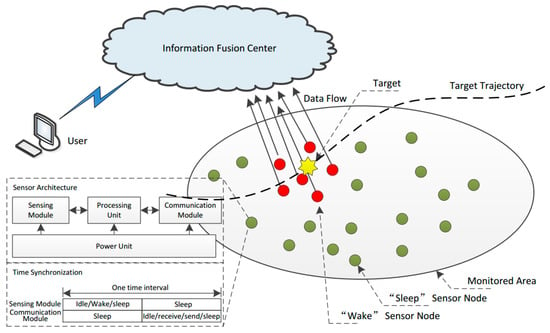
A Novel Energy-Efficient Multi-Sensor Fusion Wake-Up Control Strategy Based on a Biomimetic Infectious-Immune Mechanism for Target Tracking
by
Jie Zhou, Yan Liang, Qiang Shen, Xiaoxue Feng and Quan Pan
Cited by 5 | Viewed by 3976
Abstract
A biomimetic distributed infection-immunity model (BDIIM), inspired by the immune mechanism of an infected organism, is proposed in order to achieve a high-efficiency wake-up control strategy based on multi-sensor fusion for target tracking. The resultant BDIIM consists of six sub-processes reflecting the infection-immunity
[...] Read more.
A biomimetic distributed infection-immunity model (BDIIM), inspired by the immune mechanism of an infected organism, is proposed in order to achieve a high-efficiency wake-up control strategy based on multi-sensor fusion for target tracking. The resultant BDIIM consists of six sub-processes reflecting the infection-immunity mechanism: occurrence probabilities of direct-infection (DI) and cross-infection (CI), immunity/immune-deficiency of DI and CI, pathogen amount of DI and CI, immune cell production, immune memory, and pathogen accumulation under immunity state. Furthermore, a corresponding relationship between the BDIIM and sensor wake-up control is established to form the collaborative wake-up method. Finally, joint surveillance and target tracking are formulated in the simulation, in which we show that the energy cost and position tracking error are reduced to 50.8% and 78.9%, respectively. Effectiveness of the proposed BDIIM algorithm is shown, and this model is expected to have a significant role in guiding the performance improvement of multi-sensor networks.
Full article
►▼
Show Figures
Open AccessArticle
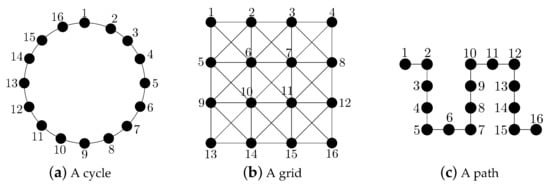
Analysis of Known Linear Distributed Average Consensus Algorithms on Cycles and Paths
by
Jesús Gutiérrez-Gutiérrez, Marta Zárraga-Rodríguez and Xabier Insausti
Cited by 11 | Viewed by 3822
Abstract
In this paper, we compare six known linear distributed average consensus algorithms on a sensor network in terms of convergence time (and therefore, in terms of the number of transmissions required). The selected network topologies for the analysis (comparison) are the cycle and
[...] Read more.
In this paper, we compare six known linear distributed average consensus algorithms on a sensor network in terms of convergence time (and therefore, in terms of the number of transmissions required). The selected network topologies for the analysis (comparison) are the cycle and the path. Specifically, in the present paper, we compute closed-form expressions for the convergence time of four known deterministic algorithms and closed-form bounds for the convergence time of two known randomized algorithms on cycles and paths. Moreover, we also compute a closed-form expression for the convergence time of the fastest deterministic algorithm considered on grids.
Full article
►▼
Show Figures
Open AccessArticle
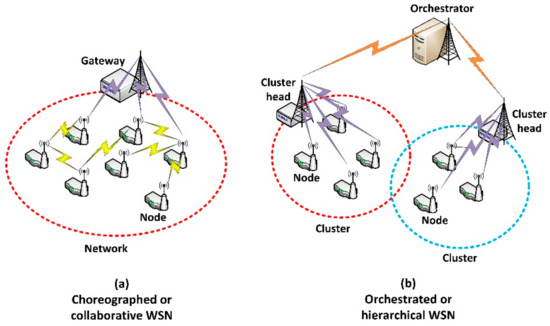
A Hardware-Supported Algorithm for Self-Managed and Choreographed Task Execution in Sensor Networks
by
Borja Bordel, Carlos Miguel, Ramón Alcarria and Tomás Robles
Cited by 13 | Viewed by 4078
Abstract
Nowadays, sensor networks are composed of a great number of tiny resource-constraint nodes, whose management is increasingly more complex. In fact, although collaborative or choreographic task execution schemes are which fit in the most perfect way with the nature of sensor networks, they
[...] Read more.
Nowadays, sensor networks are composed of a great number of tiny resource-constraint nodes, whose management is increasingly more complex. In fact, although collaborative or choreographic task execution schemes are which fit in the most perfect way with the nature of sensor networks, they are rarely implemented because of the high resource consumption of these algorithms (especially if networks include many resource-constrained devices). On the contrary, hierarchical networks are usually designed, in whose cusp it is included a heavy orchestrator with a remarkable processing power, being able to implement any necessary management solution. However, although this orchestration approach solves most practical management problems of sensor networks, a great amount of the operation time is wasted while nodes request the orchestrator to address a conflict and they obtain the required instructions to operate. Therefore, in this paper it is proposed a new mechanism for self-managed and choreographed task execution in sensor networks. The proposed solution considers only a lightweight gateway instead of traditional heavy orchestrators and a hardware-supported algorithm, which consume a negligible amount of resources in sensor nodes. The gateway avoids the congestion of the entire sensor network and the hardware-supported algorithm enables a choreographed task execution scheme, so no particular node is overloaded. The performance of the proposed solution is evaluated through numerical and electronic ModelSim-based simulations.
Full article
►▼
Show Figures
Open AccessArticle
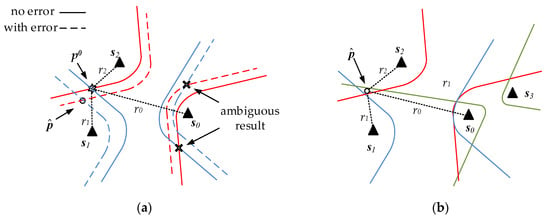
Robust Time-Difference-of-Arrival (TDOA) Localization Using Weighted Least Squares with Cone Tangent Plane Constraint
by
Bonan Jin, Xiaosu Xu and Tao Zhang
Cited by 63 | Viewed by 10924
Abstract
Finding the position of a radiative source based on time-difference-of-arrival (TDOA) measurements from spatially separated receivers has been widely applied in sonar, radar, mobile communications and sensor networks. For the nonlinear model in the process of positioning, Taylor series and other novel methods
[...] Read more.
Finding the position of a radiative source based on time-difference-of-arrival (TDOA) measurements from spatially separated receivers has been widely applied in sonar, radar, mobile communications and sensor networks. For the nonlinear model in the process of positioning, Taylor series and other novel methods are proposed. The idea of cone constraint provides a new way of solving this problem. However, these approaches do not always perform well and are away from the Cramer-Rao-Lower-Bound (CRLB) in the situations when the source is set at the array edge, the noise in measurement is loud, or the initial position is biased. This paper presents a weighted-least-squares (WLS) algorithm with the cone tangent plane constraint for hyperbolic positioning. The method adds the range between the source and the reference sensor as a dimension. So, the space-range frame is established. Different from other cone theories, this paper sets the reference sensor as the apex and finds the optimal source estimation on the cone. WLS is used for the optimal result from the measurement plane equations, a vertical constraint and a cone constraint. The cone constraint equation is linearized by a tangent plane. This method iterates through loops and updates the tangent plane, which approximates the truth-value on the cone. The proposed algorithm was simulated and verified under various conditions of different source positions and noises. Besides, some state-of-the-art algorithms were compared in these simulations. The results show that this algorithm is accurate and robust under poor external environment.
Full article
►▼
Show Figures
Open AccessFeature PaperArticle
Design and Deployment of Low-Cost Sensors for Monitoring the Water Quality and Fish Behavior in Aquaculture Tanks during the Feeding Process
by
Lorena Parra, Sandra Sendra, Laura García and Jaime Lloret
Cited by 111 | Viewed by 14594
Abstract
The monitoring of farming processes can optimize the use of resources and improve its sustainability and profitability. In fish farms, the water quality, tank environment, and fish behavior must be monitored. Wireless sensor networks (WSNs) are a promising option to perform this monitoring.
[...] Read more.
The monitoring of farming processes can optimize the use of resources and improve its sustainability and profitability. In fish farms, the water quality, tank environment, and fish behavior must be monitored. Wireless sensor networks (WSNs) are a promising option to perform this monitoring. Nevertheless, its high cost is slowing the expansion of its use. In this paper, we propose a set of sensors for monitoring the water quality and fish behavior in aquaculture tanks during the feeding process. The WSN is based on physical sensors, composed of simple electronic components. The system proposed can monitor water quality parameters, tank status, the feed falling and fish swimming depth and velocity. In addition, the system includes a smart algorithm to reduce the energy waste when sending the information from the node to the database. The system is composed of three nodes in each tank that send the information though the local area network to a database on the Internet and a smart algorithm that detects abnormal values and sends alarms when they happen. All the sensors are designed, calibrated, and deployed to ensure its suitability. The greatest efforts have been accomplished with the fish presence sensor. The total cost of the sensors and nodes for the proposed system is less than 90 €.
Full article
►▼
Show Figures
Open AccessArticle
Low Cost Efficient Deliverying Video Surveillance Service to Moving Guard for Smart Home
by
Tatiana Gualotuña, Elsa Macías, Álvaro Suárez, Efraín R. Fonseca C. and Andrés Rivadeneira
Cited by 6 | Viewed by 6080
Abstract
Low-cost video surveillance systems are attractive for Smart Home applications (especially in emerging economies). Those systems use the flexibility of the Internet of Things to operate the video camera only when an intrusion is detected. We are the only ones that focus on
[...] Read more.
Low-cost video surveillance systems are attractive for Smart Home applications (especially in emerging economies). Those systems use the flexibility of the Internet of Things to operate the video camera only when an intrusion is detected. We are the only ones that focus on the design of protocols based on intelligent agents to communicate the video of an intrusion in real time to the guards by wireless or mobile networks. The goal is to communicate, in real time, the video to the guards who can be moving towards the smart home. However, this communication suffers from sporadic disruptions that difficults the control and drastically reduces user satisfaction and operativity of the system. In a novel way, we have designed a generic software architecture based on design patterns that can be adapted to any hardware in a simple way. The implanted hardware is of very low economic cost; the software frameworks are free. In the experimental tests we have shown that it is possible to communicate to the moving guard, intrusion notifications (by e-mail and by instant messaging), and the first video frames in less than 20 s. In addition, we automatically recovered the frames of video lost in the disruptions in a transparent way to the user, we supported vertical handover processes and we could save energy of the smartphone's battery. However, the most important thing was that the high satisfaction of the people who have used the system.
Full article
►▼
Show Figures
Open AccessArticle
Optimal Scheduling and Fair Service Policy for STDMA in Underwater Networks with Acoustic Communications
by
Miguel-Ángel Luque-Nieto, José-Miguel Moreno-Roldán, Pablo Otero and Javier Poncela
Cited by 7 | Viewed by 3637
Abstract
In this work, a multi-hop string network with a single sink node is analyzed. A periodic optimal scheduling for TDMA operation that considers the characteristic long propagation delay of the underwater acoustic channel is presented. This planning of transmissions is obtained with the
[...] Read more.
In this work, a multi-hop string network with a single sink node is analyzed. A periodic optimal scheduling for TDMA operation that considers the characteristic long propagation delay of the underwater acoustic channel is presented. This planning of transmissions is obtained with the help of a new geometrical method based on a 2D lattice in the space-time domain. In order to evaluate the performance of this optimal scheduling, two service policies have been compared: FIFO and Round-Robin. Simulation results, including achievable throughput, packet delay, and queue length, are shown. The network fairness has also been quantified with the Gini index.
Full article
►▼
Show Figures
Open AccessArticle
Towards Efficient Wireless Body Area Network Using Two-Way Relay Cooperation
by
Maham Waheed, Rizwan Ahmad, Waqas Ahmed, Micheal Drieberg and Muhammad Mahtab Alam
Cited by 38 | Viewed by 5036
Abstract
The fabrication of lightweight, ultra-thin, low power and intelligent body-borne sensors leads to novel advances in wireless body area networks (WBANs). Depending on the placement of the nodes, it is characterized as in/on body WBAN; thus, the channel is largely affected by body
[...] Read more.
The fabrication of lightweight, ultra-thin, low power and intelligent body-borne sensors leads to novel advances in wireless body area networks (WBANs). Depending on the placement of the nodes, it is characterized as in/on body WBAN; thus, the channel is largely affected by body posture, clothing, muscle movement, body temperature and climatic conditions. The energy resources are limited and it is not feasible to replace the sensor’s battery frequently. In order to keep the sensor in working condition, the channel resources should be reserved. The lifetime of the sensor is very crucial and it highly depends on transmission among sensor nodes and energy consumption. The reliability and energy efficiency in WBAN applications play a vital role. In this paper, the analytical expressions for energy efficiency (EE) and packet error rate (PER) are formulated for two-way relay cooperative communication. The results depict better reliability and efficiency compared to direct and one-way relay communication. The effective performance range of direct vs. cooperative communication is separated by a threshold distance. Based on EE calculations, an optimal packet size is observed that provides maximum efficiency over a certain link length. A smart and energy efficient system is articulated that utilizes all three communication modes, namely direct, one-way relay and two-way relay, as the direct link performs better for a certain range, but the cooperative communication gives better results for increased distance in terms of EE. The efficacy of the proposed hybrid scheme is also demonstrated over a practical quasi-static channel. Furthermore, link length extension and diversity is achieved by joint network-channel (JNC) coding the cooperative link.
Full article
►▼
Show Figures
Open AccessArticle
Energy Efficient Data Transmission for Sensors with Wireless Charging
by
Xiaolin Fang, Junzhou Luo, Weiwei Wu and Hong Gao
Cited by 3 | Viewed by 3485
Abstract
This paper studies the problem of maximizing the energy utilization for data transmission in sensors with periodical wireless charging process while taking into account the thermal effect. Two classes of problems are analyzed: one is the case that wireless charging can process for
[...] Read more.
This paper studies the problem of maximizing the energy utilization for data transmission in sensors with periodical wireless charging process while taking into account the thermal effect. Two classes of problems are analyzed: one is the case that wireless charging can process for only a limited period of time, and the other is the case that wireless charging can process for a long enough time. Algorithms are proposed to solve the problems and analysis of these algorithms are also provided. For the first problem, three subproblems are studied, and, for the general problem, we give an algorithm that can derive a performance bound of
compared to an optimal solution. In addition, for the second problem, we provide an algorithm with
performance bound for the general problem. Simulations confirm the analysis of the algorithms.
Full article
►▼
Show Figures
Open AccessArticle
Optimized Sensor Network and Multi-Agent Decision Support for Smart Traffic Light Management
by
Luis Cruz-Piris, Diego Rivera, Susel Fernandez and Ivan Marsa-Maestre
Cited by 34 | Viewed by 7173
Abstract
One of the biggest challenges in modern societies is to solve vehicular traffic problems. Sensor networks in traffic environments have contributed to improving the decision-making process of Intelligent Transportation Systems. However, one of the limiting factors for the effectiveness of these systems is
[...] Read more.
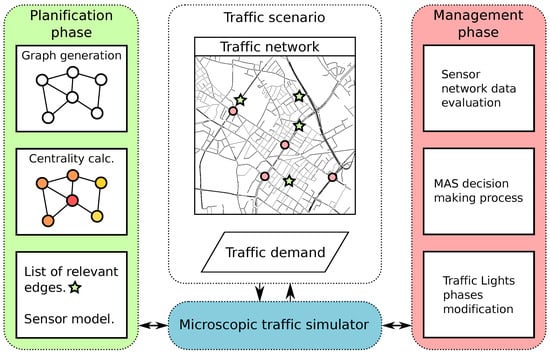
One of the biggest challenges in modern societies is to solve vehicular traffic problems. Sensor networks in traffic environments have contributed to improving the decision-making process of Intelligent Transportation Systems. However, one of the limiting factors for the effectiveness of these systems is in the deployment of sensors to provide accurate information about the traffic. Our proposal is using the centrality measurement of a graph as a base to locate the best locations for sensor installation in a traffic network. After integrating these sensors in a simulation scenario, we define a Multi-Agent Systems composed of three types of agents: traffic light management agents, traffic jam detection agents, and agents that control the traffic lights at an intersection. The ultimate goal of these Multi-Agent Systems is to improve the trip duration for vehicles in the network. To validate our solution, we have developed the needed elements for modelling the sensors and agents in the simulation environment. We have carried out experiments using the Simulation of Urban MObility (SUMO) traffic simulator and the Travel and Activity PAtterns Simulation (TAPAS) Cologne traffic scenario. The obtained results show that our proposal allows to reduce the sensor network while still obtaining relevant information to have a global view of the environment. Finally, regarding the Multi-Agent Systems, we have carried out experiments that show that our proposal is able to improve other existing solutions such as conventional traffic light management systems (static or dynamic) in terms of reduction of vehicle trip duration and reduction of the message exchange overhead in the sensor network.
Full article
►▼
Show Figures
Open AccessArticle
Prototyping a Web-of-Energy Architecture for Smart Integration of Sensor Networks in Smart Grids Domain
by
Víctor Caballero, David Vernet, Agustín Zaballos and Guiomar Corral
Cited by 18 | Viewed by 5738
Abstract
Sensor networks and the Internet of Things have driven the evolution of traditional electric power distribution networks towards a new paradigm referred to as Smart Grid. However, the different elements that compose the Information and Communication Technologies (ICTs) layer of a Smart Grid
[...] Read more.
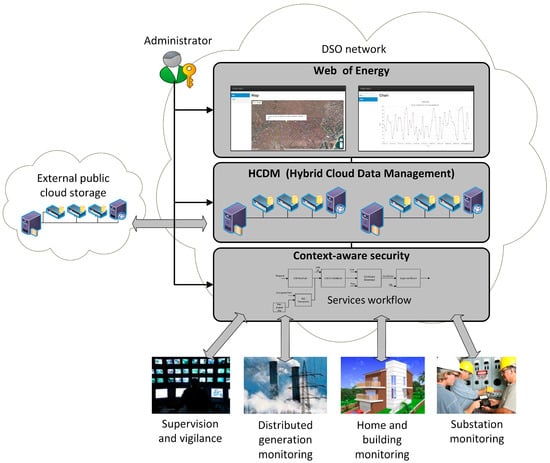
Sensor networks and the Internet of Things have driven the evolution of traditional electric power distribution networks towards a new paradigm referred to as Smart Grid. However, the different elements that compose the Information and Communication Technologies (ICTs) layer of a Smart Grid are usually conceived as isolated systems that typically result in rigid hardware architectures which are hard to interoperate, manage, and to adapt to new situations. If the Smart Grid paradigm has to be presented as a solution to the demand for distributed and intelligent energy management system, it is necessary to deploy innovative IT infrastructures to support these smart functions. One of the main issues of Smart Grids is the heterogeneity of communication protocols used by the smart sensor devices that integrate them. The use of the concept of the Web of Things is proposed in this work to tackle this problem. More specifically, the implementation of a Smart Grid’s Web of Things, coined as the Web of Energy is introduced. The purpose of this paper is to propose the usage of Web of Energy by means of the Actor Model paradigm to address the latent deployment and management limitations of Smart Grids. Smart Grid designers can use the Actor Model as a design model for an infrastructure that supports the intelligent functions demanded and is capable of grouping and converting the heterogeneity of traditional infrastructures into the homogeneity feature of the Web of Things. Conducted experimentations endorse the feasibility of this solution and encourage practitioners to point their efforts in this direction.
Full article
►▼
Show Figures
Open AccessArticle
Self-Learning Power Control in Wireless Sensor Networks
by
Michele Chincoli and Antonio Liotta
Cited by 59 | Viewed by 6941
Abstract
Current trends in interconnecting myriad smart objects to monetize on Internet of Things applications have led to high-density communications in wireless sensor networks. This aggravates the already over-congested unlicensed radio bands, calling for new mechanisms to improve spectrum management and energy efficiency, such
[...] Read more.
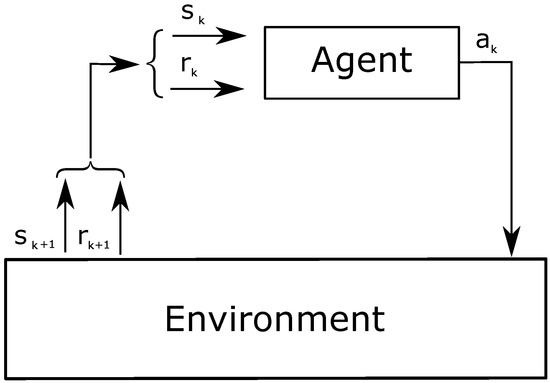
Current trends in interconnecting myriad smart objects to monetize on Internet of Things applications have led to high-density communications in wireless sensor networks. This aggravates the already over-congested unlicensed radio bands, calling for new mechanisms to improve spectrum management and energy efficiency, such as transmission power control. Existing protocols are based on simplistic heuristics that often approach interference problems (i.e., packet loss, delay and energy waste) by increasing power, leading to detrimental results. The scope of this work is to investigate how machine learning may be used to bring wireless nodes to the lowest possible transmission power level and, in turn, to respect the quality requirements of the overall network. Lowering transmission power has benefits in terms of both energy consumption and interference. We propose a protocol of transmission power control through a reinforcement learning process that we have set in a multi-agent system. The agents are independent learners using the same exploration strategy and reward structure, leading to an overall cooperative network. The simulation results show that the system converges to an equilibrium where each node transmits at the minimum power while respecting high packet reception ratio constraints. Consequently, the system benefits from low energy consumption and packet delay.
Full article
►▼
Show Figures
Open AccessArticle
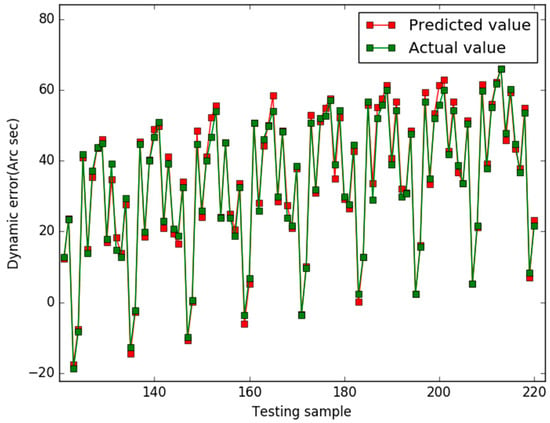
A Sensor Dynamic Measurement Error Prediction Model Based on NAPSO-SVM
by
Minlan Jiang, Lan Jiang, Dingde Jiang, Fei Li and Houbing Song
Cited by 10 | Viewed by 4611
Abstract
Dynamic measurement error correction is an effective way to improve sensor precision. Dynamic measurement error prediction is an important part of error correction, and support vector machine (SVM) is often used for predicting the dynamic measurement errors of sensors. Traditionally, the SVM parameters
[...] Read more.
Dynamic measurement error correction is an effective way to improve sensor precision. Dynamic measurement error prediction is an important part of error correction, and support vector machine (SVM) is often used for predicting the dynamic measurement errors of sensors. Traditionally, the SVM parameters were always set manually, which cannot ensure the model’s performance. In this paper, a SVM method based on an improved particle swarm optimization (NAPSO) is proposed to predict the dynamic measurement errors of sensors. Natural selection and simulated annealing are added in the PSO to raise the ability to avoid local optima. To verify the performance of NAPSO-SVM, three types of algorithms are selected to optimize the SVM’s parameters: the particle swarm optimization algorithm (PSO), the improved PSO optimization algorithm (NAPSO), and the glowworm swarm optimization (GSO). The dynamic measurement error data of two sensors are applied as the test data. The root mean squared error and mean absolute percentage error are employed to evaluate the prediction models’ performances. The experimental results show that among the three tested algorithms the NAPSO-SVM method has a better prediction precision and a less prediction errors, and it is an effective method for predicting the dynamic measurement errors of sensors.
Full article
►▼
Show Figures
Open AccessArticle
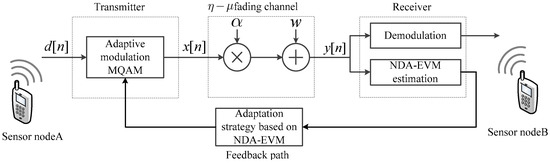
A Novel Adaptive Modulation Based on Nondata-Aided Error Vector Magnitude in Non-Line-Of-Sight Condition of Wireless Sensor Network
by
Fan Yang, Xiaoping Zeng, Haiwei Mao, Xin Jian, Xiaoheng Tan and Derong Du
Cited by 6 | Viewed by 3796
Abstract
The high demand for multimedia applications in environmental monitoring, invasion detection, and disaster aid has led to the rise of wireless sensor network (WSN). With the increase of reliability and diversity of information streams, the higher requirements on throughput and quality of service
[...] Read more.
The high demand for multimedia applications in environmental monitoring, invasion detection, and disaster aid has led to the rise of wireless sensor network (WSN). With the increase of reliability and diversity of information streams, the higher requirements on throughput and quality of service (QoS) have been put forward in data transmission between two sensor nodes. However, lower spectral efficiency becomes a bottleneck in non-line-of-sight (NLOS) transmission of WSN. This paper proposes a novel nondata-aided error vector magnitude based adaptive modulation (NDA-EVM-AM) to solve the problem. NDA-EVM is considered as a new metric to evaluate the quality of NLOS link for adaptive modulation in WSN. By modeling the NLOS scenario as the
fading channel, a closed-form expression for the NDA-EVM of multilevel quadrature amplitude modulation (MQAM) signals over the
fading channel is derived, and the relationship between SER and NDA-EVM is also formulated. Based on these results, NDA-EVM state machine is designed for adaptation strategy. The algorithmic complexity of NDA-EVM-AM is analyzed and the outage capacity of NDA-EVM-AM in an NLOS scenario is also given. The performances of NDA-EVM-AM are compared by simulation, and the results show that NDA-EVM-AM is an effective technique to be used in the NLOS scenarios of WSN. This technique can accurately reflect the channel variations and efficiently adjust modulation order to better match the channel conditions, hence, obtaining better performance in average spectral efficiency.
Full article
►▼
Show Figures
Open AccessArticle
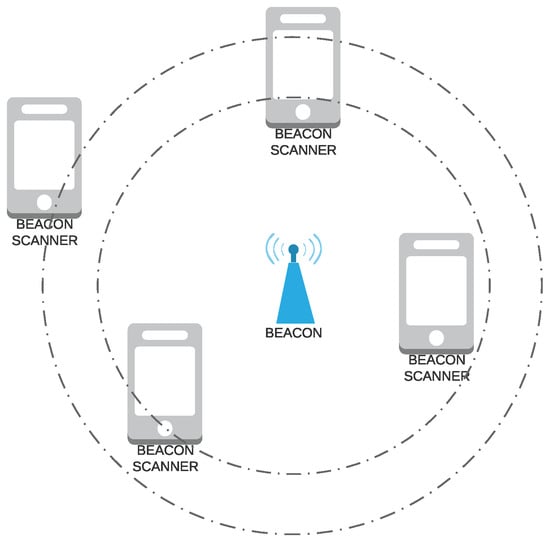
Design and Practical Evaluation of a Family of Lightweight Protocols for Heterogeneous Sensing through BLE Beacons in IoT Telemetry Applications
by
Dixys L. Hernández-Rojas, Tiago M. Fernández-Caramés, Paula Fraga-Lamas and Carlos J. Escudero
Cited by 49 | Viewed by 10695
Abstract
The Internet of Things (IoT) involves a wide variety of heterogeneous technologies and resource-constrained devices that interact with each other. Due to such constraints, IoT devices usually require lightweight protocols that optimize the use of resources and energy consumption. Among the different commercial
[...] Read more.
The Internet of Things (IoT) involves a wide variety of heterogeneous technologies and resource-constrained devices that interact with each other. Due to such constraints, IoT devices usually require lightweight protocols that optimize the use of resources and energy consumption. Among the different commercial IoT devices, Bluetooth and Bluetooth Low Energy (BLE)-based beacons, which broadcast periodically certain data packets to notify their presence, have experienced a remarkable growth, specially due to their application in indoor positioning systems. This article proposes a family of protocols named Lightweight Protocol for Sensors (LP4S) that provides fast responses and enables plug-and-play mechanisms that allow IoT telemetry systems to discover new nodes and to describe and auto-register the sensors and actuators connected to a beacon. Thus, three protocols are defined depending on the beacon hardware characteristics: LP4S-6 (for resource-constraint beacons), LP4S-X (for more powerful beacons) and LP4S-J (for beacons able to run complex firmware). In order to demonstrate the capabilities of the designed protocols, the most restrictive (LP4S-6) is tested after implementing it for a telemetry application in a beacon based on Eddystone (Google’s open beacon format). Thus, the beacon specification is extended in order to increase its ability to manage unlimited sensors in a telemetry system without interfering in its normal operation with Eddystone frames. The performed experiments show the feasibility of the proposed solution and its superiority, in terms of latency and energy consumption, with respect to approaches based on Generic Attribute Profile (GATT) when multiple users connect to a mote or in scenarios where latency is not a restriction, but where low-energy consumption is essential.
Full article
►▼
Show Figures
Open AccessArticle
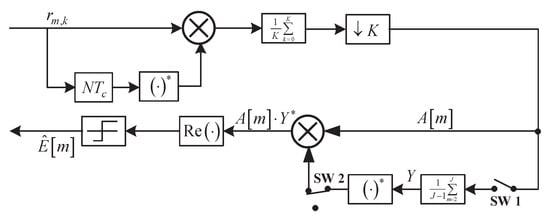
Simple Adaptive Single Differential Coherence Detection of BPSK Signals in IEEE 802.15.4 Wireless Sensor Networks
by
Gaoyuan Zhang, Hong Wen, Longye Wang, Ping Xie, Liang Song, Jie Tang and Runfa Liao
Cited by 8 | Viewed by 4504
Abstract
In this paper, we propose an adaptive single differential coherent detection (SDCD) scheme for the binary phase shift keying (BPSK) signals in IEEE 802.15.4 Wireless Sensor Networks (WSNs). In particular, the residual carrier frequency offset effect (CFOE) for differential detection is adaptively estimated,
[...] Read more.
In this paper, we propose an adaptive single differential coherent detection (SDCD) scheme for the binary phase shift keying (BPSK) signals in IEEE 802.15.4 Wireless Sensor Networks (WSNs). In particular, the residual carrier frequency offset effect (CFOE) for differential detection is adaptively estimated, with only linear operation, according to the changing channel conditions. It was found that the carrier frequency offset (CFO) and chip signal-to-noise ratio (SNR) conditions do not need a priori knowledge. This partly benefits from that the combination of the trigonometric approximation
and a useful assumption, namely, the asymptotic or high chip SNR, is considered for simplification of the full estimation scheme. Simulation results demonstrate that the proposed algorithm can achieve an accurate estimation and the detection performance can completely meet the requirement of the IEEE 802.15.4 standard, although with a little loss of reliability and robustness as compared with the conventional optimal single-symbol detector.
Full article
►▼
Show Figures
Open AccessArticle
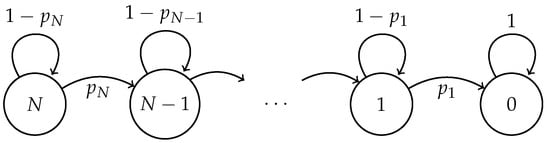
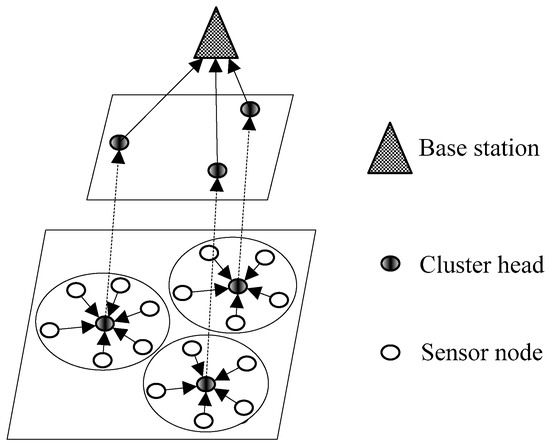
Performance Analysis of Cluster Formation in Wireless Sensor Networks
by
Edgar Romo Montiel, Mario E. Rivero-Angeles, Gerardo Rubino, Heron Molina-Lozano, Rolando Menchaca-Mendez and Ricardo Menchaca-Mendez
Cited by 10 | Viewed by 4413
Abstract
Clustered-based wireless sensor networks have been extensively used in the literature in order to achieve considerable energy consumption reductions. However, two aspects of such systems have been largely overlooked. Namely, the transmission probability used during the cluster formation phase and the way in
[...] Read more.
Clustered-based wireless sensor networks have been extensively used in the literature in order to achieve considerable energy consumption reductions. However, two aspects of such systems have been largely overlooked. Namely, the transmission probability used during the cluster formation phase and the way in which cluster heads are selected. Both of these issues have an important impact on the performance of the system. For the former, it is common to consider that sensor nodes in a clustered-based Wireless Sensor Network (WSN) use a fixed transmission probability to send control data in order to build the clusters. However, due to the highly variable conditions experienced by these networks, a fixed transmission probability may lead to extra energy consumption. In view of this, three different transmission probability strategies are studied: optimal, fixed and adaptive. In this context, we also investigate cluster head selection schemes, specifically, we consider two intelligent schemes based on the fuzzy C-means and k-medoids algorithms and a random selection with no intelligence. We show that the use of intelligent schemes greatly improves the performance of the system, but their use entails higher complexity and selection delay. The main performance metrics considered in this work are energy consumption, successful transmission probability and cluster formation latency. As an additional feature of this work, we study the effect of errors in the wireless channel and the impact on the performance of the system under the different transmission probability schemes.
Full article
►▼
Show Figures
Open AccessArticle
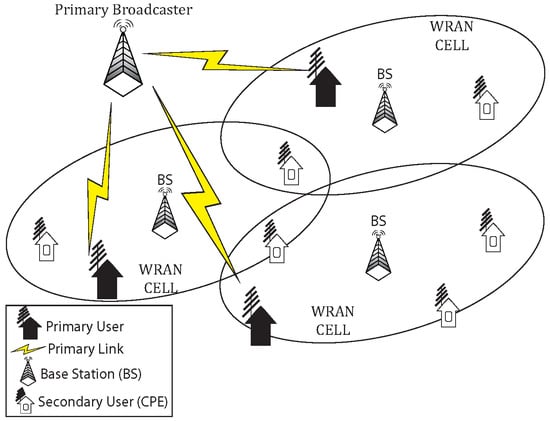
Self-Coexistence among IEEE 802.22 Networks: Distributed Allocation of Power and Channel
by
Sayef Azad Sakin, Md. Abdur Razzaque, Mohammad Mehedi Hassan, Atif Alamri, Nguyen H. Tran and Giancarlo Fortino
Cited by 4 | Viewed by 4444
Abstract
Ensuring self-coexistence among IEEE 802.22 networks is a challenging problem owing to opportunistic access of incumbent-free radio resources by users in co-located networks. In this study, we propose a fully-distributed non-cooperative approach to ensure self-coexistence in downlink channels of IEEE 802.22 networks. We
[...] Read more.
Ensuring self-coexistence among IEEE 802.22 networks is a challenging problem owing to opportunistic access of incumbent-free radio resources by users in co-located networks. In this study, we propose a fully-distributed non-cooperative approach to ensure self-coexistence in downlink channels of IEEE 802.22 networks. We formulate the self-coexistence problem as a mixed-integer non-linear optimization problem for maximizing the network data rate, which is an NP-hard one. This work explores a sub-optimal solution by dividing the optimization problem into downlink channel allocation and power assignment sub-problems. Considering fairness, quality of service and minimum interference for customer-premises-equipment, we also develop a greedy algorithm for channel allocation and a non-cooperative game-theoretic framework for near-optimal power allocation. The base stations of networks are treated as players in a game, where they try to increase spectrum utilization by controlling power and reaching a Nash equilibrium point. We further develop a utility function for the game to increase the data rate by minimizing the transmission power and, subsequently, the interference from neighboring networks. A theoretical proof of the uniqueness and existence of the Nash equilibrium has been presented. Performance improvements in terms of data-rate with a degree of fairness compared to a cooperative branch-and-bound-based algorithm and a non-cooperative greedy approach have been shown through simulation studies.
Full article
►▼
Show Figures
Open AccessArticle
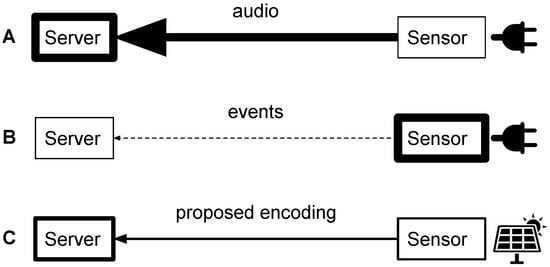
An Efficient Audio Coding Scheme for Quantitative and Qualitative Large Scale Acoustic Monitoring Using the Sensor Grid Approach
by
Félix Gontier, Mathieu Lagrange, Pierre Aumond, Arnaud Can and Catherine Lavandier
Cited by 12 | Viewed by 5018
Abstract
The spreading of urban areas and the growth of human population worldwide raise societal and environmental concerns. To better address these concerns, the monitoring of the acoustic environment in urban as well as rural or wilderness areas is an important matter. Building on
[...] Read more.
The spreading of urban areas and the growth of human population worldwide raise societal and environmental concerns. To better address these concerns, the monitoring of the acoustic environment in urban as well as rural or wilderness areas is an important matter. Building on the recent development of low cost hardware acoustic sensors, we propose in this paper to consider a sensor grid approach to tackle this issue. In this kind of approach, the crucial question is the nature of the data that are transmitted from the sensors to the processing and archival servers. To this end, we propose an efficient audio coding scheme based on third octave band spectral representation that allows: (1) the estimation of standard acoustic indicators; and (2) the recognition of acoustic events at state-of-the-art performance rate. The former is useful to provide quantitative information about the acoustic environment, while the latter is useful to gather qualitative information and build perceptually motivated indicators using for example the emergence of a given sound source. The coding scheme is also demonstrated to transmit spectrally encoded data that, reverted to the time domain using state-of-the-art techniques, are not intelligible, thus protecting the privacy of citizens.
Full article
►▼
Show Figures
Open AccessArticle
A Game Theoretic Approach for Balancing Energy Consumption in Clustered Wireless Sensor Networks
by
Liu Yang, Yinzhi Lu, Lian Xiong, Yang Tao and Yuanchang Zhong
Cited by 36 | Viewed by 4672
Abstract
Clustering is an effective topology control method in wireless sensor networks (WSNs), since it can enhance the network lifetime and scalability. To prolong the network lifetime in clustered WSNs, an efficient cluster head (CH) optimization policy is essential to distribute the energy among
[...] Read more.
Clustering is an effective topology control method in wireless sensor networks (WSNs), since it can enhance the network lifetime and scalability. To prolong the network lifetime in clustered WSNs, an efficient cluster head (CH) optimization policy is essential to distribute the energy among sensor nodes. Recently, game theory has been introduced to model clustering. Each sensor node is considered as a rational and selfish player which will play a clustering game with an equilibrium strategy. Then it decides whether to act as the CH according to this strategy for a tradeoff between providing required services and energy conservation. However, how to get the equilibrium strategy while maximizing the payoff of sensor nodes has rarely been addressed to date. In this paper, we present a game theoretic approach for balancing energy consumption in clustered WSNs. With our novel payoff function, realistic sensor behaviors can be captured well. The energy heterogeneity of nodes is considered by incorporating a penalty mechanism in the payoff function, so the nodes with more energy will compete for CHs more actively. We have obtained the Nash equilibrium (NE) strategy of the clustering game through convex optimization. Specifically, each sensor node can achieve its own maximal payoff when it makes the decision according to this strategy. Through plenty of simulations, our proposed game theoretic clustering is proved to have a good energy balancing performance and consequently the network lifetime is greatly enhanced.
Full article
►▼
Show Figures
Open AccessArticle
Efficient Graph-Based Resource Allocation Scheme Using Maximal Independent Set for Randomly- Deployed Small Star Networks
by
Jian Zhou, Lusheng Wang, Weidong Wang and Qingfeng Zhou
Cited by 7 | Viewed by 4384
Abstract
In future scenarios of heterogeneous and dense networks, randomly-deployed small star networks (SSNs) become a key paradigm, whose system performance is restricted to inter-SSN interference and requires an efficient resource allocation scheme for interference coordination. Traditional resource allocation schemes do not specifically focus
[...] Read more.
In future scenarios of heterogeneous and dense networks, randomly-deployed small star networks (SSNs) become a key paradigm, whose system performance is restricted to inter-SSN interference and requires an efficient resource allocation scheme for interference coordination. Traditional resource allocation schemes do not specifically focus on this paradigm and are usually too time consuming in dense networks. In this article, a very efficient graph-based scheme is proposed, which applies the maximal independent set (MIS) concept in graph theory to help divide SSNs into almost interference-free groups. We first construct an interference graph for the system based on a derived distance threshold indicating for any pair of SSNs whether there is intolerable inter-SSN interference or not. Then, SSNs are divided into MISs, and the same resource can be repetitively used by all the SSNs in each MIS. Empirical parameters and equations are set in the scheme to guarantee high performance. Finally, extensive scenarios both dense and nondense are randomly generated and simulated to demonstrate the performance of our scheme, indicating that it outperforms the classical max K-cut-based scheme in terms of system capacity, utility and especially time cost. Its achieved system capacity, utility and fairness can be close to the near-optimal strategy obtained by a time-consuming simulated annealing search.
Full article
►▼
Show Figures
Open AccessArticle
Multi-Source Cooperative Data Collection with a Mobile Sink for the Wireless Sensor Network
by
Changcai Han and Jinsheng Yang
Cited by 5 | Viewed by 4690
Abstract
The multi-source cooperation integrating distributed low-density parity-check codes is investigated to jointly collect data from multiple sensor nodes to the mobile sink in the wireless sensor network. The one-round and two-round cooperative data collection schemes are proposed according to the moving trajectories of
[...] Read more.
The multi-source cooperation integrating distributed low-density parity-check codes is investigated to jointly collect data from multiple sensor nodes to the mobile sink in the wireless sensor network. The one-round and two-round cooperative data collection schemes are proposed according to the moving trajectories of the sink node. Specifically, two sparse cooperation models are firstly formed based on geographical locations of sensor source nodes, the impairment of inter-node wireless channels and moving trajectories of the mobile sink. Then, distributed low-density parity-check codes are devised to match the directed graphs and cooperation matrices related with the cooperation models. In the proposed schemes, each source node has quite low complexity attributed to the sparse cooperation and the distributed processing. Simulation results reveal that the proposed cooperative data collection schemes obtain significant bit error rate performance and the two-round cooperation exhibits better performance compared with the one-round scheme. The performance can be further improved when more source nodes participate in the sparse cooperation. For the two-round data collection schemes, the performance is evaluated for the wireless sensor networks with different moving trajectories and the variant data sizes.
Full article
►▼
Show Figures
Open AccessArticle
Bio-Inspired Distributed Transmission Power Control Considering QoS Fairness in Wireless Body Area Sensor Networks
by
Chan-Jae Lee, Ji-Young Jung and Jung-Ryun Lee
Cited by 7 | Viewed by 4096
Abstract
Recently, the development of wireless body area sensor network (WBASN) has accelerated due to the rapid development of wireless technology. In the WBASN environment, many WBASNs coexist where communication ranges overlap with each other, resulting in the possibility of interference. Although nodes in
[...] Read more.
Recently, the development of wireless body area sensor network (WBASN) has accelerated due to the rapid development of wireless technology. In the WBASN environment, many WBASNs coexist where communication ranges overlap with each other, resulting in the possibility of interference. Although nodes in a WBASN typically operate at a low power level, to avoid adversely affecting the human body, high transmission rates may be required to support some applications. In addition to this, since many varieties of applications exist in the WBASN environment, each prospective user may have different quality of service (QoS) requirements. Hence, the following issues should be considered in the WBASN environment: (1) interference between adjacent WBASNs, which influences the performance of a specific system, and (2) the degree of satisfaction on the QoS of each user, i.e., the required QoS such as user throughput should be considered to ensure that all users in the network are provided with a fair QoS satisfaction. Thus, in this paper, we propose a transmission power adjustment algorithm that addresses interference problems and guarantees QoS fairness between users. First, we use a new utility function to measure the degree of the satisfaction on the QoS for each user. Then, the transmission power of each sensor node is calculated using the Cucker–Smale model, and the QoS satisfaction of each user is synchronized dispersively. The results of simulations show that the proposed algorithm performs better than existing algorithms, with respect to QoS fairness and energy efficiency.
Full article
►▼
Show Figures
Open AccessArticle
Video Synchronization With Bit-Rate Signals and Correntropy Function
by
Igor Pereira, Luiz F. Silveira and Luiz Gonçalves
Cited by 2 | Viewed by 3740
Abstract
We propose an approach for the synchronization of video streams using correntropy. Essentially, the time offset is calculated on the basis of the instantaneous transfer rates of the video streams that are extracted in the form of a univariate signal known as variable
[...] Read more.
We propose an approach for the synchronization of video streams using correntropy. Essentially, the time offset is calculated on the basis of the instantaneous transfer rates of the video streams that are extracted in the form of a univariate signal known as variable bit-rate (VBR). The state-of-the-art approach uses a window segmentation strategy that is based on consensual zero-mean normalized cross-correlation (ZNCC). This strategy has an elevated computational complexity, making its application to synchronizing online data streaming difficult. Hence, our proposal uses a different window strategy that, together with the correntropy function, allows the synchronization to be performed for online applications. This provides equivalent synchronization scores with a rapid offset determination as the streams come into the system. The efficiency of our approach has been verified through experiments that demonstrate its viability with values that are as precise as those obtained by ZNCC. The proposed approach scored
in time reference classification against the equivalent
of the state-of-the-art approach, requiring much less computational power.
Full article
►▼
Show Figures
Open AccessArticle
Dynamic Hierarchical Energy-Efficient Method Based on Combinatorial Optimization for Wireless Sensor Networks
by
Yuchao Chang, Hongying Tang, Yongbo Cheng, Qin Zhao and Baoqing Li andXiaobing Yuan
Cited by 28 | Viewed by 4564
Abstract
Routing protocols based on topology control are significantly important for improving network longevity in wireless sensor networks (WSNs). Traditionally, some WSN routing protocols distribute uneven network traffic load to sensor nodes, which is not optimal for improving network longevity. Differently to conventional WSN
[...] Read more.
Routing protocols based on topology control are significantly important for improving network longevity in wireless sensor networks (WSNs). Traditionally, some WSN routing protocols distribute uneven network traffic load to sensor nodes, which is not optimal for improving network longevity. Differently to conventional WSN routing protocols, we propose a dynamic hierarchical protocol based on combinatorial optimization (DHCO) to balance energy consumption of sensor nodes and to improve WSN longevity. For each sensor node, the DHCO algorithm obtains the optimal route by establishing a feasible routing set instead of selecting the cluster head or the next hop node. The process of obtaining the optimal route can be formulated as a combinatorial optimization problem. Specifically, the DHCO algorithm is carried out by the following procedures. It employs a hierarchy-based connection mechanism to construct a hierarchical network structure in which each sensor node is assigned to a special hierarchical subset; it utilizes the combinatorial optimization theory to establish the feasible routing set for each sensor node, and takes advantage of the maximum–minimum criterion to obtain their optimal routes to the base station. Various results of simulation experiments show effectiveness and superiority of the DHCO algorithm in comparison with state-of-the-art WSN routing algorithms, including low-energy adaptive clustering hierarchy (LEACH), hybrid energy-efficient distributed clustering (HEED), genetic protocol-based self-organizing network clustering (GASONeC), and double cost function-based routing (DCFR) algorithms.
Full article
►▼
Show Figures
Open AccessArticle
Fuzzy-Logic Based Distributed Energy-Efficient Clustering Algorithm for Wireless Sensor Networks
by
Ying Zhang, Jun Wang, Dezhi Han, Huafeng Wu and Rundong Zhou
Cited by 91 | Viewed by 7951
Abstract
Due to the high-energy efficiency and scalability, the clustering routing algorithm has been widely used in wireless sensor networks (WSNs). In order to gather information more efficiently, each sensor node transmits data to its Cluster Head (CH) to which it belongs, by multi-hop
[...] Read more.
Due to the high-energy efficiency and scalability, the clustering routing algorithm has been widely used in wireless sensor networks (WSNs). In order to gather information more efficiently, each sensor node transmits data to its Cluster Head (CH) to which it belongs, by multi-hop communication. However, the multi-hop communication in the cluster brings the problem of excessive energy consumption of the relay nodes which are closer to the CH. These nodes’ energy will be consumed more quickly than the farther nodes, which brings the negative influence on load balance for the whole networks. Therefore, we propose an energy-efficient distributed clustering algorithm based on fuzzy approach with non-uniform distribution (EEDCF). During CHs’ election, we take nodes’ energies, nodes’ degree and neighbor nodes’ residual energies into consideration as the input parameters. In addition, we take advantage of Takagi, Sugeno and Kang (TSK) fuzzy model instead of traditional method as our inference system to guarantee the quantitative analysis more reasonable. In our scheme, each sensor node calculates the probability of being as CH with the help of fuzzy inference system in a distributed way. The experimental results indicate EEDCF algorithm is better than some current representative methods in aspects of data transmission, energy consumption and lifetime of networks.
Full article
►▼
Show Figures
Open AccessArticle
A Reliable Data Transmission Model for IEEE 802.15.4e Enabled Wireless Sensor Network under WiFi Interference
by
Prasan Kumar Sahoo, Sudhir Ranjan Pattanaik and Shih-Lin Wu
Cited by 34 | Viewed by 7640
Abstract
The IEEE 802.15.4e standard proposes Medium Access Control (MAC) to support collision-free wireless channel access mechanisms for industrial, commercial and healthcare applications. However, unnecessary wastage of energy and bandwidth consumption occur due to inefficient backoff management and collisions. In this paper, a new
[...] Read more.
The IEEE 802.15.4e standard proposes Medium Access Control (MAC) to support collision-free wireless channel access mechanisms for industrial, commercial and healthcare applications. However, unnecessary wastage of energy and bandwidth consumption occur due to inefficient backoff management and collisions. In this paper, a new channel access mechanism is designed for the buffer constraint sensor devices to reduce the packet drop rate, energy consumption and collisions. In order to avoid collision due to the hidden terminal problem, a new frame structure is designed for the data transmission. A new superframe structure is proposed to mitigate the problems due to WiFi and ZigBee interference. A modified superframe structure with a new retransmission opportunity for failure devices is proposed to reduce the collisions and retransmission delay with high reliability. Performance evaluation and validation of our scheme indicate that the packet drop rate, throughput, reliability, energy consumption and average delay of the nodes can be improved significantly.
Full article
►▼
Show Figures
Open AccessArticle
A Protocol Layer Trust-Based Intrusion Detection Scheme for Wireless Sensor Networks
by
Jian Wang, Shuai Jiang and Abraham O. Fapojuwo
Cited by 37 | Viewed by 5973
Abstract
This article proposes a protocol layer trust-based intrusion detection scheme for wireless sensor networks. Unlike existing work, the trust value of a sensor node is evaluated according to the deviations of key parameters at each protocol layer considering the attacks initiated at different
[...] Read more.
This article proposes a protocol layer trust-based intrusion detection scheme for wireless sensor networks. Unlike existing work, the trust value of a sensor node is evaluated according to the deviations of key parameters at each protocol layer considering the attacks initiated at different protocol layers will inevitably have impacts on the parameters of the corresponding protocol layers. For simplicity, the paper mainly considers three aspects of trustworthiness, namely physical layer trust, media access control layer trust and network layer trust. The per-layer trust metrics are then combined to determine the overall trust metric of a sensor node. The performance of the proposed intrusion detection mechanism is then analyzed using the t-distribution to derive analytical results of false positive and false negative probabilities. Numerical analytical results, validated by simulation results, are presented in different attack scenarios. It is shown that the proposed protocol layer trust-based intrusion detection scheme outperforms a state-of-the-art scheme in terms of detection probability and false probability, demonstrating its usefulness for detecting cross-layer attacks.
Full article
►▼
Show Figures
Open AccessArticle
Power Allocation Based on Data Classification in Wireless Sensor Networks
by
Houlian Wang and Gongbo Zhou
Cited by 6 | Viewed by 4401
Abstract
Limited node energy in wireless sensor networks is a crucial factor which affects the monitoring of equipment operation and working conditions in coal mines. In addition, due to heterogeneous nodes and different data acquisition rates, the number of arriving packets in a queue
[...] Read more.
Limited node energy in wireless sensor networks is a crucial factor which affects the monitoring of equipment operation and working conditions in coal mines. In addition, due to heterogeneous nodes and different data acquisition rates, the number of arriving packets in a queue network can differ, which may lead to some queue lengths reaching the maximum value earlier compared with others. In order to tackle these two problems, an optimal power allocation strategy based on classified data is proposed in this paper. Arriving data is classified into dissimilar classes depending on the number of arriving packets. The problem is formulated as a Lyapunov drift optimization with the objective of minimizing the weight sum of average power consumption and average data class. As a result, a suboptimal distributed algorithm without any knowledge of system statistics is presented. The simulations, conducted in the perfect channel state information (CSI) case and the imperfect CSI case, reveal that the utility can be pushed arbitrarily close to optimal by increasing the parameter
V, but with a corresponding growth in the average delay, and that other tunable parameters
W and the classification method in the interior of utility function can trade power optimality for increased average data class. The above results show that data in a high class has priorities to be processed than data in a low class, and energy consumption can be minimized in this resource allocation strategy.
Full article
►▼
Show Figures
Open AccessArticle
DCE: A Distributed Energy-Efficient Clustering Protocol for Wireless Sensor Network Based on Double-Phase Cluster-Head Election
by
Ruisong Han, Wei Yang, Yipeng Wang and Kaiming You
Cited by 42 | Viewed by 7453
Abstract
Clustering is an effective technique used to reduce energy consumption and extend the lifetime of wireless sensor network (WSN). The characteristic of energy heterogeneity of WSNs should be considered when designing clustering protocols. We propose and evaluate a novel distributed energy-efficient clustering protocol
[...] Read more.
Clustering is an effective technique used to reduce energy consumption and extend the lifetime of wireless sensor network (WSN). The characteristic of energy heterogeneity of WSNs should be considered when designing clustering protocols. We propose and evaluate a novel distributed energy-efficient clustering protocol called DCE for heterogeneous wireless sensor networks, based on a Double-phase Cluster-head Election scheme. In DCE, the procedure of cluster head election is divided into two phases. In the first phase, tentative cluster heads are elected with the probabilities which are decided by the relative levels of initial and residual energy. Then, in the second phase, the tentative cluster heads are replaced by their cluster members to form the final set of cluster heads if any member in their cluster has more residual energy. Employing two phases for cluster-head election ensures that the nodes with more energy have a higher chance to be cluster heads. Energy consumption is well-distributed in the proposed protocol, and the simulation results show that DCE achieves longer stability periods than other typical clustering protocols in heterogeneous scenarios.
Full article
►▼
Show Figures